Snake Keylogger Returns in Malspam Campaign Disguised as Business Portfolio from IT Vendor

Snake Keylogger has slithered its way back into the threat landscape this week in a new malspam campaign that appears to be targeting IT decision makers within organizations.
The email campaign delivering the notorious Snake Keylogger was observed by Bitdefender Antispam Labs on Aug. 23, and seems to primarily target recipients in the US. The attack, originating from IP addresses in Vietnam, has already reached thousands of inboxes, according to Bitdefender telemetry.
In this attack, threat actors leverage the corporate portfolio of a legitimate Qatari-based IT provider of cloud storage and security solutions to trick potential victims into opening a malicious ZIP archive.
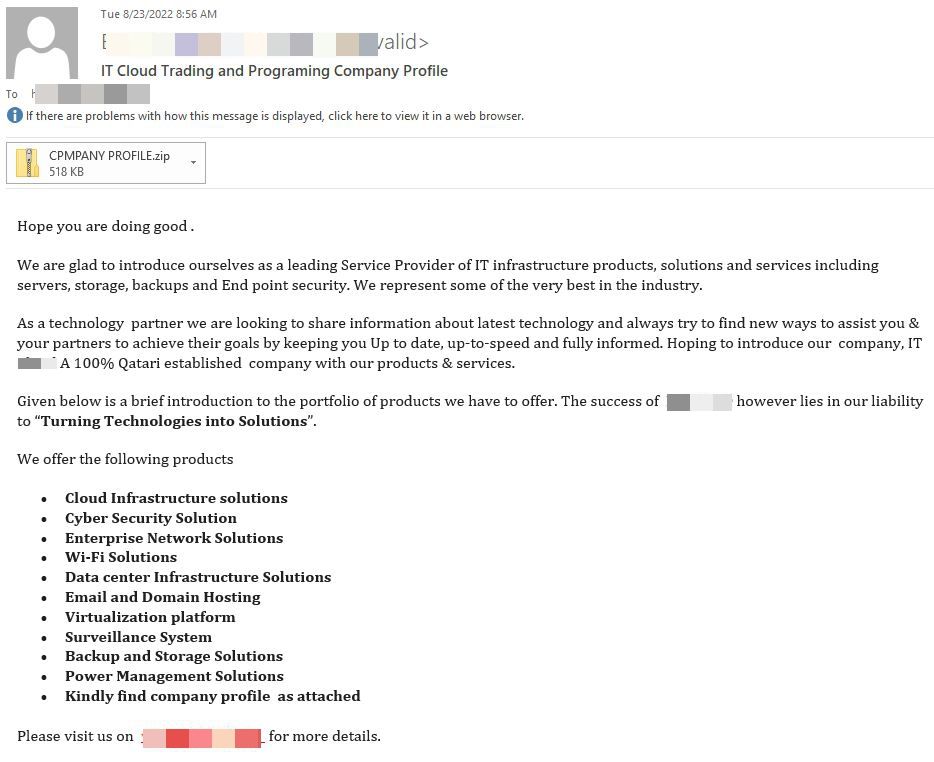
The archive (ba8e072f51e1b944bfa3466da15cefa3) contains an executable CPMPANY PROFILE.exe(9df140013f2b8627f7ea911d9767acdc) which loads the Snake Keylogger payload onto the victims’ system host. Captured data is exfiltrated via SMTP.
Snake Keylogger (also known as 404 Keylogger) is an info-stealer that exfiltrates sensitive information from infected systems and has keyboard logging and screenshot capabilities, as well as the ability to extract information from systems’ clipboards. The infamous credential-stealing trojan appeared in late 2020 and can be found on message boards and underground marketplaces for just a couple of hundred dollars or less, depending on the level of service the customer requires.
Snake infections are mostly financially motivated, with individuals potentially facing identity theft and fraud, among other crimes. The credential-stealing malware also poses a high security risk for enterprises due to its data-harvesting and spy tool capabilities that could allow threat actors to gain access to high-level accounts and deploy more crippling attacks within an organization.
Previously, Snake attacks have been known to leverage Microsoft Office documents (Word and Excel) and PDFs, which makes them highly efficient social engineering tactics.
Cybercriminals running the campaign could make victims susceptible to major security and privacy threats, including holding data for ransom and exfiltrating financial data.
To help protect yourself and your organization against keylogger attacks, always verify the origin and validity of correspondence before interacting with links or attachments, and deploy security solutions. Ensure that accounts are protected via two-factor (2FA) or multi-factor (MFA) authentication processes that will prevent cybercriminals from logging into accounts should your system get compromised, and install a security solution on their devices.
Bitdefender customers are protected from Snake malware. This malspam campaign is detected by the Bitdefender antispam technology and the
the attachment is detected as Trojan.GenericKD.61435093and blocked by both our consumer and enterprise solutions.
With Bitdefender Total Security and XDR, users and businesses enjoy the best anti-malware protection and threat detection and response against e-threats across all major operating systems. The real-time protection feature included in Bitdefender security solutions safeguards against e-threats, including keyloggers or spyware, viruses, worms, Trojans, ransomware and zero-day exploits, to keep you and your data safe.
Note: This article is based on technical information courtesy of Bitdefender Labs
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








