Pegasus Spyware: What It Is and How to Protect Yourself

In a perfect world, you should be able to store files securely on your mobile device and have private conversations at home without fear of being monitored. But when Pegasus spyware hijacks your smartphone, that privacy disappears, and you become a victim of 24/7 surveillance.
A malicious actor can instantly spy on your daily activities, track your location, see who you’re with, and what you’re doing.
If you’re concerned about being monitored, don’t panic. Our Bitdefender security experts have outlined straightforward methods to detect spyware and practical steps to remove threats and restore your privacy.
In this guide, we’ll explain what Pegasus spyware is, why it poses such a serious risk, and what to do if your device is compromised.
What is Pegasus spyware, and where did it come from?
Pegasus spyware is a sophisticated surveillance tool designed to steal data from a target’s device and monitor their activities. Once installed on an Android or iPhone, it can collect sensitive data like media files, access contacts and call logs, and read private text messages and emails. In more extreme cases, it can even activate your microphone or camera to spy on your conversations and daily activities.
While you might be shocked that such a tool exists, Pegasus was not initially intended to violate civilian privacy. Developed in 2011 by the Israeli cyber-intelligence company NSO Group, a government agency that prevents and investigates terrorism, Pegasus was a counterterrorism software used for tracking and combating security threats.
But since 2011, governments and state agencies from over 50 countries have reportedly used Pegasus to attack journalists, activists, lawyers, and politicians for their dissenting opinions or policies. The first recorded case was in 2016, involving a failed exploit attempt on a human rights defender’s device. Subsequent investigations, like the Pegasus project by Forbidden Stories and Amnesty International, confirmed that Pegasus spyware infections were far more widespread than initially believed, with evidence of more than 50,000 potential targets worldwide.
Pegasus spyware and human rights abuses
In 2021, then-United Nations High Commissioner for Human Rights, Michelle Bachelet, described the Pegasus system as a threat to human rights and privacy, following reports of its unlawful use.
“Various parts of the UN Human Rights system, including my own Office, have repeatedly raised serious concerns about the dangers of authorities using surveillance tools from a variety of sources supposed to promote public safety in order to hack the phones and computers of people conducting legitimate journalistic activities, monitoring human rights or expressing dissent or political opposition.” — Former UN Human rights chief
Human rights organizations have since warned that Pegasus spyware allows for unauthorized surveillance practices that undermine freedom of expression and the right to privacy. Investigations by Amnesty International and Citizen Lab revealed that journalists, political figures, activists, and lawyers were among those targeted, proof that the spyware is used for purposes far beyond criminal investigations.
These findings raised concerns about the lack of transparency in how governments deploy such tools and sparked several lawsuits against NSO Group. In 2019, WhatsApp’s parent company, Meta, sued the firm for allegedly hacking more than 1,400 users through its platform.
Apple followed in 2021 after discovering iPhones had been targeted with zero-click attacks. And in 2025, a U.S. court ordered NSO to pay Meta $167 million — one of the biggest penalties ever issued against a spyware company. Still, NSO Group maintains that its software is only available to governments that support human rights and denies involvement in the high-profile abuses reported in the media.
Why is Pegasus spyware so dangerous?
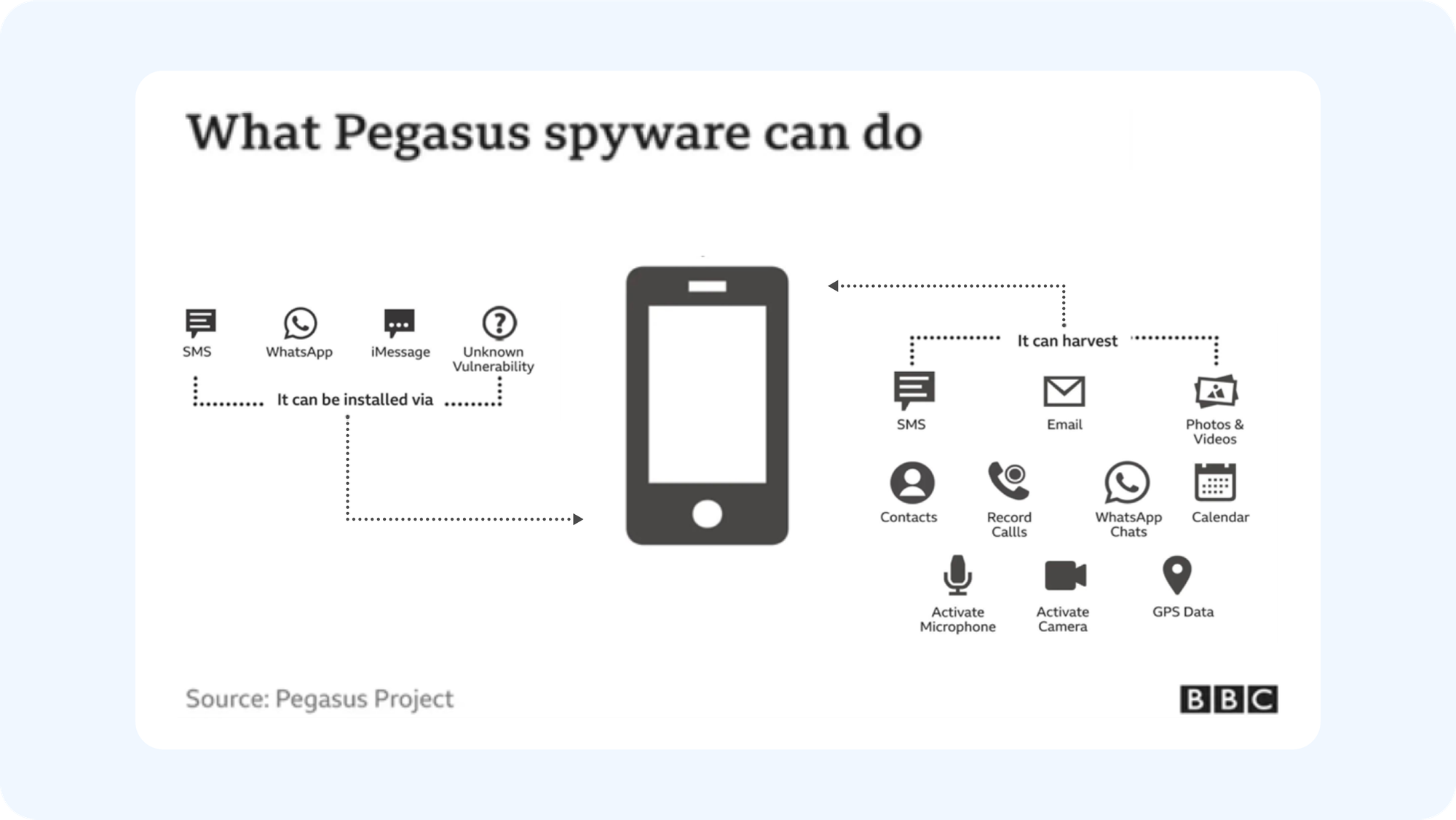
Source: BBC
With other spywares, there is a clear prevention strategy: don't click on suspicious links and don't install apps from third-party platforms. But Pegasus is more advanced than any spyware you may have previously encountered. Here’s why you should be concerned:
Zero-click attacks
What sets Pegasus spyware apart from other potential threats is that it doesn’t always rely on phishing or social engineering to hack devices. Instead, it can use zero-click attacks, which compromise your phone without any interaction on your part. Simply receiving a message or notification can be enough for Pegasus to gain access. This ability makes Pegasus one of the most elusive and dangerous spyware threats ever discovered.
Complete data harvesting and device compromise
After a successful infection, Pegasus requests system privileges and permissions, giving it full access to your personal and corporate data. This includes text messages, phone calls, photos, videos, and information from other apps. It also hijacks your microphone and camera to secretly monitor your private conversations in real time.
It is persistent and works silently
Pegasus spyware operates silently in the background, leaving almost no trace of its presence. You could be infected with Pegasus for weeks or even months without noticing anything unusual. Plus, removing it is extremely difficult, as the spyware can persist or reinstall itself through hidden duplicates within your system.
Threat to national security and freedom of speech
When terrorists or criminals get their hands on Pegasus, they can use it to monitor and silence key figures such as government officials, politicians, human rights activists, and journalists. These tools can also collect sensitive data, potentially compromising national security.
In many cases, these surveillance attempts force journalists and researchers to self-censor and omit critical information. Former UN chief of Human Rights shared the same sentiment:
“Use of surveillance software has been linked to arrest, intimidation and even killings of journalists and human rights defenders. Reports of surveillance also have the invidious effect of making people censor themselves through fear. Journalists and human rights defenders play an indispensable role in our societies, and when they are silenced, we all suffer.”
This undermines the principles of free press and journalistic integrity. And over time, such abuse can weaken public trust in media organisations and restrict the free flow of information.
How does Pegasus spyware work?
You’re probably familiar with how common malware infections happen: you click a malicious link, install a harmful program, or download a corrupted app from an unverified store. Well, NSO's software operates differently. Instead of relying mainly on social engineering, it uses sophisticated threats to gain access without any obvious interaction. Let’s break down how the Pegasus spyware works.
Targets are identified and researched
Once Pegasus operators select a target, they gather vital information about the victim's device, phone numbers, email addresses, device model, and operating system version. This information helps attackers determine the most effective entry point for infection, which could be through WhatsApp, iMessage, or even a phone call. For example, if a potential target uses an iPhone but does not have WhatsApp installed, the hackers are more likely to choose iMessage as the point of entry.
Delivery and entry
This phase can be executed through phishing links sent to your DMs or emails, but more advanced attacks utilize zero-click exploits, which don't require user interaction. The attacker simply has to call your device or send a message through your communication channels, and you are instantly infiltrated. Attackers can also install spyware directly if they briefly obtain physical access to your phone.
Zero-day Vulnerabilities and exploits
A zero-day vulnerability is a flaw or weakness in an operating system, software, or app that developers did not notice or fix promptly. These can be bugs or missing security patches that leave your device or certain apps exposed to hacking.
Once your device is breached, attackers can gain control and escalate system privileges or permissions, such as access to your contacts, calendar, location, microphone, or camera. This helps them steal data like text messages, photos, videos, and call logs.
Command-and-control
After Pegasus runs on your device, it communicates with its operators and transmits data through a two-way channel known as the Command and Control server (C2). Through this channel, the operator instructs the spyware on which files to steal, and the harvested data is silently transmitted back to the hackers (a process known as exfiltration).
All of this occurs quietly in the background because the server is often encrypted or routed through Pegasus anonymizing transmission networks such as proxies, VPNs, or cloud services. This makes Pegasus' activities extremely difficult to trace or detect.
Persistence
Persistence is another tactic Pegasus infections use to remain active even after a reboot or software update. The spyware can duplicate itself into hidden modules, bury them deep within your device, create background tasks that run automatically, or disguise itself as a system app to avoid detection.
Even if one manifestation is removed, multiple copies may remain on the device and can reinstall themselves without your knowledge. This is why it's difficult to remove Pegasus spyware, as hackers can continuously access your data while bypassing protective measures.
Who is at risk of Pegasus spyware surveillance?

Source: BBC
Not everyone is at risk of a Pegasus spyware attack. NSO Group reportedly charges clients over $500,000 to access its spyware, so targets are typically of interest to state or security agencies. They may include members of an opposing political party, investigators of classified government activities, or journalists in possession of highly sensitive information. If you fall into any of these categories, then exercise caution:
Government officials and political figures
Pegasus is often used to spy on high-ranking officials and diplomats to gain insight into national policies and negotiations. According to Amnesty International, over 600 government officials in more than 34 countries have allegedly been targeted by NSO Group’s spyware. One of the reported victims was French President Emmanuel Macron in 2021.
That same year, Citizen Lab, a Toronto-based research group that investigates digital threats, alerted the UK government about attacks on the Prime Minister’s Office and the then-Foreign and Commonwealth Office (FCO). While the purpose of these attacks isn’t publicly known, Citizen Lab suggests that spying on government officials is often part of international espionage.
Journalists, human rights defenders, and civil society leaders
These are some of the most well-known cases involving Pegasus:
- The very first reported attack, in 2016, targeted Emirati human rights defender Ahmed Mansoor, who received a malicious link disguised as classified information about inhumane activities in UAE prisons. Activists and human rights defenders are often at risk because they expose corruption or report on sensitive issues that could damage the reputation of influential political figures.
- One of the most cited examples is the gruesome assassination of Saudi journalist and activist Jamal Khashoggi in 2018, while he was planning his marriage. Khashoggi was the former editor-in-chief of the progressive Saudi newspaper Al Watan and a dedicated critic of the Saudi government, particularly King Salman and Crown Prince Mohammed bin Salman.
Forensic analysis later revealed that Pegasus spyware had been installed on the phones of his family and associates months before his murder. This allowed hackers to monitor his location and conversations. - In a similar case, journalist Coco Pineda Birto appeared on a list of Pegasus targets a month before his equally brutal assassination in 2017.
These incidents just go to show that Pegasus truly threatens the safety of journalists worldwide.
Friends and family of high-profile figures
If you don’t consider yourself a high-profile figure, you may be relatively safe from Pegasus and similar threats. But if you are in contact with a politician, journalist, or activist, whether as a close friend or family member, you could still be at risk.
Attackers may exploit vulnerabilities on your device to spy on these individuals and track their location. This was the case with Hanan Elatr, Jamal Khashoggi’s wife, whose device was reportedly compromised months before her husband’s murder.
How do you detect Pegasus spyware on your mobile device?
Unfortunately, Pegasus is not the typical spyware that leaves evident traces for users to detect. Thanks to its zero-click exploits and other advanced techniques, your device could be infected for months without your knowledge. Still, some potential warning signs may indicate a compromise, including unusual battery drain, device overheating, sudden spikes in data usage, and other abnormal behavior.
Unusual battery drain
If your phone suddenly struggles to last through the day despite minimal usage, it could be a sign of a spyware infection. Malicious programs like Pegasus run numerous operations in the background that require a lot of power.
They duplicate themselves, communicate with their operators, and transmit your data via Command and Control (C2) channels. All of this puts a heavy load on your device’s processor, which can lead to significant battery drain. This is how to check if this is the culprit:
- On iOS devices: Go to Settings > Battery > check the Battery Level graph and Battery Usage by App.

- On Android devices: Open Settings > Battery > Battery usage (or Device Care) > review which apps are using the most power. If you notice any app consuming a lot of power in the background, it could indicate hidden processes like spyware.

Sudden overheating
With the number of processes Pegasus runs in the background, it’s not surprising that overheating is another common symptom of an infected phone. To see if this might be the cause, check your battery usage for unusually high consumption and remove any unfamiliar apps that are draining your battery.
Unexpected data usage spikes
The operations Pegasus performs on your phone require large amounts of data. This includes transmitting stolen photos, videos, text messages, and location data. If you haven’t been downloading large files or streaming long videos, these spikes could indicate that malicious software is running in the background. Follow these instructions to check for unusual data usage:
- iOS devices: Go to Settings > Mobile Data > Scroll down to view data usage per app.
- Android devices: Go to Settings > Network and Internet > Data Usage > Mobile Data Usage. Review recent data activity and check for apps you don’t recognize or rarely use that consume excessive data.
Frequent crashes or slowdowns
Mobile devices naturally slow down as they age. But in rare cases, this could signal a spyware infection. Pegasus can interfere with core system functions or apps such as Gmail, WhatsApp, and iMessage, which it often uses as entry points for exploits. The result can be a device or specific apps that crash or freeze unexpectedly.
Indicator lights are turning on and off
If Pegasus has compromised your device, you might notice your indicator lights flickering randomly, even when you’re not using the camera or microphone. This can be a warning that spyware has taken control of these components.
Even brief flickers could mean that your conversations are being recorded, or photos or videos are being captured. On iOS devices, a green light indicates camera use, and an orange light indicates microphone access. On Android devices, similar activity usually appears as a green or orange dot near the top-right corner of the screen, close to the battery status icon.
Unknown installed programmes and certificates
Pegasus often installs hidden configuration profiles or digital certificates that give it administrative control over your device. These profiles can grant permissions beyond what regular apps can access, enabling deeper system-level monitoring.
- On iOS devices: If you notice a configuration profile you didn’t install in Settings > General > VPN and Device Management, this could be a red flag.
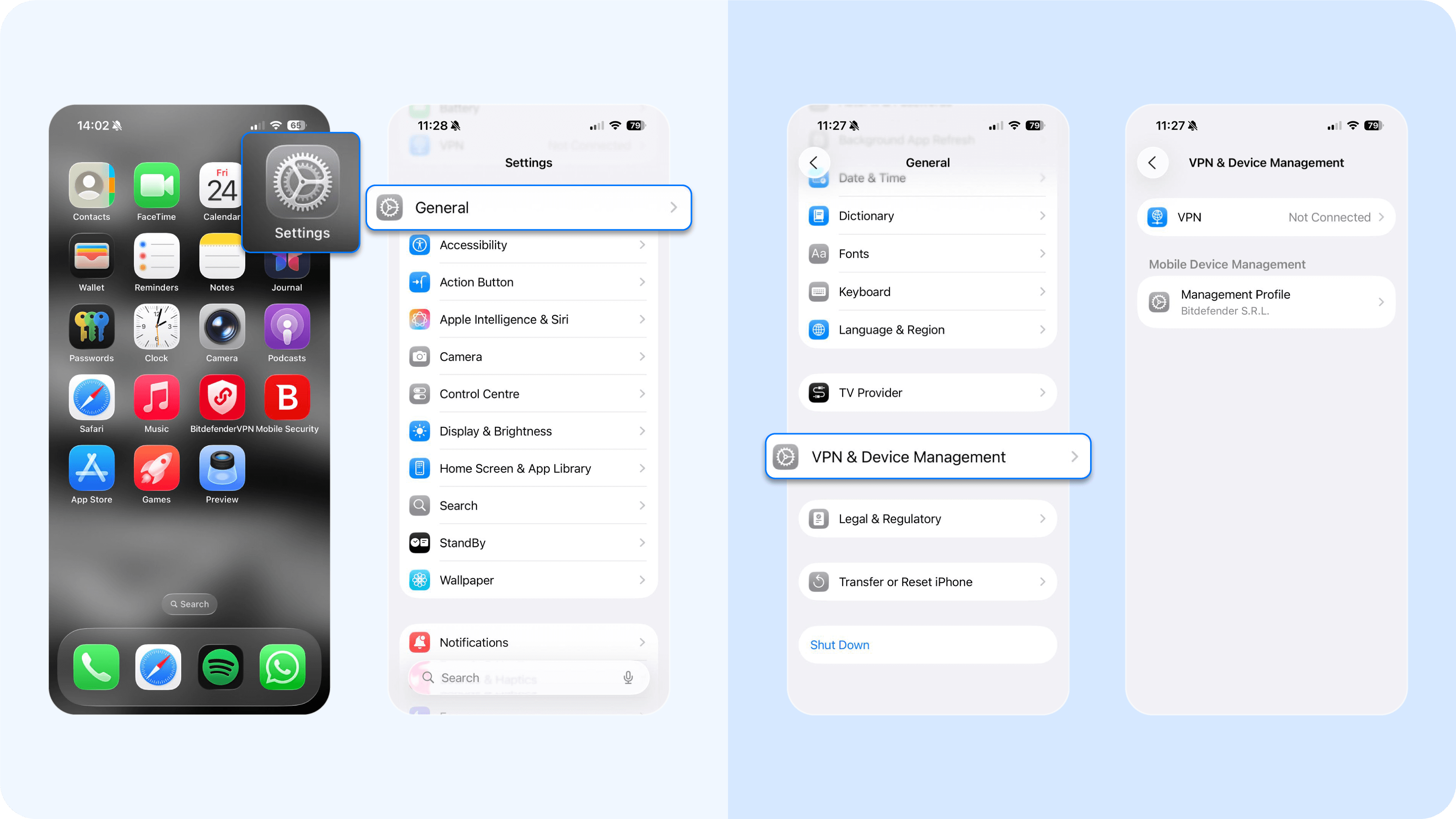
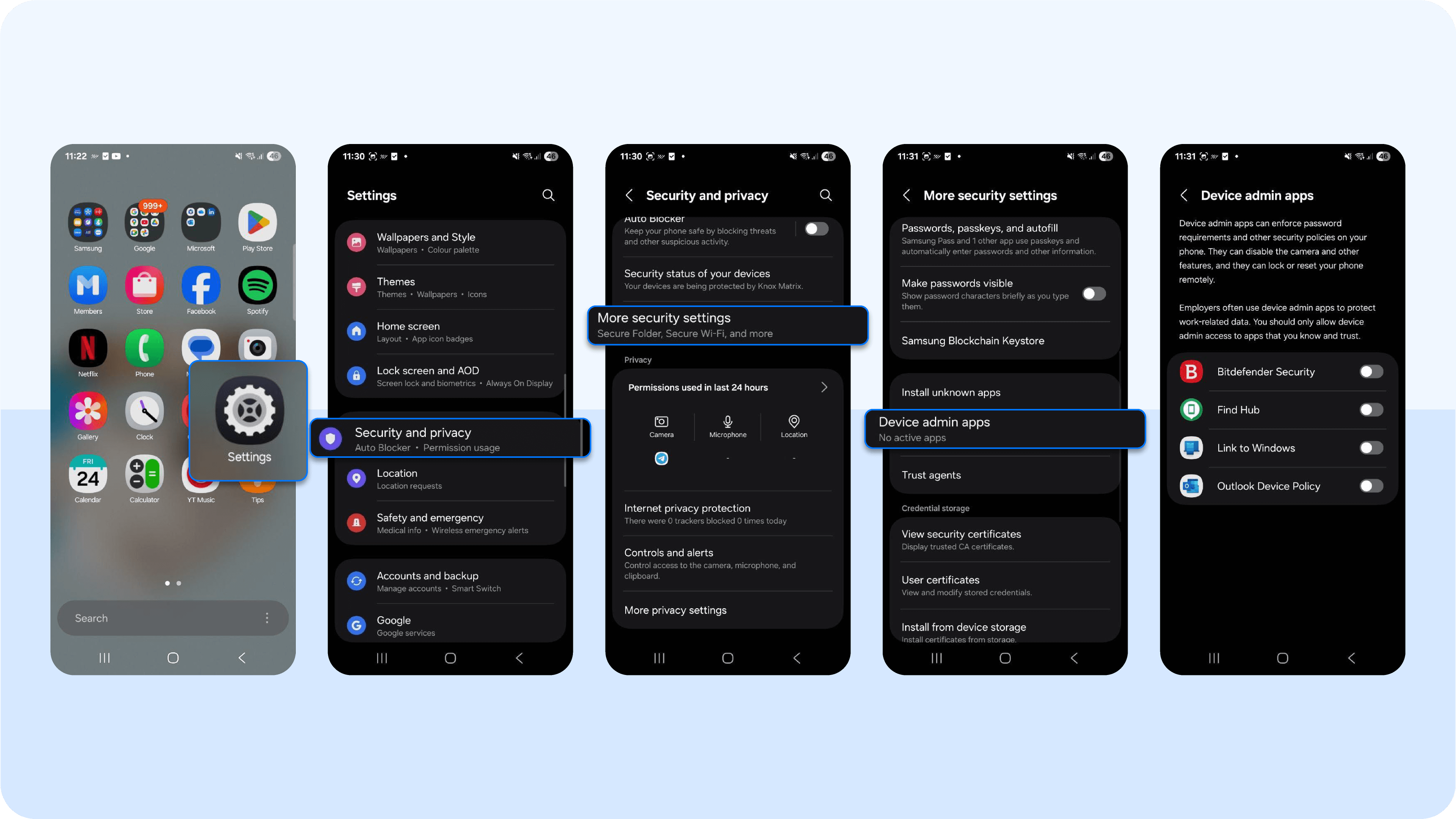
- On Android devices: Check for unknown device admin apps or unfamiliar certificates by going to Settings > Security and Privacy > More Security Settings > Device Admin Apps (or Encryption and Credentials > Trusted Credentials). Disable or remove any apps or certificates that have system-level permissions but aren’t recognized.
Suspicious iTunes backup or sync behaviour
In a bid to persist or reinstall itself on your device, regardless of updates, reboots, or factory resets, Pegasus can interfere with your device’s backup system by manipulating iTunes or iCloud backups.
You might notice your phone suddenly initiating backups you didn’t trigger, or find unfamiliar backups on your computer or iCloud account. This allows the spyware to reinstall itself even if your device is wiped. Here’s how to check for this:
- iOS devices: Go to Settings > [your name] > iCloud > iCloud Backup or open Finder/iTunes > Preferences > Devices. Check for unfamiliar backup files, unknown timestamps, or multiple backups you didn’t initiate.
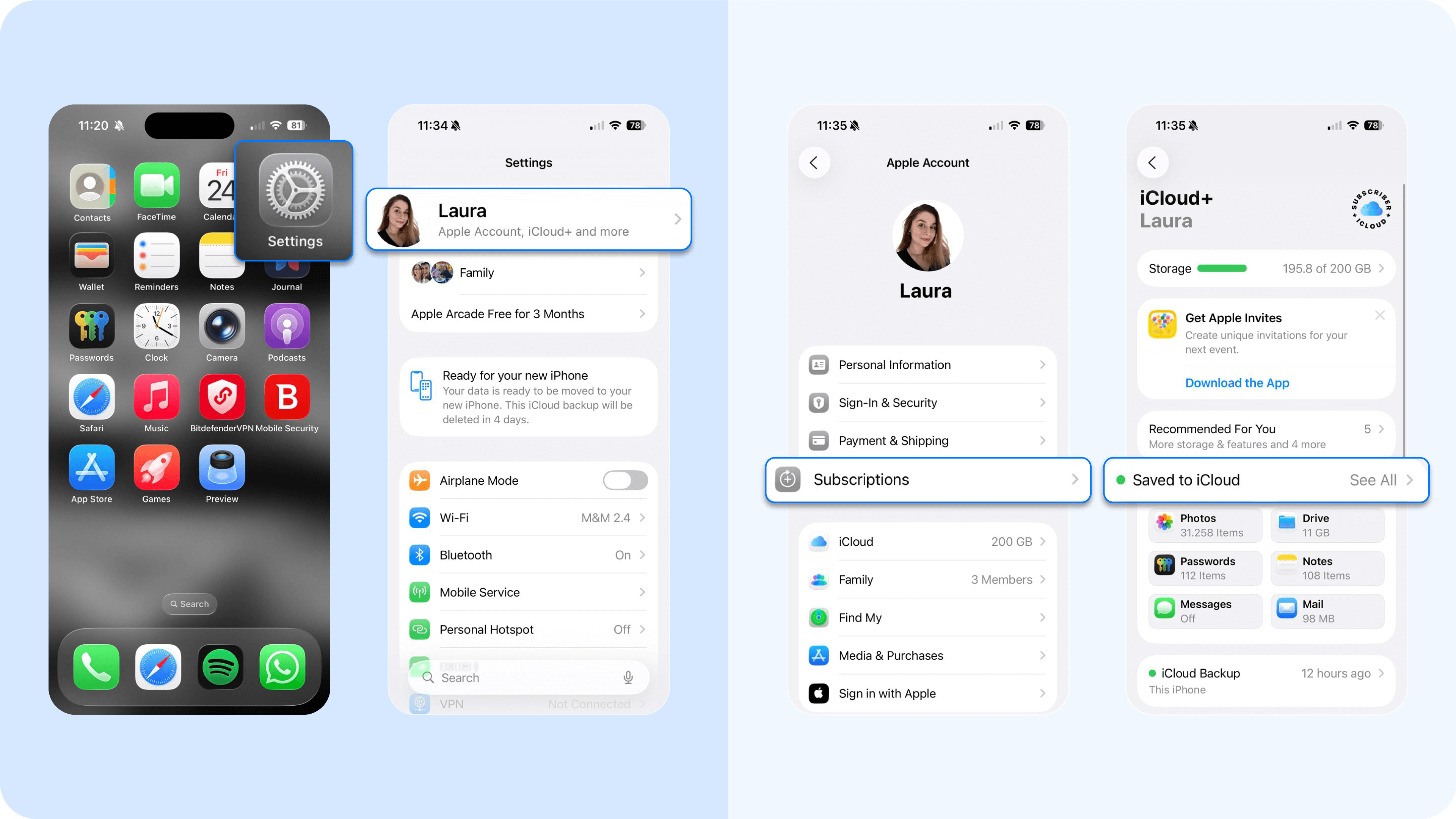
- Android devices: Go to Settings > Google > Backup or Settings > System > Backup. Review the listed backups, note unusual timestamps, or devices you don’t recognize. Delete questionable backups from your Google account and reset your Google password and Apple ID.
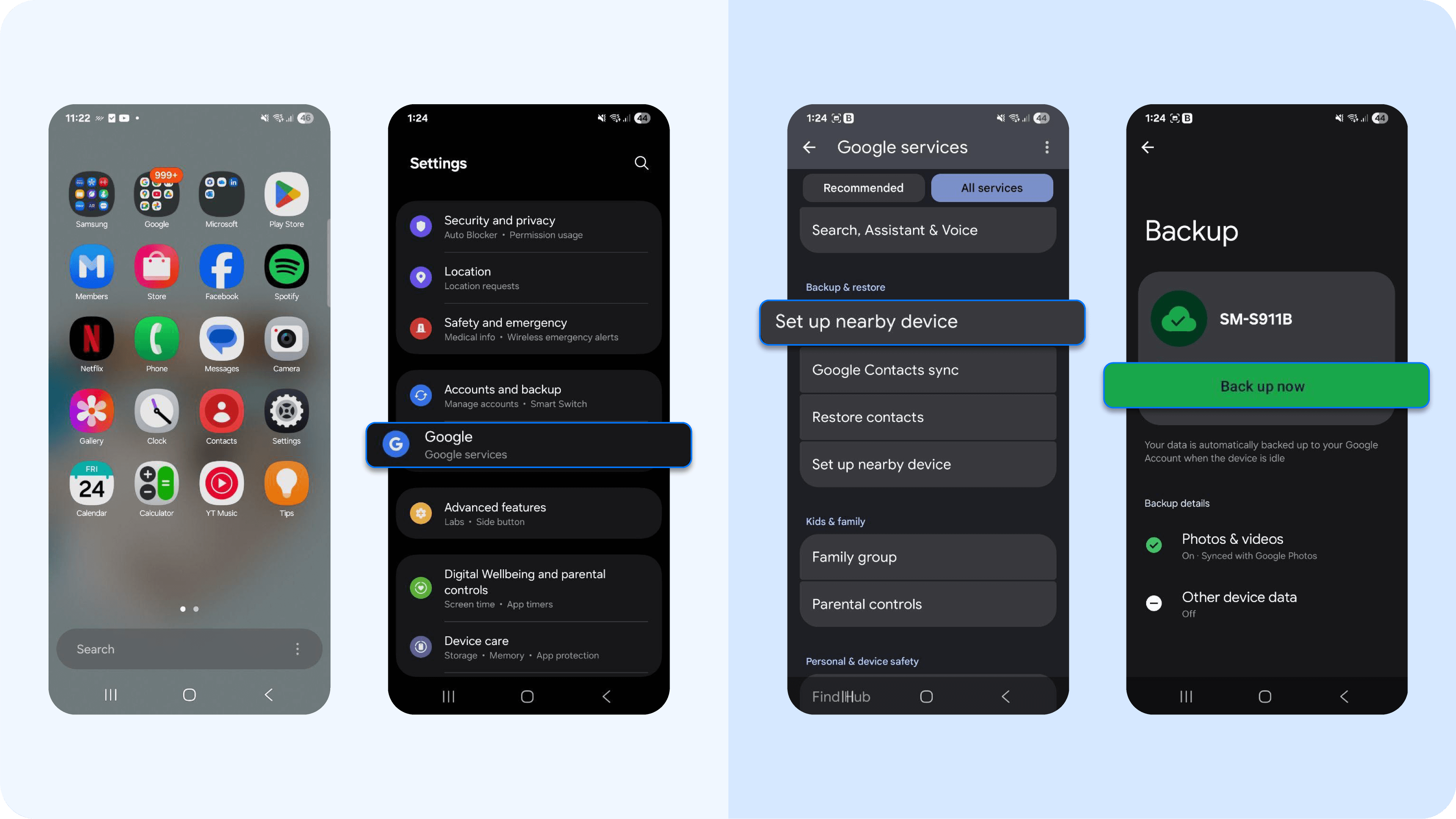
Unusual push notifications or missed calls
One of the main entry points for Pegasus infections is through messaging or phone call apps. On WhatsApp or iMessage, you might notice strange missed call notifications from numbers you don’t recognize, or call alerts that vanish almost immediately after they appear. These unusual or disappearing alerts could indicate that an attacker attempted to install spyware on your device through one of these channels.
Tampered security or privacy settings
A compromised phone may also show tampered security or privacy settings. Your system updates may be turned off, or some app permissions granted without your consent.
- On iPhone: Go to Settings > Privacy and Security > App Privacy Report to see which apps have accessed your camera, microphone, and location.
- On Android devices: Go to Settings > Privacy > Permission Manager to review recent app access. Any unexpected changes to your security settings or app permissions should raise suspicion.
Seek digital forensics help from Citizen Lab or Amnesty International
For journalists, human rights activists, or politicians, the best way to confirm a hack is by consulting forensic teams like Citizen Lab in Canada or Amnesty International. This was the case in 2016 with the human rights activist who suspected he was being targeted by Pegasus.
Thanks to Citizen Lab's intervention, the hacking attempt was promptly discovered and prevented. You can also take proactive steps by
- Reaching out directly: Visit Citizen Lab’s official website or Amnesty International’s Security Lab for instructions on how to submit your device for forensic analysis.
- Preparing your device: Avoid factory resetting or tampering with your phone before sending it in. This could erase vital forensic evidence.
- Documenting your concerns: Keep a record of suspicious behavior (unusual calls, text messages, or phone performance) to assist their investigation.
How can I remove Pegasus spyware from my device (Android and iPhone)?
In the event of a Pegasus infestation, here are some quick troubleshooting tips you can perform to remove the hackers from your device.
Install the latest security patches
Keeping your device updated is one of the most effective ways to protect against Pegasus and similar spyware. Security patches are designed to fix the vulnerabilities these threats exploit to enter your phone in the first place.
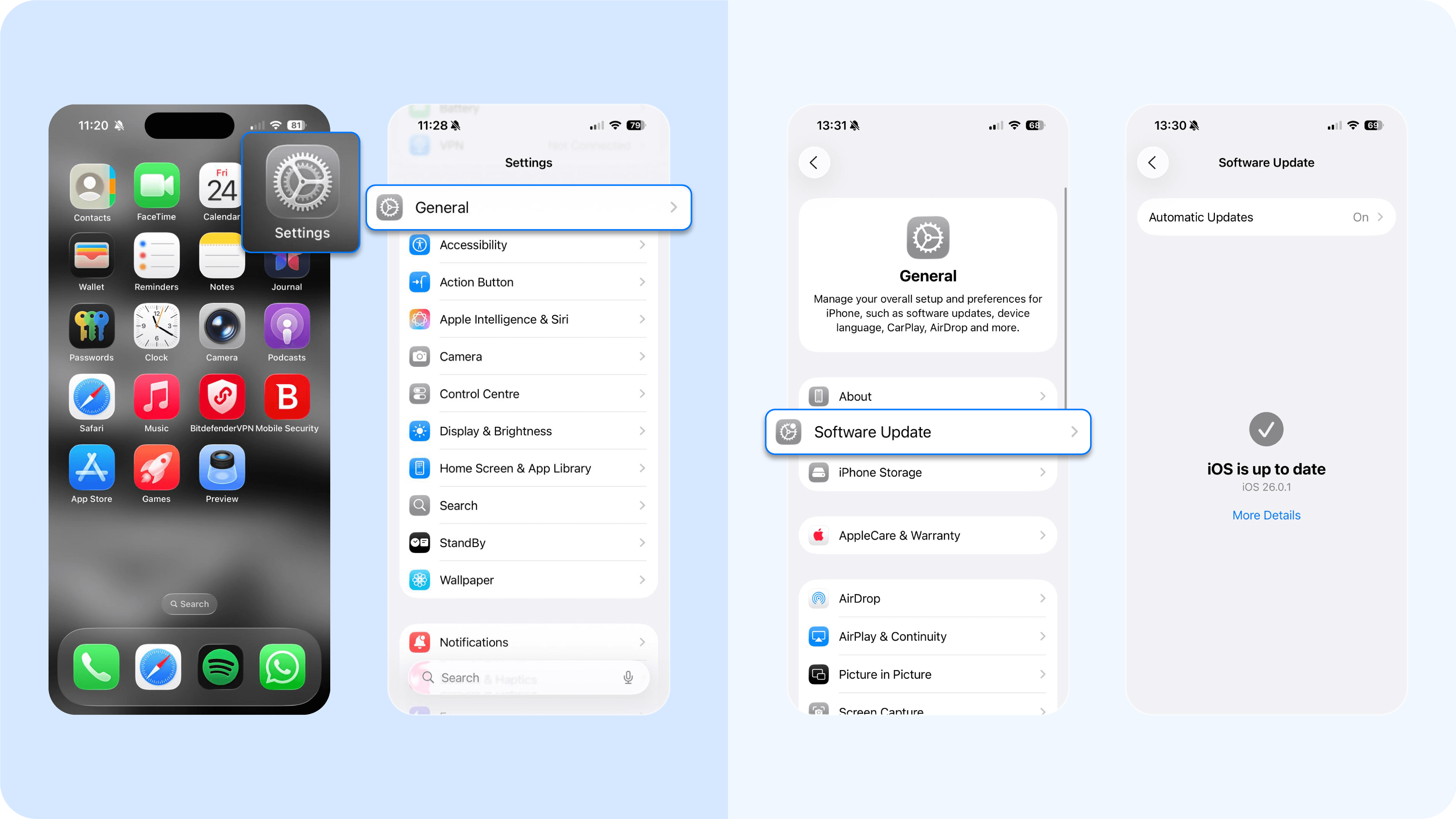
- For iPhone: head to Settings > General > Software Update > Download and Install > If an update is available, tap Download and Install, then follow the prompts. Make sure your phone is plugged in and connected to Wi-Fi.
- On Android: Settings > Software update > Check for updates > Download and install
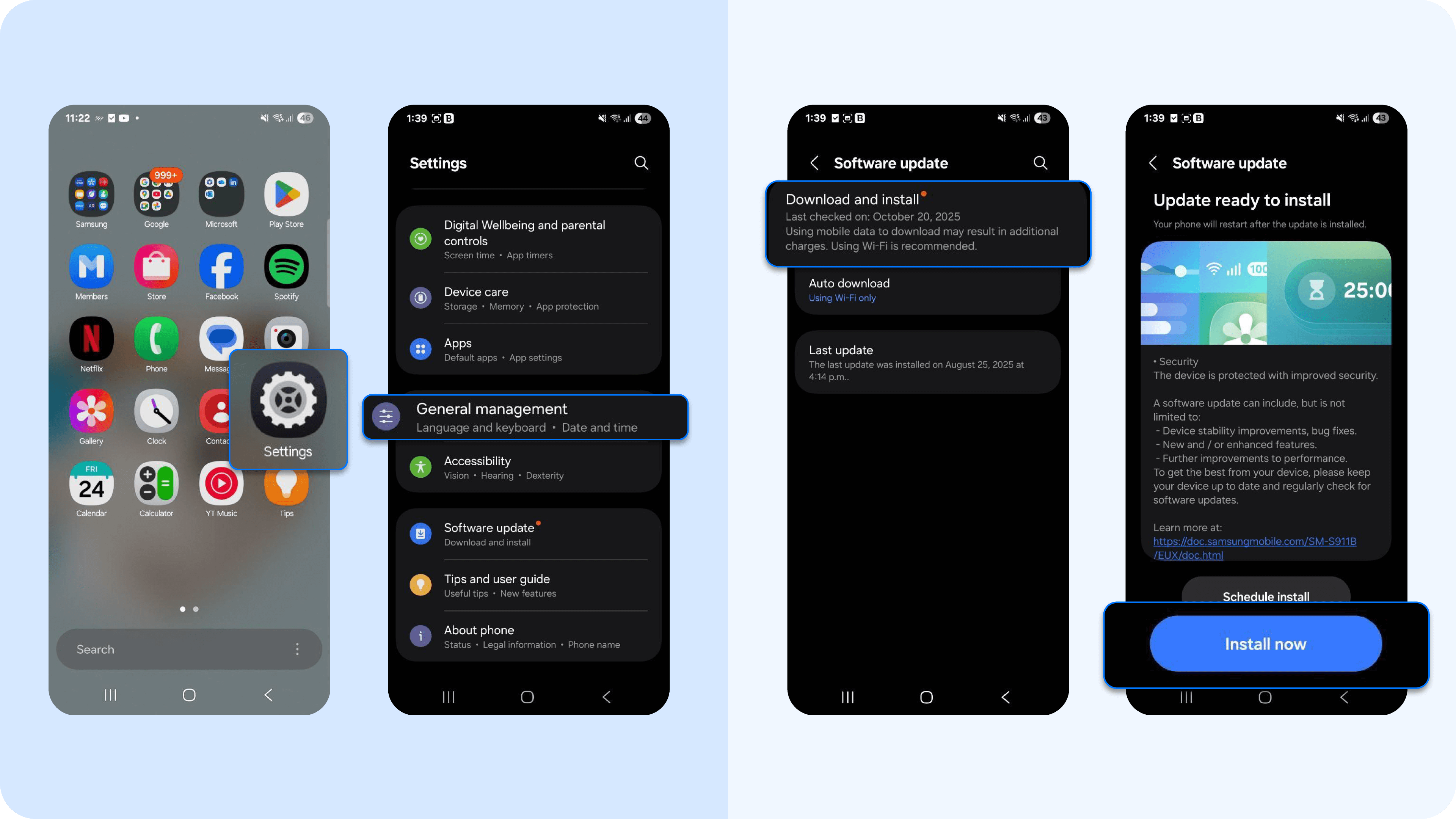
It's important to note that while installing updates can remove Pegasus spyware from your device, this doesn’t always work if you’ve already been infected. Pegasus is engineered to burrow deep into a system’s core files, so eliminating it is extremely difficult.
Still, prompt updates can make a real difference. For instance, in 2021, Apple released an emergency iOS update (version 14.8) after Citizen Lab discovered a zero-click Pegasus exploit using iMessage.
This update successfully patched the vulnerability and immediately blocked further infiltration through that channel. That’s why you should install updates immediately once they’re available. Doing so closes known vulnerabilities and prevents reinfection.
Delete and reinstall problematic apps
Some apps can become compromised or serve as gateways for spyware like Pegasus. Deleting and reinstalling them helps remove Pegasus spyware that may have been injected into their files.
- iPhone: From your Home Screen scroll to Recently Added Apps > Delete App

- Android: Go to Settings > Apps > [Select App] > Storage and cache > Clear cache > Clear storage > Uninstall >. This process removes Pegasus spyware and ensures you reinstall a clean, verified version of the app.
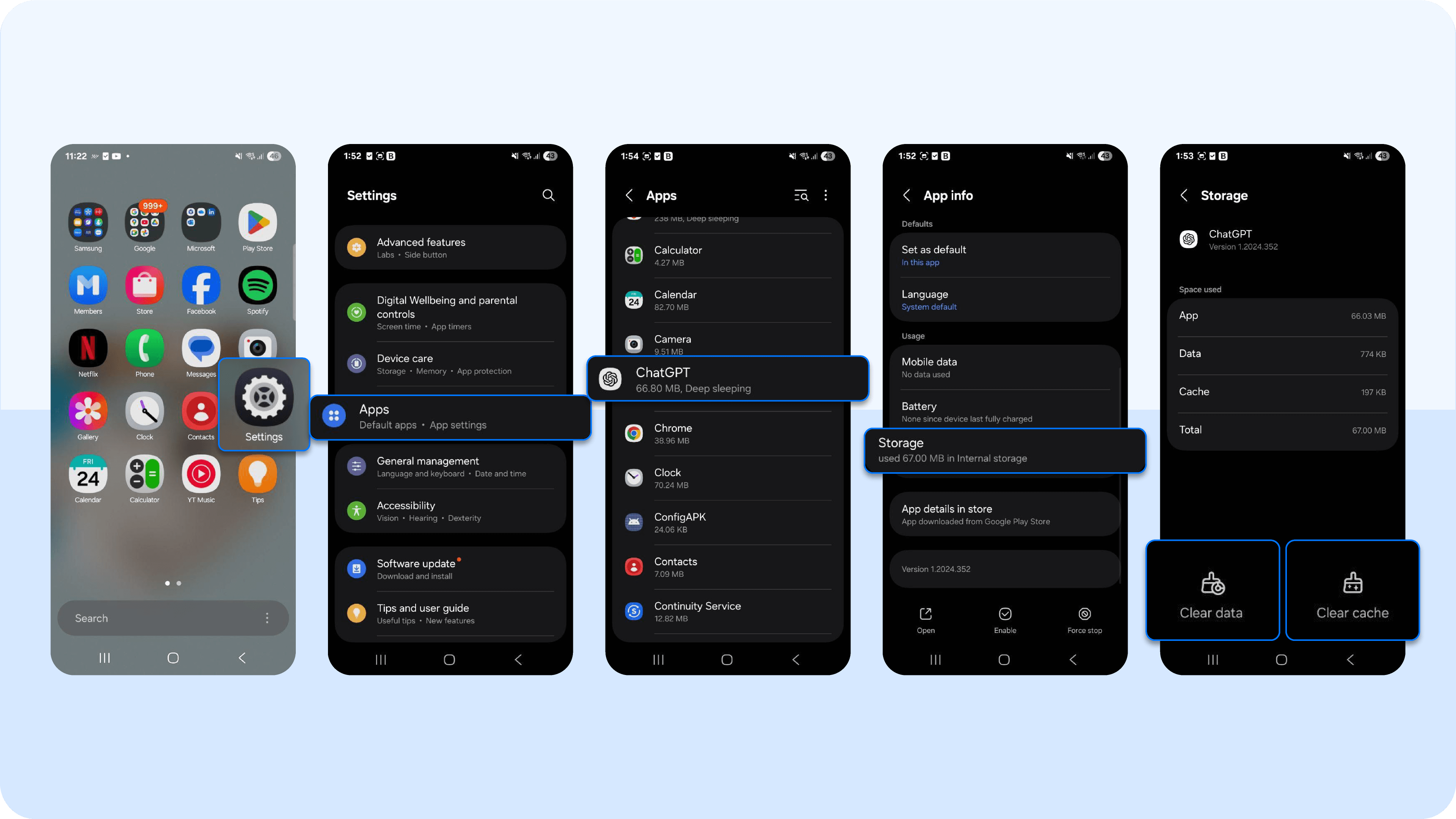
Pro Tip: Always reinstall apps from the official sources — the App Store or Google Play Store. Avoid third-party APKs or unofficial stores, as they often host tampered or spyware-laced versions of legitimate apps.
Run a mobile security scan
Even if your phone seems fine, a full mobile security scan can detect unusual background activity and remove Pegasus spyware from your devices. One of the most reliable options is Bitdefender Mobile Security, available for both Android and iOS. To run your first scan:
Go to the App Store or Google Play Store> Search “Bitdefender Mobile Security” > Install > Open > Sign in or create an account > Run Quick Scan.

Remember to keep Bitdefender updated and enable real-time protection so it can automatically monitor and block new threats. This helps detect advanced spyware like Pegasus that can reappear after restarts or updates.
Change passwords for all accounts afterward
If there’s even a slight chance your device was compromised, assume that all your passwords and logins have been exposed. Spyware can record keystrokes, intercept authentication codes, and access stored credentials, meaning no account linked to that device is entirely safe. Here's what you should do:
- Use a different, clean device (not the one potentially infected with Pegasus) to change your passwords.
- Start with your compromised email accounts, since they’re often the recovery hub for other logins.
- Then update passwords for social media, banking apps, and cloud storage.
- Create strong, unique passwords for each account by combining uppercase, lowercase, numbers, and symbols.
- Enable two-factor authentication (2FA) wherever possible for extra protection, and use a password manager to secure your passwords in one encrypted vault.
Restore factory settings
If your mobile device continues to show suspicious behavior even after installing updates and scanning with security tools, performing a factory data reset may help remove Pegasus spyware from your device. This process wipes all apps, data, and settings from your phone and restores it to its original, “like-new” state. This is how it is done:
- On iPhone: Go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings > enter your passcode > confirm Erase iPhone.

- On Android: Go to Settings > General Management > Reset > Erase all data (factory reset) > confirm with your PIN or password.

We advise not uploading backups to a wiped phone, as backed-up threats could reinstall themselves.
Replace your phone
Pegasus is designed to replicate itself, hide in backups, and reinstall even after system updates or resets by exploiting deep, often invisible vulnerabilities in your phone’s operating system. This makes traditional recovery methods unreliable.
If you still notice signs of infection after a reset, the only truly secure solution is to replace your device entirely. A fresh, uncompromised phone ensures that Pegasus can no longer transmit your data or track your activities.
How can I protect my phone from Pegasus infections and other potential threats?
Pegasus may be one of the most advanced spyware ever developed, but that doesn’t mean your defenses are powerless. Taking proactive steps to secure your device reduces your risk of infection and shields you from countless other forms of malware, phishing, and data theft. The following are practical ways to strengthen your phone’s defenses.
Always keep your operating system updated
Most spyware attacks, including Pegasus, rely on exploiting software vulnerabilities or security loopholes in your phone’s system that developers haven’t fixed yet. Once discovered, companies like Apple and Google release updates to seal those gaps. Keeping your phone updated ensures that your device has the latest security patches against known exploits.
Secure your device by avoiding unattended access
Another way to protect your phone from spyware is to never leave your device unattended. Even brief physical access can be exploited to install malicious software. In Jamal Khashoggi’s case, his wife’s device was infiltrated with spyware in just 72 seconds during her detention at the Dubai International Airport in April 2018. This unauthorized Pegasus surveillance continued until Khashoggi's assassination in October 2018.
Use real-time protection with trusted mobile security tools
Installing a security tool like Bitdefender gives your mobile device an added layer of defense against all forms of malicious software. From the app’s dashboard, you can access the Malware Scanner feature, which regularly scans your device to detect any suspicious activity before it can compromise your data.
Avoid malicious links or suspicious SMS messages
Though NSO's software doesn't always rely on phishing links, there is still a possibility of being infected with Pegasus software and other potential threats when you click on phishing links or deceptive SMS messages. Never click on links from unknown sources, and be cautious even with text messages that appear to come from friends or legitimate services. When in doubt, verify the source before interacting.
Review and limit app permissions regularly
Many apps request access to sensitive information such as your microphone, camera, location, or contacts. Regularly check which apps have these permissions and revoke any that aren’t necessary. Limiting app access reduces potential entry points for spyware and keeps your personal data safer.
- Review app permissions regularly: Go to your phone’s settings and check which apps have access to sensitive data. On iPhone and Android, go to Settings> Privacy and Security / Privacy and select Permissions Manager on Android. On both devices, choose a category (like camera, microphone, or location) and then review all apps that have requested this permission. Toggle off access for any apps you don’t want to allow.
- Be cautious with new apps: Before installing, check what permissions the app requests. Avoid apps that ask for more access than necessary.
- Update apps responsibly: Keep apps updated, but always review permission changes after updates.
- Uninstall unused apps: Apps you no longer use can still have active permissions. Removing them reduces potential vulnerabilities.
Block Pegasus software before it hits with Bitdefender
Your phone holds your world. It stores sensitive text messages, photos, passwords, and even corporate data. But all these can fall into the wrong hands if your device gets infected by spyware. Detecting these threats early and securing your phone is the only way to stay safe. So, remember to:
- Monitor your phone for unusual activity like rapid battery drain, unexpected backups, or suspicious app behavior to catch potential spyware before it escalates.
- Use trusted security apps to scan, detect, and remove malware. Also, maintain strong passwords and two-factor authentication for added safety.
- Regularly update your operating system and apps to patch vulnerabilities that spyware could exploit, so your device stays resilient against sophisticated attacks.
Protecting your device is much easier with a security tool like Bitdefender. Once installed on your iOS or Android device, it can quickly detect threats and safeguard all your personal information from malicious actors. Consider downloading it today to take full control of your privacy.
tags
Author
The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsYou might also like
Bookmarks


