What is Split Tunneling and How Does It Work?
VPN is gaining popularity nowadays as casual Internet users grow more concerned about online privacy. A trustworthy VPN in today’s climate is paramount to keep your online whereabouts away from prying eyes.
All VPN services share two important advantages that keep your privacy safe:
- A network of private servers where the VPN directs your traffic
- Solid encryption technology
Without either one, VPN would probably be quickly surpassed by other privacy services, such as proxy servers or HTTPS. And, aside from these critical features that ensure their functionality, modern VPN solutions also incorporate additional features for convenience.
Some now include a kill switch, which we previously discussed, and split tunneling. Although it sounds convoluted, we can assure you that split tunneling is not only a handy feature, but a simple one, too.
What is split tunneling?
VPN services protect your privacy by redirecting your traffic away from its usual ISP-assigned route. They also encrypt that traffic, so even if someone did intercept it, they couldn’t make anything of it.
These tools create a virtual network adapter on your computer and use it to connect to a virtual private network (i.e., a VPN).
It’s worth mentioning that the VPN connection supersedes your regular, unencrypted one; in simpler terms, it stacks on top of it, so online entities no longer detect you on your regular (home or work) network.
Although that sounds like good news, if you have shared resources (documents, devices, or services) on your local network, connecting to a VPN means they’ll become inaccessible to you.
For instance, if you have a shared folder on your home network, you may no longer be able to access it while you’re connected to the VPN, since you’re technically not on your home network anymore.
The same goes for network printers, mail servers, multimedia servers, and everything else you host locally.
That’s where split tunneling comes in: this feature essentially splits your connection, letting you choose which apps go through the VPN’s encrypted tunnel and which don’t.
Why should you use split tunneling?
Although the example above is among the most common, split tunneling is handy for many other reasons, namely:
- Preserve Bandwidth– VPN traffic is encrypted, so it’s transmitted slower than regular, unencrypted traffic. Enabling split tunneling can enhance speed, which is paramount if the network has bandwidth restrictions.
- Use LAN Resources – If you need to access network resources such as shared folders, devices or services, doing so is impossible if your entire traffic is routed through a VPN tunnel. Split tunneling lets you exclude certain apps or services from being tunneled, letting you access LAN resources.
- Enhanced Security for Remote Workers – Split tunneling lets employees work remotely with sensitive resources securely through an encrypted connection while also letting them access other non-critical Internet resources faster through their ISP connection.
- Flexibility – While traveling, you can use split-tunneling to access content in your home country and still access potentially geo-restricted local websites by excluding certain apps from the encrypted VPN tunnel (i.e., your web browser).
Bitdefender VPN includes split tunneling
Sturdy VPN solutions, such as Bitdefender VPN, embrace split tunneling, increasing the convenience and flexibility of the product.
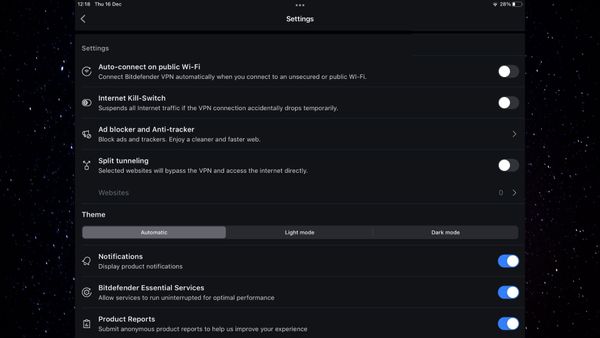
To enable it, access the Settings menu, then flip the Split tunneling switch on. Once you’ve toggled the feature, you’ll also need to configure the websites that will bypass your VPN connection.
We recommend keeping the list as light as possible and only excluding websites from the VPN tunnel if absolutely necessary.
tags
Author

Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









