Pegasus Spyware Found Using Novel Exploits in Latest Attacks on Civilians

NSO Group’s Pegasus spyware is making headlines again after researchers found new evidence that the Israeli cyberweapon was used in targeted attacks in 2022.
Just days after blowing the lid off a lesser-known spyware operation, researchers at Citizen Lab have released details about new spyware infections allegedly leveraging NSO Group’s infamous Pegasus unfolding in 2022.
The Toronto-based watchdogs, notorious for their piercing analysis of mercenary spyware over the years, say NSO Group was at it again in 2022, selling an updated Pegasus spyware equipped with novel hacking techniques that exploited vulnerable versions of Apple’s mobile operating system, including iOS 15 and iOS 16.
Two-phase, zero-click exploits
An exploit dubbed by the researchers PWNYOURHOME uses two attack surfaces to compromise the device, without requiring interaction from the victim (zero-click). The first step targets Apple’s HomeKit framework, and the second targets the iPhone’s SMS stock app, iMessage.
FINDMYPWN, a nearly identical attack avenue, uses the iPhone’s Find My feature – it too coupled with an iMessage side-component for deploying the actual spyware payload, the analysis reveals.
A third exploit, dubbed LATENTIMAGE, leverages a different exploit chain, and was allegedly used to deploy Pegasus to at least one victim’s iPhone.
With the help of human rights defenders in Mexico, the researchers gained forensic visibility into new NSO Group exploit activity. The finding followed the discovery of infections among members of Mexico’s civil society, including two human rights defenders from Centro PRODH, which represents victims of military abuses in Mexico.
The lab’s investigation led it to conclude that, “in 2022, NSO Group customers widely deployed at least three iOS 15 and iOS 16 zero-click exploit chains against civil society targets around the world.”
While keeping its investigation under lock and key last year, the team at Citizen Lab kept Apple on speed dial as it helped patch vulnerable iOS versions. One such endeavor was the eventual release of iOS 16.3.1 in February of this year, which included bug fixes that stifle the PWNYOURHOME exploit.
Lockdown Mode works
In its crusade against spyware, Apple not only sued NSO Group over its practices, but also went to develop a Lockdown Mode to reduce the attack surface on iOS, albeit at the cost of some functionality.
Citizen Lab says it found evidence that Lockdown Modeworks as intended. An illustration derived from victim screenshots (available below) shows notifications related to the PWNYOURHOME exploit in attempted attacks.
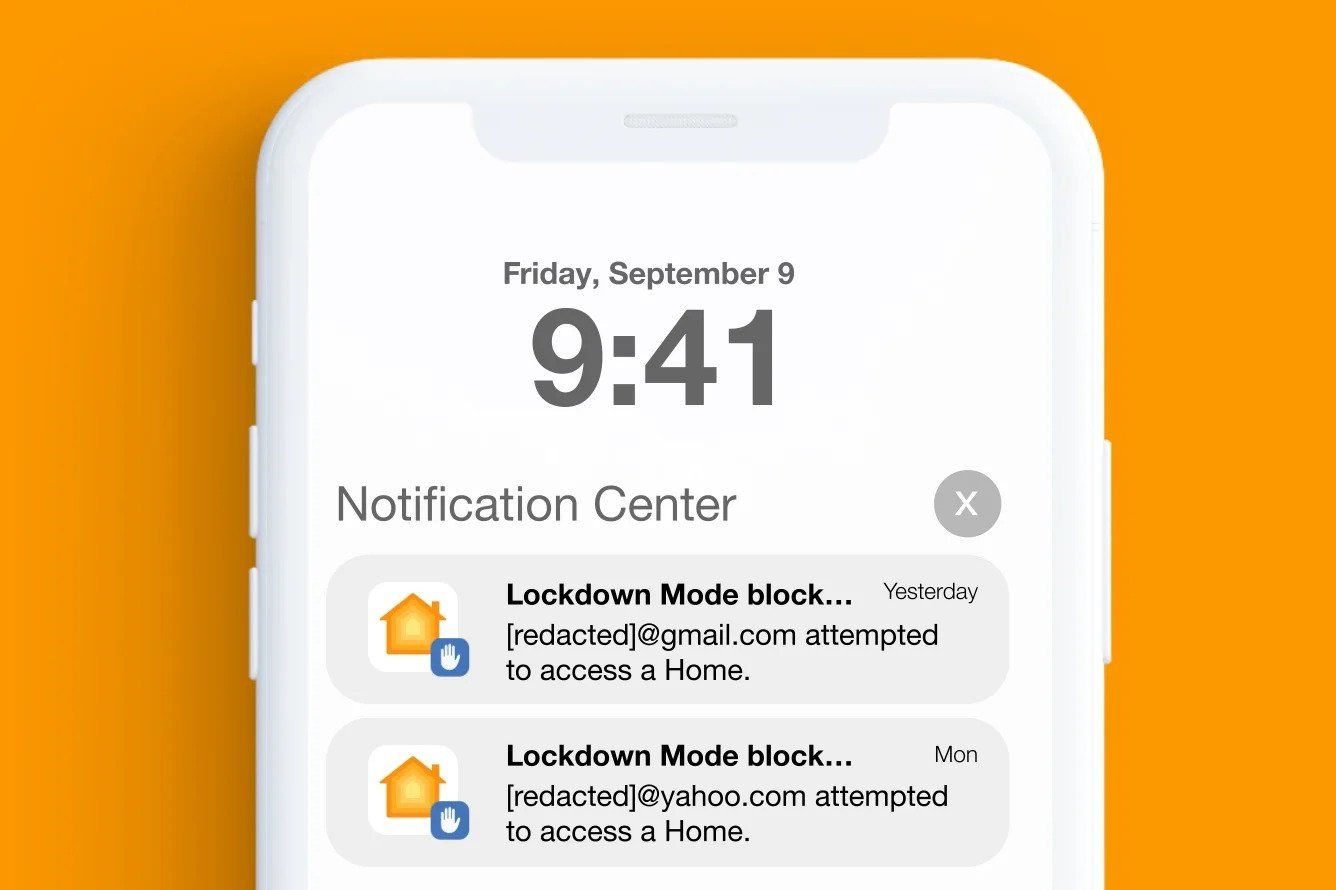
Credits: citizenlab.ca
“We highly encourage all at-risk users to enable Lockdown Mode on their Apple devices,” the researchers said. “While the feature comes with some usability cost, we believe that the cost may be outweighed by the increased cost incurred on attackers.”
PWNYOURHOME and FINDMYPWN are the first zero-click exploits found to use two separate remote attack surfaces on the iPhone. The team at Citizen Lab says this finding should encourage developers to “think holistically about device security, and treat the entire surface reachable through a single identifier as a single surface.”
At Bitdefender, we strongly recommend that everyone keep their smartphones updated with the latest security patches issued by the phone / OS vendor. Equally important, both iPhone and Android users should consider deploying a dedicated security solution to stay safe from online threats at all times.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








