Spying on personal alarms and GPS trackers is as simple as sending an SMS

It sounds like a great idea for the elderly and vulnerable members of society, who still want to retain their independence.
A personal alarm and tracker service, the size of a key fob, that can transmit its location via SMS or a GPRS data connection. If the SOS button is pressed, its location is sent to registered contact numbers, and a two-way voice call can be initiated.
And if the device detects its owner has fallen over it can automatically send an alert, with no need to press the SOS button.
With real-time monitoring, loved ones and relatives can monitor the individual’s location, and geofences can even be set up to send an alert if the wearer enters or leaves a pre-defined area.
What could possibly go wrong?
Security experts have found that the devices – manufactured in China, and rebadged by multiple companies around the world – are unfortunately vulnerable to a simple hack that could allow a hacker to track their location, and even secretly listen in via the microphone.
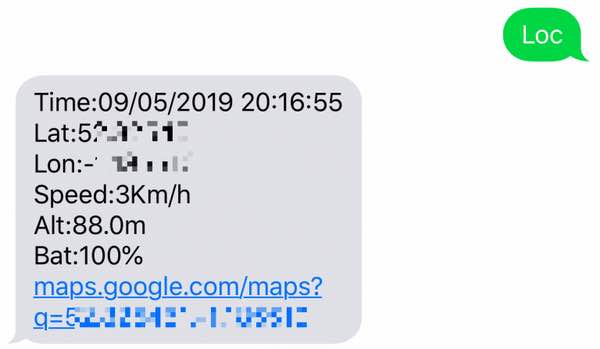
Researchers at UK firm Fidus Information Security looked at the devices after an elderly relative had their previous emergency panic button – which only worked in-home – upgraded by their local council. The “upgrade” was designed to improve protection for the relative, as for the first time it would be capable of detecting falls and its in-built SIM card meant it did not have to be in vicinity of a base station based in their home.
To their dismay, the researchers discovered that all that was required to interact with a tracking device remotely was its mobile phone number. A simple SMS text message could be sent to devices to trigger them into responding with their real-time location, as well as secretly turning on the microphone.
“There were no signs from the device when this was activated or when you called in, turning this device issued to vulnerable people into a remote listening bug!”
Furthermore, an unauthorised third party could use the same text message method to disable features such as the low battery alarm, fall detection and motion detection, and reset the device’s list of emergency contacts.
The researchers say that they have identified “many, many” rebadged versions of the device from multiple companies selling it in the United States, United Kingdom, Australia, Germany, Spain, Finland, and beyond.
Affected devices sold in the United Kingdom are said to include the following:
- “Personal Alarm & GPS Tracker with Fall Alert – Unforgettable
- Footprint – Anywhere Care
- GPS Tracker – Fall Alarm – Amazon/Tracker Expert
- SureSafeGO 24/7 Connect ‘Anywhere’ Alarm – SureSafe
- Ti-Voice – TrackIt24/7″
By this point you may be wondering how on earth the Chinese manufacturer failed to put some authentication in place to check that an SMS text message communicating with the device was coming from an authorised administrator.
And the surprise is that there was built-in PIN functionality to lock down devices, but it was by default disabled.
Worse still, even if you had successfully protected a device from malicious commands with a PIN, the PIN was entirely ignored if a RESET command was sent, removing all stored contacts and returning the device to its factory default settings.
“Once a factory reset had been applied, the device was then open to all to access again, without the requirement of knowing the PIN. If anything, the RESET functionality provides a malicious user with the ability to gain remote access to the device and conduct further attacks.””
Unfortunately there does not appear top be any way to apply a security update to devices already out in the wild. Fidus’s research team recommends that alternative devices with better in-built security be used instead.
The researchers claim to have contacted some of the biggest suppliers of the devices in the UK to make them aware of the risks. But from the sound of things, some of the warnings may be falling on deaf ears”
“Some UK suppliers are looking into and are actively recalling devices and some have not responded.”
Take care folks.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








