Secure Boot or Bust Under the New EU Cyber Law

As the EU’s new cybersecurity laws take effect, device makers must either build secure boot into their products or fall behind compliance and consumer trust.
EU’s push for built-in integrity
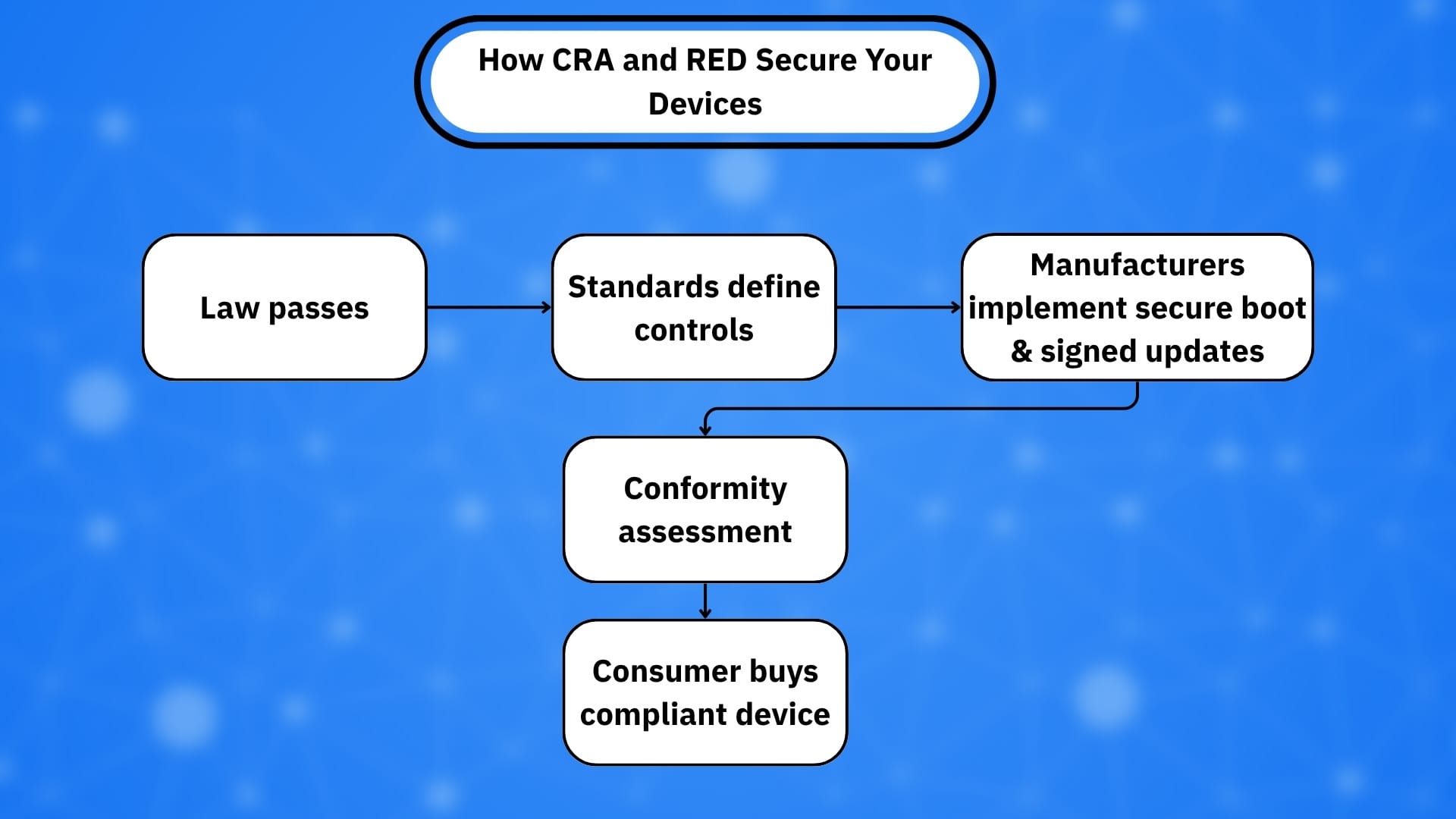
As the EU’s new cybersecurity rulebook lands, one message to device makers (and their customers) stands out: if your gadget can run code, you must prove that only trusted code runs at boot, during updates, and throughout its life.
This is one of the pillars of “secure by design” under the EU’s Cyber Resilience Act (CRA) and the Radio Equipment Directive’s new cybersecurity rules (RED DA).
While the law doesn’t always use the term “secure boot,” integrity protection that acts like secure boot is quickly becoming the baseline. For consumers, that’s good news: fewer bricked homes, fewer zombie botnets, and a more honest interpretation of what “secure” actually means.
What changed and when it hits consumers
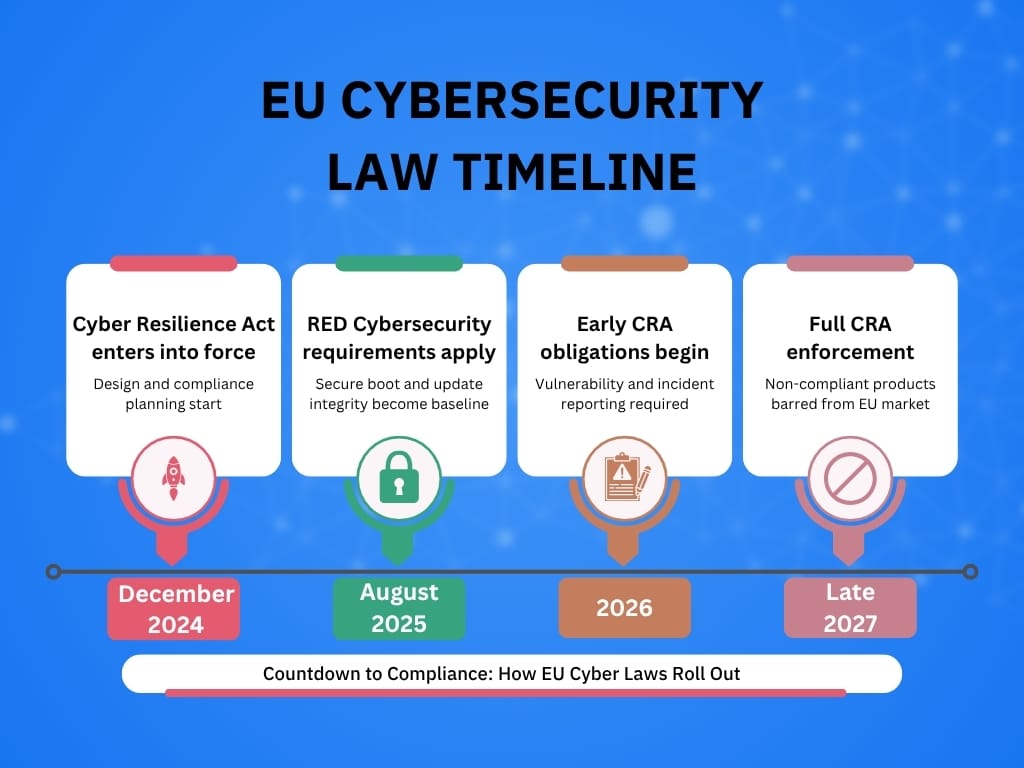
The CRA took force on December 10, 2024. It creates EU-wide cybersecurity obligations for “products with digital elements” such as smart thermostats, cameras, TVs, toys, routers and software, and keeps manufacturers on the hook throughout the product’s lifecycle. Most core obligations ramp up over the next two years, with early reporting obligations starting in 2026 and broad compliance kicking in later.
In parallel, the RED Delegated Act brings mandatory cybersecurity requirements for internet-connected radio equipment as of August 1, 2025. New accompanying standards (EN 18031 series) spell out technical expectations so products can be assessed by uniform criteria. For many consumer devices, those expectations include cryptographic update verification and protection against running tampered firmware, such as secure boot or an equivalent integrity scheme.
So … does the EU literally mandate secure boot?
Strictly speaking, the laws set outcomes, not brand-name features. The CRA and RED DA require that software and firmware integrity be protected, updates be authenticated and that products resist tampering that could harm networks or privacy. In practice, manufacturers meet these outcomes with a chain-of-trust starting at boot (secure boot), plus signed updates and rollback protection. We should expect this pattern to become the standard for phones, wearables, hubs and IoT appliances sold in the EU.
Standards and industry guidance reinforce the point. ETSI EN 303 645 (consumer IoT baseline) and RED cybersecurity standards emphasize software integrity and verified updates; industry notes and vendor compliance guides explicitly map these to secure boot implementations.
Timeline in plain language
- Now: CRA is in force; planning and design work should already align with it.
- Aug 1, 2025: RED DA cybersecurity requirements apply to applicable radio equipment (a big chunk of consumer IoT). EN 18031 standards support conformity.
- From 2026: Early CRA duties start (e.g., reporting actively exploited vulnerabilities and major incidents).
- Late 2027: The main CRA obligations apply broadly; non-compliant products can’t be sold in the EU.
Why consumers should care
- More trustworthy updates: Devices should accept only unauthenticated firmware and software, blocking malicious or accidental tampering.
- Fewer long-term orphans: Manufacturers remain responsible for security throughout the lifecycle, including vulnerability handling and patches.
- Clearer accountability: If a product is insecure by design or ships without proper integrity protections, the manufacturer – not the buyer – bears regulatory risk.
Practical guide for buyers
When shopping for connected devices over the next year, look for:
- Secure boot or equivalent integrity protection: “Only signed firmware runs” or “verified boot” in datasheets and support articles.
- Signed updates and rollback protection: Vendors should state that update signatures are verified and older vulnerable versions can’t be reinstalled.
- Lifecycle and patch policy: Watch for a stated support window (years, not months) and a process for vulnerability disclosure and fixes.
- Conformity claims: References to CRA deadlines and RED cybersecurity compliance (EN 18031 / ETSI EN 303 645) are green flags.
If a vendor is evasive about these topics today, that’s a sign to hold off, especially if the device will be in your home network for years.
What this means for power users and tinkerers
A common worry is that secure boot kills modding. Reality will vary by product, but the requirement is to prevent unauthorized code, not to outlaw customization. Some vendors may support developer modes that keep integrity guarantees (e.g., allowing user-provisioned keys or unlock workflows that don’t gut security).
Expect tighter bootloader policies in phones and IoT hubs as vendors balance compliance with user freedom – the direction of travel under RED DA is firmly toward signed-only firmware on consumer devices.
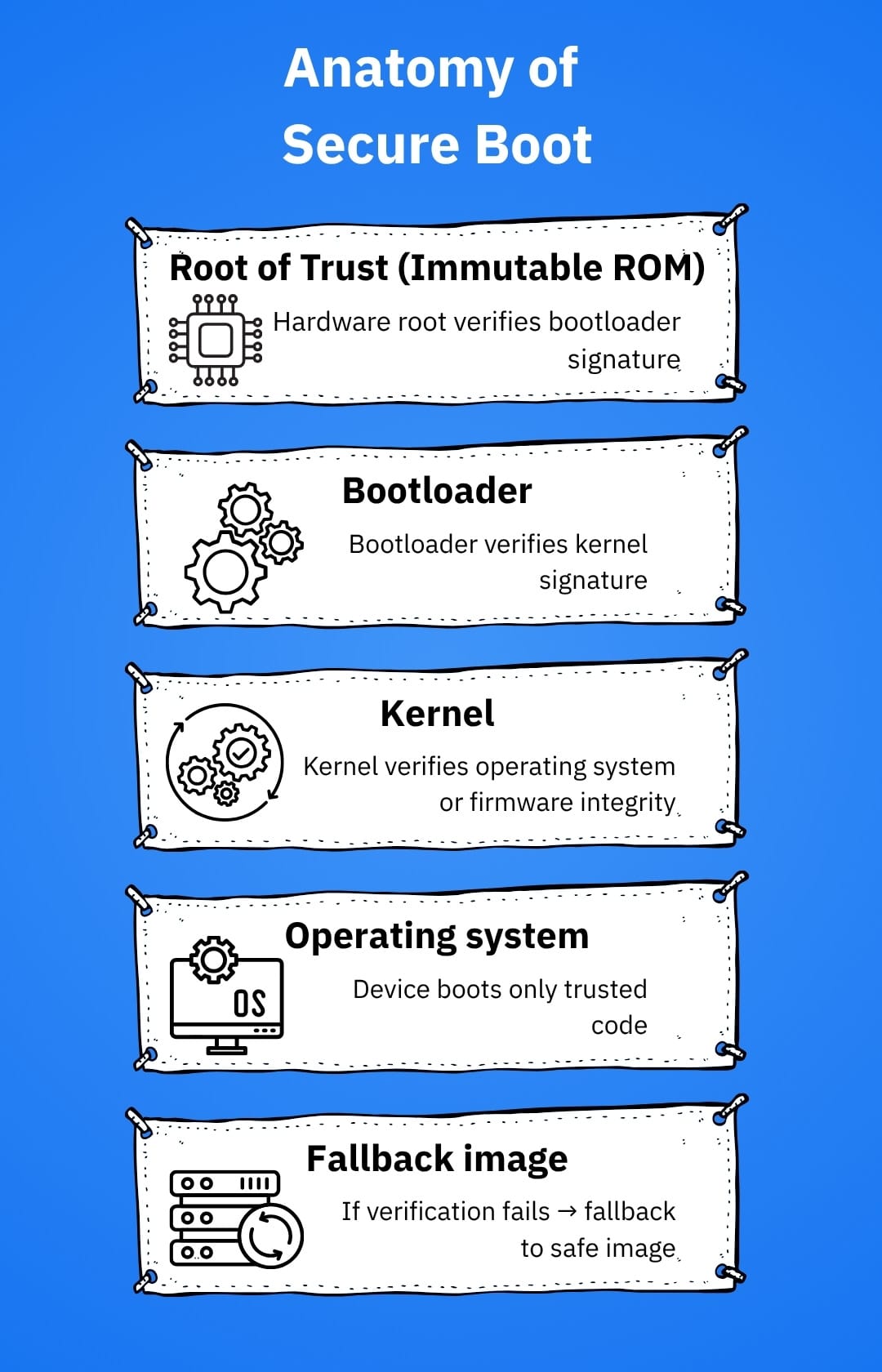
For the curious: how secure boot protects you
Think of secure boot as a door chain for your device’s brain. At power-on, a tiny immutable root checks the next stage’s signature, which checks the next stage, and so on, until the operating system loads. If any steps fails verification, the device refuses to boot untrusted code or falls back to a known-good image.
Combine that with signed updates and rollback protection, and you’ve closed off the easiest persistence tricks attackers use on smart gadgets. This is precisely the integrity posture EU lawmakers are pushing into the mainstream market.
Where the laws go next
The European Union Agency for Cybersecurity (ENISA) and industry groups are steadily publishing guidance that maps legal text to technical controls.
Expect more harmonized standards and certification pathways that make it easier for buyers to recognize compliant products and for vendors to prove security.
Bottom line for consumers
The EU’s new rules finally make the integrity of what runs on your devices non-negotiable. Whether vendors call it secure boot or verified boot, the effect is the same: it leaves fewer paths for malware to persist, enabling safer updates and delivering a stronger promise that the gadget you bought can’t be silently rewired into something hostile.
Over the next two years, let those integrity features and a clear lifecycle pledge be the deciding factors in what you bring home.
Frequently Asked Questions (FAQ)
What is secure boot in simple terms?
Secure boot is a security feature that ensures only trusted, verified software runs when a device starts up. It checks each component in a chain, from the hardware root to the operating system, to prevent tampered or malicious code from loading.
Does the EU’s Cyber Resilience Act specifically require secure boot?
Not by name. The law requires that software and firmware integrity be protected and that unauthorized modifications are prevented. Secure boot, or similar verified-boot mechanisms, are the most practical and accepted ways to achieve that.
When will these EU rules actually affect consumers?
The transition has already started. The RED cybersecurity requirements apply from August 2025, and the Cyber Resilience Act will be fully enforceable by late 2027. That means most new connected devices entering the EU market after those dates must comply.
Why should consumers care about this?
Device integrity directly affects user safety, privacy and reliability. Secure boot and verified updates mean your smart gadgets can’t be silently hijacked, turned into bots or rendered useless by malware.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks