IoT botnet launched massive 13-day DDoS attack against streaming service

Can you put your hand on your heart and say the web application your company has built would be able to handle 292,000 requests per second, from 402,000 different IP addresses?
A denial-of-service attack of that magnitude would be hard for many services to stand up against, regardless of how well they had been built, the security best practices that had been followed, the penetration tests that they had survived.
Yet, according to a new report from DDoS mitigation firm Imperva, one company was targeted with just that size of attack earlier this spring.
The company, which is unnamed, but said to produce an entertainment streaming app, was the subject of a massive Application Layer 7 DDoS attack starting in later April.
For nearly two weeks the DDoS attack was consistently over 100,000 requests per second, peaking at 292,000 requests per second.
Imperva described it as the largest Layer 7 DDoS attack it had ever seen.
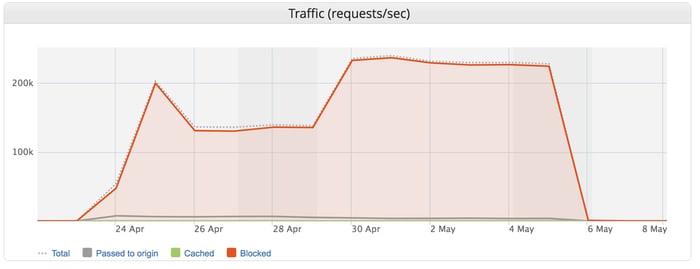
Application Layer 7 DDoS attacks differ from network layer DDOS attacks that aim to congest communication between a targeted site and the rest of the internet, gobbling up as much bandwidth as possible. Instead Layer 7 DDoS attacks attempt to mimic normal user behaviour, consuming resources on a web server by flooding a web with a large number of HTTPS GET/POST requests.
Such traffic can be difficult to tag as malicious, as it can be hard to differentiate from legitimate user activity.
As a result, Layer 7 DDoS attacks can be more difficult to defend against – although Imperva says it was able to mitigate the attack and its customer, thankfully, suffered no downtime.
However, in their investigation into the attack researchers pointed a finger of suspicion at IoT devices, infected with a version of the Mirai malware.
Mirai made headlines in 2016, after a devastating DDoS attack was launched at the Dyn domain name service, disrupting access to some of the world’s most popular websites.
Mirai created a huge botnet by scanning huge swathes of the internet, searching for open Telnet ports, and attempted to gain access to devices via Telnet through the simple trick of trying weak usernames and passwords.
With sad predictability, it was shown that owners of vulnerable IoT routers and webcams had failed to learn that using a default username and password on an internet-enabled device was about as good as having no password at all.
It doesn’t appear that it was the original Mirai botnet that attacked the unnamed entertainment company, but instead one of the many Mirai variants which emerged after the source code for Mirai was made available for download.
The release of that code made it that little bit easier to hijack CCTV cameras, routers, and all manner of other IoT devices to bombard websites with attacks, including this latest Layer 7 DDoS attack.
Analysis of the IP addresses that performed the attack revealed that the majority of them, by far, were based in Brazil.
In an attempt to evade interception by DDoS mitigation services, the attackers used a legitimate User-Agent in order to appear to look the same as queries by a legitimate streaming app.
And, although it has been hard to confirm, it is thought that the motivation for the attack may have been to break into accounts using credential stuffing and brute force techniques.
As IoT botnets continue to be harnessed to launch damaging DDoS attacks it becomes more important than ever for consumers to ensure that their internet-connected gadgets are properly secured and patched.
After all, you don’t want to be partly responsible for one of the biggest Layer 7 DDoS attacks in history, do you?
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Microsoft Is Done With Windows 10 but Bitdefender Will Keep You Safe Until October 2026
October 14, 2025
Recruitment Scam Alert: Fraudsters Impersonate Bitdefender in Fake Job Interviews
October 13, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








