What are Data Breaches? And What to Do if Your Personal Info is Leaked Online

Whether you are aware of it or not, it is very likely your personal information is already on the Internet after it was involved in a data breach. Moreover, malicious actors may be trying to profile you based on your digital footprint – so now is the right time to gain back control.
Do not let others decide what happens to your private data. Bitdefender cybersecurity experts discuss the right tools and tactics to monitor and manage your personal information, even after a major data breach.
What Is a (Data) Breach of Personal Information?
The definition of a data breach refers to the security violation that involves releasing secure or private/confidential information into an untrusted environment (such as the public Internet or the Dark Web) where unauthorized individuals can access it (download, copy, view, or otherwise transmit it).
The type of sensitive information usually involved in data breaches falls into three categories:
- financial data – credit card or bank details, loan, pension, and insurance information
- personally identifiable information (PII) – Social Security numbers, mail addresses, phone numbers, Driver’s License information, email addresses - but also IP addresses, login IDs, social media posts, digital images, geolocation data, behavioral data
- personal health information (PHI) – medical history, prescriptions, biometric data (including your fingerprints and full photographic images of your face), test results, billing information from medical facilities
- intellectual property – research (commercial, medical, scientific, etc.), trade secrets, patents, trademarked assets
No matter what you call it (data leak, data spill, information leakage), or who is responsible for it, the consequences of a data breach are the same.
“When it comes to data breaches, the regular user really doesn’t have a say.
We can take all the necessary precautions to make sure that we’re not actively leaking information – install security solutions and adhere to best practices. But when a company gets breached, it’s not because of us. It’s because of their oversight in security or because the technology on their end is so complex that it’s barely manageable.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
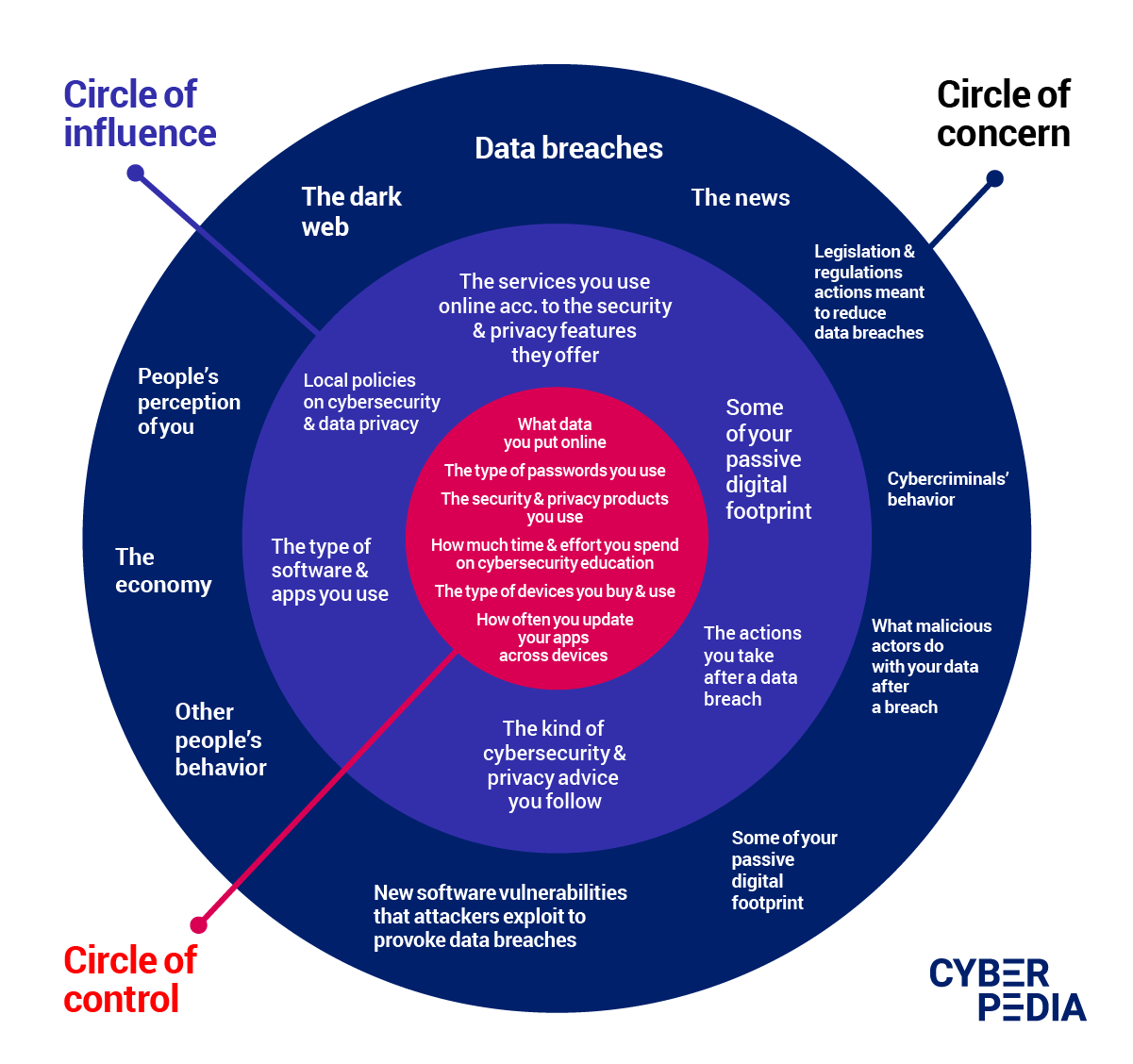
When trying to protect your online privacy , you need to put your resources to good use and find out what you can and cannot control.
The more you focus on controlling and securing your data, through the methods highlighted in the "Circle of control", the stronger your ability to manage your digital footprint becomes - even if your personal information is leaked in a data breach.
Types of Data Breaches
Data breaches come in two types:
- intentional – caused by malicious actors such as cybercriminals, state actors, malicious insiders, hacktivists
- unintentional – provoked by mistake, often human error, such as leaving the option of public access to a database with customer information that should be private.
When referring to deliberate data leaks, black hat hacking (cyber-crime) is often involved in a wide range of activities that violate computer security and legal provisions.
Let’s take a closer look.
What all data leaks have in common is that they expose information to untrusted, unauthorized individuals and entities. What makes them different is how they happen.
Premeditated data breaches involve illicit actions such as:
- illegally breaking into computer systems
- harvesting data from various systems and/or people
- corroborating that data to identify the most valuable sets of information
- monetizing it through other criminal activities, including extortion, selling it on the Dark Web, and using it for subsequent, more targeted attacks
Accidental data spills are often caused by simple mistakes but can be just as damaging. Real-world scenarios include setting a private file to “public” by mistake, misconfiguring cloud storage buckets, forgetting to password-protect a database, and losing devices (computers, smartphones, USB drives).
Sometimes, cybersecurity researchers (white hat hackers) come across unintentional data breaches, alerting organizations through a process called responsible disclosure. However, most often online criminals (who also come across these accidental information leaks) take full advantage of this data and the potential financial benefits involved.
What Are the Common Causes of Data Breaches?
Attackers will hunt for vulnerabilities and use any available means to gain access to valuable, confidential information about organizations, governments, and individuals. That is because their business model is centered on making a quick profit by using the data itself of by selling it to other parties.
One of the tactics they use is leveraging weak, commonly used passwords to break into computer systems both in terms of software (applications) and hardware (devices).
“Data breaches generate a lot of information about us, that’s for sure.
Some of the information includes usernames and passwords that have leaked out and that cybercriminals can crack in an instant because they have so much computing power.
With those credentials, they attempt to log into different other services, including social networks, for instance. If you reuse those leaked passwords, they will sooner or later match an identity on social networks that accepts those credentials, and then malicious hackers have your account.
From there on, they’re just clicks away from conning other people into installing malware, donating money, or even going through private conversations or sending pictures.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Another thing black hat hackers often do is exploit vulnerabilities in widely used applications or devices. The bigger an organization is, the more probable it is they have a complex infrastructure that is always evolving. All malicious actors have to do is find a single security weakness to gain access, while defenders must manage and cover all possibilities.
