E-mails claiming your computer was hacked and your privacy exposed - what you need to know (spoiler: you can relax - they’re bluffing)

In the past two weeks, Bitdefender Antispam Lab has been tracking a couple of extensive extortion campaigns leveraging user credentials exposed in data breaches and leaks in recent years.
The attacks spread across the globe, with unusually high numbers of spam emails reaching users in Romania (over 400,000 emails), Italy and the Netherlands. The messages originate from multiple IP addresses in Europe, Asia, Africa and the Americas. It seems they've been distributed en masse via a large spam botnet controlled by the same threat group.
The spammers bombard inboxes under a spray and pray model in the hopes of deceiving as many victims as possible. Specifics of these extortion scams are not new. While some scammers occasionally spawn new and convincing ruses to dupe victims, the most recent attempts build upon previous scams, borrowing previously used arguments and scare tactics. In this case, spammers attempt to fool recipients by referring to old passwords and existing email addresses, most of which have already been exposed online.
The perps specify that login credentials to your online accounts were purchased from the web and used to install malicious software and spyware on your device. They use scare tactics to induce a sense of panic in recipients, threatening to expose a video montage containing lewd scenes of victims watching adult videos online to friends and family.
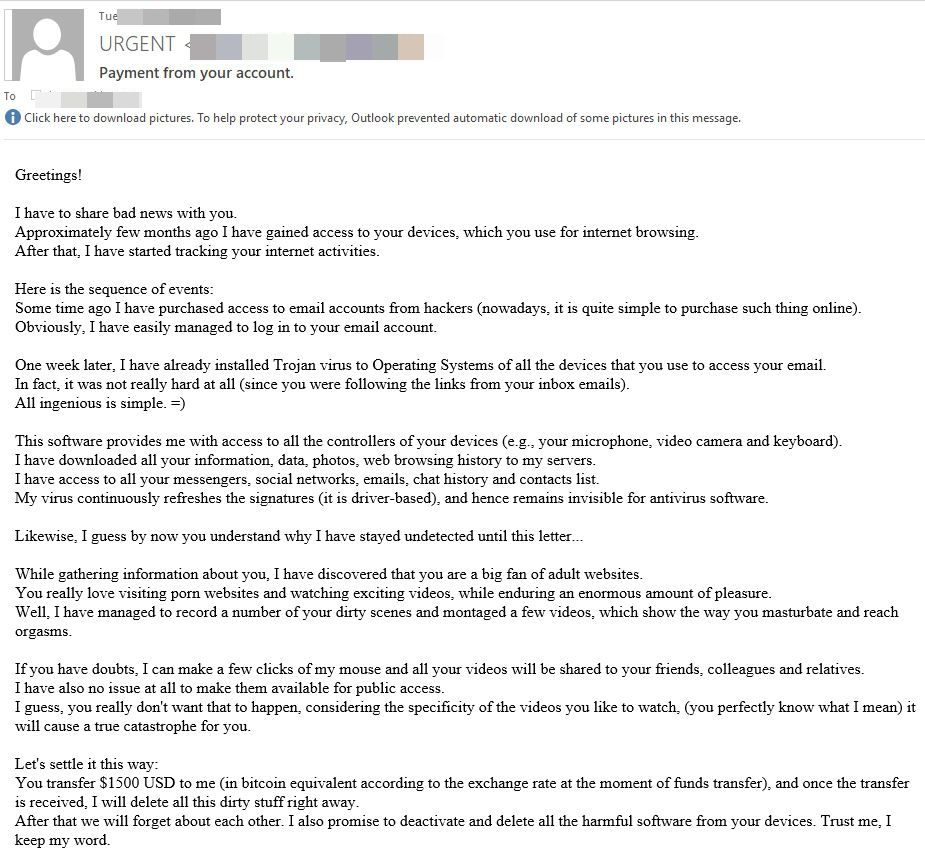
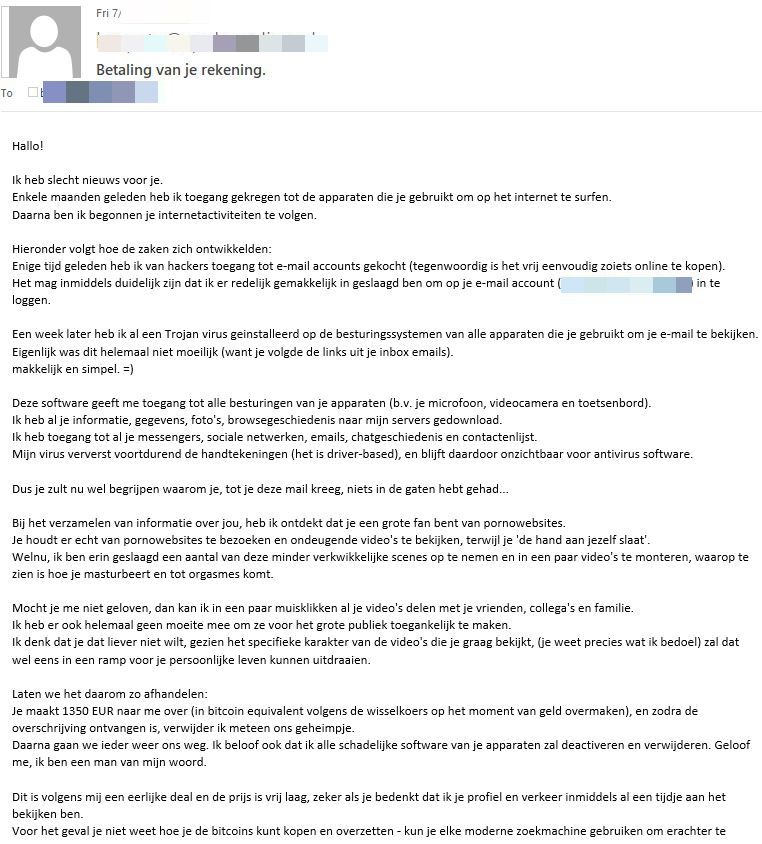
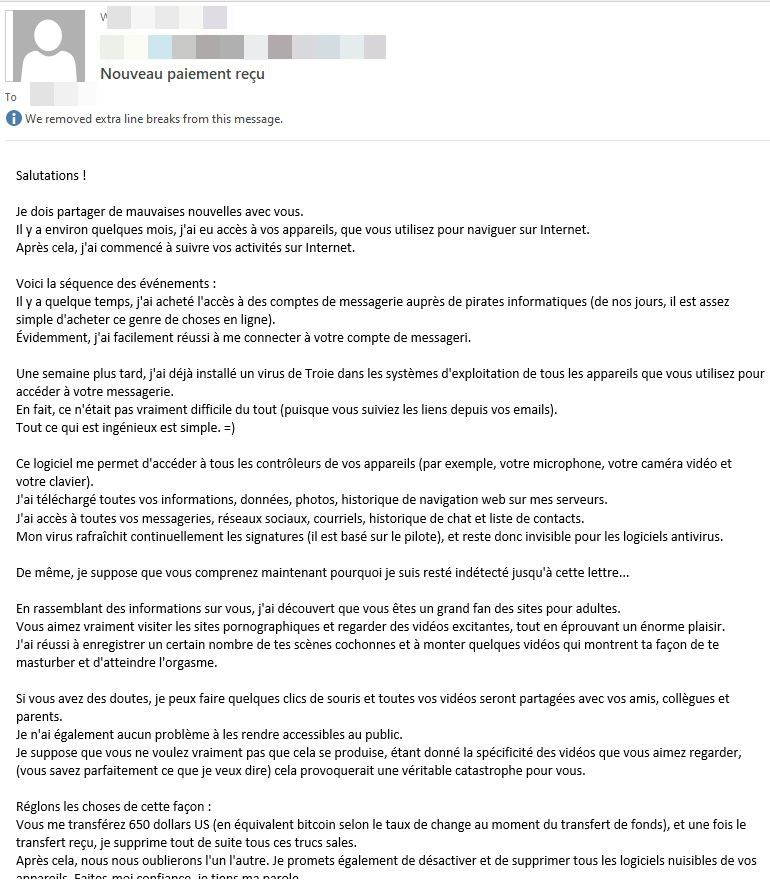
During the expose, scammers say that using a security solution is pointless. "My virus continuously refreshes the signatures (it is driver-based), and hence remains invisible for antivirus software," the scammer writes. "Likewise, I guess by now you understand why I have stayed undetected until this letter..."
Even if the email says they have access to your webcam, microphone and other software on your device, it's all a bluff.
The emails are language-specific and payment amounts differ, according to the recipients' location:
- Italy -950 EUR
- The Netherlands - 1350 EUR
- Brazil - 1600 BRL (approx. 309 USD)
- France - 650 USD
- Romania - 1250 USD
- United States - 1500 USD
Similar to previous extortion campaigns reported by our researchers, the perps outline a set of rules. The messages specify that "offers" are non-negotiable and require a 48-hour payment in cryptocurrency (Bitcoin). Users should not reply to the email and should never contact the police or security solution providers.
Every email ends with recommendations, courtesy of the scammer himself. "One more thing... Don't get caught in similar kind of situations anymore in future!" he adds. "My advice - keep changing all your passwords on a frequent basis!"
Extortionists strive to make it big
Analysis of the Bitcoin addresses shows that users continue to fall victim to extortion attempts despite numerous awareness campaigns and alerts reminding users about email-based threats.
Attackers used multiple bitcoin addresses to receive payment from victims, and some of them revealed several transactions from victims amounting to thousands of dollars. Tracking some of these fraudulent exchanges is a painstaking task. However, a Bitdefender researcher notes that the threat actors were sloppy when handling some of the transactions.
"Victims are making payments directly through exchanges into the scammers' addresses," he notes. "The scammers themselves don't seem to care much about BTC best practices, reusing a lot of these addresses when making transactions (both for transfers and for change outputs), funneling money through a relatively hierarchical setup which they own. The top addresses (where the crypto ends up) are usually "clean" in the sense that they do not appear in the extortion emails themselves. This is because most large exchanges will monitor lists of addresses that have been reported for abuse and will block transactions for them. These addresses are then used for conversion into real money through said exchanges and/or BTC mixing systems which will cause a complex transaction setup that can no longer be followed."
Data dumps on the dark web fuel spam and extortion campaigns
Data breaches and leaks happen daily, exposing email addresses and more sensitive information such as clear-text passwords, Social Security numbers and credit card details.
Stolen or scraped information gets dumped on the dark web where cybercriminals and fraudsters pay a trivial amount to browse through the data and use it to steal identities or phish victims to compromise online accounts and ruin finances.
However, cybercriminals can use even the smallest amount of leaked data to extort victims. The art of extortion was already an ancient practice long before the dawn of internet. However, it has morphed into a highly profitable business in the digital age for cybercriminals who can reach millions of individuals in just a couple of clicks without necessarily having compromising evidence on them.
A separate extortion attempt can be linked to the COMB data leak, the largest compilation of stolen credentials to date, posted for sale on an underground forum in February. The validity of the passwords mentioned in the correspondence have indeed appeared in the leaked data.
The subject line conveniently reads "Your Password: [redacted]". Here's a sample of the message:
"I know [redacted] is one of your password on day of hack..
Lets get directly to the point. Not one person has paid me to check about you. You do not know me and you're probably thinking why you are getting this email? in fact, i actually placed a malware on the adult vids (adult porn) website and you know what, you visited this site to experience fun (you know what i mean). When you were viewing videos, your browser started out operating as a RDP having a key logger which provided me with accessibility to your display and web cam. immediately after that, my malware obtained every one of your contacts from your Messenger, FB, as well as email account."
Long story short, recipients need to pay $1,364 USD to make the whole incident go away and, most importantly, keep their reputation in one piece.
Five practices to ward off email-based extortion attempts
Extortion scams can be made to appear credible when paired with your account password, technical details about how your system was compromised and other plausible arguments. The success of these scams is always a gamble, but individuals continue to respond to threats that involve exposing compromising details and videos of users visiting adult websites.
Emotional triggers that send you into a panic often explain why users give into the demands of scammers.
Here's what you can do:
- Stay calm and analyze the situation – even if the email includes your password, it was likely gathered from previous data breaches and leaks. If the scammer says your system is already infected with malicious software and spyware, why would he need you to personally transfer the ransom amount? He could easily harvest all of your account passwords and start draining your financial accounts?
- Review and update your account passwords regularly
- Never respond to threatening messages by asking the perps to provide you with a different payment method; report them to local authorities instead
- Install a local security solution on your devices
- Enable two-factor or multi-factor authentication
Bitdefender Digital Identity Protection is your dedicated online privacy service that helps you take control of your digital footprint to minimize the risks associated with data breaches and leaks. Our tool continuously monitors the web for any data related to the information provided in the onboarding process (email address and phone number).
You can analyze the exposed data to better understand your risks of falling victim to scammers and take more privacy-focused decisions for all your future digital endeavors.
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







