Android Instapaper App Vulnerable to Man-in-the-Middle Attacks

The Bitdefender Research team analyzed popular Android app Instapaper and found it can be vulnerable to man-in-the-middle attacks that could expose users’ signup/login credentials when they try to log in into their accounts. The vulnerability may have serious consequences, especially if users have the same password for more than one account, leaving them potentially vulnerable to intrusions.
The Problem.
Instapaper allows users to save and store articles for reading, particularly for when they’re offline, on the go, or simply don’t have access to the Internet. The application works by saving most web pages as text only and formatting their layout for tablets or phone screens. Everyone who wants to use the application is required to sign-up and create an account to check out notes, liked articles or access other options.
However, the vulnerability lies not in the way the application fetches content, but in the way it implements (or in this case, doesn’t implement) certificate validation.
Although the entire communication is handled via HTTPS, the app performs no certificate validation. If someone were to perform a man-in-the-middle attack, he could use a self-signed certificate and start “communicating” with the application.
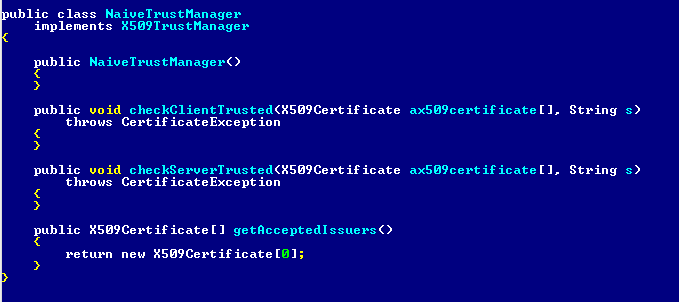
The application sets a SSLSocketFactory and uses a TrustManager without having any implementation for certification validation. Here’s how it looks:
The SSLSocketFactory class is responsible for validating the HTTPS server against a list of certificates and validating the authenticity of the HTTPS server using a private key. The implementation of this class is particularly important as it enables server authentication and guarantees communication between user and server is encrypted and cannot be viewed in plain text by traffic-sniffing tools.
The TrustManager checks whether the specified certificate chain can be validated and is trusted for client/server authentication for the specified authentication type. In other words, if there is no implementation for TrustManager, anyone can impersonate the Instapaper server and start collecting authentication credentials via a man-in-the-middle attack.
The Attack
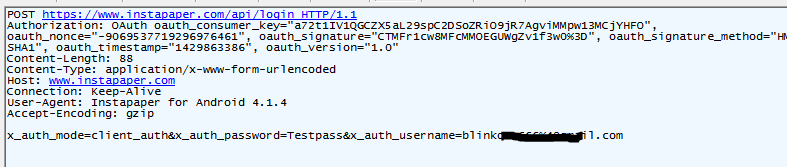
If a user were to sign into his account while connected to a Wi-Fi network that’s being monitored by an attacker, his authentication credentials (both username and password) could easily be intercepted using any a fake certificate and a traffic-intercepting tool.
Our experiment involved using a MitM proxy that could intercept the broadcasted Instapaper credentials, as shown below:
Implications
While the attacker might seem to only gain access to your Instapaper account, most people use the same password for multiple accounts. A cybercriminal could try and use your Instapaper password to access your social media or email accounts. Studies have shown that more than 50% of users reuse the same password, so the chances are better than even that more than one account could be vulnerable if your Instapaper credentials have been stolen.
We have notified the development team behind the Android Instapaper app about the found vulnerability, but they have yet to confirm when a fix will become available.
Note: This article is based on technical information provided courtesy of Vlad Bordianu, Bitdefender Researcher. The research was conducted on Instapaper Version 4.1.4 (version code: 46).
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks