Dnsmasq vulnerability puts home routers and IoT devices at risk

Vulnerability researchers at Google have uncovered exploitable software flaws in code running on internet-connected devices that could allow a malicious hacker to run remotely any code of their choosing.
The Dnsmasq network services software, popular because of its easy configuratiuon and low impact on resources, is commonly pre-installed on a wide variety of systems, including Linux distributions, home routers and IoT devices.
In a blog post published on Monday, Google researchers explained how it had discovered “seven distinct issues” in Dnsmasq while conducting a regular internal security review.
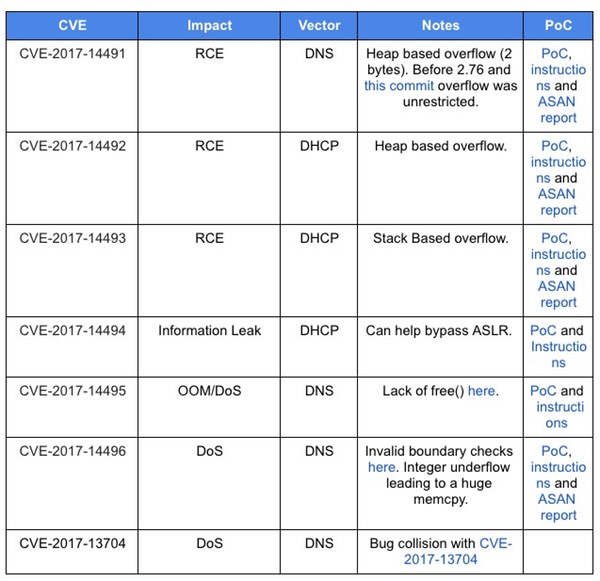
One of the flaws is described as a “trivial-to-exploit” DHCP-based buffer overflow vulnerability, that can be combined with another information-leaking exploit to bypass protection systems and gain remote code execution.
In short, an attacker could exploit the flaws to execute malicious code on a vulnerable device and hijack it for their own purposes. As we’ve seen many times in the past, malicious hackers find it all too easy to seize control of poorly-secured IoT devices to assist them in their criminal activities such as distributed denial-of-service (DDoS) attacks.
In this particular instance, an attacker may have to be a little more creative than normal to exploit vulnerable devices – but you still don’t want at-risk devices on your network do you?
A search on Shodan reveals that there are approximately 1.1 million internet-facing devices currently running Dnsmasq services.
Google’s research team says that after it recognised the severity of the issue, it worked with the maintainer of Dnsmasq to produce fixes, which have since been released as version 2.78. Furthermore, patches have been included in the Android monthly security update for October.
My concern is that some manufacturers are selling IoT devices and routers at a very low price, making tiny margins. As a result, some will feel little incentive to develop and push out a patch to their userbase – if indeed any updating infrastructure is available at all.
As always, be sure to pester your firmware manufacturers for updates, or consider voting with your wallet – boycotting those vendors who are failing to keep your IoT devices patched against the latest vulnerabilities.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








