Can iPhones Get Viruses? Security Experts Answered [+Warning Signs]
![Can iPhones Get Viruses? Security Experts Answered [+Warning Signs] Can iPhones Get Viruses? Security Experts Answered [+Warning Signs]](https://blogapp.bitdefender.com/hotforsecurity/content/images/size/w600/2025/10/iphone_virusart.png)
The most fascinating shift we've seen in cybersecurity over the last few years is that attackers have realized it's infinitely easier to fool a person than to break a billion dollars' worth of encryption. So when people ask me, 'Can iPhones get viruses?'... it feels like a question from five years ago. The game has completely changed.
While Apple has built one of the most secure operating systems in the world with iOS, it cannot prevent iPhone users from being tricked into willingly opening malicious apps.
What our Bitdefender Labs see playing out millions of times a day are attacks on your trust, through phishing and suspicious apps.
So, we won't give you a simple yes or no, but something much more valuable: our playbook. You'll learn how to diagnose the subtle signs of a compromise and the exact protocol to follow to take back control.
The 5 Most Common Ways Your iPhone Gets Infected
So, how does an attacker actually get onto a device as secure as an iPhone? Let's be very clear. They look for ways around the security Apple builds into iOS. They exploit behaviors, overlooked settings, and the blind spots in the ecosystem itself.
Here are the five most common vectors we see in the market right now and you should look for when removing hackers from your phone.
1. Zero-click & zero-day exploits

This is the most sophisticated threat, and it's even used for targeted espionage. Attackers use 'zero-day' vulnerabilities, which are flaws previously unknown to the security community, to deliver spyware.
A 'zero-click' exploit is the most potent version because it requires no interaction from you. A malicious iMessage or a missed FaceTime call can be enough to trigger the exploit and grant an attacker complete access.
Here's how to stay ahead of zero-day vulnerabilities:
- Your primary defense is disciplined updates. Go to Settings > General > Software Update and enable Automatic Updates to receive latest version security patches as soon as they are available.
- Activate Lockdown Mode (If Necessary). High-risk individuals like journalists, activists, or executives must definitely use this feature, but we strongly advise everyone to use it for better device protection. You can find it under Settings > Privacy & Security > Lockdown Mode.
Our 2025 threat research shows that attackers are still actively exploiting zero-day flaws (most recently a WinRAR bug). The only reliable defense is a mix of fast updates, exploit protection, and continuous threat intelligence that can catch malware attacks before you even know the flaw exists.
2. Malicious QR codes (“quishing”)

The QR code has become a recent security blind spot. Its convenience is what attackers exploit, as they trick you into visiting malicious websites or iPhone malware apps. The FBI has issued public warnings about this trend, and our own telemetry confirms its explosive growth.
The scam is simple: an attacker places a malicious QR code sticker over a legitimate one on a parking meter. You scan it and are taken to a perfect clone of the city's payment portal, where your sensitive data, like financial info, is stolen.
To combat this mechanism, preview every link. When you scan a code, your iPhone's Camera app shows a preview of the URL. Take a moment to read the website data. Only tap links with familiar, expected URLs to keep the phone safe. If the preview uses a URL shortener, run it through Scamio before opening.
"Your phone's camera can show you a link, but it can't determine intent. The safest approach is to use an AI-powered analysis tool like Scamio. It's free and acts as a crucial second opinion, analyzing the link for you and flagging known phishing sites before you visit them." — Alexandru Cosoi, Chief Security Strategist at Bitdefender
3. Sideloading via malicious profiles
App Store is a walled garden, but attackers persuade you to install Configuration profiles that can force the iPhone to trust malicious apps or even enroll the device into a rogue Mobile Device Management (MDM) system. They can accomplish this by abusing "Enterprise Certificates," which makes their malicious software appear legitimate to your iPhone.
How to audit your device:
- Navigate to Settings > General > VPN & Device Management. This is the only place profiles can be installed.
- Review the list. If you see an Apple ID profile you did not knowingly install from a trusted administrator (like your work IT), it should be considered hostile.
- Tap the profile and select "Remove Profile" to delete it.
4. Malicious calendar invites & AirDrop spam

This vector turns the iPhone's helpful, integrated features into a channel for harassment and phishing. A spammer can send a calendar subscription that floods your Calendar app with fake events and malicious links. Even after you delete the source email, the events may remain and push phone viruses.
Here's how to combat this approach:
- Turn off your AirDrop. Before entering a crowded public space, open your Control Center, long-press the connectivity quadrant, tap AirDrop, and set it to "Contacts Only" or "Receiving Off."
- Remove calendar spam. For a single event, tap the event, then select Delete Event. If the sender is unknown, you can also choose Report Junk. For an entire calendar, tap Calendars at the bottom of the screen, then the info (i) icon next to the unwanted calendar, and select Delete Calendar or Unsubscribe.
The safest action is to delete the entire subscribed calendar without interacting with the event's suspicious link. A common mistake is to tap 'Decline' on a spam event. This action confirms to the spammer that your account is active, which will only lead to more spam.
5. Compromised Wi-Fi networks
The most common threat is an "Evil Twin" attack, where a hacker sets up a malicious hotspot with a legitimate-sounding name like "Airport_Free_WiFi." If you connect, all your unencrypted traffic is routed through their servers. This allows them to capture logins, session cookies (AKA your history and website data, browsing history), and other sensitive information.
Here's how to stay safe on Wi-Fi:
- Verify the network. Ask an employee for the exact name (SSID) of the official guest Wi-Fi before connecting.
- Disable auto-join. Go to your Wi-Fi settings for any public network and turn off "Auto-Join" to prevent your phone from connecting to it automatically in the future.
- Encrypt your connection. A VPN is non-negotiable digital hygiene in these environments. Bitdefender Mobile Security includes a high-speed VPN for this exact purpose, shielding you from these common threats.
Top 7 signs of an iPhone virus to know ASAP
So, how would you even know if your device is compromised? Malware on an iPhone doesn't announce itself with a big pop-up that says 'You're Hacked.' However, it mimics the symptoms of other problems like a bad network connection, a buggy app, or an old battery.
Here is the diagnostic checklist our security analysts recommend when investigating a potentially compromised device.
1. Sudden and severe battery drain
Every app uses power, but malware is exceptionally greedy. Malicious processes running constantly in the background, such as spyware transmitting your data or adware fetching new ads, consume enormous amounts of CPU cycles. Viruses and malware burn through your battery at a rate that is completely out of line with your actual Apple device usage.
Here's how to investigate malicious activity:
- Go to Settings app > Battery.
- Scroll down to the "Activity by App" chart.
- Look for apps with high percentages of background activity, like ones that have no reason to be running when you're not using them. A weather app running for 8 hours in the background is not normal.
2. Unusually high data usage

Spyware and info-stealing malware are useless unless they can send the data they've collected back to the attacker's command-and-control server. This transmission of your photos, messages, contacts, or other data consumes a significant amount of your mobile or Wi-Fi data allowance.
How to investigate increased data usage:
- Navigate to Settings > Mobile Service.
- Scroll down to see the data usage statistics for each application. Click "Show All".
- Look for anomalies in data usase, a suspicious new app or weird app icon, etc. A simple utility or a game you barely play should not be consuming gigabytes of data.
3. Constant app crashes & overheating
A virus from an iPhone can conflict with iOS, other applications, or itself. This conflict consumes excess resources and causes apps to freeze or crash. This constant, inefficient processing also generates a noticeable amount of heat. That's how you know your iPhone has a virus.
4. Unexplained pop-ups or ads
Your iPhone's home screen and system interface should be a completely ad-free space. If you are seeing pop-up ads outside of your web browser or a specific ad-supported application, it is a definitive sign of adware. This can be installed via a rogue configuration profile or other malware, like malicious calendar subscription you accepted.
5. Apps you don't remember downloading
Fake apps could have been installed via a malicious profile that grants installation privileges, a sophisticated zero-click exploit, by someone who had physical access to your unlocked device, or even you (unknowingly).
How to check iOS devices for malware infection via a strange app:
- Do not just scan your home screen folders. Swipe to the very end of your home screens to open the App Library.
- Browse the alphabetical list or the automatically generated categories for any app you do not recognize.
- Tapping "delete app" will however solve the issue partially, if third party sources installed malicious code when downloading apps or via links you clicked.
On a standard, non-jailbroken iPhone, deleting an app is highly effective at removing the app itself and its immediate data. Apple's iOS is built on a "sandboxing" model, which means every app runs in its own isolated, secure container. When you tap "Delete App," you are deleting that entire container.
But if the app tricked you into installing a configuration profile (under Settings > General > VPN & Device Management), that profile remains even after the app is gone. This profile could still be redirecting your web traffic, browser history, or monitor your data.
Furthermore, deleting the app does nothing to undo the damage that has been done. Before you removed it, the app could have already exfiltrated (stolen and sent) your contacts, photos, or credentials to an attacker's server.
Alexandru Cosoi, Chief Security Strategist at Bitdefender, advises, "This is a must-have check if you've bought a secondhand iPhone. The previous owner could have jailbroken the device and installed deep-level spyware that persists even after a simple reset. If you find an unfamiliar app, the safest course of action is a full factory reset of the device."
Stop cleaning up damage after the fact. Bitdefender Mobile Security for iOS offers malware protection and scam links before they can infect your device. Get proactive protection. Stop malware infection today.
6. Your iPhone is "jailbroken" without your knowledge

Jailbreaking removes Apple's ecosystem of core security protections. It gives applications dangerous levels of access to your data and the iOS operating system itself.
How to investigate for jailbroken iPhones:
- Use the search bar on your home screen (swipe down from the middle).
- Search for apps that are hallmarks of a jailbroken device, such as Cydia, Sileo, or Checkra1n. Their presence is definitive proof.
7. Strange outgoing calls or account activity
A compromised device can be added to a botnet to send spam text messages, make fraudulent calls to premium-rate numbers, or be used to intercept two-factor authentication codes to take over your other online accounts.
How to check for strange activity:
- Check your "Sent" folder in Messages and your "Recents" list in the Phone app for any activity you don't recognize.
- More importantly, cross-reference this with your official phone bill from your carrier, which provides an undeniable log of all billable activity.
How to get rid of viruses (an emergency action plan)
If you've identified the signs of a compromise, follow this protocol to clear malware from your device. Start with the least invasive steps and proceed only if the problems persist and you can’t get rid of the virus.
Step 1: Clear your browser and restart
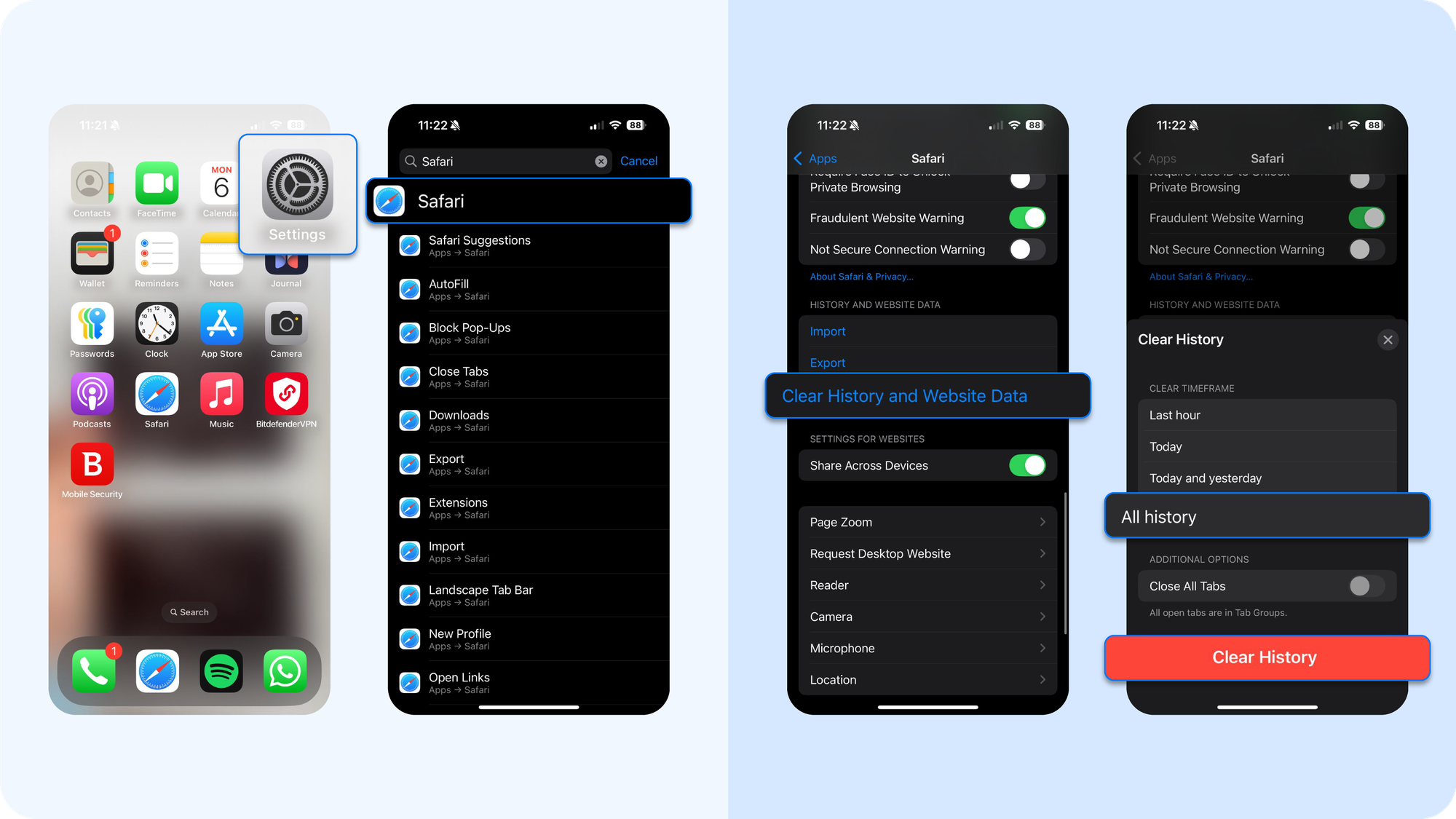
Malicious code can reside in your browser's cache from unsafe websites.
- First, open Settings and tap Safari.
- Scroll down and tap Clear History and Website Data. This is the simplest way to clear history and remove lingering scripts.
Next, perform a full restart. Press and hold the side power button and a volume button, then slide to power off.
Step 2: Restore from a clean backup
If the issue continues, your next step is backup restoring. This can revert your phone to a state before the infection occurred.
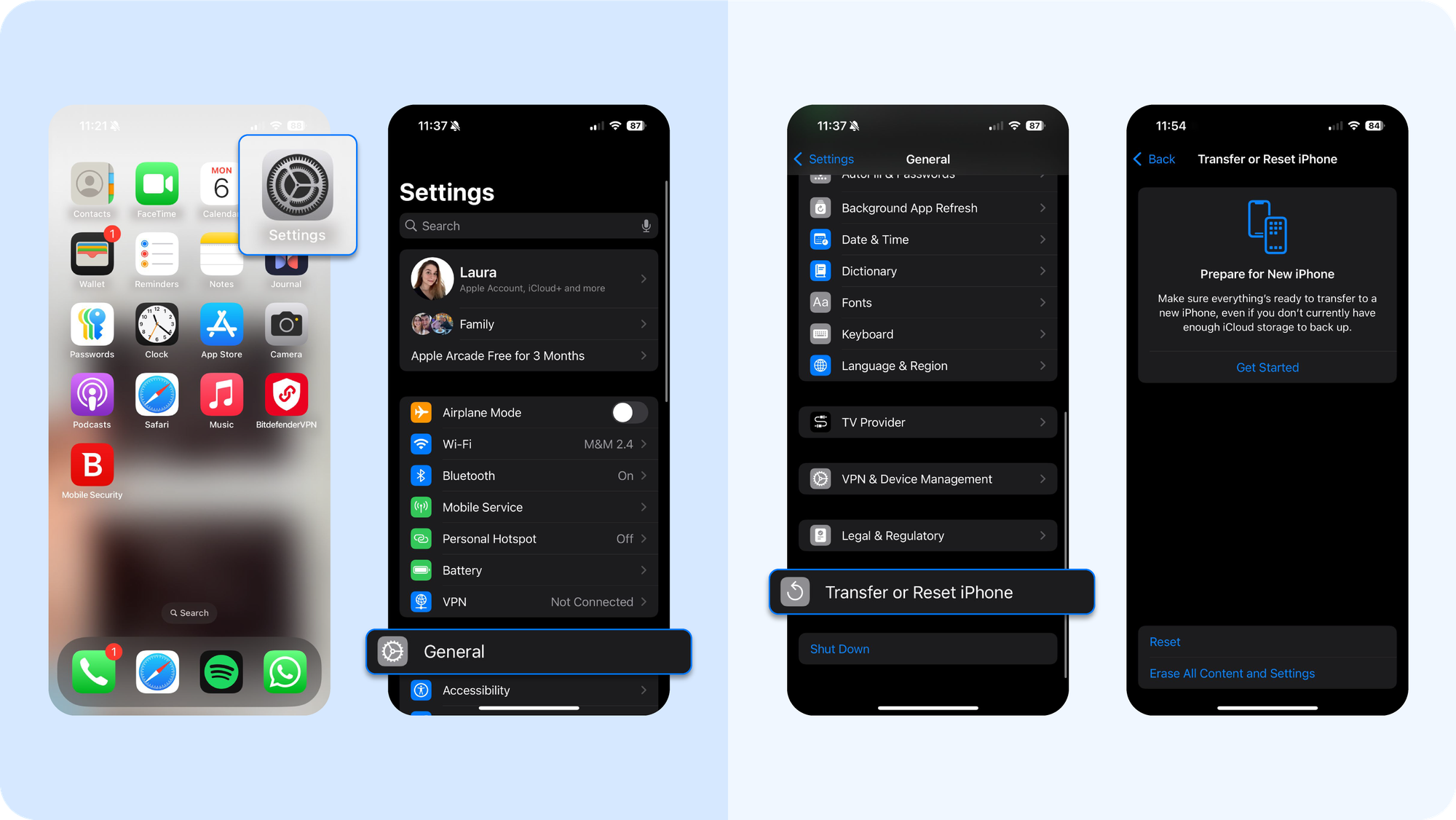
- Go to your Settings > General > Transfer or Reset iPhone
- You can access your iCloud backup from here during the setup process after erasing.
- The key is to select a previous backup from a date before you noticed any problems. Choose an earlier backup version to avoid restoring the malware along with your data.
Step 3: Reset to factory settings
If you have no clean backup or if restoring doesn't solve the problem, the only way to be certain you get rid of viruses is a full reset. This is the ultimate way to get rid of a persistent infection.
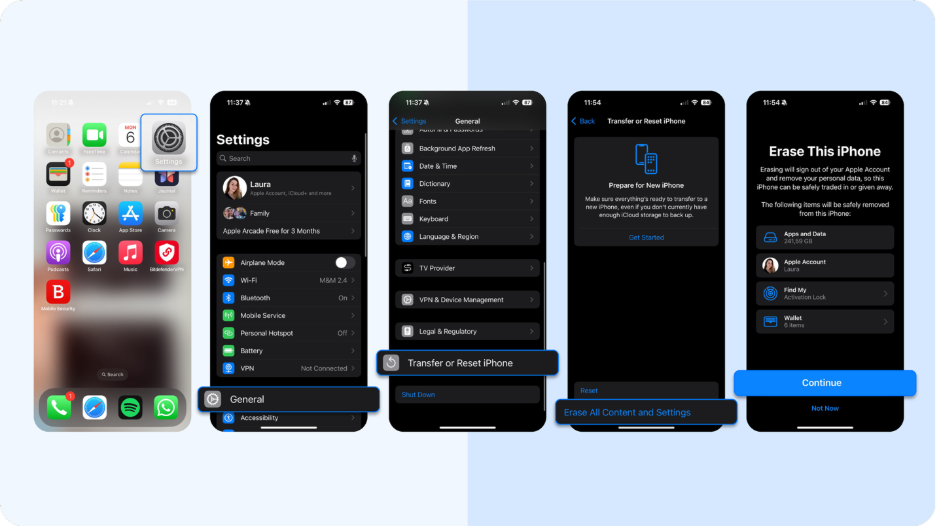
- Navigate to Settings > General > Transfer or Reset iPhone.
- To proceed, tap Erase All Content and Settings.
This action will wipe the device completely and return it to its original factory settings. It removes everything, including the malware, and revokes all app permissions to sensitive information like your location data, protecting your mobile device from other online threats.
How to Protect Your iPhone From Future Threats
So, we've covered the diagnostics. Now let's talk about defense.
Enable automatic updates
This is the single most critical security habit you can adopt. The high-stakes race between Apple's engineers and global attackers is fought in software updates. When a zero-day is discovered, hackers immediately weaponize it against any device that is unpatched. Delaying an update is like leaving a known, unlocked entrance to your digital life. Follow these steps:
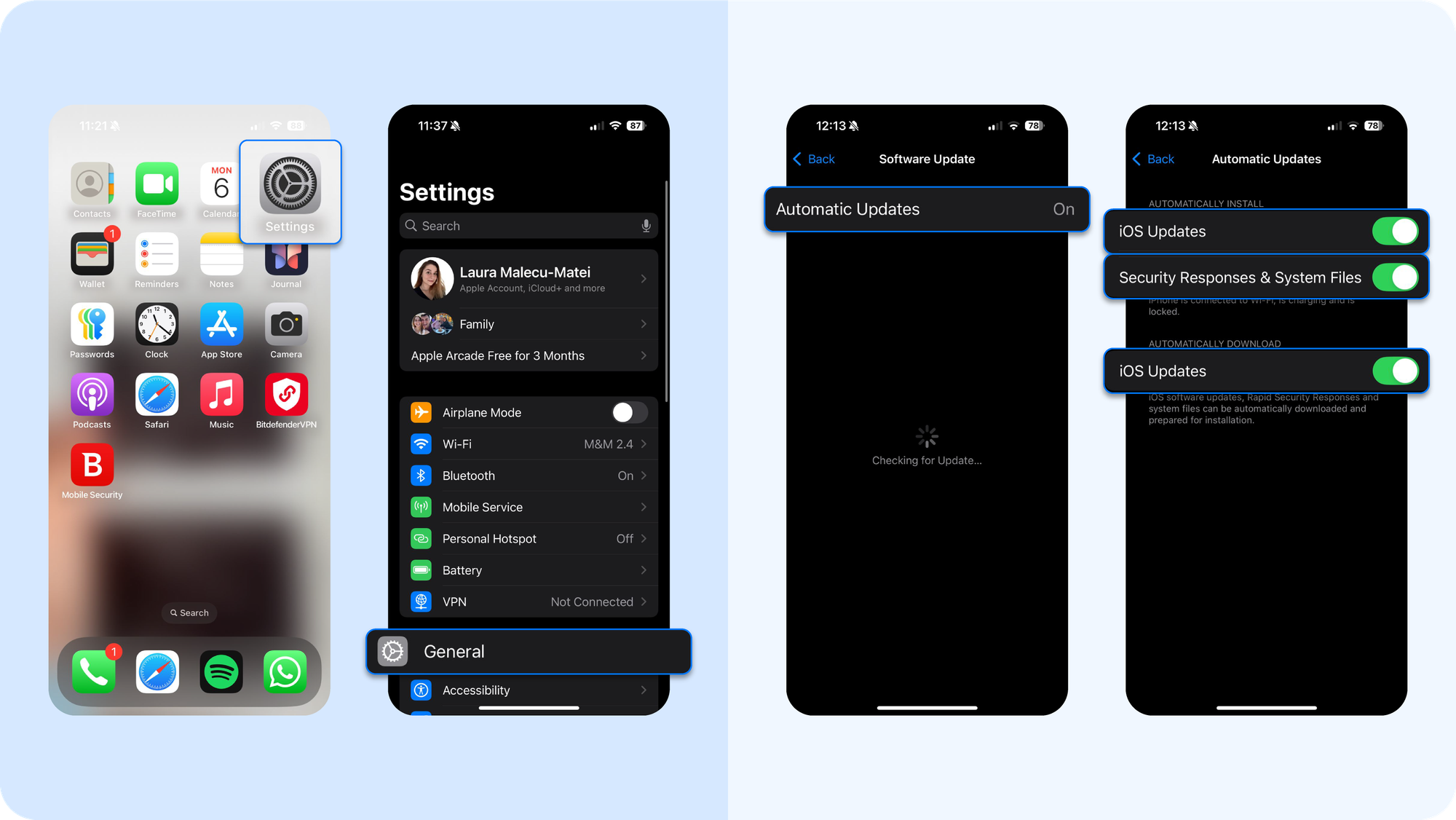
- Open Settings > General > Software Update.
- Tap on Automatic Updates.
- Make sure both "Download iOS Updates" and "Install iOS Updates" are toggled on. This allows your iPhone to download and install critical security patches overnight while it charges.
Use a VPN on public Wi-Fi
Follow these steps:
- Install a reputable VPN application from the App Store.
- Before you start browsing on any public Wi-Fi, open the VPN app and activate the connection with a single tap. All your internet traffic will then be routed through a secure, encrypted tunnel.
PS: Bitdefender's iOS security app has a built-in VPN offering up to 200MB of traffic per day. Learn more about the antivirus app.
Use a trusted security tool for iOS
Apple designs iOS to be resilient, but it won’t stop a convincing phishing page or a malicious profile. Bitdefender Mobile Security adds real-time web protection, link scanning, and an integrated VPN so bad links and unsafe Wi-Fi are blocked before they become incidents.
Apple can't stop you from being tricked into clicking on suspicious websites and apps. That's the gap a tool like Bitdefender fills. Instead of having to remove viruses, invest in prevention tactics and tools.
Activate lockdown mode (for high-risk users)
This is an extreme security measure, but it is a critical one for those who may be personally targeted by sophisticated spyware. Lockdown Mode works by drastically reducing the "attack surface" of your device, disabling features that are often targeted by advanced exploits.
- Navigate to Settings > Privacy & Security > Lockdown Mode.
- Read the description carefully to understand the features that will be limited (e.g., link previews in iMessage, certain web technologies, incoming FaceTime calls from unknown numbers).
- If you believe your public profile or work makes you a target, use it. It's an effective, free threat protection tactic that doesn't require installing a new iPhone app.
Practice "zero trust" with links & QR codes
"Zero Trust" is a core cybersecurity principle that means you should never trust by default, and always verify. Apply this mindset to every link, QR code, and attachment you receive. Treat them as potentially malicious until you can prove otherwise. Hover over links to review their URL, inspect any domain or email sender twice before clicking, and overall have a preventative mindset.
PS: For any suspicious link, use a free tool like Scamio to get an objective analysis before you click.
Remove a virus or prevent your mobile device from ever getting it in the first place? If you're serious about iPhone security, give Bitdefender a try.
tags
Author
The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsYou might also like
Bookmarks


