Annabelle Ransomware decryption tool

Annabelle Ransomware is a family of file encrypting malware inspired from the horror movie franchise Annabelle. In addition to its file encryption capabilities, the Annabelle ransomware goes the extra mile and attempts to disable the firewall, deny the execution of an array of utilities, spread via connected USB drives and ultimately, overwrite the MBR with a movie-inspired bootloader.
Bitdefender offers a tool to decrypt the ransomed files for free. Here is how to get your files back if your data has already been encrypted.
Infections with Annabelle are easy to tell from other ransomware strains because of the particular, movie inspired ransom note.

Annabelle encrypts user files using AES256 CBC with a hardcoded key and IV.
Example of encrypted files:
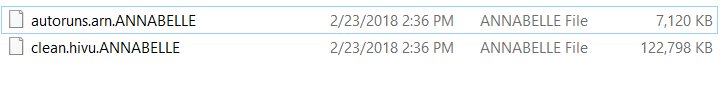
The infection process takes place in two phases. First, the malware locks the PC screen and then changes the MBR. Because of this, in order to be able to use the tool, the user is required to do some clean-up as follows:
- Recover the device’s Master Boot Record (replace or change it via various tools)
- Delete the registry keys in order to prevent the malware from starting with the operating system. You can use the Bitdefender Rescue CD to initiate a scan and get rid of the infection.
- After you have removed the infection, download the decryptor below and start the decryption.
Because of the way AES encryption works, some files might have up to 15 extra bytes appended at the end. These extra bytes should notimpact the decrypted file in any way – we cannot remove these extra bytes as there is no mark of the original size inside the encrypted file.
How to use this tool
Step 1: Download the decryption tool below and save it somewhere on your computer.
Download the Annabelle decryptor
Step 2: Double-click the file (previously saved as BDAnnabelleDecryLast week wasptor.exe) and allow it to run by clicking Yes in the UAC prompt.
Step 3: Agree with the End User License Agreement
Step 4: Select “Scan Entire System” if you want to search for all encrypted files or just add the path to your encrypted files if you have them grouped in a folder.
We strongly recommend that you also select “Backup files” before starting the decryption process, should anything occur while decrypting. Then press “Scan”.
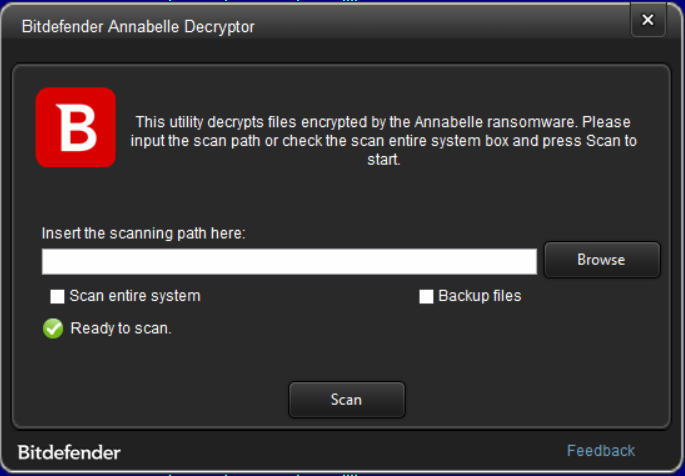
At the end of this step, your files should have been decrypted.
If you encounter any issues, please contact us via the e-mail address specified n the feedback section of the decryption tool
If you checked the backup option, you will see both the encrypted and decrypted files. You can also find a log summarizing the decryption process in %temp%\BDRemovalTool folder
Acknowledgement:
This product includes software developed by the OpenSSL Project * for use in the OpenSSL Toolkit (http://www.openssl.org/)”
tags
Author
Right now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks













