Hitler Ransomware Revived in Roblox Executors

Imagine a simple scenario: a kid playing Roblox wants to enhance his gameplay by downloading some files he found online. He installs the files and a countdown starts. A simple message accompanied by an image referencing Adolf Hitler demands payment via gift card, warning that files will be deleted in 1 hour. It looks terrifying – and that’s by design.
This isn’t some new cyberattack. It’s actually an old malware named “Hitler Ransomware,” which seems to be resurfacing in 2025 through Roblox exploits that pose as “Synapse X Revival” tools, according to a Reddit user who made the mistake of downloading malware.
While it might not encrypt the user’s data, it can still wipe files – or even the entire operating system if ignored. Even worse, it might simply be yet another way to run much more dangerous and current malware in the background.
Editorial Note:
This article is intended for informational and educational purposes only. It does not promote, justify, or glorify Adolf Hitler, the Nazi regime, or its symbols. The purpose of this article is to raise awareness about the resurgence of a piece of malware known as “Hitler Ransomware,” which uses that imagery in its design.
What Is Hitler Ransomware?
Hitler ransomware found in Roblox Executors. This is one sentence people don’t often hear.
The malware was first spotted in 2016. Hitler Ransomware is better described as a screen locker rather than real ransomware. In this case, it uses shock imagery and a countdown timer to scare people into paying small ransoms via Vodafone or Google Play gift cards.
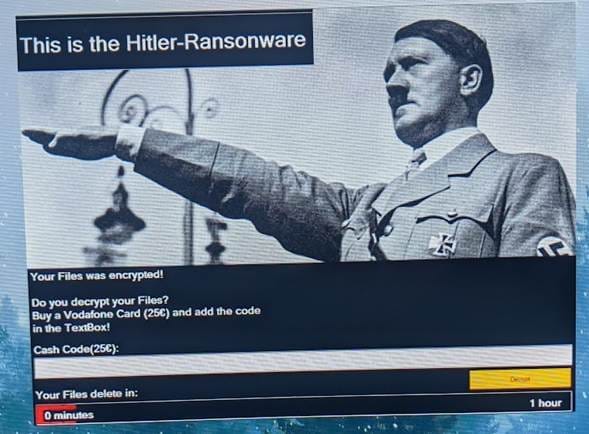
There were several variants and updates to the initial malware, some of which don’t even have a timer.
Instead of encrypting files, it tries to:
- Lock the computer’s display.
- Trigger a forced restart after the timer expires.
- Delete files from the C:\Users directory using a batch script, or even attempt to crash the OS.
Now, the same type of malware has reappeared in fake Roblox exploit downloads. There seems to be more than one version floating around, a clone that uses the name ‘The Führer Ransomware’ in its interface.
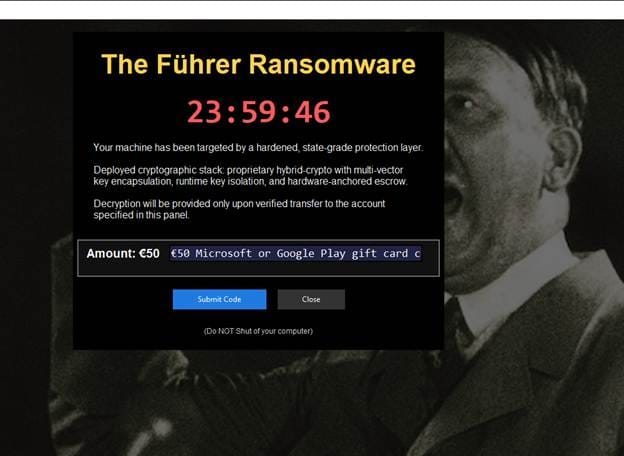
Both follow the same pattern:
- Fake “encryption complete” message.
- Timer counting down to deletion.
- A simplistic GUI with fake ransom instructions.
It’s also highly likely that these screen lockers can hide real data stealers in the same package, making them more than just a prank.
The Truth About “Synapse X Revival” Tools
Synapse X was a very real Roblox exploit engine project, which was a paid scripting tool developers and modders used to inject custom Lua scripts into Roblox. That changed when its creators had to shut it down in 2023 after legal pressure.
After the project was shuttered, tons of unofficial “revival” projects appeared out of nowhere on Discord, YouTube and forums. They all claim to bring “Synapse X Revival” or “Synapse X 2025 Edition” back for free.
Many of these projects actually spread malware and just use Synapse’s former popularity as bait.
There are many GitHub repositories claiming to be “Synapse X”, “Synapse X Fork”, “Synapse X 2025,” but the best the user can hope is that it’s just an innocent fork.
What’s Inside These Fake Tools
When users download Roblox executors, their systems often get infected.
The bundles often include:
- Fake ransomware lockers, like Hitler Ransomware or its “Führer” clone.
- Password and cookie stealers that target Roblox, Discord, Steam credentials, and browser sessions.
- Cryptominers and droppers that silently install other types of malware.
- Persistence scripts that ensure the malware survives reboot.
These “revival” packs typically use social engineering: friendly YouTube tutorials, Discord giveaways, or “community fixes” that are there only to convince Roblox players to disable the security solution before running them.
How to Remove Hitler Ransomware Safely
- Isolate the Device
Disconnect from Wi-Fi or LAN immediately to prevent data loss or spread. It’s a distinct possibility that the device is infected with other kinds of threats.
- Run an Offline Scan
Use Bitdefender Rescue Environment to remove the locker and any hidden payloads. This can be done from Windows OS if the security solution is available. If not, it can be started from Safe Mode.
- Re-enable Protections
After cleanup, re-enable real-time protection, update your security solution, and change all online passwords.
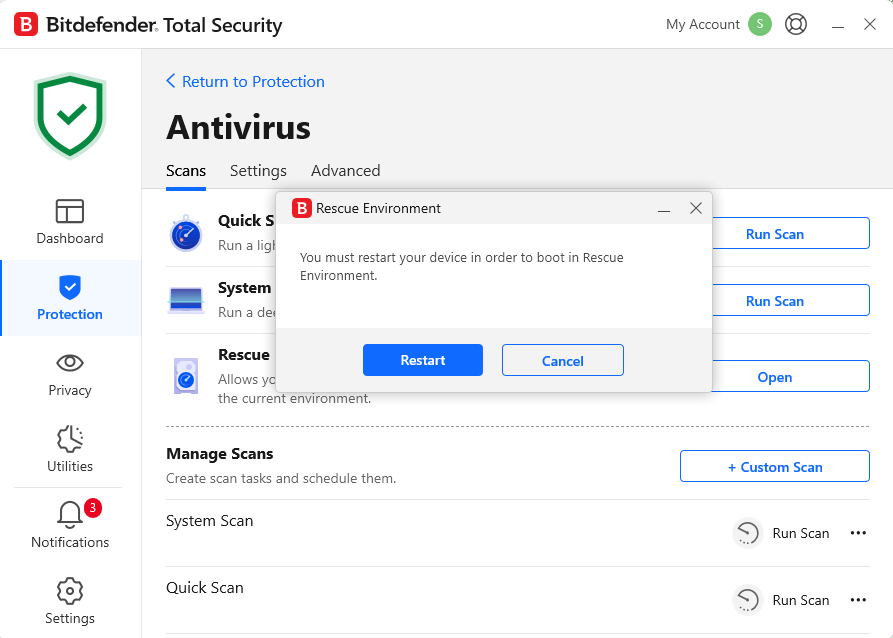
Keep in mind that while Total Security is running, Roblox players won’t get infected by running these infected executors, because malware installation (and even downloading) will be blocked. Unfortunately, victims are persuaded to turn off security solutions.
Protect Yourself with Bitdefender
Bitdefender detects and blocks both screen lockers and file-encrypting ransomware before they launch.
Use Bitdefender Total Security to:
- Detect trojans hidden in mods, trainers, cracks, archives, and any other files.
- Use the Game mode available for users who want the best possible performance.
- Protect against ransomware with a dedicated technology designed specifically for this purpose.
- Roll back unauthorized file deletions.
- Protect backups from tampering.
FAQ: Everything You Need to Know About Hitler Ransomware
1. Is Hitler Ransomware real?
Yes, but it’s more of a screen-locking hoax than true ransomware. It’s still dangerous and can cause real harm.
2. Does it encrypt files?
No. It uses scare tactics and may delete files using a script, but it doesn’t encrypt anything.
3. What is “The Führer Ransomware”?
It seems to be a clone or an evolution of the same locker, distributed through channels like fake Roblox tools.
4. How do I remove it if my antivirus won’t open?
Use Bitdefender’s Rescue Environment. It runs outside Windows and cleans even locked systems.
5. Should I pay the ransom?
Never. It won’t decrypt or recover files. The locker only tries to scare victims. There's also a distinct possibility that other types of malware are installed in the background.
6. How can I prevent this?
Avoid unverified downloads, enable real-time protection, and back up your files regularly. Always be suspicious of advice that includes the “option” to disable the security solution.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
Microsoft Is Done With Windows 10 but Bitdefender Will Keep You Safe Until October 2026
October 14, 2025
Recruitment Scam Alert: Fraudsters Impersonate Bitdefender in Fake Job Interviews
October 13, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







