How to Map, Monitor and Manage Your Digital Footprint

Out of sight, out of mind. That is the main aspect of your digital footprint that cyber-criminals and scammers exploit.
They know what your digital footprint is and how to manipulate it in their favor. This leaves most people unaware of how their personal details travel across the internet, making money for malicious actors.
But it does not have to be that way. With a few hours to spare, you can make it almost impossible for them to take advantage of your digital footprint.
Ready to give hackers the cold shoulder? Let’s get you set up!
Is Your Digital Footprint Permanent?
Pretty much. And that is because information permanence manifests in often unexpected ways.
Your digital footprint is made up of all the different bits and pieces of information the digital world has on you. But this is not limited to what websites, online services, platforms, apps and other entities store on their servers right now. It also comprises data from backups, other people’s devices, your old devices, and all kinds of formats (old CDs and memory sticks, for example).
While some say the Internet has a short-lived memory, many examples attest to the contrary.
Even when you delete one of your accounts, sometimes you have to specifically ask for your data to be fully removed from the company’s records. And then trust they will do it and be thorough about it. For instance, a social network permanently removes your posts and activity 30 days after deleting your account (on average). But if you want to purge your browser history, you will have to do it manually.
Laws are especially important to regulate how much information companies can collect on you and for how long they can store it. Case in point, in the EU, GDPR states that companies should not store browser cookies for longer than 12 months.
“One of the tricky things about digital information is that it can be replicated and stored without our consent, even when we are actively trying to combat that.
We have no guarantees a company will delete that information from backups dating years or that they will not restore it in case of catastrophic failure.
So if we want to control some information about ourselves, the best thing is not to hand it over in the first place. Once we post it or fill in a form with those details, there is no way for us to revoke it.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
It is realistic to understand that your digital footprint is permanent but, at the same time, that you can really do something to protect it.
How to Deal with People Without a Digital Footprint
When you get an unexpected message on social media from someone you share no connections with, you should see it as a red flag. Scams often involve fake accounts, bot accounts and impersonators with no digital footprints. It is one of the first things you need to do when checking if a connection request or proposal is legitimate or not.
At the same time, there are increasingly more people who decide to strengthen their privacy by deleting their social media accounts, for instance.
If you simply cannot decide if a person is acting suspicious or simply being very careful about their privacy, see if you can validate their claims from multiple sources. Look for digital fingerprints such as online comments or other activities that show that their online profile was not created recently. If you are still unsure, just ignore the request. They will come back if the subject was important or try to use a different channel to contact you.
How to Manage Your Digital Footprint
Privacy is a trade-off many people make because they want the convenience and functionality of products and services that are easy to use. Unfortunately, that is also the riskiest road from a security standpoint.
Whenever you contribute to your active digital footprint, provide the least amount of information possible. This general rule will help you minimize the damage in case of a data breach that leaks your personal information.
“It helps to understand what you can and cannot control.
You can take control of the things you post online: the information you willingly share online or with application service providers. But once you send that information to a third party, you cannot control what happens to it from that point on.”
Liviu Arsene (Senior E-threat Analyst, Bitdefender)
How to Map Your Digital Footprint
With your sensitive information already out there, here’s what you can do to get a clearer picture of your digital footprint:
- Search for your name (and your phone number) and scrutinize what you find. Run a search every few months to see what type of information others can access about you.
- Set up alerts to find out when your name pops up across the web.
- Make a list of accounts and delete the ones you do not use anymore. Use this opportunity to see which are worth prioritizing for a clean-up and security boost.
- Review your main online accounts and make it difficult for malicious actors to compromise them. Change your password with a stronger one, set up a connected back-up email and turn on multi-factor authentication.
- Check if your email address is leaked in a data breach with Bitdefender Digital Identity Protection and immediately change the password to that account and others where you used the same password.
- Unsubscribe from emails you never open and that keep piling up in your inbox.
- Delete spam emails and empty your spam folder without opening the emails.
- Clean up your social media accounts by deleting some photos, videos and posts and/or asking to be untagged in them. You can also consider removing location data from your posts where possible.
- Use Bitdefender Home Scanner to find out if you have any vulnerable devices and passwords and get detailed security recommendations for your home network.
With this map of your most exposed assets, you are ready to set a baseline in terms of privacy and security. And then develop habits that help you avoid unnecessarily expanding your digital footprint.
How to Prevent Leaving Digital Footprints
Depending on the level of caution you want to exercise going forward, there are many things you can do. Here’s a list of the most effective ways to reduce your digital footprint:
- Turn off location settings on your phone and only use them when necessary.
- Avoid using your real name when creating online accounts unless you absolutely have to.
- Have different email addresses for work and for personal accounts. This makes it easier to manage them and helps you avoid security and even social mishaps.
- Ramp up your privacy settings on social media to limit the number of people who can read your content.
- Avoid oversharing on social media. Refrain from posting pictures and videos of your home and belongings. Do not broadcast your whereabouts. This also applies to similar information about your parents, siblings, friends or other people you care about.
- Uninstall the apps on your phone you do not need and keep your digital setup minimal. A side benefit is that you are less likely to be distracted as you go about your day.
- Delete old emails, messages, and accounts you no longer need. Do this regularly to unclutter your devices and digital life and make it easier to spot spam or phishing emails.
- Make sure you have a security solution on your device that also protects your browser.
- Use a secure VPN to protect your IP and internet traffic from malicious onlookers. This is fundamental when connecting to Wi-Fi networks.
- Do not create unnecessary loyalty cards with merchants you do not have a longstanding relationship with. You are less likely to use them and you will most likely get tons of emails.
A little caution goes a long way in terms of your privacy and security on the Internet. Consider every bit of information you put on the web as permanent and you might think twice before hitting “send.”
How to Protect Your Digital Footprint
If you are wondering how to curate your digital persona to avoid using the data that is already public, try incorporating the recommendations below into your routine:
- Use a separate email address for your main accounts and do not use it to sign up for other products and services to minimize exposure.
- Have a secondary email you can use to access your main accounts in case you need to. You can also set trusted contacts to help you regain access in case of a takeover.
- Use disposable virtual cards for online payments to avoid revealing your main card details.
- Never share your passwords with anyone, especially in chats. Use a password manager to avoid (re)using weak credentials that cyber-criminals can crack in seconds.
- Read the terms and conditions when joining a new service. Legal terms are not fun but this helps you form an opinion of how digital footprint expands with each sign-up.
- Cover the camera on your device with a piece of black tape or a dedicated cover. Alternatively, you can use a Bitdefender security solution with built-in alerts that warn you if an external party is using your camera and microphone without permission.
- Use encrypted messaging apps for your communications.
- Choose a privacy-focused browser with built-in ad blockers. Do the same for your search engine.
- Avoid hosting and sharing sensitive documents on channels such as messaging apps or free, unencrypted cloud storage platforms.
- Turn off Internet-connected devices whenever you are not using them. Pay special attention to home assistants.
- Use your legal “Right to be forgotten” under the EU General Data Protection Regulation (GDPR) and other laws to ask for your data to be completely wiped out from specific providers.
- Start using a monitoring tool for digital identity protection to get instant notifications when your email address, phone number or credit card details get leaked in data breaches.
How to Prevent Your Digital Footprint from Getting on the Dark Web
Sometimes malicious actors are successful in harvesting your data and selling it for a good price on the Dark Web. If this is happening, you should be informed and act on it – fast.
When big companies get breached, it takes them a few months to assess the damage and then let you know your data was affected. With a tool like Bitdefender Digital Identity Protection, you get an instant alert when your data gets leaked or fake online profiles use your identity. It helps you keep track of your digital footprint and monitors several email addresses, credit card, social security number and accounts.
Based on these alerts, you can limit the damage by changing your password, calling the bank to freeze your card or reporting impersonators.
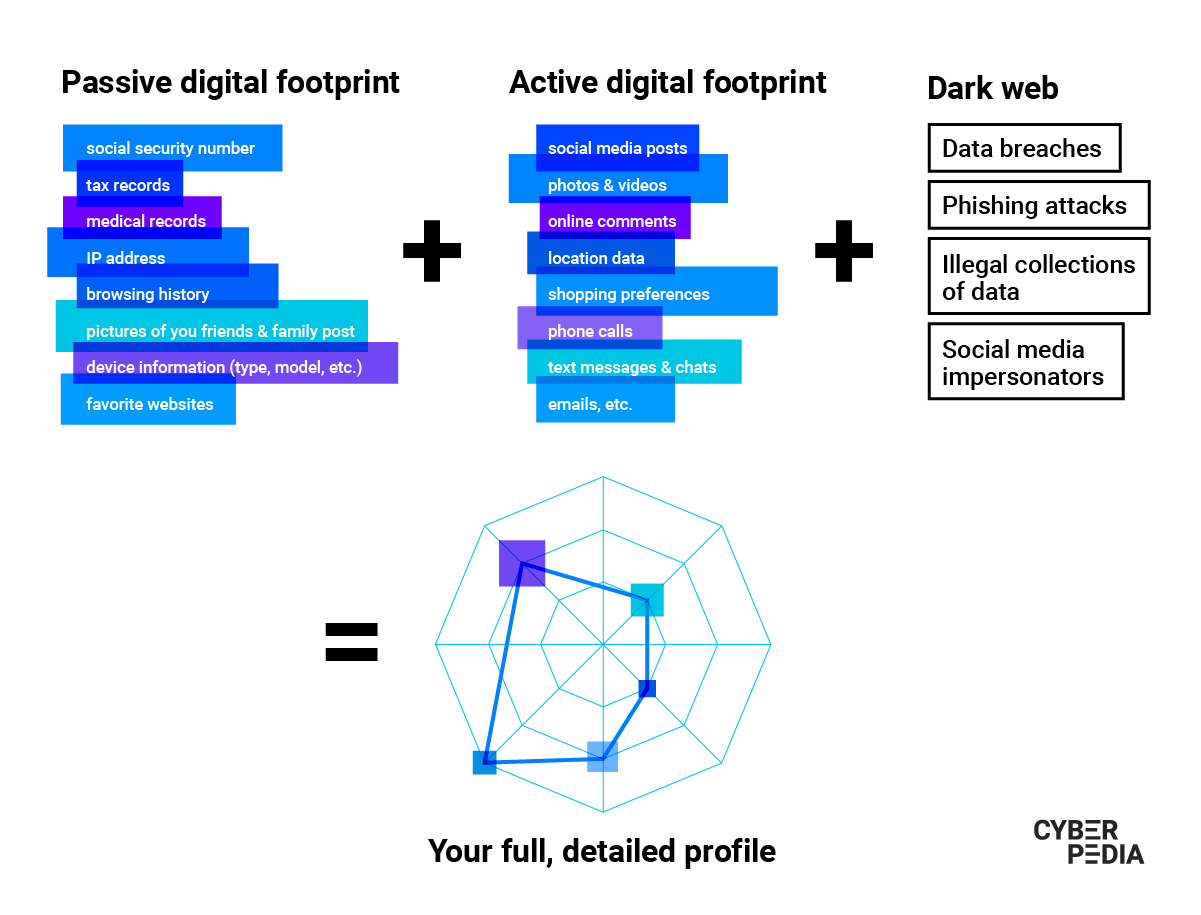
How to Delete Your Digital Footprint
If you want to leave the web entirely, it is going to be a complicated undertaking. You can delete some of your digital footprint (e.g. social media accounts) but there are parts of it you can never erase (e.g. government records).
But your ever-growing digital shadow does not have to be that distressing. Constantly purging your accounts, emails, messages, and other types of digital information gives you more control and makes for a more manageable online presence.
Remember that malicious hackers will use old information they find online about you, piecing it together with your active digital footprint to find a vulnerability. That is why sometimes you may want to completely purge an online account before deleting it, to prevent the company from storing copies of your data.
The best way to delete your digital footprint is to clean it up, one account and device at a time.
“One of the most important tools is the person themselves.
Even if cybersecurity has many blankets to prevent us from shooting ourselves in the foot, we should not only rely on technology. We should also start sticking to the best practices to help us minimize the digital footprint we generate around us.”
Bogdan Botezatu (Director of Threat Research and Reporting, Bitdefender)
Think of your online privacy as a virtual currency: keep it safe, spend it wisely and always ask yourself if you are getting your money’s worth.
tags
Author
Choose what the experts use. Award-winning cybersecurity you can trust and rely on.
View all posts

