Stop emerging attacks by automatically ingesting fresh malicious data on prolific cyber threats.
Automatically detect more threats faster, with specialized M2M (machine-to-machine) data extracted from Bitdefender’s large sensor base.
Reduce breach odds and detection time by integrating the latest threat data into your EDR/XDR platforms.
Bitdefender’s Reputation Threat Intelligence delivers high quality, high quantities of indicators of compromise (IoCs) like IP addresses, file hashes, URLs, and more. Pulled from over 500 million global sensors, this data is ready for M2M (machine to machine) integration.
Bitdefender Reputation Threat Intelligence Services can augment the detection and filtering capabilities of security solution vendors.
By ingesting large quantities of updated Indicators of Compromise delivered in real time, partners can enhance the effectiveness of backend systems for EDR/EPP solutions, NGFWs, UTMs, and more.
This expanded visibility can aid licensees with threat exposure management, overall security posturing, risk assessment, and more.
Reputation Threat Intelligence Feeds and APIs
Partners can license a variety of Reputation TI feeds and APIs, depending on their needs and visibility gaps.
Consistent performance above any other competitor.

34% of top performing AV-Comparatives products use our SDKs
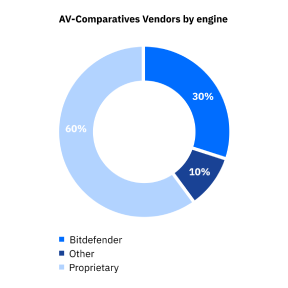
Bitdefender achieved 100% analytical coverage for both Linux and macOS, with zero False Positives (FPs) in both cases.

A Customers' Choice in EMEA
Gartner® Peer Insights™



Bitdefender has been at the forefront of cybersecurity innovation for over 20 years. Use the technologies we’ve built in this time to grow your business.