Android Campaign from Known OceanLotus APT Group Potentially Older than Estimated, Abused Legitimate Certificate

A group of sophisticated threat actors known as OceanLotus or PhantomLance has recently become known for disseminating advanced Android threats via official and third-party marketplaces since 2014. They have sought to remotely control infected devices, steal confidential data, install applications and launch arbitrary code.
While security researchers have recently documented the group and their campaigns, a Bitdefender investigation has revealed 35 new malicious samples, and evidence that the campaign may have used a legitimate and potentially stolen digital certificate to sign some samples.
The modus operandi for the APT group involved spreading tainted Android apps through Google Play and third-party marketplaces by initially uploading a clean version and then adding malware.
Security researchers have linked attribution to the OceanLotus APT group to the shared infrastructure between the Android malware and past command and control domains used for Windows-based advanced threats that have historically targeted Microsoft users. It is believed these older campaigns also had connections to the Hacking Team group, which is known to have served the APT32 group.
While OceanLotus targets victims mostly from Africa and Asia, Bitdefender telemetry also indicates scans in countries such as Japan, South Korea, Vietnam, Germany and India. This threat is detected as Android.Trojan.OceanLotus by Bitdefender.
Finding Patient Zero
The oldest sample found in the Bitdefender repository (APK MD5: 315f8e3da94920248676b095786e26ad) and associated with the OceanLotus APT group seems to have first landed on Google Play in April 2014. Previous estimates of the campaign’s origin date the oldest known Google Play sample to December 2014.
According to the internal zip file timestamp, the sample was built on 2014.04.05 and ended up in our collection just days after.
An interesting observation is that this sample is signed with a certificate belonging to VL Corporation. This certificate was generated on July 2013, and over 100 different applications on Google Play, other than OceanLotus Malware, seem to have been using it until 2014. This suggests that the cybercriminal group may have successfully smuggled tainted apps into Google Play using a valid certificate.
Certificate: Data: Version: 3 (0x2) Serial Number: 2002933886 (0x7762587e) Signature Algorithm: sha256WithRSAEncryption Issuer: C=VN, ST=10000, L=HN, O=VL Corporation, OU=VL Corporation, CN=VL Corporation Validity Not Before: Jul 22 18:57:09 2013 GMT Not After : Jul 16 18:57:09 2038 GMT Subject: C=VN, ST=10000, L=HN, O=VL Corporation, OU=VL Corporation, CN=VL Corporation
It’s likely that he certificate was leaked and abused by the APT group. Currently, none of the over 100 applications that were in Google Play and signed with this certificate still have it.
Targeted Countries
In terms of telemetry, over the past 3 months alone we have seen 25 reports involving this threat, mostly in the US, Japan and South Korea. Granted, it’s likely that the reports in the US may not be actual devices, but Amazon-hosted Android machines rigged to run the samples potentially for security analysis. It’s not uncommon for security researchers to perform this type of sandboxing, especially when trying to pull indicators of compromise or study malicious behavior.
However, reports from South Korea and Japan do indicate at least a limited number of devices have recently encountered OceanLotus APT samples.
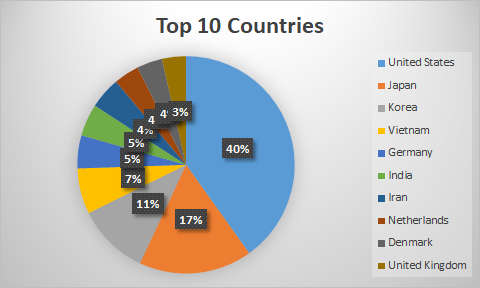
Tracking the Spread
In terms of spread, while security researchers already reported that distribution occurred through both the official Google Play marketplace and third-party marketplaces, some that mirror Google Play still host these samples. This means that, while Google does a great job at timely managing their app collection and responding to input from security researchers and vendors, third-party marketplaces remove these threats slowly – if ever – potentially exposing users to malware, indefinitely.
Some examples of third-party marketplaces that still host these malicious samples include:
hxxps://apkpure.com/opengl-plugin/net.vilakeyice.openglplugin hxxps://apk.support/app/net.vilakeyice.openglplugin hxxps://apkplz.net/app/com.zimice.browserturbo hxxps://apk.support/app/com.zimice.browserturbo hxxps://androidappsapk.co/download/com.techiholding.app.babycare/ hxxps://www.apkmonk.com/app/com.techiholding.app.babycare/ hxxps://apkpure.com/cham-soc-be-yeu-babycare/com.techiholding.app.babycare hxxps://apk.support/app-th/com.techiholding.app.babycare
While there’s already a comprehensive list of samples attributed to the OceanLotus APT group, for which we know they have been in Google Play, we’ve added the following that have also been confirmed on Google Play at some point.
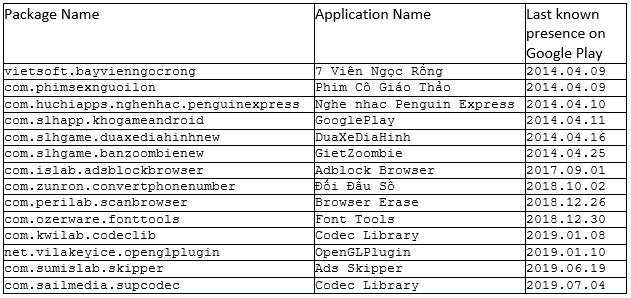
For the full list of additional new samples (md5) found by Bitdefender researchers and attributed to the OceanLotus APT, please check below:
3043a2038b4cb0586f5c52d44be9127d f449cca2bc85b09e9bf4d3c4afa707b6 76265edd8c8c91ad449f9f30c02d2e0b 5d909eff600adfb5c9173305c64678e7 66d4025f4b60abdfa415ebd39dabee49 7562adab62491c021225166c7101e8a1 7b8cba0a475220cc3165a7153147aa84 63e61520febee25fb6777aaa14deeb4a 9236cf4bf1062bfc44c308c723bda7d4 f271b65fa149e0f18594dd2e831fcb30 e6363b3fae89365648b3508c414740cd d9e860e88c22f0b779b8bacef418379e 3d4373015fd5473e0af73bdb3d65fe6a a57bac46c5690a6896374c68aa44d7b3 08663152d9e9083d7be46eb2a16d374c 18577035b53cae69317c95ef2541ef94 eee6dcee1ab06a8fbb8dc234d2989126 5d07791f6f4d892655c3674d142fe12b f0ea1a4d81f8970b0a1f4d5c41f728d8 320e2283c8751851362b858ad5b7b49c 1fb9d7122107b3c048a4a201d0da54cd bb12cc42243ca325a7fe27f88f5b1e1b 01b0b1418e8fee0717cf1c5f10a6086b 4acf53c532e11ea4764a8d822ade9771 6ff1c823e98e35bb7a5091ea52969c6f 1e5213e02dd6f7152f4146e14ba7aa36 3fe46408a43259e400f7088c211a16a3 c334bade6aa52db3eccf0167a591966a 53ba3286a335807e8d2df4aae0bd0977 7f59cb904e2e0548b7f0db12c08b9e25 49d1c82a6b73551743a12faec0c9e8b1 6b323840d7cb55bb5c9287fc7b137e83 2e1ed1f4a5c9149c241856fb07b8216b 6737fba0f2b3ea392f495af9a0aa0306 bda442858c33ae7d9f80227c55f6a584
Circumventing Google Play Protection
It’s common for attackers to submit a clean version to Google Play, then wait a random amount of time and simply update the application with malicious code. This tactic seems to have been used by the cybercriminal group as well.
For example, the application net.vilakeyice.openglplugin (OpenGLPlugin) was first uploaded as clean, on August 5th 2018, and then the malicious payload was introduced on August 21st.
APK Seen on Google Play No Payload 7285f44fa75c3c7a27bbb4870fc0cdca 2018.08.05 With Payload d924211bef188ce4c19400eccb6754da 2018.08.21
The payload is then decrypted and loaded dynamically within the application. If older samples had the decryption key embedded locally within the original clean application, newer samples no longer store it locally, as they seem to receive the decryption key along with the malicious payload.
Attribution and Availability
While attribution for these Android malware samples has already been the subject of analysis from the security industry, with the OceanLotus APT group tagged as responsible, the fact that samples still exist on third-party marketplaces should raise red flags.
Some samples that were on Google Play at some point are currently still available on third-party markets, including on Amazon. In regions around the world where access to content from the official Google Play marketplace may be restricted, users still risk infection with this type of malware.
In this particular example with Amazon India, the developer name is Caleb Eisenhauer (a fake name) and the application seems to have been published on February 16th 2020. The email address associated with the account ([email protected]) sends to a privacy policy hosted on GitHub (https://github.com/malcesshartspur).
It’s likely that similar fake developer accounts exist, all spreading various samples on third-party marketplaces with the potential to infect victims over an extended period of time if not removed.
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks















