Despite all the advice, 97.7% of Twitter users have still not enabled two-factor authentication

Twitter has revealed that the vast majority of its users have ignored advice to protect their accounts with two-factor authentication (2FA) - one of the simplest ways to harden account security.
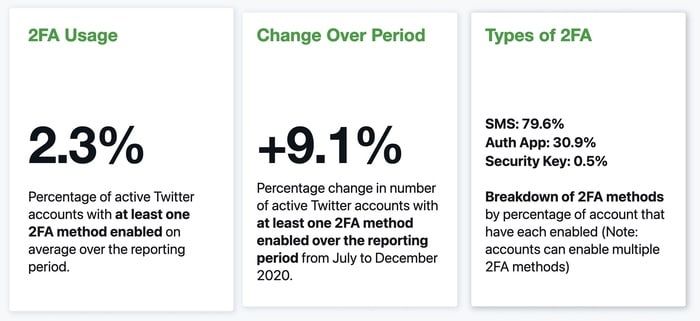
According to Twitter's own data, revealed in its recently-published transparency report, just 2.3% of users had 2FA enabled in the second half of 2020.
In Twitter's own words, "enabling 2FA ensures that even if your account password is compromised (perhaps due to the reuse of your Twitter password on other, less secure, websites), attackers will still be blocked from logging into your account without access to the additional authentication required."
2FA on Twitter is available regardless of whether you access your account from your smartphone or desktop computer. Once enabled, Twitter will prompt you - alongside requesting your password - to confirm that you are authorised to access the account by entering a six digit code or using a security key.
Unlike your Twitter password, the six digit code doesn't remain the same. It's a unique number generated by a hardware key or authenticator app on your smartphone, or sent to you via SMS.
If you don't pass the additional security step of entering the right code, Twitter won't allow you to access your account.
The beauty of this approach is that an unauthorised party probably does not have physical access to your smartphone or security key, and so shouldn't be able to determine the code. And even if they do manage to trick you into handing over the code, it will have changed within 30 seconds or so.
This doesn't mean 2FA guarantees that your account will never be hacked.
For instance, SMS-based 2FA is regarded as less secure because of the problem of SIM swap attacks (sometimes called a Port Out scam) where fraudsters trick cellphone operators into giving them control of someone else’s phone number.
In addition, more sophisticated cybercriminals might be able to trick users via phishing attacks into handing over their 2FA codes in real-time, abusing the tokens before they expire.
Despite not being perfect, enabling 2FA is one of the wisest steps you can take in hardening your online security.
Which makes it disappointing to discover that more than eight years after Twitter first introduced two-factor authentication to stop hackers from hijacking accounts, only 1 in 50 users have chosen to enable the feature.
Any 2FA is better than no 2FA, even if it is SMS-based. And hardware security keys are the strongest version of 2FA that Twitter supports.
Unfortunately, according to Twitter's own stats, when the pitiful 2.3% who are using 2FA is examined more closely, almost 80% of them are using the most problematical SMS-based version.
There's clearly room for improvement in these figures, but Twitter is trying to be upbeat about the chances of the figures improving in future:
Overall, these numbers illustrate the continued need to encourage broader adoption of 2FA, while also working to improve the ease with which accounts may use 2FA. Making 2FA methods simpler and more user friendly will help to encourage adoption and increase security on Twitter.
Make Twitter happy, and harden your account security at the same time, by enabling two-factor authentication.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








