BTCWare decryption tool now available

If your computer has been hit by BTCWare, fear not; you now have a free and safe way to recover your data without paying the ransom.
The Bitdefender Labs team has released the BTCWare decryption tool, available either as a standalone free tool or as part of the Bitdefender Ransomware Recognition tool, which is available for download here (also for free).
If you’re sure your computer has been encrypted with the BTCWare ransomware, download this tool directly and run it on the infected computer. We always recommend you decrypt your data via the Bitdefender Ransomware Recognition tool, as it first detects the type of ransomware that infected your device, then suggests the latest version of the appropriate decryption tool.
[mks_button size=”large” title=”Download the BTCWare decryption tool” style=”squared” url=”https://labs.bitdefender.com/wp-content/uploads/downloads/btcware-decryption-tool/” target=”_self” bg_color=”#81d742″ txt_color=”#FFFFFF” icon=”” icon_type=”” nofollow=”0″]
Using the decryption tool
- Download the BTCWare Decryption Tool from the Tools repository.
- Run the downloaded tool and allow it to execute if prompted by User Account Control
- Agree to the End User License Agreement (make sure you have a backup of the data)
- Point the application to a folder containing the encrypted files. If the encrypted files are scattered across a drive, check the Scan entire system option.
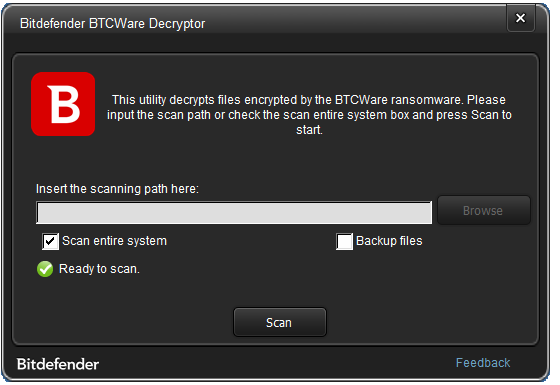
The decryption tool will not run if:
- It can’t find a valid ransom note
- It cannot find a valid encrypted file (i.e a file that is not corrupted)
- It can’t decrypt the User ID field in the ransom note
- It cannot pass the test of decrypting 5 random files in the folder / drive – this helps us protect from corruption files that might be encrypted with a different family of ransomware and that are stored in the same folder as BTCWare-encrypted ransomware.
Some technical info about the tool
This family of ransomware was first spotted in March 2017. It encrypts user files with three different cyphers (AES192, RC4 and AES256) and all keys are encrypted into the Ransom Note in the so-called User ID file. Practically, the User ID field is the encryption key itself in Base64 format.
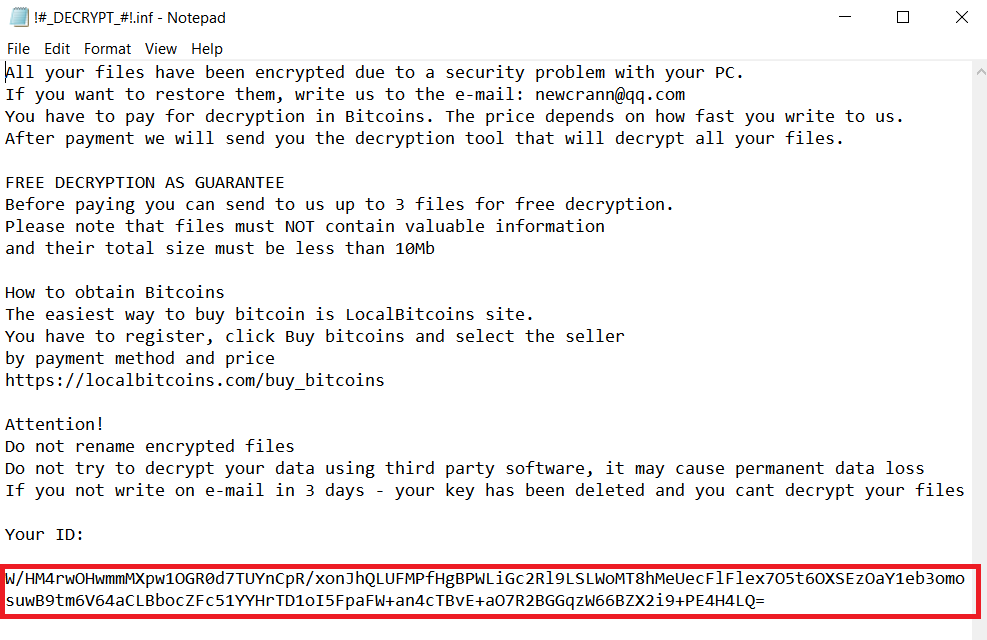
Examples of decrypted user-IDs from different malware versions:
- [.cryptobyte] – [SSLL-A332m8UneXS4oom962a4dTTzo-2017-07-31]
- [.onyon] – [DN-19701465958ig2oO1PxH3f32A971dTHXLM7NB0KIjRKV854E197013966619947408188ig2o76E55C60-2017-07-31]
- [.cryptowin] – [ADM-gZ5Lw14Im6qGM9tcv8kfA4sR5-2017-07-31]
- [.theva] -[OBAMA-7P5Yc37RuTFyxwtBVuvIq69SyFj7c728e1TQ3QY1ipWA1gQg4cmu83bGTsX6YwoUqYAGh1i7P92EQ38bMe2008-2017-07-31]
- [.master] – [3-76F93D951D611E203B45894ED48856B2532691C756DF21276E554528B664B5176E55C60-2017-07-31]
As of the moment of writing this article, this malware family uses 9 different extensions grouped into the 3 encryption algorithms described above. We classify them into 4 different versions using the encryption type, as shown in the table below:
| Ver | Extension used | Encryption type | Ransom-note name | Decrypted |
| 1 | .btcware | RC4 <1KB chunked | #_HOW_TO_FIX.inf | YES |
| 1 | .cryptobyte | RC4 <1KB chunked | #_HOW_TO_FIX.inf | YES |
| 2 | .onyon | RC4 first 10MB only | !#_DECRYPT_#!.inf | YES |
| 2 | .xfile | RC4 first 10MB only | !#_DECRYPT_#!.inf | YES |
| 3 | .cryptowin | AES192 <1KB chunked | #_HOW_TO_FIX.inf | YES |
| 3 | .theva | AES192 <1KB chunked | #_README_#.inf | YES |
| 4 | .master | AES256 first 10MB only | !#_RESTORE_FILES_#!.inf | YES |
| 4 | .aleta | AES256 first 10MB only | !#_READ_ME_#!.inf | NO |
| 4 | .blocking | AES256 first 10MB only | !#_READ_ME_#!.hta | NO |
Some ransom notes may be overlapping.
To build our tool, we used leaked private keys that can decrypt almost all versions of the malware (v1, v2 and v3 ), as well as the .master extension in version 4 of the malware. We are also working to add some optimized brute-forcing technologies to cover the instances in which the leaked keys don’t work.
The decryption tool we provide also uses additional safety mechanisms to protect against file damage. Mass decryption only starts if the tool successfully decrypts 5 random files, as well as the ransom note. These files are either selected from an indicated folder or from the entire pool of files, if no specific folder is indicated.
Please note that there is no way to decrypt your files without the ransom note, so make sure you keep a copy of it for the future.
Log generation
During decryption, a number of logs are generated and saved inside the %temp% folder. There are two types of logs, but the most relevant to the operation is the BitdefenderLog.txt file, where decryption results are stored. If you encounter any issue with the tool, please get in touch with us via the contact option in the tool and provide us with this log file:
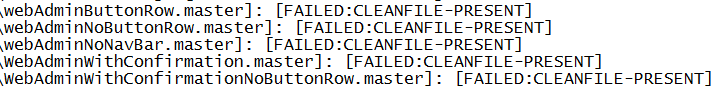
The log file also keeps tabs of the files that could not be decrypted, so you may submit these files to analysis and help us improve the process, if possible.
The log file also keeps tabs on the files that could not be decrypted, so you may submit these files for analysis and help us improve the process, if possible.
Decryption fails in some instances
Sometimes, in circumstances beyond our control, decryption might fail. This happens in particular cases when the malware attempted to encrypt files in use by the operating system and got to creating the encrypted file, but could not delete or replace the original. Such files will be displayed in the log with additional clarification as to why the decryption process failed – the file was in a clean state and no decryption was needed. Another variation of this scenario happens when the original file is encrypted and a copy renamed with an extension that suggests it is encrypted, yet its contents are unencrypted.
The information included in this blogpost is provided courtesy of Bitdefender malware researcher Vlad Craciun.
tags
Author
Right now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks













