Bitdefender Threat Debrief | November 2025

The ALPHV Insiders: Cyber Defenders Who Cast a Shadow on Enterprise Security
This edition of the Bitdefender Threat Debrief includes coverage on the indictment of ALPHV affiliates, Qilin’s exponential growth, Sinobi’s return to our Top 10, and more.
As ransomware continues to evolve, our goal with this monthly Bitdefender Threat Debrief is to help you stay ahead of the curve. To do this, we combine information from openly available sources (OSINT) - things like news reports and research – with data we gather by analyzing Data Leak Sites (DLSs), websites where ransomware groups post details about their victims. It is important to remember that we can't independently verify all of these claims but are confident in the trends we see over time.
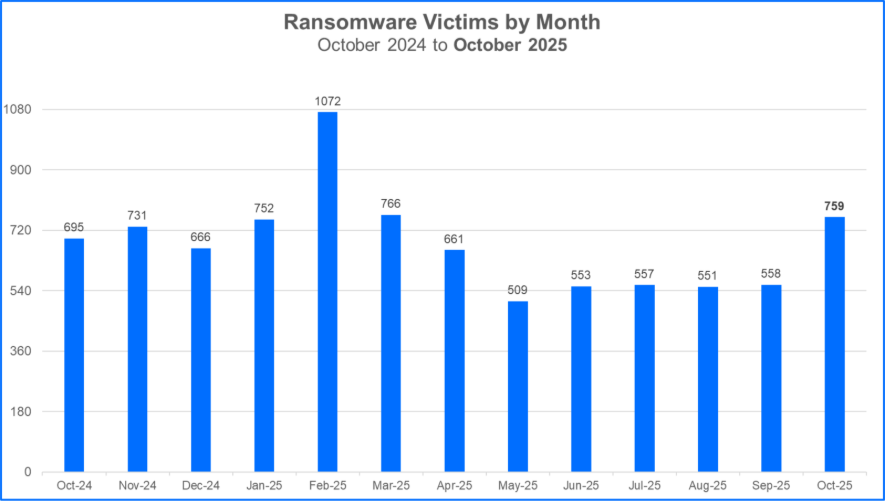
For this month's report, we analyzed data from October 1 to October 31 and recorded a total of 759 claimed ransomware victims. This is the third-highest month for the number of claimed victims within the past year.
Featured Story: The ALPHV Insiders: Cyber Defenders Who Cast a Shadow on Enterprise Security
What Happened?
In October, three individuals connected to the ALPHV ransomware group were indicted in the United States. ALPHV, also known as BlackCat rose to prominence in 2023. The group claimed more than 400 victims that year, accumulating sizable ransom payments, totaling hundreds of millions of dollars. The road to the indictments started in December 2023 when ALPHV’s infrastructure was seized by the FBI as a result of an OPSEC failure. Although the group continued to execute ransomware campaigns in early 2024, ALPHV’s activities ceased in September that year.
The individuals indicted were identified as insiders who worked incident response duties for cybersecurity firms, yet still joined an ALPHV affiliate group to support ransomware campaigns against U.S. organizations.
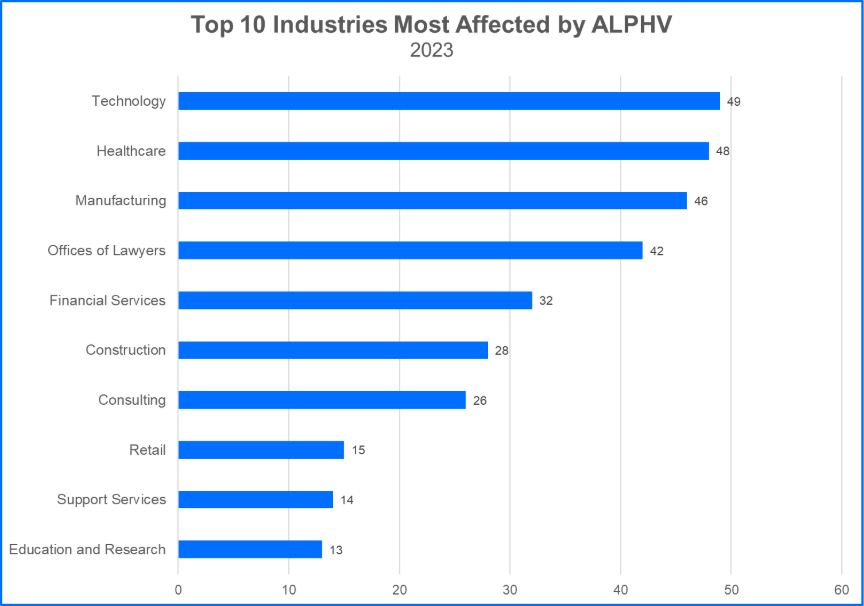
The parties identified, Clifford Goldberg and Kevin Tyler Martin, are U.S. citizens who could face a minimum of 20 years in prison for damage to protected systems and conspiracy to commit extortion. Two of the three indicted individuals were likely still employed as cybersecurity managers during their time aiding ALPHV, and one was a former employee of a cybersecurity firm. The affiliate members leveraged their technical expertise in ALPHV’s RaaS operations between May and November 2023. ALPHV claimed 278 victims during this timeframe, including organizations in the technology, healthcare, and manufacturing industries. These are all sectors with an increasing need for security resources and staff.
How Cybersecurity Insiders Can Help a Ransomware Group
When identifying the ways insiders can support a ransomware group, interesting scenarios emerge. Technical knowledge is often the first area to come to mind as an advantage. It’s true that developing APIs and tools to boost the functionalities of a group’s infrastructure can create significant opportunities for an adversary to strengthen their capabilities. The same can be said for knowledge transfer in cases where insiders share information about the mechanisms that operate within a specific security stack, or about anti-virus technologies and workarounds to evade detection.
A security professional’s familiarity with organizational policies and breach notification rules and regulations is equally beneficial. ALPHV was one of the first groups that introduced a different type of extortion-one that involved threats and reports to third parties such as the U.S. Securities and Exchange Commission (SEC). When organizations failed to notify such authorities of a cyber incident, the cybersecurity insiders could have helped convince leadership to submit payment to ransomware groups, especially in circumstances where other staff may not understand recovery methods and the ‘safety nets’ upheld by keeping secure data outside of the immediate compromised ecosystem. If no other options are communicated to leadership or legal teams, they may feel immense pressure to concede to ransom demands.
What Are the Lessons Learned?
No environment is immune to the insider threat. An emphasis on detecting and hunting external adversaries presents major gaps in risk assessment programs. The indictment of the ALPHV affiliate staff underscores the importance of maintaining and hardening defenses against all threat types. Multiple strategies can be implemented to proactively combat insider threats, including the following:
- Limit the systems that staff may access based on the principle of least privilege
- Enforce monitoring logging across administrative functions, ensuring alerting is also in place for events that include log-ons, data transfers, deletion or modification activities, etc.
- Establish training to educate staff about insiders and communicate protocols for reporting unusual activity
Other Notable Ransomware News
Now, let’s explore the notable news and findings since the last Threat Debrief release
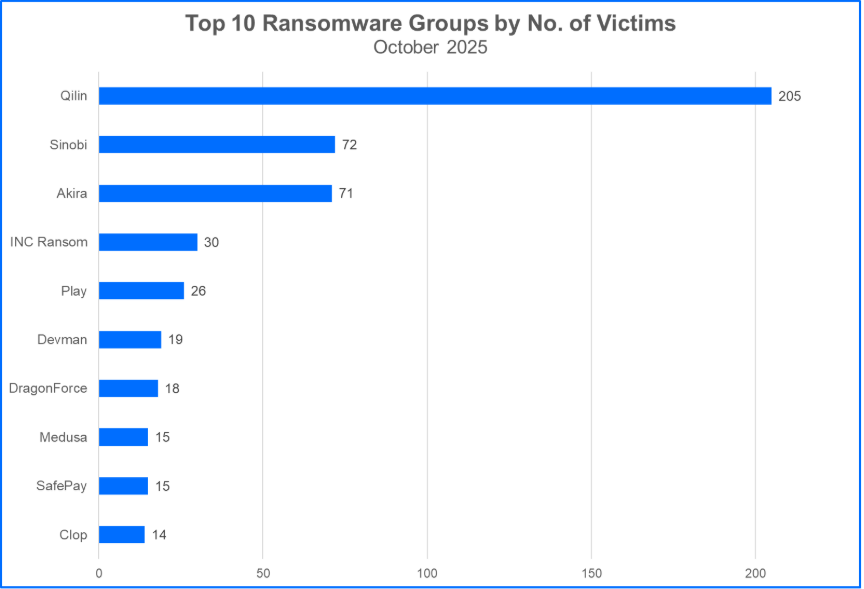
- Qilin ranks in the Top 10 for the sixth consecutive month: Qilin claimed 205 victims in October, which is a significant increase from their 96 victims reported in the last release. We have not seen the total number of victims claimed by an individual group exceed 200 since Clop’s milestone of surpassing 300 victims in February this year. As 2025 Q4 approaches its midpoint, QIlin’s presence and expansion puts both competing groups and victim organizations at risk.
- Bitdefender monitors campaigns targeting WSUS: CVE-2025-59287 was identified in a recent string of campaigns and allows an unauthenticated attacker to send requests to WSUS; then, the attacker can execute remote code with the highest level of privileges. Readers may stay informed about how threat actors targeting WSUS, by reading the latest advisory. Organizations are advised to apply the current Out-of-Band security update to mitigate this flaw.
- Sinobi makes their return to the Top 10 groups: Sinobi ransomware claimed 72 victims in October, narrowly surpassing Akira. Sinobi’s data leak site resembles those of other groups like Lynx. These sites feature News, Leaks, and Report sections with the same gray background and similar fonts and web components. Several hypotheses explain this resemblance: it’s possible that Sinobi is a Lynx affiliate. Another hypothesis points to the group’s use of a common developer: Multiple groups may employ the same contractor to maintain their site. An additional option is that similarities in the layout of a DLS may be a threat actor’s attempt to shirk responsibility by imitating another adversary.
- Handala’s decline in activity continues: Earlier this year, Bitdefender’s 2025 Cybersecurity Predictions included the resurgence of hacktivism in combination with ransomware campaigns. Handala, a group that has claimed nearly 125 victims since 2023, has engaged in hacktivist activities targeting Israeli entities. This aligns with their pro-Palestine dogma and repeated campaign activity. While Handala’s activity saw a sharp decline in August, this does not mean that further leaks will not be publicized. It is not uncommon for campaigns with such unique targets to see dips when the focus narrows to a specific group of potential victims.
- Kazu steps in with numerous breaches: Kazu is a ransomware group that has been active since September 2025. Despite their recent emergence, the group has already leaked data from government, military, and healthcare organizations. The majority of Kazu’s current victim demographic is from Southeast Asia, the Middle East, and South America.
Top 10 Ransomware Families
Bitdefender's Threat Debrief analyzes data from ransomware data leak sites, where groups publicize their claimed number of compromised organizations. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and may be unreliable. Additionally, this method only captures the number of victims claimed, not the actual financial impact of these attacks.
Top 10 Most Attacked Countries
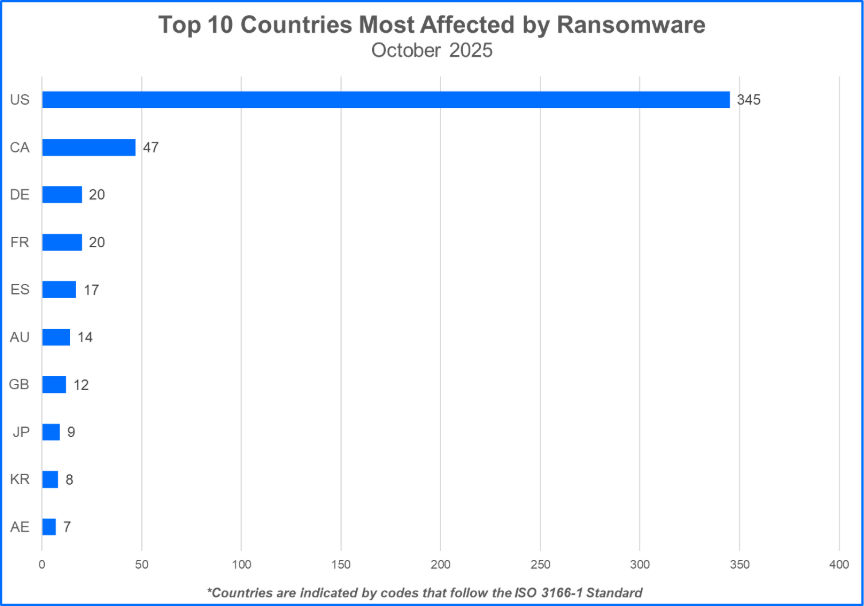
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. In many cases, this means focusing on developed countries with higher projected growth rates. Threat actors may also execute strategic attacks that unfold during geopolitical conflicts or periods of social unrest. Let’s see the top 10 countries that took the biggest hit from ransomware attacks.
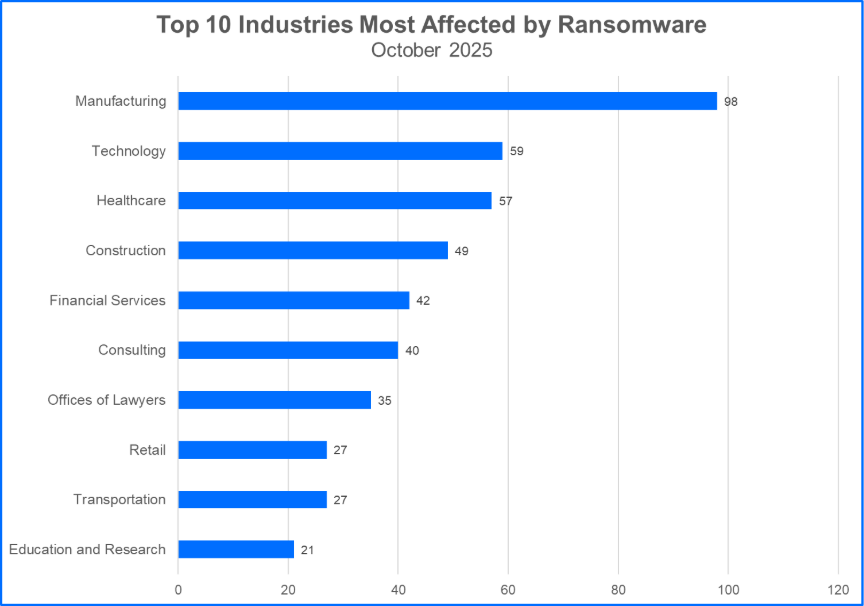
Top 10 Most Attacked Industries
Ransomware gangs may target organizations in critical infrastructure sectors, select organizations that offer services tailored to the consumer marketplace, or choose to attack organizations that fall into both categories. Understanding the trends and ramifications associated with specific industries, and how specialized services and clientele may be impacted, is crucial to assessing risks and anticipating incidents that may occur. Here are the Top 10 industries affected by ransomware groups.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed Bitdefender technology and added it to their product or service offerings. This vast OEM ecosystem complements the telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discovers 400+ new threats each minute and validates 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Gabriel Macovei, Andrei Mogage, and Rares Radu (sorted alphabetically) for their help with putting this report together.
tags
Author
Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsYou might also like
Bookmarks

