DragonForce: The Ransomware Cartel Guarding Its Burrow

DragonForce is a threat actor that takes deliberate steps to grow its influence within the ransomware ecosystem. Since initial reports documenting DragonForce attacks circulated in 2023, the group has shifted its operational model, developed affiliate connections, and appealed to emerging and longstanding operators. These elements have combined to make DragonForce a ransomware group to watch in 2025.
Who is DragonForce?
Not to be confused with the metal band of the same name, DragonForce refers to a ransomware group that was identified in fall 2023. The threat actor once operated within the context of a Ransomware as a Service (RaaS) model and pivoted to operate as a ransomware cartel. There is some debate about whether this DragonForce group is the same entity associated with a hacktivist group. The hacktivist group known as DragonForce (Malaysia) was recognized back in 2021. DragonForce Malaysia previously launched attacks against organizations based in the Middle East several years ago.
Where Are They Based and Who Might They Support?
Despite the previously known DragonForce operating in Malaysia, there is no data to suggest that the current DragonForce ransomware group is based there. The threat actor has used Russian-linked infrastructure which supports previous claims that the group has Russian-aligned interests within their cybercrime operations. The group previously posted on the RAMP platform, expressing a need for more recruits. And RansomHub members even accused the group of associating with the FSB, a Russian intelligence unit.
What Distinguishes a Hacktivist Group from a Ransomware Group?
DragonForce has used ransomware throughout its operations. The DragonForce ransomware that was used in late 2023, leading into the first half of 2024, shared several characteristics with LockBit 3.0. However, DragonForce implemented changes during the summer of 2024, adopting a RaaS model and deploying a Conti variant.
While collaborations between ransomware and hacktivist groups exist and traits associated with the two can become blurred, we do not currently characterize DragonForce as a hacktivist group.
Hacktivist groups differ from ransomware groups in several ways. It is customary for hacktivists to be motivated by geopolitical influences, or a militant ideology bound by ideas of justice or rebellion. Ransomware groups, on the other hand, are typically motivated by financial gain.
A hacktivist or hacktivist collective may shift to operating as a ransomware group to maneuver with fewer restrictions surrounding who they’d attack or partner with. Hacktivists often have political motivations for harming select targets and may limit their victims, as a result, to organizations based in a particular region, sector, or size.
They could also choose for instance to adopt some rules of engagement to prohibit attacks against more controversial victims such as non-profit organizations in healthcare, entrepreneurial businesses with limited resources, or public sector organizations in education. Deciding to shift to ransomware operations may also follow issues such as restaffing or a takeover.
Ransomware, distributed as a result of a code leak or an OPSEC failure, can also create the opportunity for a hacktivist group to transform it, for their own campaign.
Quality Over Quantity - DragonForce Attack Rates
DragonForce claimed more than 120 victims in the past year. The group has attacked organizations based in countries that include the United States, Italy, and Australia. And, they have developed encryptors used against Windows, Linux, and ESXi environments.
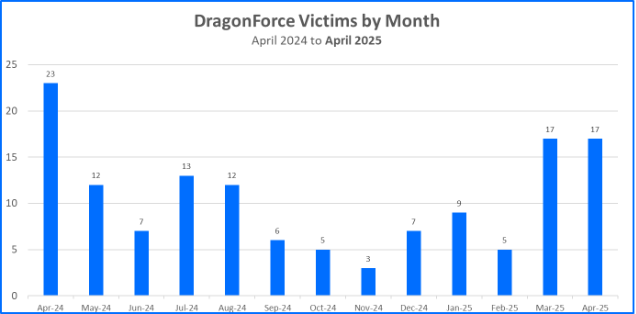
DragonForce claimed their largest number of victims per month, 23 in total, in April of 2024. While this total may pale in comparison to the victim totals of other groups such as RansomHub, DragonForce’s presence and strategy seem to be enabling its own ongoing success in the ransomware ecosystem.
DragonForce has targeted organizations in manufacturing, construction, technology, healthcare, and retail industries. The group posts ransom demands that vary tremendously, from several hundred thousand to millions of dollars. They exercise due diligence in researching organizations and their estimated revenue to generate ransom amounts. During a 2024 DragonForce chat with a victim, the group demanded a $7 million ransom.
The DragonForce Data Leak Site
DragonForce uses a data leak site and has done so since mid-2024. The group initially hosted a chat server as well. The site changes as the group does, including the March 2025 announcement of the DragonForce ransomware cartel.
![]()

The DragonNews blog section of the data leak site lists entries of victim organizations, including the victim’s site, the size of the stolen data, and the data leak publication date — or time remaining until publication. DragonForce recently removed the CAPTCHA verification that was implemented on their data leak site. While this may have been done to increase their visibility among other threat actors and the public, it’s also possible that a future update may enforce another verification method.
Visitors can view the file/folder structures of stolen data under select blog pages and be redirected to DragonFiles to view and download their contents. Since early May, the site has been under a global update model.
Events Throughout the Cartel Transformation
In the last few months DragonForce interacted with several other threat actors. More recently, it was reported that DragonForce claimed victims in the retail industry in a manner similar to another threat actor named Scattered Spider. Scattered Spider has formed tactical partnerships with other ransomware groups, especially those affiliated with Russia in the past, including ALPHV and RansomHub. Scattered Spider has gained initial access to systems by using social engineering techniques, masquerading as IT to help staff in need of assistance before deploying DragonForce ransomware and other malicious tools.
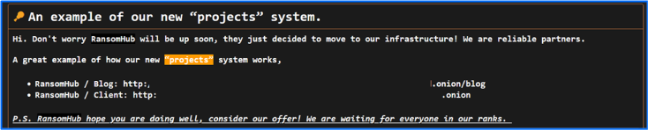
In early May, DragonForce posted: An example of our new “projects” system on the data leak site. The post referenced onion links, which have been obscured in the figure below, to RansomHub’s blog and infrastructure. Once selected, those links redirected to a page which displayed the text: RansomHub R.I.P. (03.03.2025).
![]()
![]()
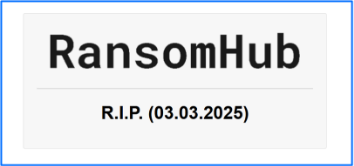
These actions took place several weeks after RansomHub’s infrastructure was taken offline and DragonForce announced a partnership. However, a post on their data leak site still encourages RansomHub to join their ranks, which suggests that RansomHub did not voluntarily agree to establish a partnership.
In March 2025, DragonForce also defaced the data leak site of a group named Mamona after Mamona’s infrastructure was published online. Mamona’s defacement was likely part of a premediated plan to take down emerging RaaS groups.
What’s In It for Me: The Cartel Perspective
DragonForce differs from other RaaS groups because in addition to offering partners 80% of their profits, they also provide the infrastructure necessary for their partners to manage a presence online and deploy ransomware attacks. Additionally, DragonForce provides automation of work processes, a blog, file server, admin and client panels, 24/7 monitoring, petabytes of storage, Kerb decryption and other benefits.
The Windows encryptors are designed to enable partial, full, and header encryption. Filename or log encryption is supported, and encryption can be set to select folders. When examining the DragonForce DLS, it also appears that the group has taken lessons learned from an Akira decryption process, publicized earlier this year, that uses a GPU cluster, to improve their own encryption and file recovery methods for Linux, ESXi and other systems. Additional information on encryption parameters for these systems is captured below.
Fig. 4, Encryption features for ESXi, Linux, BSD and NAS.
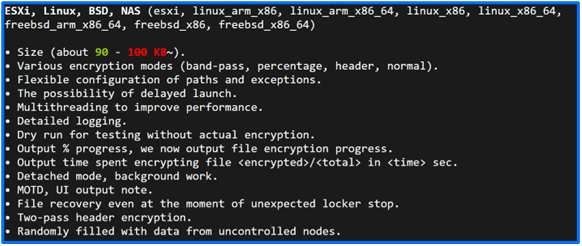
By aiding other ransomware groups in setting up an infrastructure, DragonForce controls the resources of allies and competitors. They have the ability to eradicate or terminate services attached to threat actors who may develop interests that clash with their own or get in the way of their profits.
Russian Cannibalism - Who Is Overtaking the Russians?
RansomHub, a prominent Russian threat actor in the ransomware ecosystem, went offline in April. A month later, LockBit suffered a compromise. The LockBit incident culminated in a message left on the victim infrastructure that read "Don't do crime CRIME IS BAD xoxo from Prague”. Could DragonForce be the threat actor who compromised LockBit? It’s possible. Variables such as DragonForce’s expanding affiliate base, which could be made up of insider staff or rival groups, also add a degree of plausibility to this working theory.
Why dominate other groups for resources and victims? With DragonForce only claiming 20% of affiliate profits, a move like this may have less to do with widening profits and more to do with influence and power. Efforts to eliminate competition or additional conflicts can also provide some assurance that operations will not cease if schisms, common in the turbulent ransomware economy, pit allied groups against each other. DragonForce’s push to provide infrastructure and services alongside their ability to limit or terminate those services is one way to prevent fallout from short-lived or volatile affiliate relationships.
Tactics, Techniques and Procedures
Initial Access
DragonForce is able to establish initial access to target systems through exposed credentials and other means, including phishing and exploiting flaws in applications. Notably, the group exploits multiple vulnerabilities to conduct attacks. These vulnerabilities include CVE-2024-21412, CVE-2024-21887, and CVE-2024-21893.
Execution
The dragonfroce.exe ransomware can be executed through a few different methods. One tactic leverages commands within Windows Command Shell. Another method involves abusing shared modules or leveraging DLL hijacking.
Persistence
DragonForce has leveraged Living Off the Land techniques, using legitimate executables such as Schtasks.exe and Taskkill.exe to establish persistence. This allows the group to add scheduled tasks, introduce malicious payloads, alter system settings and other data, and terminate active tasks. The group also alters Power Settings to establish persistence, preventing a system from changing states or rebooting.
Defense Evasion
The ransomware is equipped to perform actions such as deleting files, timestomping, and modifying security tools. The group's ransomware is also equipped with discovery capabilities to identify analysis and debugging environments and prevent the malware from running in these settings.
Discovery
DragonForce performs discovery actions, including identifying remote systems, application windows, and identifying network connections and network configurations.
Lateral Movement
DragonForce abused an RMM tool named SimpleHelp in recent campaigns against managed service providers. The RMM tool is a convenient way for them to leverage an application that is typically permitted in enterprise environments for admin purposes.
After establishing remote control to other systems, they’re able to move throughout the network. The use of an RMM is just one type of Living Off the Land technique that is increasing in prevalence. A recent Bitdefender analysis of 700,000 cyber incidents revealed that 84% of critical attacks involve Living Off the Land tactics. Excluding the use of Living Off the Land techniques, the DragonForce ransomware is also capable of replicating through removable media connected to victim systems.
Command and Control
DragonForce utilizes Ingress Tool Transfer, a method of moving tools from the adversary’s controlled environment to the victim’s network. This technique is typically executed by using protocols such as FTP. However, other methods involving Certuitl.exe or PowerShell commands may also be used.
Impact
Once the attacker executes the ransomware to encrypt data, .dragonforce_encrypted is appended to affected files.
Ransom Note
In the ransomware execution process, a ransom demand is issued. The following excerpt was extracted from a DragonForce ransom note:
Hello!
Your files have been stolen from your network and encrypted with a strong algorithm. We work for money and are not associated with politics. All you need to do is contact us and pay.
--- Our communication process:
- You contact
- We send you a list of files that were stolen.
- We decrypt 1 file to confirm that our decryptor works.
- We agree on the amount, which must be paid using BTC.
- We delete your files, we give you a decryptor.
- We give you a detailed report on how we compromised your company, and recommendations on how to avoid such situations in the future.
--- Recommendations:
DO NOT RESET OR SHUTDOWN - files may be damaged.
DO NOT RENAME OR MOVE the encrypted and readme files.
DO NOT DELETE readme files.
--- Important:
If you refuse to pay or do not get in touch with us, we start publishing your files.
…(redacted). the decryptor will be destroyed and the files will be published on our blog.
Sincerely, 01000100 01110010 01100001 01100111 01101111 01101110 01000110 01101111 01110010 01100011 01100101
Bitdefender Recommendations
A multi-layered security approach that combines Prevention, Protection, Detection, and Response security measures is essential to mitigate ransomware risk and develop a mature security posture.
Prevention security practices, notably Patch Management and Risk Management aid an organization in mitigating weak points such as using out of date or vulnerable system components before they become severe risks.
Protection security practices, including but not limited to Network Protection, Malware Protection, and Ransomware Protection are also instrumental in keeping both sensitive data and system resources secure. In addition, implementing multi-factor authentication (MFA) can add another layer of defense, making it more difficult for threat actors, including those who have obtained exposed credentials, to gain unauthorized access to a target system.
Advanced Threat Intelligence: The right threat intelligence solutions can provide critical insights into attacks. Bitdefender’s IntelliZone consolidates all the knowledge we've gathered on cyber threats and the associated threat actors into a single console for security analysts to leverage. If you have an IntelliZone account, you can find additional structured information under the following Threat IDs: BDwi1buv8f, BDm18y8qto, BDxso4f8qr, and BDuwpdacqn.
Detection practices that include Incident Investigation and Forensics and Threat Response aid organizations in maintaining continuous practices in order to identify activities and IOCs to investigate—along with measures to respond to events and incidents as they occur.
Understanding how legitimate binaries can be abused in your environment and the risk profile that encompasses your unique users and assets are crucial steps to building a proactive defense strategy. Our GravityZone PHASR (Proactive Hardening and Attack Surface Reduction) technology combines machine learning with behavioral analysis to identify attack vectors and implement actionable, customized recommendations to reduce the attack surface.
PHASR is also unique because it proactively evaluates LOTL use cases. It can identify and prevent attacks that operate using similar malicious contexts across ransomware and attacker playbooks. More information on LOTL attacks can be found in our webinar.
Indicators of Compromise
DragonForce is a ransomware group to watch in 2025. Here are IOCs associated with this threat actor:
| SHA256 |
| e1b147aa2efa6849743f570a3aca8390faf4b90aed490a5682816dd9ef10e473 |
| 7126b9932dc0cdfe751340edfa7c4a14b69262eb1afd0530e6d1fdb2e25986dd |
| ba1be94550898eedb10eb73cb5383a2d1050e96ec4df8e0bf680d3e76a9e2429 |
| 88169b1d4778ed6c5fda97375efb5b9171ea52649c8715bb449801c39bce4ad4 |
| 5c54bd1aa2abf024f53490b7d93101496b5842a5a81a51955fe7f1d5e4281409 |
| 01f1e82d4c2b04a4652348fb18bb480396db2229c4fd22d2be1ea58e6bf4a570 |
| 312ca1a8e35dcf5b80b1526948bd1081fed2293b31d061635e9f048f3fe5eb83 |
| d4de7d7990114c51056afeedb827d880549d5761aac6bdef0f14cb17c25103b3 |
tags
Author
Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks