Field Test: Setting Up Split Tunnels Over Satellite for Real-World Use

How to make a VPN play nice with Starlink and other satellite links without slowing everything to a crawl.
Why split tunneling matters on satellite
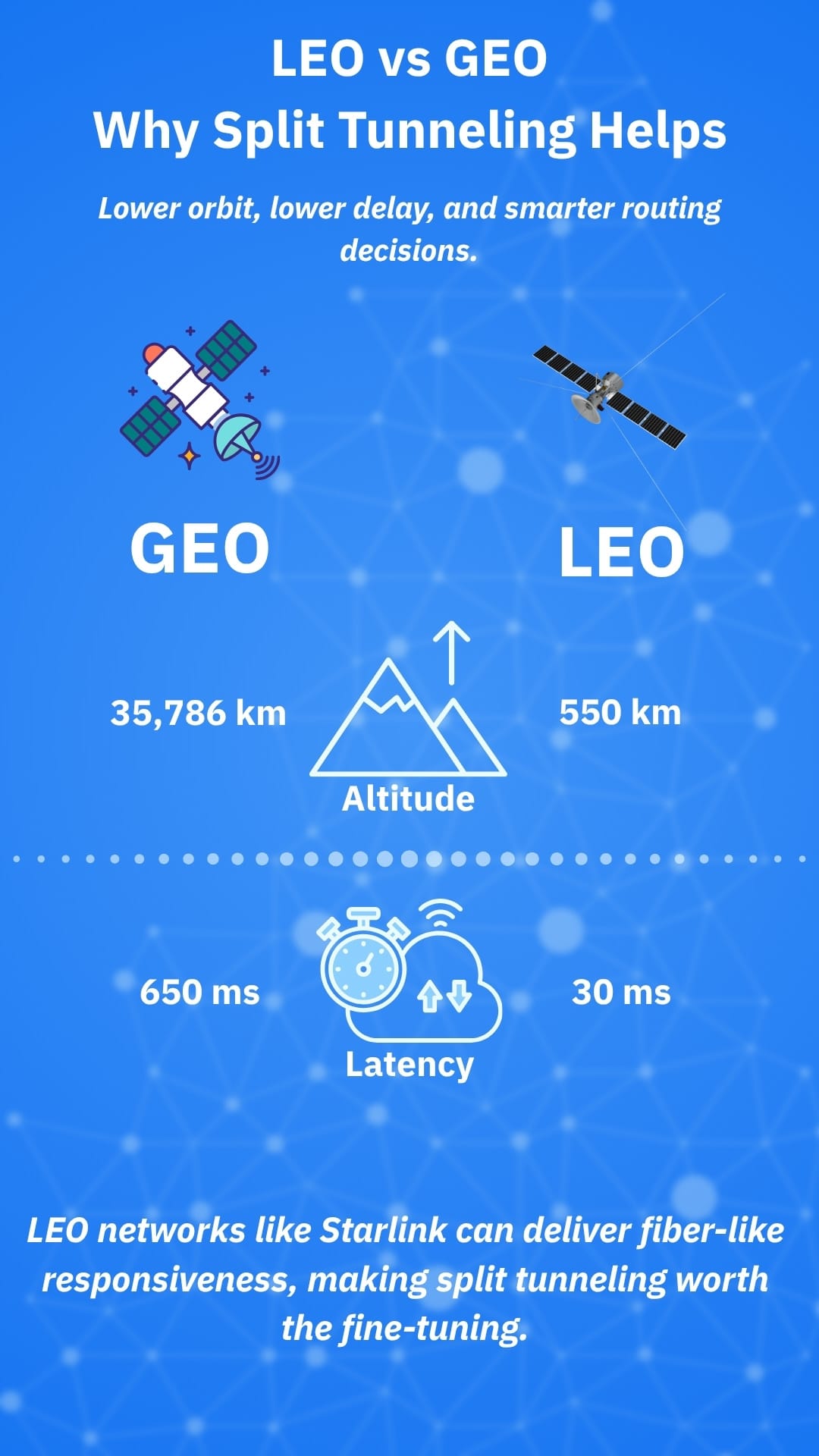
Satellite is no longer just a backup link. Low-Earth orbit (LEO) services can deliver fiber-like responsiveness for many users (often in the tens of milliseconds), while legacy geostationary (GEO) links still sit in the ballpark of 600 ms.
That latency delta changes what “good” VPN design looks like: you want security where it counts, without forcing all traffic through a long round trip. That’s exactly what split tunneling does: route sensitive or geo-restricted traffic through your VPN, and let everything else go straight to the World Wide Web.
Security note: regulators and government baselines often discourage or forbid split tunneling because it can create blind spots and backdoors if misconfigured. If you enable it, compensate with strong endpoint protection and strict whitelists.
The test scenario you can replicate at home
Goal: keep your work apps and banking inside the VPN while letting streaming, gaming and large updates use the satellite link directly for best performance.
Things you’ll need (or you can substitute equivalents):
- Satellite WAN: a consumer LEO service (e.g., Starlink)
- Router/firewall: a consumer router that supports policy-based routing and per-app/per-domain rules (many modern models do)
- VPN: use a trustworthy VPN such as Bitdefender VPN, WireGuard or OpenVPN
Why this setup: LEO latency varies by geography and time of day, but is routinely far lower than GEO. Independent measurements from Australia’s regulator found an average latency of ~30 ms for LEO vs ~665 ms for GEO, which aligns with broader observations from the Internet Society’s global tests. That means a well-tuned split tunnel can feel “local” for most browsing, while still protecting sensitive flows.
Step-by-step: make split tunneling work over satellite
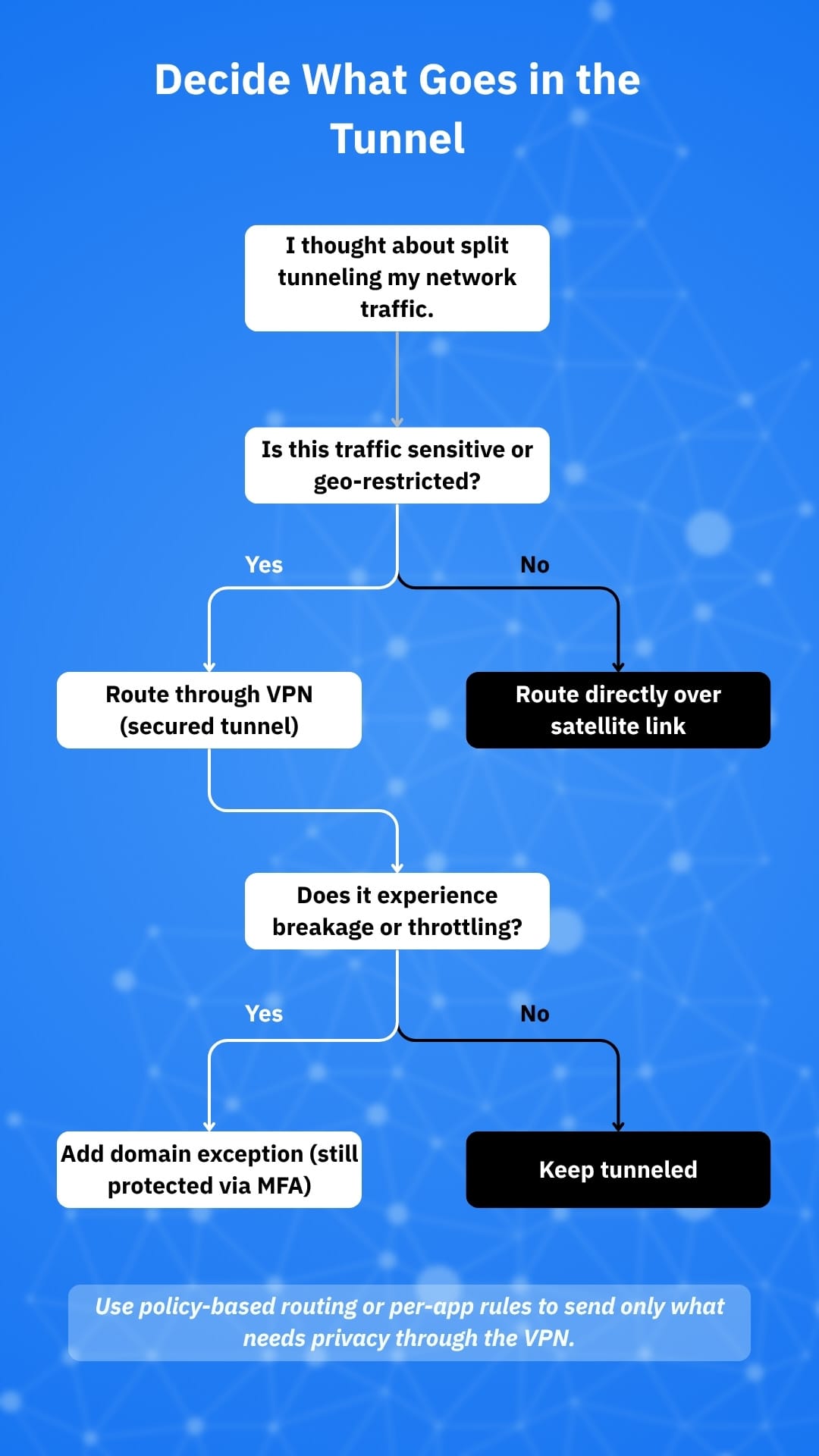
1. Map your traffic
List categories that must stay in the tunnel (work SaaS, corporate IPs, banking, remote desktop to your office, IoT admin pages) and what can go direct (streaming apps, game consoles, operating-system updates).
2. Choose the split method
On consumer gear you’ll typically see:
- Per-app rules (on the device): select apps that use the VPN client; others bypass
- Per-domain/IP policy routing (on the router): traffic to specified domains/IP ranges goes via the VPN; the rest goes direct.
If you can, prefer router-level policy routing so every device at home benefits, even those without a VPN client.
3. Prioritize whitelists, not blacklists
Route only named apps/domains through the VPN (such as your employer’s SSO, identity, and SaaS ranges). Everything else uses satellite natively. This “least-privilege” mindset is consistent with split-tunnel hardening guidance.
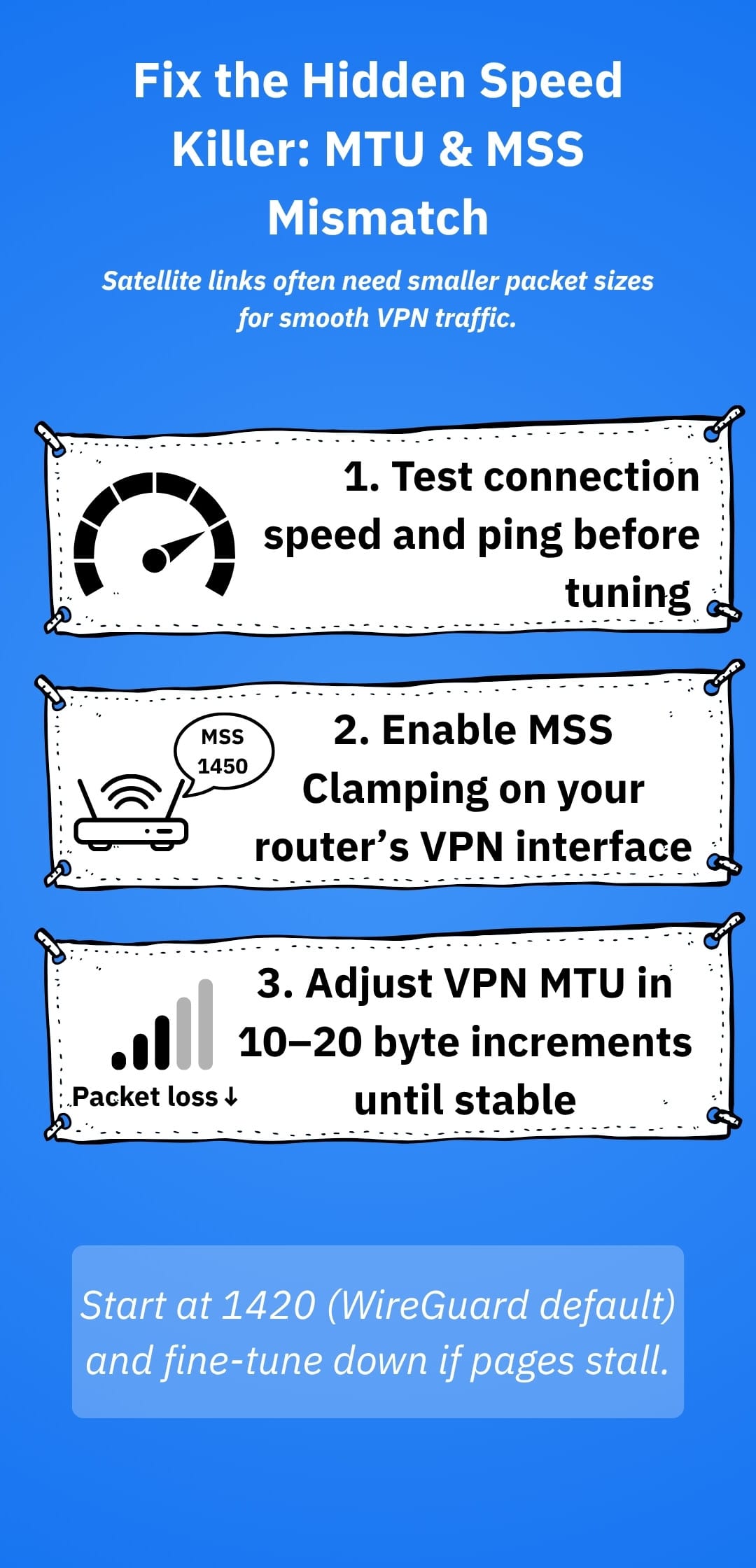
4. Tame MTU before it bites you
Encrypted tunnels add overhead. If packets exceed the path MTU they fragment or stall, causing slow pages and mysterious timeouts, especially noticeable over high-variance satellite paths. Set MSS clamping on the router’s VPN interface and, if needed, reduce the VPN MTU (common WireGuard defaults ~1420, OpenVPN often ~1500 minus overhead). Test and adjust in 10-20 byte steps until retransmits drop.
5. Prefer UDP-based VPNs
Bitdefender VPN supports multiple protocols, including WireGuard, OpenVPN and IKEv2. WireGuard’s use of UDP generally tolerates variable latency better than TCP-in-TCP. Expect throughput to dip as latency rises (window scaling and congestion control still apply) but you’ll keep jitter down versus TCP-tunneled VPNs.
6. Expect CGNAT limitations and plan around them
Most consumer satellite plans use carrier-grade NAT, which blocks inbound connections and classic port forwarding. For remote access to your home, use reverse tunnels, a VPN with hosted port-forwarding, or your provider’s paid public IP option where available. Check the provider’s official help docs and reputable workarounds before assuming you can open ports.
7. Add endpoint security to close the split-tunnel gap
Because some traffic bypasses your VPN, lean on device-level defenses, such as automatic updates, reputable AV/EDR like Bitdefender Ultimate Security or NETGEAR Armor, DNS filtering and phishing protection. This mirrors government best-practice guidance for reducing attack surface at the edge.
Field-style results to look for (and how to measure)
You can’t change physics, but you can measure and tune according to your needs:
- Latency/jitter: run ping to a public DNS and to a host behind your VPN. Expect a ~20-50 ms baseline when going direct on LEO versus notably higher once you cross continents through a VPN PoP. GEO links will be hundreds of ms regardless.
- Throughput: test with and without the tunnel using the same server region (e.g., speed.cloudflare.com, fast.com, then the provider’s test server via the VPN). The WireGuard protocol usually tracks closest to line rate, while OpenVPN may trail on CPU-limited routers.
- Page-load hiccups: if certain websites hang until refresh, lower your VPN MTU or enable MSS clamping. It’s the classic symptom of PMTU black holes.
Security pitfalls and how to avoid them
- Leaky rules: broad “allow internet” policies can accidentally expose admin pages or sensitive SaaS outside the tunnel. Fix with strict per-domain whitelists and enforce DNS over HTTPS on the router, if possible. Regulatory and standards bodies warn that sloppy split tunneling creates backdoors; treat rules like a firewall policy, not a convenience toggle.
- Management interfaces on the open web: never expose router or NAS logins for “easy remote access,” especially since CGNAT workarounds tempt people to poke holes. Use zero-trust or client VPNs instead.
- Trusting the wrong VPN: choose a vetted, trustworthy VPN for port-forwarding or exit nodes, taking logging practices and jurisdiction into consideration.
Frequently asked questions (FAQ)
Will split tunneling make streaming faster?
Often yes on LEO, because you avoid VPN detours and TCP-in-TCP overheads, so long as your satellite link isn’t congested and MTU is tuned.
Can I host services from home on Starlink?
Not with traditional port forwarding on standard residential plans due to CGNAT. Use reverse tunnels/relays or a provider-offered public IP option if available.
What about other LEO networks?
Competition is growing (e.g., Amazon’s Project Kuiper), but consumer availability and performance are still evolving; Starlink remains the most widely deployed consumer LEO option today.
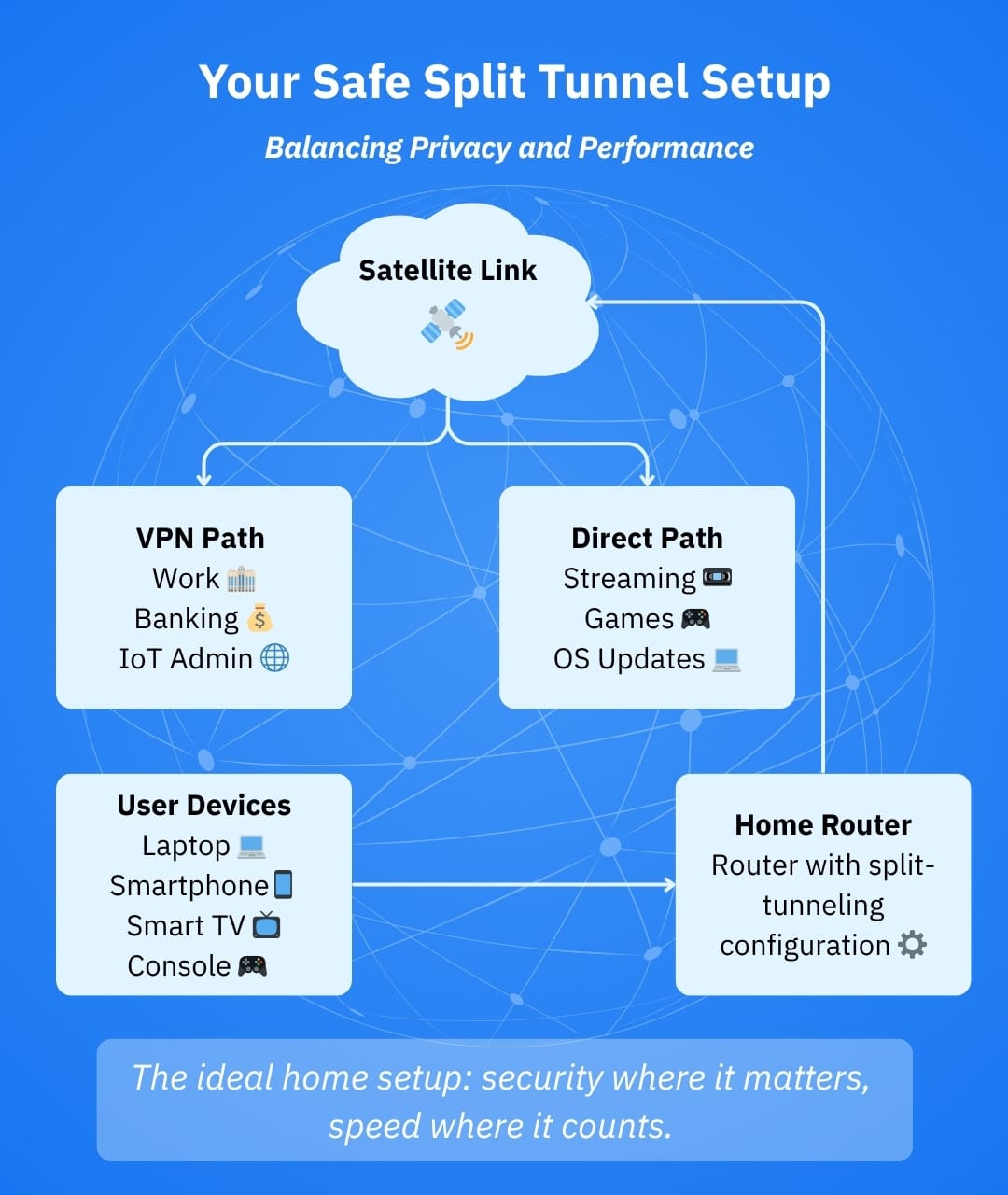
What is a safe default split tunneling recipe?
- Route only your work apps, banking sites and remote-admin subnets through the VPN
- Keep everything else (streaming, consoles, updates) direct over satellite
- Enforce DoH/DoT on the router so DNS doesn’t leak privacy
- Enable MSS clamping and adjust VPN MTU until stalls disappear
- Harden endpoints and use multi-factor authentication (MFA) everywhere
Conclusion
Split tunneling over satellite works well when you treat it like a security policy and not a speed hack. LEO links make “direct” traffic feel local, while sensitive flows stay protected in the tunnel.
Tune MTU/MSS early, pick UDP-friendly VPNs and remember CGNAT changes how you do remote access. Do it right, and you’ll keep both privacy and performance, even at the edge of the internet.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsYou might also like
Bookmarks


