Wrapping up the 2019 PwnThyBytes CTF

Here we are at the end of the first edition of the PwnThyBytes Capture The Flag Competition. We hope it was a challenging, learning and intriguing experience for all teams that took part. As organizers, we can say it certainly was for us.
Without further ado, here are the winners of the contest:
First place goes to LC↯BC, who managed to solve roughly half of the published challenges. Their efforts paid off (literally), as they receive the top prize of €2,048. Congratulations, guys!
The runner-up this time is team hxp, which really pulled through during the last 7 hours of the competition, closing the gap between themselves and LC↯BC to just a task’s worth of points. For their sustained effort, they receive €1,024. Impressive determination!
And the bronze medal goes to team meltdown. They were neck and neck for 1st place for most of the competition, and they earn €512. Way to go!
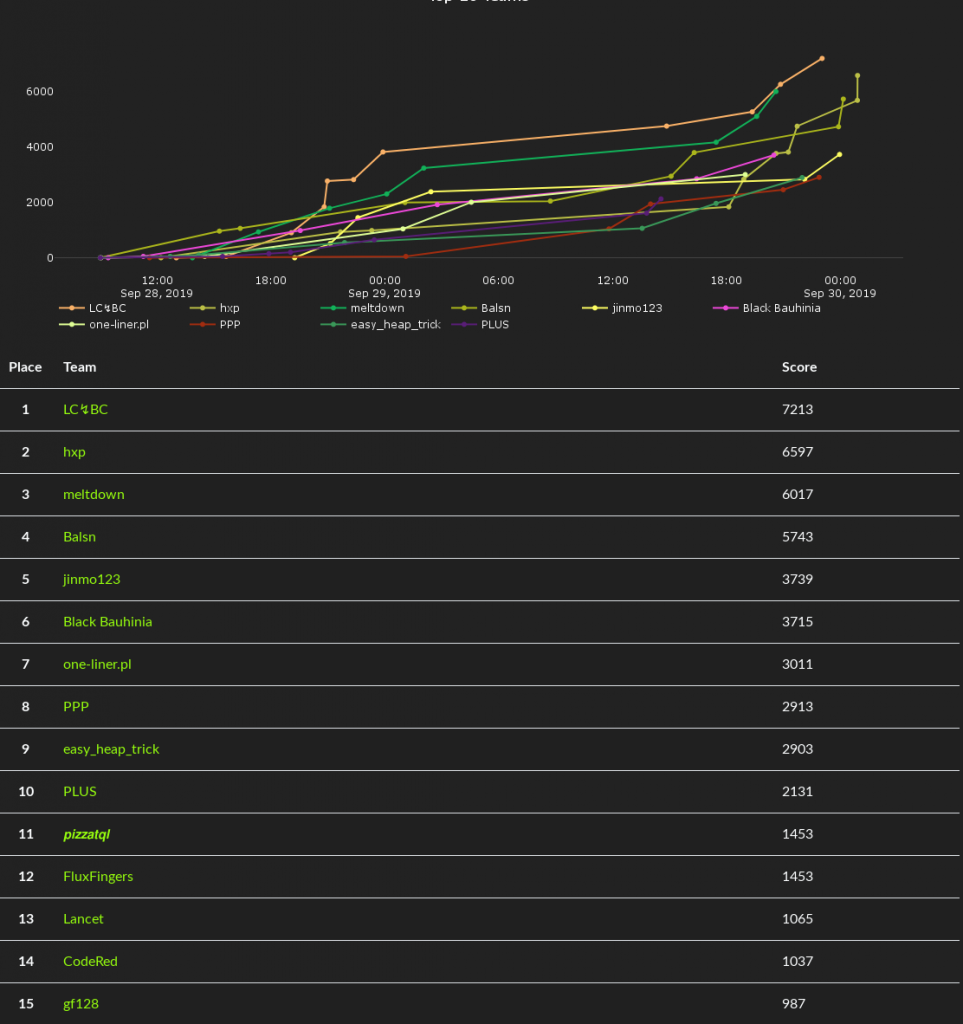
Now that that’s out of the way, we’d like to talk about what we wanted to achieve with this contest, as a team of players who has seen a few CTFs, good and bad, fun and frustrating.
We set off to create a CTF that would give no quarter to participants, with the end goal of winnowing the best from the rest. The challenges were intentionally hard and very hard, based on information security problems we had faced or thought about intensively. We were curious to see if other teams were familiar with these topics or were able to become familiar with them during the contest.
Bearing in mind that a new CTF will also attract people new to CTFs, we also devised what we considered simpler tasks, with the idea that beginners will focus on one or two tasks, learn about a particular subject in detail and gain knowledge that will be useful for them after the competition.
Moving on, we’d like to share a few stats to better illustrate the interest the CTF community has shown in our little contest:
– 1,162 teams have registered for the CTF, while 455 actually played and 53 solved at least one challenge; we didn’t want our tasks to be that daunting, but that’s how it turned out
– all those teams used 4,368 IP addresses to tackle our challenges; not quite a botnet, but not negligible either
– none of the top 3 teams managed to solve a Memory Corruption (pwn) task; we were not expecting this, but as a team called PwnThyBytes, we’re not sorry about this 😛
As to the geographic diversity of participating teams, the top 20 countries by number of IPs that accessed our infrastructure during the competition looks like this:
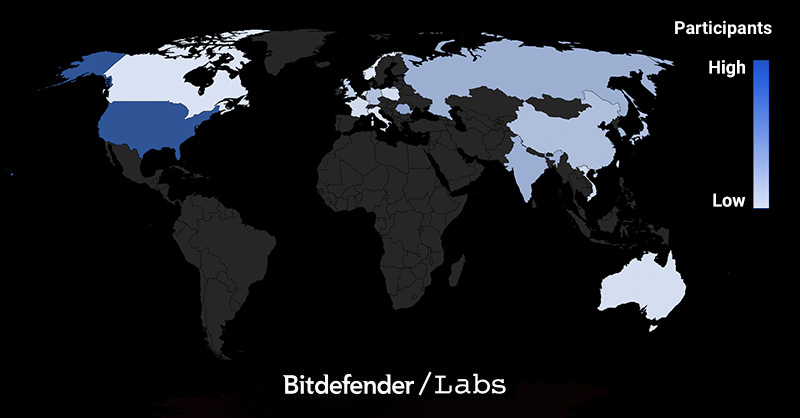
These 20 countries account for roughly 82% of visitors. We notice most of the countries are in the Northern Hemisphere, with representatives spread across North America, Europe and Asia. It’s noteworthy that Romania reached second place in this statistic, but that is somewhat to be expected given we are a Romanian team.
This was our first attempt at organizing CTFs, instead of just playing them. We got some things right, we also got some things wrong. Although this article sums up the first edition of PwnThyBytes CTF, our work will not end here. We’ll be looking at anything remotely resembling a log file or feedback: our Google form, the ctftime.org rating comments, public and private chat messages on our Discord, as well as actual logs that show how our platform performed during the CTF. While we will do our very best to iron out the details, we hope the contest was a stimulating, fun and educational experience for the participating teams. Enough so that they come back next year. We’ll try to one-up ourselves!
We’d like to thank Bitdefender for providing the resources to reward the winning teams and for footing the bill for the infrastructure we used.
Last, but certainly not least, we’d like to thank the people that willingly subjected themselves to a 40-hour meandering journey through some tough tasks to tackle. No CTF can be good without the players that seek it.
For those who love to hack, we salute you!
Of course, for those who have been patient enough to read this far, here is a selection of writeups, either from participating teams or from the authors, so those of you who hit a snag when solving the challenges and were left wondering what they missed can enjoy some not-so-light reading. Pull requests are welcomed! 🙂
tags
Author

The meaning of Bitdefender’s mascot, the Dacian Draco, a symbol that depicts a mythical animal with a wolf’s head and a dragon’s body, is “to watch” and to “guard with a sharp eye.”
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks













