Plite Bootkit Spies on Gamers

While some are dropping their rootkit components, others are designing new ones from scratch, in hopes of staying hidden from most AV software – and sometimes they almost succeed. A team of Bitdefender reasearchers (Balazs Biro, Cristian Istrate and Mircea Pavel) has recently come across just such an example of misapplied ingenuity.
Plite is a bootkit that inserts a trojan in the user’s system on every boot. Currently, Bitdefender software detects the mbr infection as Rootkit.MBR.Plite.A.
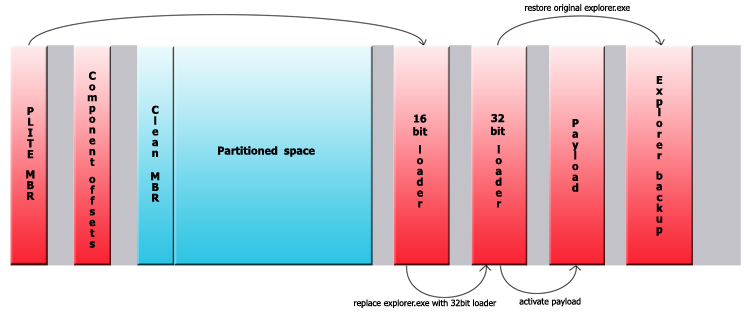
The dropper will first make a backup copy of explorer.exe(test1234.dat) and then load 4 resources, each of them being a separate component of the bootkit(infected MBR, a 16-bit loader, a 32-bit loader and the payload).
The original MBR is saved at the sector 0x28 and the infected one will overwrite sector 0. Since only 0xBA bytes are overwritten, a chunk of the original MBR will still remain on sector 0. The other three components are written on disk between the end of the last partition and the end of the disk. Then, in the sector 0x1E a structure is written with the purpose of storing the offsets of the components and their size as well as other information regarding the infection process.
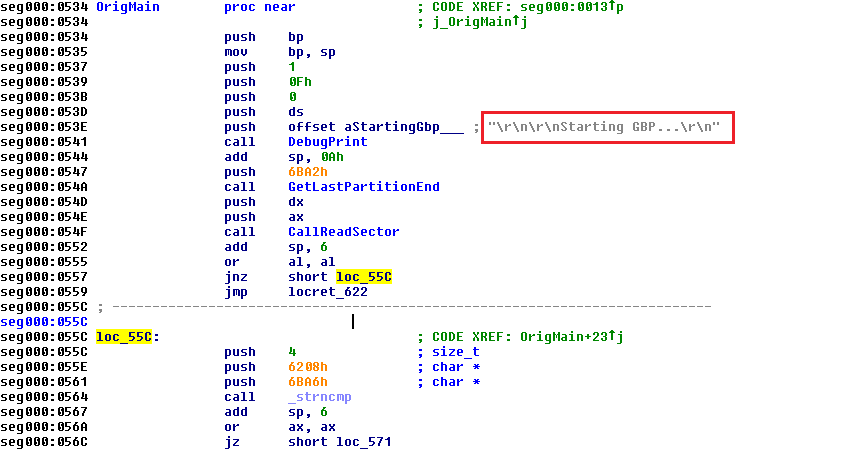
The 16-bit loader is then loaded and control is passed to it. This one was probably written in C and compiled with one of the early Microsoft compilers ( it contains the 16-bit Microsoft Run-Time Library). However, it has been modified in such a manner that it will work without DOS running. The MZ header is stripped, there is a small stub before the executable that calls the original main function. The author has commented out the code of the function used for printing out debug messages, but he (or she) forgot to delete the actual messages before compiling it, which makes the file easier to analyze.
The bootkit has routines for parsing the FAT and NTFS metadata, with the help of which it overwrites explorer.exe. Replacing a file by parsing the NTFS before the OS load is not a new technique in the bootkits’ world, having been used previously by malware such as Yoddos and Mybios.
The 32-bit loader that now replaces explorer.exe will be loaded by the operating system. It will make a copy of itself and as a copy, the loader will now be able to restore the original explorer.exe , reading the backup directly from the disk and execute it so the system loads normally. Then it will place the payload executable in the system32 folder and run it.
To conceal its presence on the system the payload will hide it’s process using an undocumented API, ZwSystemDebugControl, but this only works on operating systems before Vista. With the help of this function it can read and can write kernel memory directly, it will unlink its process from the list of running processes, thereby making it invisible. This is also a well known technique used by malware to access kernel memory without much effort.
This component also manages the communication with the command center. It was observed that it connects to 118.103.xxx.4:11190 or 113.30.xx.20:11180, but both connections were refused. The data sent to the server starts with a “AS101” signature. The rest is encrypted(“not” operator applied on every byte) and includes: a word representing a command, user name, OS , version of the dropper. After decryption, the traffic looks like this:
The command dwords can be 3001(initiates the conversation, letting the server know that the client is active), 3002(the client may receive a file to be written on the disk, probably for update purpose), 3004(client’s system is shutting down). Here is for example a part of the 3002 command:
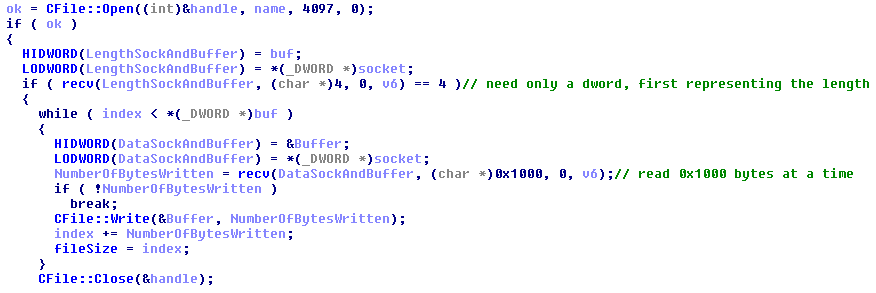
Embedded in this executable as a resource we find a subcomponent of the payload. This is a trojan that will scan the memory for the following game processes: highlow2.exe, LASPOKER.exe, poker7.exe, Baduki.exe, HOOLA3.exe, DuelPoker.exe, FRN.exe. If a game is launched the trojan searches for a window at an exact position, where it should find the game window. Data about the window it finds there is gathered. If the window has the title “GAME” it also captures an image of the screen. Data like computer name, the window name and the captured screens are sent over the TCP protocol to 113.30.xx.20:81, a South Korean address. The purpose is spying in online games. The sent data is not encrypted as you can see from the image:
The data is sent into chunks starting with a tag, for the jpeg image the tag is 6003. Other chunks contain info about computer name (tag 9000), name of the window (tag 6004). The trojan is written in Delphi, unlike the other components. It seems that the bootkit makers added the trojan from other sources, for example this project request looks very similar in functionality.
The bootkit is only detected by Bitdefender, so far. Here’s the hash, in case you’re wondering if you have already come across it in the wild:
md5: b12fe0dd8fbef09b2ad78deadbe2311a
tags
Author

Razvan Stoica is a journalist turned teacher turned publicist and technology evangelist. Recruited by Bitdefender in 2004 to add zest to the company's online presence.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks