KeRanger Is Actually A Rewrite of Linux.Encoder

According to Bitdefender researchers, the trojaned Transmission torent client update dubbed KeRanger racks up a number of firsts, being the world’s first piece of fully functional Mac OS X ransomware, first Mac OS X malware distributed via a signed software update from a legitimate developer, and the first cross-platform ransomware ever.
A closer look at the KeRanger ransomware Trojan reveals that it is actually a Mac version of the Linux.Encoder Trojan.
The infected Mac OS X torrent client update analyzed by Bitdefender Labs looks virtually identical to version 4 of the Linux.Encoder Trojan that has been infecting thousands of Linux servers since the beginning of 2016.
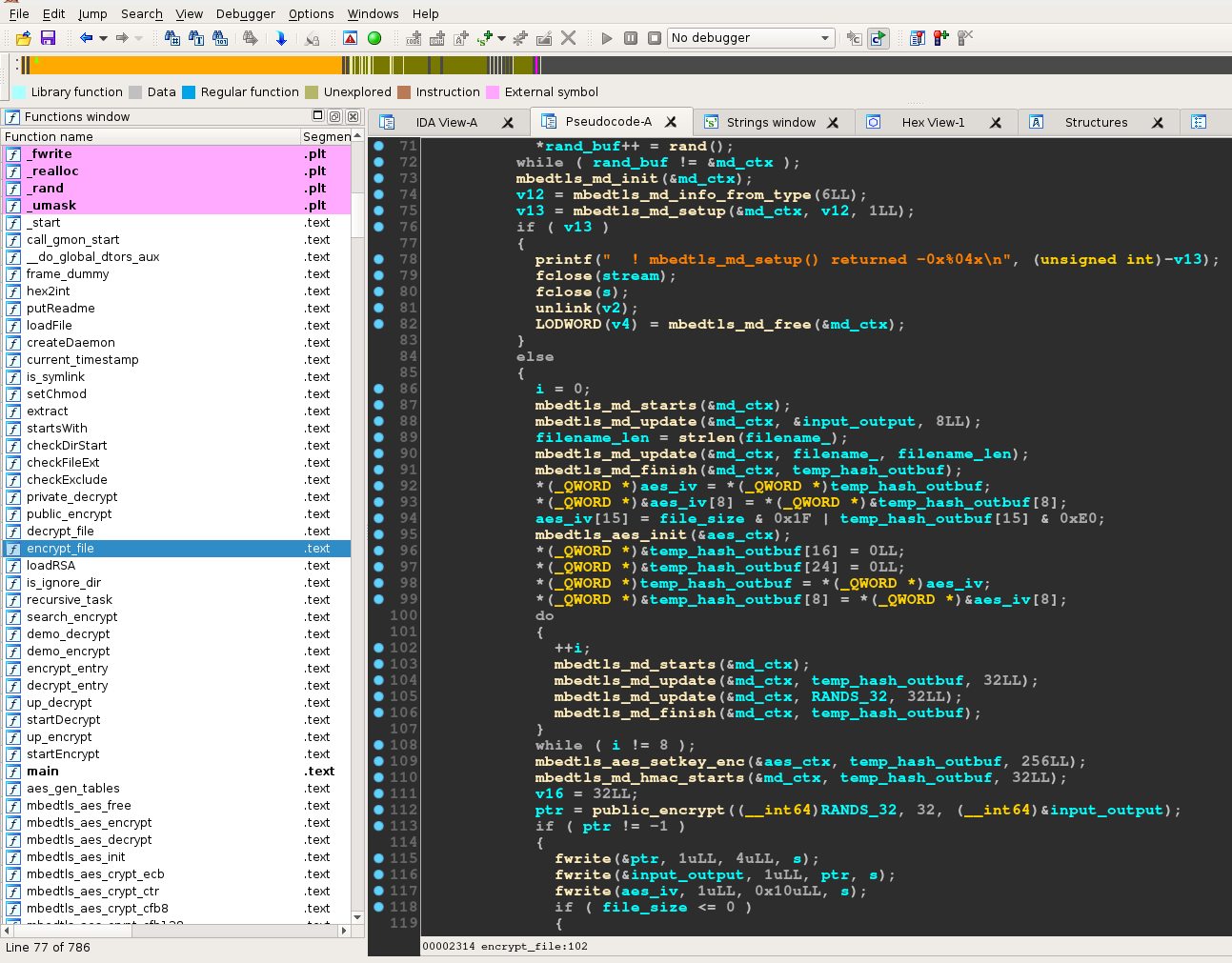
Fig. 1 – Linux.Encoder.4 disassembly
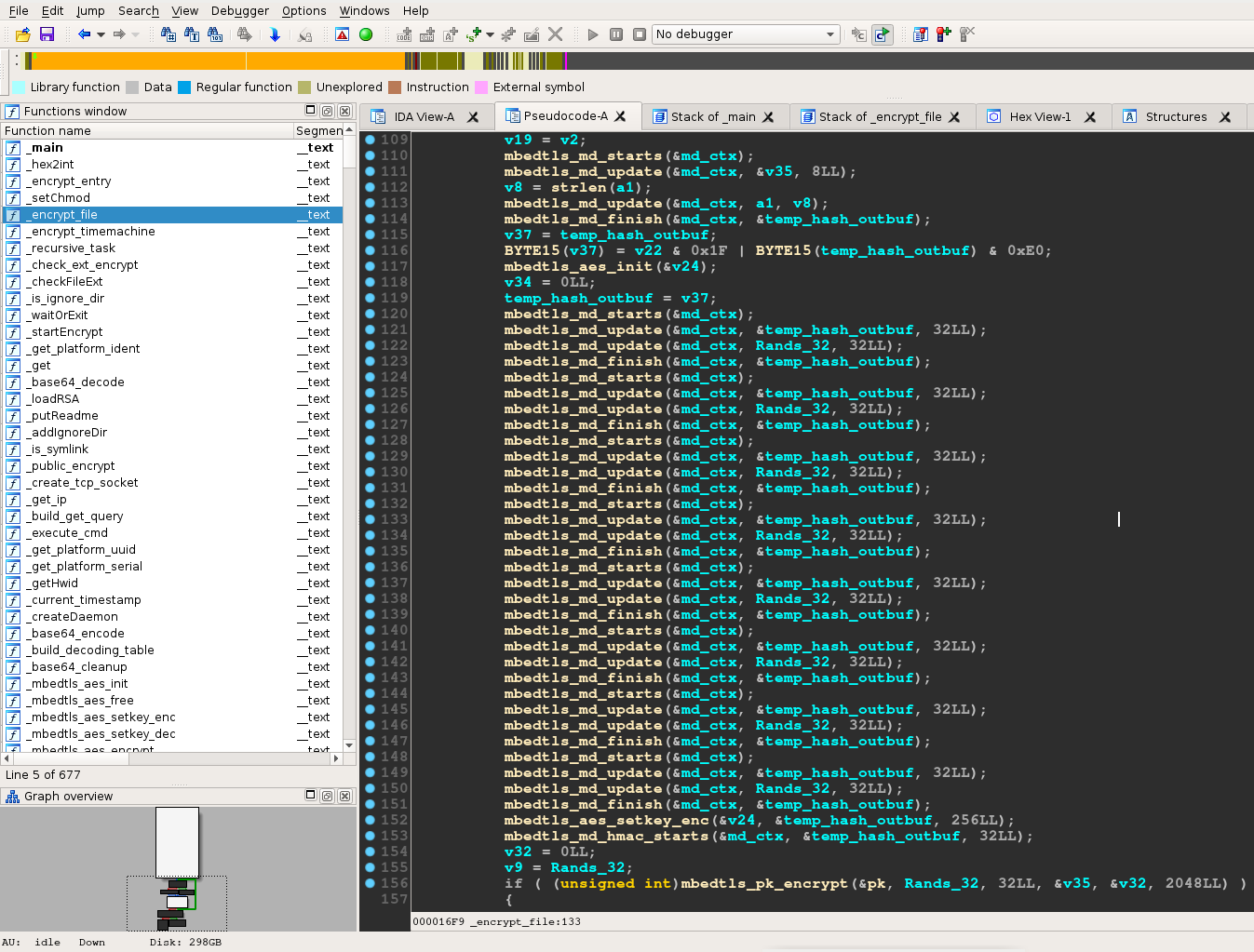
Fig. 2 – KeRanger disassembly
Defeating the Mac OS X defenses
As of Mountain Lion, Mac OS X ships with a security feature called Gatekeeper. It allows users to restrict which sources they can install applications from in order to minimize the likelihood of deploying a tainted app. The default setting allows users to install applications from the Mac App Store and identified developers (namely applications that are digitally signed by a developer).
To circumvent Gatekeeper, the attackers have digitally signed the Transmission update package. According to apple, a legitimate certificate issued by Apple was used. The developer listed this certificate is a Turkish company with the ID Z7276PX673, which was different from the developer ID used to sign previous versions of the Transmission installer. This is not the first time cyber-criminals managed to circumvent Gatekeeper by misusing legitimate digital certificates. In 2013, a backdoor signed with a compromised digital certificate (MAC.OSX.Backdoor.KitM.A) was found on the computers belonging to Angolan civil rights activists.
Once the infected installer is executed, the Trojan connects to the command and control centers via TOR and retrieves an encryption key. After encryption finishes, the KeRanger ransomware creates a file called README_FOR_DECRYPT.txt that holds the information on how the victim should take to pay the ransom.
“The encryption functions are identical and have same names: encrypt_file, recursive_task, currentTimestamp and createDaemon to only mention a few. The encryption routine is identical to the one employed in Linux.Encoder,” explained Catalin Cosoi, Chief Security Strategist at Bitdefender.
Lessons learned
Six months ago, ransomware was a threat that only Windows and Android users had to worry about. In December last year, world’s first piece of Linux ransomware was spotted in the wild after encrypting thousands of webservers. Fortunately, Bitdefender researchers could circumvent the encryption algorithm and provide decryption utilities for all four variants in the wild. It seems that the developers behind the Linux.Encoder malware have either expanded to Mac OS X or have licensed their code to a cybercrime group specialized in Mac OS X attacks.
“It is worth emphasizing that nothing short of a fully-fledged, native MacOS X security solution with real-time, behavior-based detection techniques could have saved MacOS X users from having their systems infected and their files encrypted. There is more, much more, to security than merely disallowing unsigned software” Catalin Cosoi concluded.
tags
Author
Right now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks















