Bitdefender Threat Debrief | May 2025

From Locked In to Compromised: LockBit Exposure Fuels Hunt for Threat Intelligence
In this edition of the Bitdefender Threat Debrief, we cover several key ransomware developments, including a recent LockBit exposure, Qilin’s rise, and updates on DragonForce activities.
Ransomware is a moving target, and our goal with this monthly Bitdefender Threat Debrief is to help you stay ahead of the curve. To do this, we combine information from openly available sources (OSINT) - things like news reports and research – with data we gather by analyzing Data Leak Sites (DLSs), websites where ransomware groups post details about their victims. It’s important to remember that we can't independently verify all of these claims but are confident in the trends we see over time.
 For this month's report, we analyzed data from April 1 to April 30 and recorded a total of 542 claimed ransomware victims.
For this month's report, we analyzed data from April 1 to April 30 and recorded a total of 542 claimed ransomware victims.
Featured Story: LockBit Exposure
The LockBit Breach
LockBit is a Ransomware as a Service (RaaS) group that regularly navigates challenges, and most recently, it was a case of attackers being attacked.
On May 7, 2025, reports of a breach exposing LockBit’s operations spread throughout cybersecurity forums and social media platforms. The attacker breached a LockBit 4.0 onion site and posted the following message:
"Don't do crime CRIME IS BAD xoxo from Prague."
Those behind the breach also posted a link on the page that allows visitors to access a MySQL database dump of LockBit’s data.
How did the breach occur?
The threat actor that compromised LockBit exploited a flaw in the server that affects PHP 8.1.2. Once this flaw is exploited, a threat actor can perform remote code execution.
What was stolen and leaked?
The database dump contains data that spans the last five months, from December 2024 to April 2025. The data available provides details on LockBit’s affiliate program and tools, including individual builds and build configurations for attacks against ESXi and other systems. User values for 75 affiliate members and passwords, stored in plaintext, are also included in that data dump. Nearly 60,000 Bitcoin addresses were extracted. The threat actor also extracted thousands of chats from a chats table. The LockBit builder itself and the decryptor tool were not compromised or leaked, and several additional LockBit domains remain active and unaffected.
How is this data useful?
Threat researchers and security teams can leverage the leaked data to advance threat intelligence and attribution efforts. For example, security engineers and researchers can draw connections between affiliate groups by referencing a wider dataset on tooling components and affiliate contacts.
This data breach has also spurred the creation of LockBit GPT to enhance threat analysis and intelligence tasks that are essential to understand and combat LockBit’s operations.
You may already be familiar with BlackBasta GPT. Following Black Basta’s exposure in late February, that tool was used to automate the process of collecting and analyzing leaked data to simplify and examine developments in Black Basta operations. Hudson Rock, the security and intelligence firm behind BlackBasta GPT created the new LockBit GPT as well.
Who is responsible for the LockBit breach?
Could an affiliate or rival be behind the attack? While there are multiple scenarios that may explain why an individual or entity would attack LockBit’s infrastructure, there’s one explanation that has striking implications for LockBit and similar groups. Consider the message associated with the attack and the potential impact. The same message, "Don't do crime CRIME IS BAD xoxo from Prague," was observed in the Everest defacement in March of 2025. This indicates the breach may be part of a larger effort by another ransomware group to derail the competition and acquire greater resources, including affiliates and targets.
LockBit’s Recent Challenges
The most recent breach adds to the list of challenges LockBit has navigated over the years. In September 2022, LockBit 3.0 builder was leaked, lifting the barrier for other groups to operate as they’d develop encryptors using the builder. Then, in 2024, law enforcement hit LockBit’s operations with a seizure of their infrastructure. Staffing concerns and greater scrutiny of the group also emerged in the wake of charges against seven key LockBit personnel, including the developer Rostislav Panev, nearly a year later.
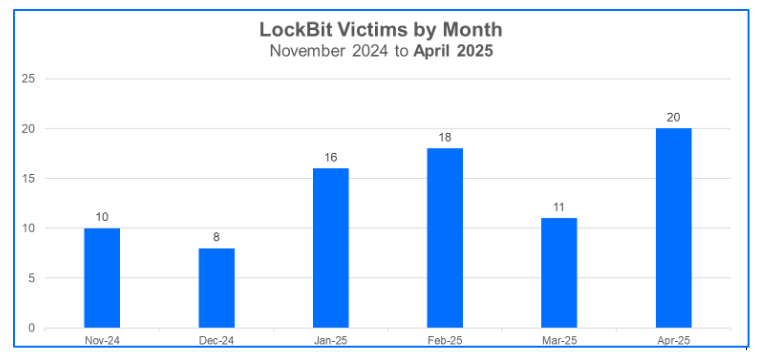
LockBit Victims
LockBit fell from our Top 10 Ransomware Groups in October of 2024 but remained active in the six months that followed, conducting attacks that leveraged lockbit and lockbit3 ransomware. However, the number of victims LockBit claimed each month in that time span declined significantly, and at this point, they have not regained a spot in the Top 10.
Ransomware and Security Awareness
Some ransomware groups operate for years and have a devastating impact across public and private sectors. Other groups may cease their operations, often as a result of law enforcement efforts, schisms within the group, or external factors like competition and limited resources.
Regardless of a ransomware group’s maturity, operational gaps, or shifting influence, it is important to understand ransomware threats and best practices that are essential to secure your organization’s assets. For a comprehensive analysis of the current ransomware playbook, including how these attacks are executed and how to defend against them, please read our updated Ransomware whitepaper.
Notable Ransomware News
Now, let’s explore other notable news and findings since our last Threat Debrief release.
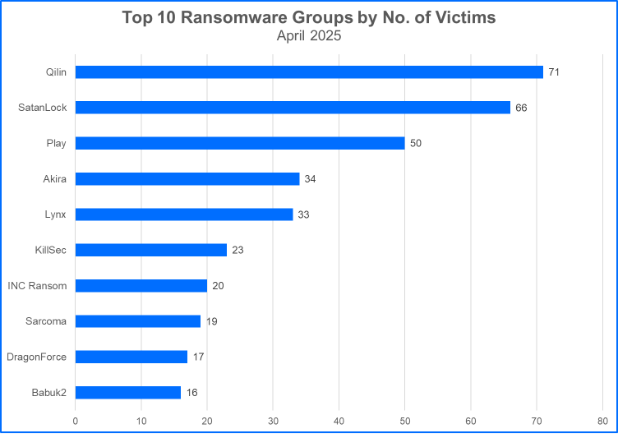
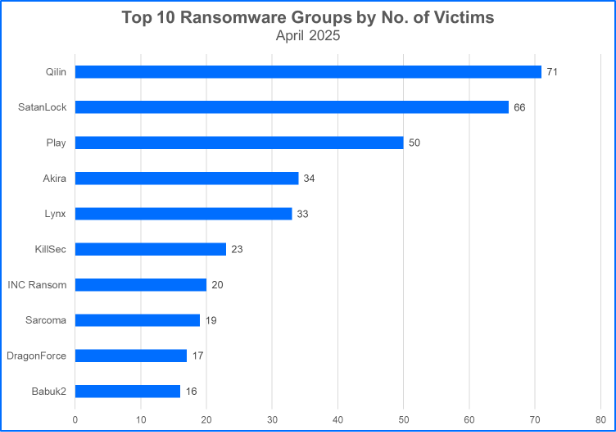
- Qilin Ranks as the Top Group in April: Qilin is making waves in the threat landscape, not only for their victim count but also their use of stealthy techniques and defense evasion tactics. The group and its affiliates used .NET loaders in recent campaigns to combat common antivirus detection methods by obfuscating the control flow of malicious code and using reflective injection to load malware in memory. Qilin claimed its largest number of victims yet in April with a total of 71 victims. This comes shortly after the group’s partnership with DragonForce. With RansomHub out of the way, the group may continue to secure higher ranks in the top 10.
- SatanLock Attacks are Close Behind Qilin: SatanLock ranked second in the top 10. The group is associated with Babuk2, a group that was also known by the alias Bjorka. Bjorka corresponded with the group named FunkSec earlier in the year, seeking out opportunities to become an affiliate. SatanLock’s connection to Babuk2 raises questions about the characteristics of their attacks and whether they’ll continue to leverage ransomware or use tactics that have become a hallmark of Babuk2’s behavior. These tactics include revictimization and data theft, resulting in extortion and/or auctioning on a closed marketplace.
- DragonForce Debuts a Different Ransomware Service Model: DragonForce announced that it now operates as a cartel. Rather than limiting services to the developer-level (by solely distributing ransomware and other malicious scripts), the group now offers infrastructure and admin panels for hackers and affiliates. In exchange, DragonForce receives 20% of profits. This announcement came nearly two weeks after RansomHub moved their infrastructure to DragonForce. DragonForce is not the only group that adopted a profit model that diverges from RasS. Anubis, a group that emerged in February, made a similar announcement.
- RansomHub Operates Under DragonForce: After claiming 70 victims in March, RansomHub’s infrastructure went offline. RansomHub used DragonForce’s infrastructure, which created a lot of confusion in the days to follow. The decision was initially considered a temporary move. However, DragonForce announced a partnership with RansomHub that sparked conflict among RansomHub members. RansomHub’s affiliates could not access RansomHub communications; and some affiliates expressed their bewilderment in the RAMP cybercrime community. Several weeks later, RansomHub remains inactive. It’s unclear whether their move to DragonForce was intentional and planned, or forced upon the group.
- RAlord Rebrands as Nova: Nova is a ransomware group with a data leak site, and name and shame blogs, that date back to March 2025. However, they are not a new or emerging group. Nova’s operations can be linked back to RAlord. According to the Nova data leak site (DLS), it’s the group’s second DLS since 2017. The group does not use CAPTCHAs to secure their DLS. Instead, Nova uses a CTA or Capture the Answer assessment. Multiple questions are displayed to site visitors about common ethical hacking subjects, scenarios around using tools, command issues, and XOR operations. Users who answer all questions correctly can access the DLS. Those who fail are redirected to a Script Kiddies Wiki page.
- BYOI Attack is Used to Bypass EDR: Bring Your Own Installer, or BYOI, is a technique used by threat actors as a workaround to bypass EDR and anti-tampering protections. It is similar to the Bring Your Own Vulnerable Driver (BYOVD) technique because it incorporates the use of legitimate components (a signed installer for the BYOI approach). According to a recent report, threat actors are using a BYOI attack that exploits a known flaw in a major EDR agent. This allows the threat actor to disable the EDR without immediate access to the EDR's anti-tampering code and enables the actor to deploy Babuk ransomware. This approach is often effective. In fact, in a recent AV-Comparatives Evaluation, one in three security solutions failed an Anti-Tampering Certification Test.
- ToyMaker Teams Up with Cactus, providing access to targets: Toymaker is a group that functions as an initial access broker (IAB). ToyMaker collaborated with the Cactus ransomware group, granting them access to systems after exploiting vulnerabilities or leveraging custom tools like LAGTOY malware. The LAGTOY malware can perform several actions, including stealing credentials, creating reverse shells and connecting to a C2 server to receive and execute commands. While ToyMaker is a financially motivated group, the percentage of profits they may receive from Cactus is not yet known.
Top 10 Ransomware Families
Bitdefender's Threat Debrief analyzes data from ransomware leak sites, where groups publicize their claimed number of compromised organizations. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and may be unreliable. Additionally, this method only captures the number of victims claimed, not the actual financial impact of these attacks.
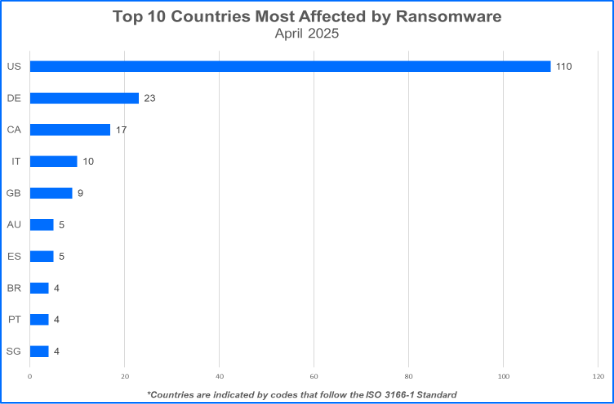
Top 10 Targeted Countries
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. Here are the top 10 countries that took the biggest hit from these attacks during April 2025.
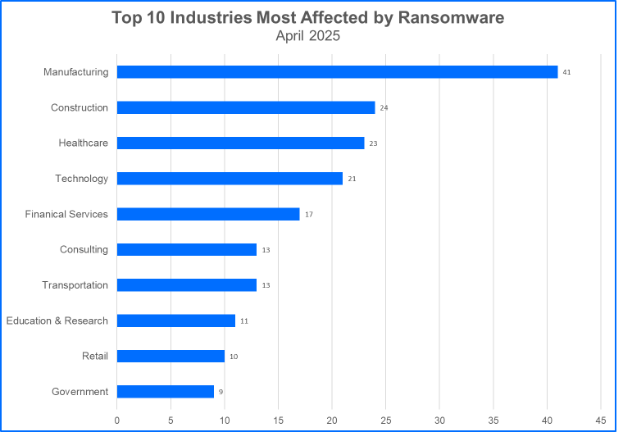
Top 10 Most Targeted Industries
Ransomware gangs may target organizations in the critical infrastructure ecosystem, select other organizations that offer services tailored to the consumer marketplace, or attack both. Here are the Top 10 industries ransomware groups attacked during April.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing ransomware-related threat news, trends, and research from the previous month. Don’t miss the next BDTD update, subscribe to the Business Insights blog, and follow us on X. You can find last month's debrief here.
About Bitdefender
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. Bitdefender Labs discovers 400+ new threats each minute and validates 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Gabriel Macovei, Andrei Mogage, and Rares Radu for their help with this report.
tags
Author
Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsYou might also like
Bookmarks