Malware is another common cause of data breaches. Cyber-criminals constantly craft, buy or even rent malicious software designed to infiltrate computer systems and harvest data. They routinely deliver it through infected emails, links, websites, and even online ads. The malware goes on to search for passwords, sensitive files and even to log keyboard strokes, sending back all this information to servers controlled by the attackers.
Social engineering, which includes various types of psychological manipulation, is also part of the mix in most data spills. Fraudsters, scammers, and criminals engage employees who have access to sensitive information and try to persuade them to provide access, help them bypass security measures or simply hand over the information under a believable pretense.
Sometimes competitors even try to bribe company employees to do their dirty work for them. This is the case of malicious insiders who fall for the promise of financial gain by abusing their access to organizational secrets.
Human error and unauthorized use of data (without malicious intent) are also among the most common reasons for information leakage.
How Data Breaches Affect You
You may think that data breaches cannot impact you on a personal level. However, that is exactly what cyber-criminals want you to believe. As Bitdefender cybersecurity specialists will tell you, the data correlations that take place on the Dark Web, where only security researchers have access, often go beyond your wildest assumptions.
“All of those data breaches that happen to companies whose services you’ve used in the past (or are still using) can be used by attackers to paint a very clear picture of you, even if those data breaches are unrelated and come from different service providers.”
Liviu Arsene (Senior E-threat Analyst, Bitdefender)
With data breaches fueling the underground economy where cyber-criminals sell, trade, monetize and weaponize information, the personal risk for each of us is very real.
Your personal information was most likely already involved in a data breach. This can weaken your online privacy and exposes you to risks such as digital identity theft and social media impersonation.
“Data breaches have a cascading effect. They often start with email addresses and usernames or passwords but, if not plugged in a very, very short timeframe, they can cascade into having more accounts compromised than we bargained for. “
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Most cyber-attacks use the “spray & pray” technique which consists in hackers spreading their malware across as many targets as possible, hoping that a high percentage of them will install it. If that is the case, you can become a victim even if they did not specifically target you.
If you work at an organization they are interested in, you can also be a stepping stone in their plan, an innocent bystander who gets involved in a cyber-criminal offense without their knowledge.
Data breaches also have long-term effects that weaken the security of our entire ecosystem, going beyond the tech layer that is now so deeply embedded into our lives. With information harvested from data spills, malicious actors can attack critical infrastructure that keeps our water and our electrical grid safe. They can encrypt data and hold it for ransom and block the activity of crucial institutions such as hospitals or the mayor’s office.
Just because they happen often and they are outside your circle of control, it does not mean you should ignore the consequences of data breaches. It is one more reason to boost your cyber savviness level and act smart to monitor your most sensitive data.
Who Stands to Gain from Data Breaches?
In our current connected economy, data is the most valuable currency for most organizations around the world.
The volumes of data we produce are not just enabled by technology, but also closely monitored by it in a way that has never happened before. Because of its abstract nature, it is challenging to see just how much of your digital footprint is monetized through anything from ads to ransomware attacks.
All the data that overflows from closed systems into the public domain or the Dark Web finds its way into the underground economy, where it becomes fuel for more attacks that cause more data breaches.
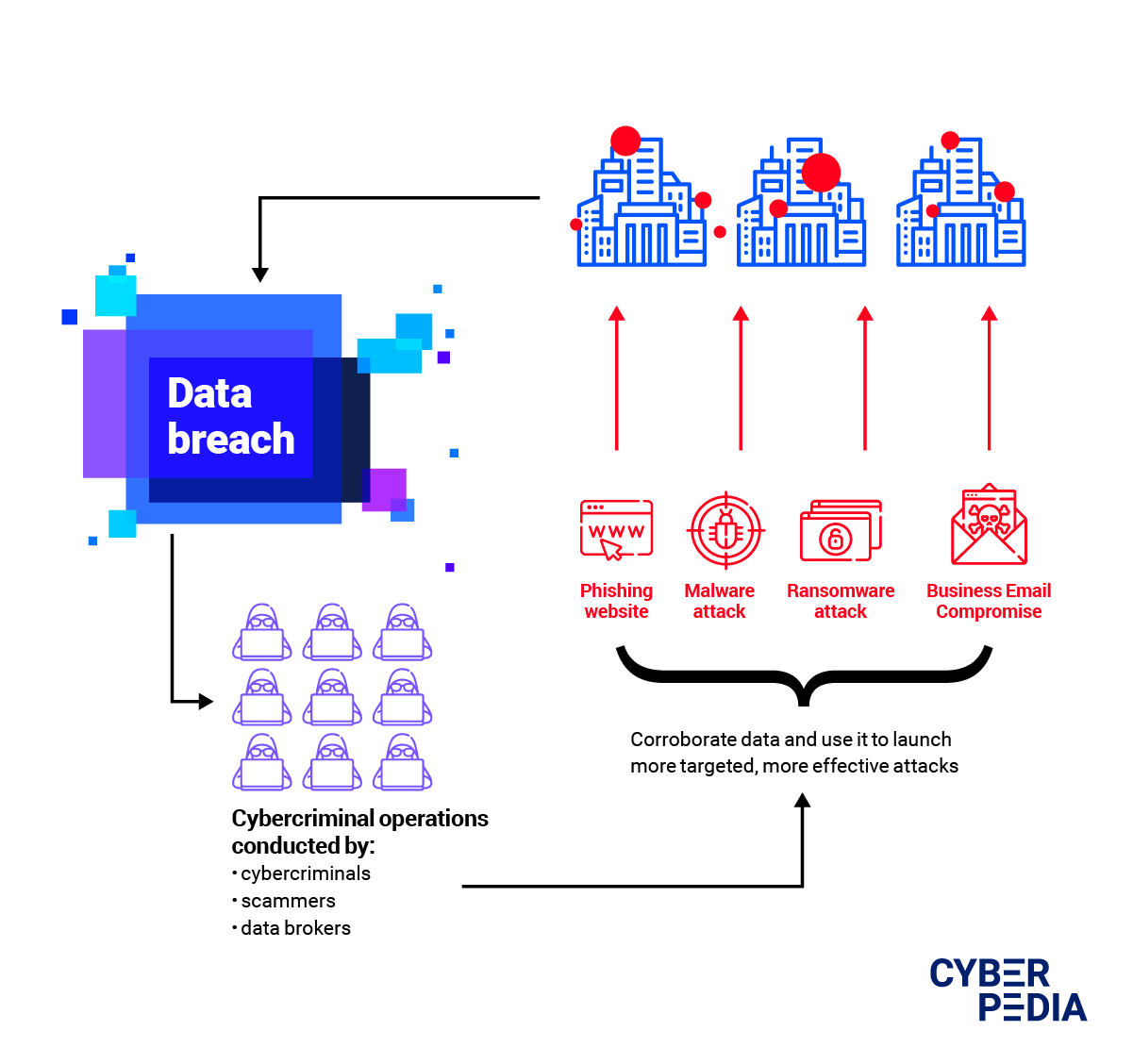
Cyber-criminal organizations, scammers, and data brokers are the malicious actors who make the biggest gains by causing data breaches and using their consequences to their advantage.
They hold data for ransom (ransomware attacks), blackmail companies by threatening to expose their security weaknesses (extortion) and corroborate the data from information leaks to craft highly targeted attacks such as Business Email Compromise scams. They also actively sell data from breaches on Dark Web forums.
How Much Should You Worry about Data Breaches?
Although regulations such as the GDPR have made it mandatory for organizations to report data breaches, most of the incidents still do not make it into the public sphere or the news.
The even bigger problem is that even more of these data spills go undetected or unreported – or both – for months. Some even for years! If the company does not know what is happening, most likely neither do you.
We have reached a point in our digital lives where we need to take charge and put some safeguards in place for our most sensitive data.
What Happens to Private Data Exposed in a Breach?
Depending on the type of leaked information, your home address, passwords, credit card details, medical history, and even confidential items from work can fall into the hands of hackers.
Once they have this data, it is impossible for you to retrieve it, delete it, or otherwise eliminate it from the Internet. It goes on to live on their servers, computers, backups, on Dark Web forums and even in public data repositories accessible through search engines. Your personal information spreads and travels across systems you have no control over - and probably do not even realize exist.
How to Find out if Someone is Using Your Data Leaked from a Breach
“There are two ways people usually find out their information is exposed online.
Either they read the news and find that a service provider or a company they work with or whose services they use has been breached and there’s a chance that some of their personal information has been leaked online. Or, if it doesn’t make the news, they sometimes get an email from the breached company notifying them that ‘Hey, there’s been a breach. Your personal information may have been affected.’”
Liviu Arsene (Senior E-threat Analyst, Bitdefender)
However, this is the “too little, too late” scenario and it does not help you much. While breached organizations struggle to identify the information leak and confer with lawyers and their team to communicate the compromise, cyber-criminals are already working to turn that data into $$$.
Fortunately, now there is a way you can have your own early-warning system that alerts you when an unauthorized individual is using your email address, credit card or Social Security Number for malicious purposes.
Bitdefender Digital Identity Protection monitors your most sensitive data starting with just an email address and phone number. It automatically finds your private information in online legal and illegal collections of data and even checks if your personal details have been exposed on the Dark Web. Plus, you get instant alerts for new breaches and privacy threats (including social media impersonation) so you can act quickly to limit their impact.
Once you set up the service, you will find out how far your digital footprint extends. It also gives you actionable tips to help you clean up your essential accounts and improve your security settings.
How to Protect Yourself Against Data Breaches
We have no control over how information leaks happen. However, we can do a bit of clean-up and maintenance in our digital lives to at least minimize the amount of data we put out there.
The same rules that protect your privacy are also the most effective to help you curb the impact of a data breach on both your online and offline life:
- Gradually move your passwords to a password manager – you will only have to remember a single password and this will save you from setting weak passwords and reusing them
- Turn on two-factor authentication for those important accounts and set passwords for your essential devices
- Remove all unnecessary applications from your devices (especially add-ons in your browser!)
- Delete any online accounts you do not use anymore (if they are from an EU-based or California-based provider, you can also ask them to delete your data entirely)
- Disallow access of third-party apps to your main accounts and apps (e.g. your fitness tracker may plug data into the health app on your smartphone)
- Back up all your important assets on an external hard drive or in the cloud (encrypted) or, ideally, both
- Update all your software applications across your devices
- Secure your web browser by strengthening your security and privacy settings
- Install a security solution and explore its features to make sure you get the most out of it
- Use a virtual private network (VPN), especially when you use wi-fi networks that are not yours or when using websites where you need extra safety (think medical and financial ones)
- Pay attention that all the websites you use employ HTTPS to secure your connection and the data you submit to them
- Share files online securely through reputed services and avoid sending personal data via instant messaging platforms (IDs, documents, bank details, and especially passwords!)
- Use secure online communication platforms that use encryption and don’t share your data with third parties
- Set up Bitdefender Digital Identity Protection and have it monitor your most valuable digital information for you, 24/7, 365 days/year, even in places on the Internet you do not normally have access to.
What Are Organizations Doing to Prevent Data Breaches?
Either through their own will or determined by legislation and regulations, private and public companies alike are strengthening their defenses against cyber-attacks and scammers.
But the challenge of securing data in motion remains an incredibly complex task. Cybersecurity and tech experts everywhere are just a small part of the infosec community working hard to develop stronger internal processes and embed security solutions that also have proactive protection capabilities.
“Even if cybersecurity has many blankets to prevent us from shooting ourselves in the foot, we shouldn’t only rely on technology. We should also start sticking to the best practices to help us minimize the amount of data we generate on the web.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Companies still have a long way to go, and change must come from within. From ensuring that software and hardware are shipped with fewer errors and no fundamental security vulnerabilities, to training employees to recognize and handle attacks that prey on their trusting nature, a lot is going on.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts

