French submarine secrets surface after cyber attack

European defence giant Naval Group has confirmed that it is investigating an alleged cyber attack which has seen what purports to be sensitive internal data published on the internet by hackers.
Naval Group builds and maintains an array of ships and submarines for the French navy, including aircraft carriers and nuclear submarines. It counts several foreign navies amongst its customers including India and Brazil.
As such, a security breach against the defence contractor should be considered a concern for not just France's national security, but that of other nations as well.
The alleged breach first came to light after a hacker calling themselves "Neferpitou" put up for sale what they claimed to be approximately 1 TB of Naval Group's internal data, offering a 13GB free "sample" of its contents.
The announcement was made in a post on an underground hacking forum.
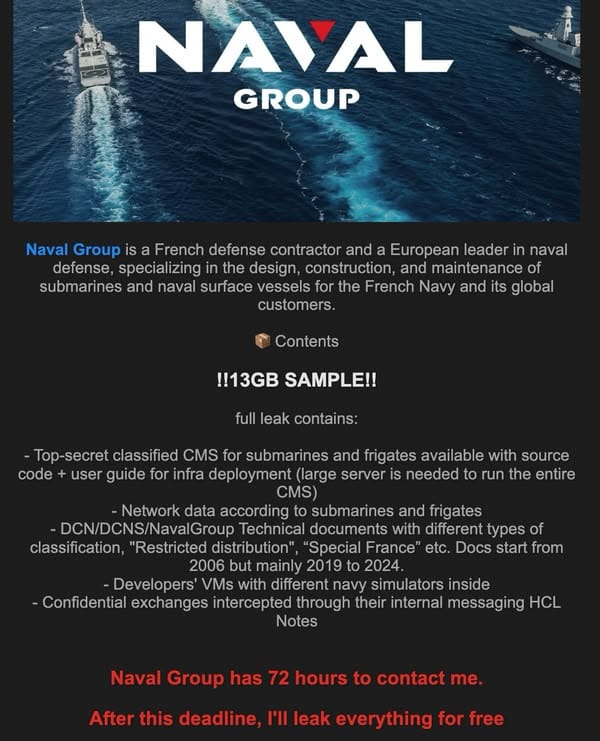
The data was said to include source code related to combat systems used on French nuclear submarines and frigates, weapon system software, simulation environments, network designs, user manuals, and internal communications.
In their forum post on 23 July, Neferpitou said that Naval Group had 72 hours to make contact or "I'll leak everything for free." No ransom demand has been made public to date.
On 25 July, Neferpitou posted an update sharing a link to more detail and said that Naval Group had 24 hours left to contact them.
True to their word, the hacker posted again on Saturday 26 July, sharing a link to what they claimed was the entirety of the leaked data, under a banner saying "!! ENJOY AND SEE YOU NEXT TIME !!"
In what seems likely to be an indication of how Neferpitou gained access, the hacker signed off with the message:
"Keep in mind, nothing is truly disconnected from Internet..."
At this point Naval Group issued a statement in French and English, saying that it was aware of the cyber attack claim, and that it had launched a technical investigation supported by a team of cybersecurity experts.

The statement said that it was analysing and verifying the authenticity of the data that had been shared online in what it described as a "reputational attack."
"At this stage, no intrusion into our IT environments has been detected and there has been no impact on our activities," concluded Naval Group's advisory.
Last week, Microsoft warned that Chinese hackers were actively exploiting a remote code execution vulnerability known as "ToolShell" in businesses' SharePoint servers.
The vulnerability, known technically as CVE-2025-53770, was determined by Bitdefender researchers to have compromised systems across Europe, the Middle East, and North America.
Although it has not been confirmed that the source of Naval Group's leak was due to exploitation of an on-premises SharePoint server, what is undeniable is that there has been a long history of countries breaching the defence infrastructure of other nations to gather intelligence and cause disruption.
Cybercriminals, whether state-sponsored or not, are interested in stealing sensitive information which could have more than a financial value.
All businesses, regardless of whether they work in the defence sector or not, would be foolish to ignore the threat posed by hackers. It is essential to ensure that your organisation has strong defences in place to reduce the risk of a successful attack.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







