AV-Comparatives Analysis: GravityZone Stops C2 Attacks

For organizations supporting hybrid and remote staff, the traditional network perimeter is no longer sufficient. This operational shift demands that security solutions offer comprehensive protection at the endpoint that extends deep into network traffic analysis, particularly against malicious egress connections—traffic moving from the inside-out.
Understanding this security challenge, Bitdefender developed GravityZone Network Attack Defense. It acts as a secure web gateway on each endpoint that performs deep-packet inspection of network traffic on endpoints and identifies activity associated with malicious intent.
NAD monitors a variety of protocols including (IPv4/IPv6), Transport (TCP/UDP), and Application levels including HTTP(S), SSL, SCP/SSH, (S)FTP, RDP, DNS, Telnet, SMB (including Samba-based subprotocols such as RPC), and several others. It blocks activity based on many factors including reputation-based analysis (IP/Domain/URLs that are known to be malicious), as well as performing behavioral analysis on the network traffic. This network inspection is done in nanoseconds, without slowing network speeds or interrupting productivity.
Third-Party Validation Results
In AV-Comparatives NGFW Egress C2 Certification Test, GravityZone demonstrated absolute protection against Command-and-Control (C2) connections, and it was the only vendor certified to do so during the 2025 tests. The inclusion of this unique technology as part of the core endpoint protection prevents targeted attacks and Advanced Persistent Threats (APTs) that are expertly engineered to bypass initial defenses to allow threat actors to take control of an organization’s entire network.
The Danger of Allowed Egress C2 Connections
When an attacker successfully compromises a single device, their main objective is to establish a hidden channel back to their server. This connection, commonly known as a command-and-control (C2), enables the threat actor to perform a litany of activity – including running reconnaissance, planting ransomware, exfiltrating files, and setting the stage for supply chain attacks.
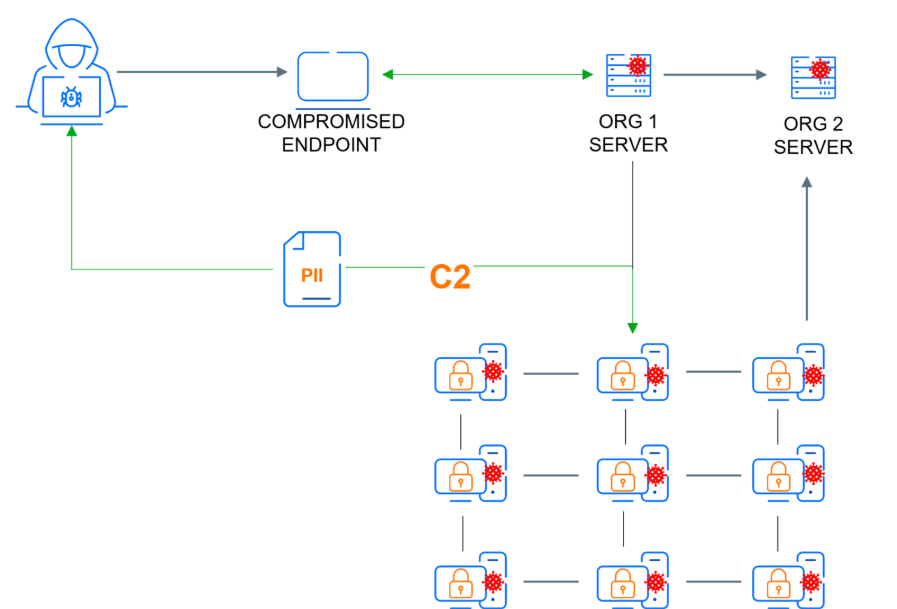
Figure 1: Using a single compromised endpoint, an attacker can infiltrate an organization and its partners
While traditional firewalls often excel at blocking outside-to-inside attacks (attempts to penetrate the network), C2 channels are characterized by traffic flowing from inside to outside (egress). If this connection is established and not prevented by the defensive product, the attacker can leverage the C2 channel for post-exploitation activities using the appropriate C2 framework.
Endpoints aren’t the only targets, however, as edge devices can also be exploited by threat actors to establish a foothold into an organization’s network. Protecting devices that fall outside of an organization’s network perimeter is especially challenging.
Effective protection must therefore focus on the outgoing network traffic prevention and detection capabilities in the context of well-known C2 products and C2 ransomware profiles. Successful solutions must address the problem at the network level, scanning the encrypted traffic due to the prevalence of HTTPS usage. These must also be independent of perimeter defenses, which are typically ill-equipped to protect remote workers.
Setting a New Standard for Network Defense
To validate the resilience of this crucial second line of defense, Bitdefender recently participated in the NGFW Egress C2 Certification Test conducted by AV-Comparatives. This certification focused on measuring the effectiveness of products’ capabilities to prevent and detect outgoing network traffic. Many vendors are invited to participate in these very specific tests AV-Comparatives performs periodically, but only those that achieve perfect results are certified.
Crucially, the testing methodology was designed to evaluate network-layer protection in isolation, ensuring that results were not dependent on traditional execution-prevention features. For the certification test, AV-Comparatives set strict parameters:
- AV, EPP, and EDR evaluation as the first line of defense were explicitly out of scope.
- Endpoint protection-related modules or features were prohibited from being enabled.
- Signature-based and behavior-based malware prevention or detection features were required to remain disabled.
The test product was Bitdefender GravityZone Business Security Enterprise 7.9. In adherence with the rules established by AV-Comparatives, all related detection and protection technologies, including Antimalware, Sandbox Analyzer, Exchange Protection, Antispam, Incident Sensor, and fileless attack protection were disabled.
The only technology allowed to be active was Network Attack Defense, and all detected activity was set to block. Utilizing real-time stream processing, Network Attack Defense (NAD) provides continuous traffic inspection. Its operational state is determined by the deployment configuration: inline integration within Bitdefender Endpoint Security (available for Windows, macOS, or Linux), tap-mode for Bitdefender XDR network sensing, or PCAP mode for capturing packets for subsequent analysis. For this test, it operated in inline mode as part of Bitdefender Endpoint Security.
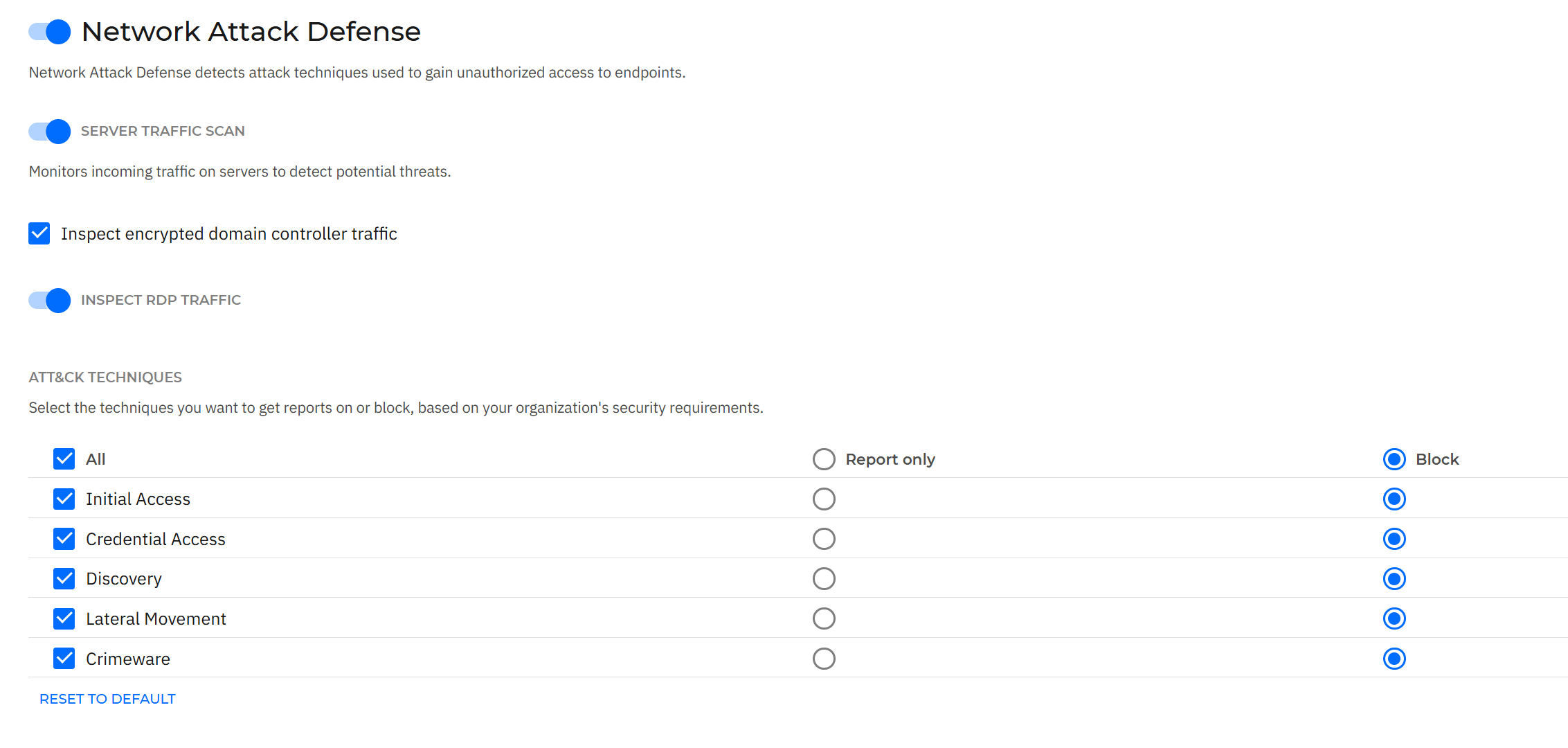
Figure 2: GravityZone Network Attack Defense is designed to thwart advanced network attack techniques, independent of network connection
The configuration, which isolated only the network protection features, meant that the solution was tested only on its ability to detect and prevent C2 communication based on network traffic characteristics, regardless of whether the initial infection successfully launched.
To be approved for the AV-Comparatives NGFW Egress C2 certification, the product had to block all malicious traffic scenarios executed during the test. Bitdefender GravityZone Business Security Enterprise successfully reached the certification requirements by blocking all the malicious traffic used in this test.
This included blocking various HTTP command and control traffic profiles such as Meterpreter, Emotet, Trickbot, Havex, Gandcrab, and Bazarloader. In the test cases involving Gandcrab and Bazarloader, a stable C2 channel could initially be established. However, even in these instances, all post-exploitation communication was successfully blocked by Bitdefender’s network defenses.
GravityZone Stands Alone
GravityZone was the only product to receive the AV-Comparatives certification in this specialized evaluation this year. GravityZone Network Attack Defense technology unilaterally prevents stable C2 channels and blocks subsequent post-exploitation communication—even when all other endpoint defenses were intentionally deactivated.
These independent testing results provide confidence that an organization’s critical assets remain protected even against advanced threats designed to bypass multiple layers of initial defense. This isolated validation confirms that the network-based C2 prevention layer functions as a robust and essential safeguard against emerging threats in today's distributed IT environments.
Learn more about the GravityZone unified security platform or contact us to schedule a demo to see how GravityZone can align with the needs of your organization.
tags
Author
My name is Richard De La Torre. I’m a Technical Marketing Manager with Bitdefender. I’ve worked in IT for over 30 years and Cybersecurity for almost a decade. As an avid fan of history I’m fascinated by the impact technology has had and will continue to have on the progress of the human race. I’m a former martial arts instructor and continue to be a huge fan of NBA basketball. I love to travel and have a passion for experiencing new places and cultures.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











