Bitdefender Threat Debrief | October 2022

MDR Insights
Cyber Security Awareness: Threat Modeling
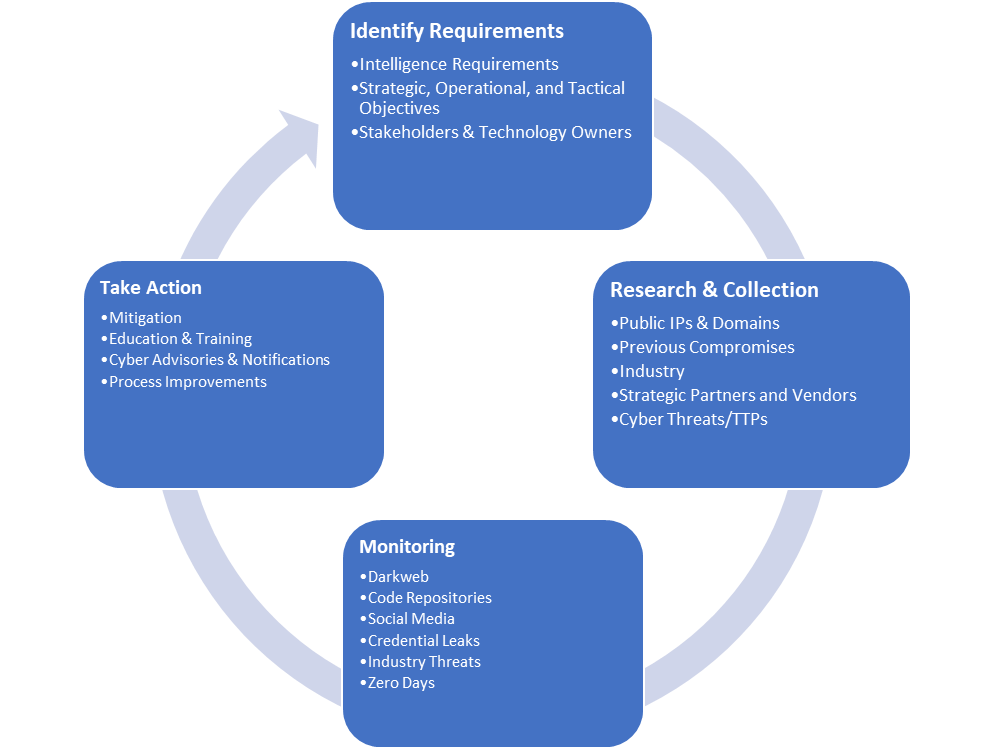
As stated by OWASP, “Threat modeling works to identify, communicate, and understand threats and mitigations within the context of protecting something of value.” Threat modeling must evolve into a way that continuously monitors cyber threats. As we focus on cybersecurity awareness month, threat modeling is an essential step for organizations because it can help answer questions about the potential threats and understand the sprawl of infrastructure and tooling and where the risks may lie. When done correctly, building a threat model should establish processes that allow for data collection, gathering intelligence that supports or refutes findings, reducing risk, monitoring data, and making the information useful to the business. It should also not be static, living at one point in time, but rather a living document that goes through regular revisions as the landscape changes.
How to build a threat model
First, the threat modeling process should gather intelligence requirements that support strategic, operational, and tactical business goals. Collecting details about the organization and monitored environment can be done with various IT and support departments, product or technology owners, questionnaires, threat intelligence tools, and attack-surface monitoring tools. Intelligence requirements help teams define not just the required resources but also gaps in capabilities for collection management purposes.
Here are some things to think about when gathering requirements:
- Who are the stakeholders? These may range from technology or product owners, C-Level leadership, middle management, and security and IT professionals.
- What intelligence requirements matter to the organization? Examples to start the conversation might be pre- or post-attack tactics, attacks by geography or industry, fraud or social engineering, supply chain attacks, and compromises, or vulnerabilities and exploits.
- Business-specific questions are also critical but will also be ever-changing: Has the organization been attacked before? Who has the “keys to the castle?” Where does critical information or data reside (the crown jewels)? What kind of critical information lives on your estate? Are there products or services that might interest a criminal or nation-state actor? What operating systems and applications are in use? Who does business with you? Do any third parties have access?
You can now move to research and collection by using direction from stakeholders, business objectives, and intelligence requirement data as a starting point. The subsequent research, done from an attacker’s perspective, provides useful details about who, what, where, how, and why an organization could be at risk. For example, cyber actors use tactics, techniques, and procedures (TTPs), paired with what is known about the environment, provide data points that can be monitored with security and threat intelligence tools and analyst research. This information is also useful for hunting or incident response because it often produces a baseline of what is known and is otherwise considered a normal business activity in the environment. Another benefit is that knowing the types of software and operating systems and where they’re deployed, for example, can help inform vulnerability management. Understanding who the critical users are can guard against exposure on the internet and help with access management.
Monitoring is probably the most crucial step, and something not commonly considered when building a threat model. Threat models are usually built as a single model that gets updated quarterly or yearly, which often results in an outdated and cumbersome process that is less effective. Monitoring allows cybersecurity professionals to continuously evaluate the threat landscape and discover threats quickly. Domains, public IP addresses, industry-specific information, attack vectors, previous compromises, and tech stack information are data points that can be monitored and alerted when vulnerabilities are discovered, phishing campaigns target specific industries or companies, or attackers leak corporate information. Various intelligence platforms provide the ability to input data related to the environment and find public-facing information, often with context, to make it more relevant.
Finally, the outcome of threat modeling should produce many actions, including playbooks for risk mitigation, overall process improvement, education and training, and cyber advisories or notifications when a threat is suspected or present. Steps taken to deter, prevent or discover threats allow organizations to change the narrative and proactively take steps to reduce their risk. Ultimately, there’s the added benefit of peace of mind for every single stakeholder, often a result of discovering that not every threat is out to get to you and not everything is under attack, which allows the defenders to better focus their attention on what the actual threats are to your organization.
Bitdefender MDR
Bitdefender MDR focuses on preventing attacks as far left of the attackers’ life cycle as possible. Threat modeling creates a process that aids in identifying the right threats while enabling security teams to monitor the right things with a higher degree of confidence. Critical information such as industry, geographic locations, previous incidents or compromises, and technology stack information creates additional data points that can be monitored; and, also add more context. These data points, when considered against potential zero-days and exploits, vulnerabilities, data exposure, or typosquatting, for example, gives defenders a better understanding of what attackers might use against them. Understanding this information helps produce actionable intelligence needed to make security decisions and effectively monitor customer environments.
Ransomware Report
Spear phishing attacks are often used as an initial attack vector and ransomware infection is often the final stage of the kill chain. For this report, we analyzed malware detections collected in September 2022 from our static anti-malware engines. Note: we only count total cases, not how monetarily significant the impact of infection is. Opportunistic adversaries and some Ransomware-as-a-Service (RaaS) groups represent a higher percentage compared to groups that are more selective about their targets, since they prefer volume over higher value.
When looking at this data, remember these are ransomware detections, not infections.
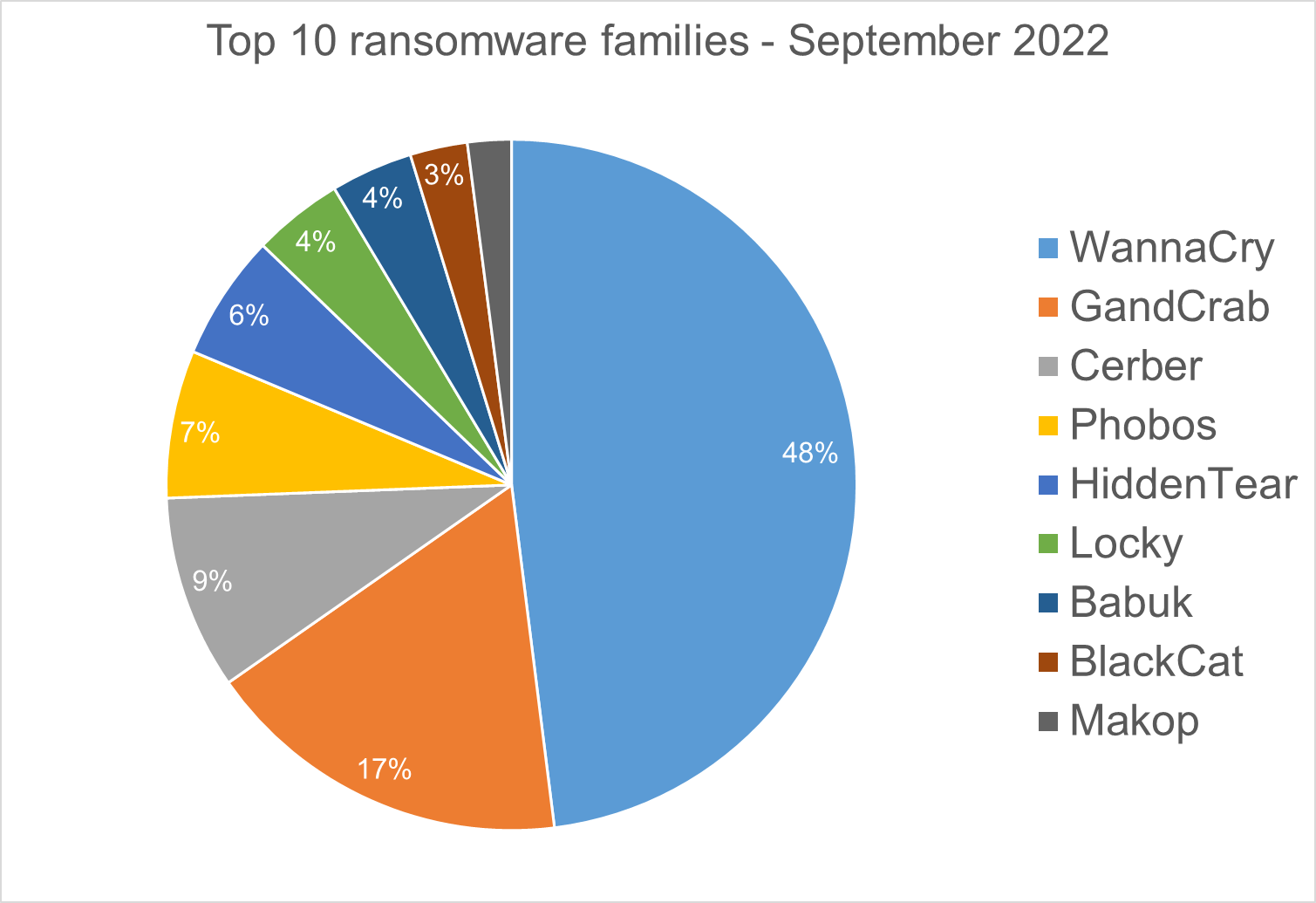
Top 10 Ransomware Families
We analyzed malware detections from September 1 to September 30. In total, we identified 196 ransomware families. Number of detected ransomware families can vary each month, depending on the current ransomware campaigns in different countries.
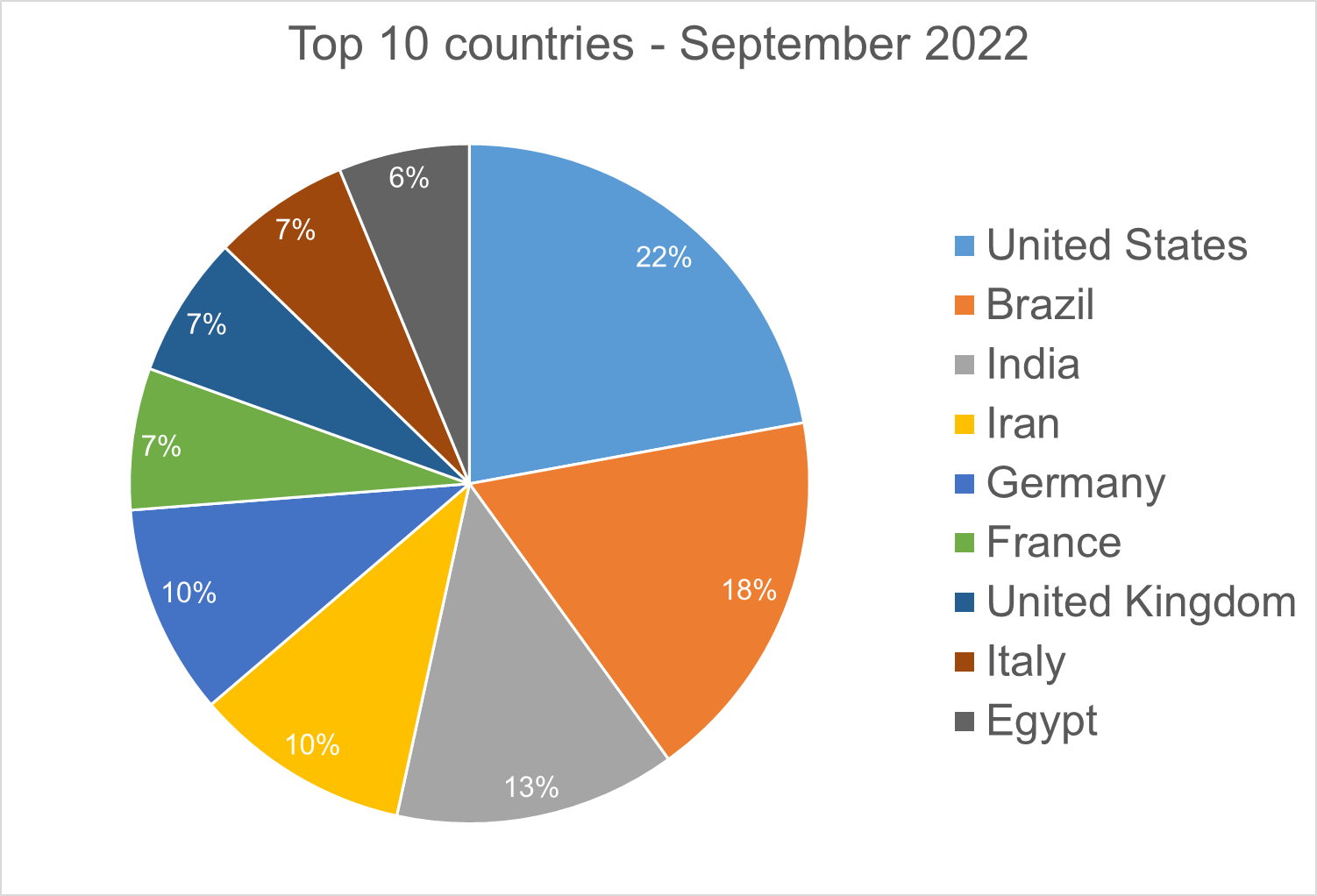
Top 10 Countries
In total, we detected ransomware from 148 countries in our dataset this month. Ransomware continues to be a threat that touches almost the entire world. Below is a list of the top 10 countries most impacted by ransomware. Many ransomware attacks continue to be opportunistic, and the size of population is correlated to the number of detections.
Android trojans
Below are the top 10 trojans targeting Android we have seen in our telemetry during September 2022.
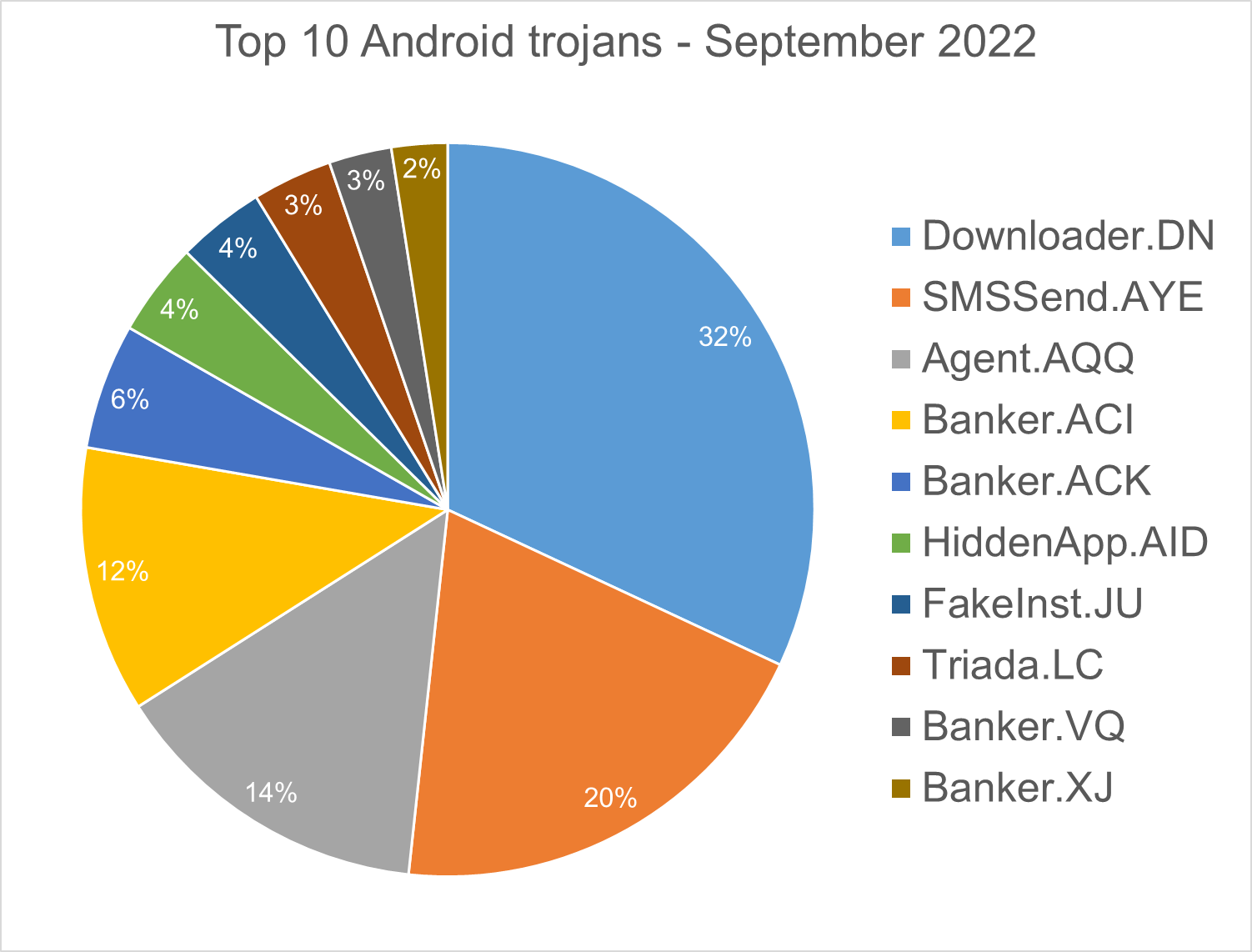
Downloader.DN – Repacked applications taken from Google App Store and bundled with aggressive adware. Some adware downloads other malware variants.
SMSSend.AYE - Malware that tries to register as the default SMS application on the first run by requesting the consent of the user. If successful, it collects the user's incoming and outgoing messages and forwards them to a Command & Control (C&C) server.
Agent.AQQ - A dropper malware is a trojan that hides the dangerous payload inside an app as an evasion technique. If it can avoid security defenses, this payload is deployed. The malicious payload is decrypted and loaded by the dropper.
Banker.ACI, ACK - Polymorphic applications that impersonate legit apps (Google, Facebook, Sagawa Express ...). Once installed, it locates banking applications installed on the device and tries to download a trojanized version from the C&C server.
HiddenApp.AID - Aggressive adware that impersonates AdBlock applications. When running for the first time, it asks permission to display on top of other apps. With this permission, the application can hide from the launcher.
FakeInst.JU – Malware that has the capability to read and send text messages. A text message is sent to a premium number every 1000 seconds. After deployment, it hides its icon from the application menu, and sends sensitive data from the phone (IMEI, phone number, network info…) to a remote server.
Triada.LC – Malware that gathers sensitive information about a device (Device IDs, Subscriber IDs, MAC addresses) and sends them to a malicious C&C server. The C&C server responds by sending back a link to a payload which the malware downloads and executes.
Banker.VQ - Applications that drop and install encrypted modules. This trojan grants device admin privileges, and gains access to manage phone calls and text messages. After deploying, it maintains a connection with the C&C server to receive command and upload sensitive information.
Banker.XJ - Applications that drop and install encrypted modules. This trojan grants device admin privileges, and gains access to manage phone calls and text messages. After deploying, it maintains a connection with the C&C server to receive command and upload sensitive information.
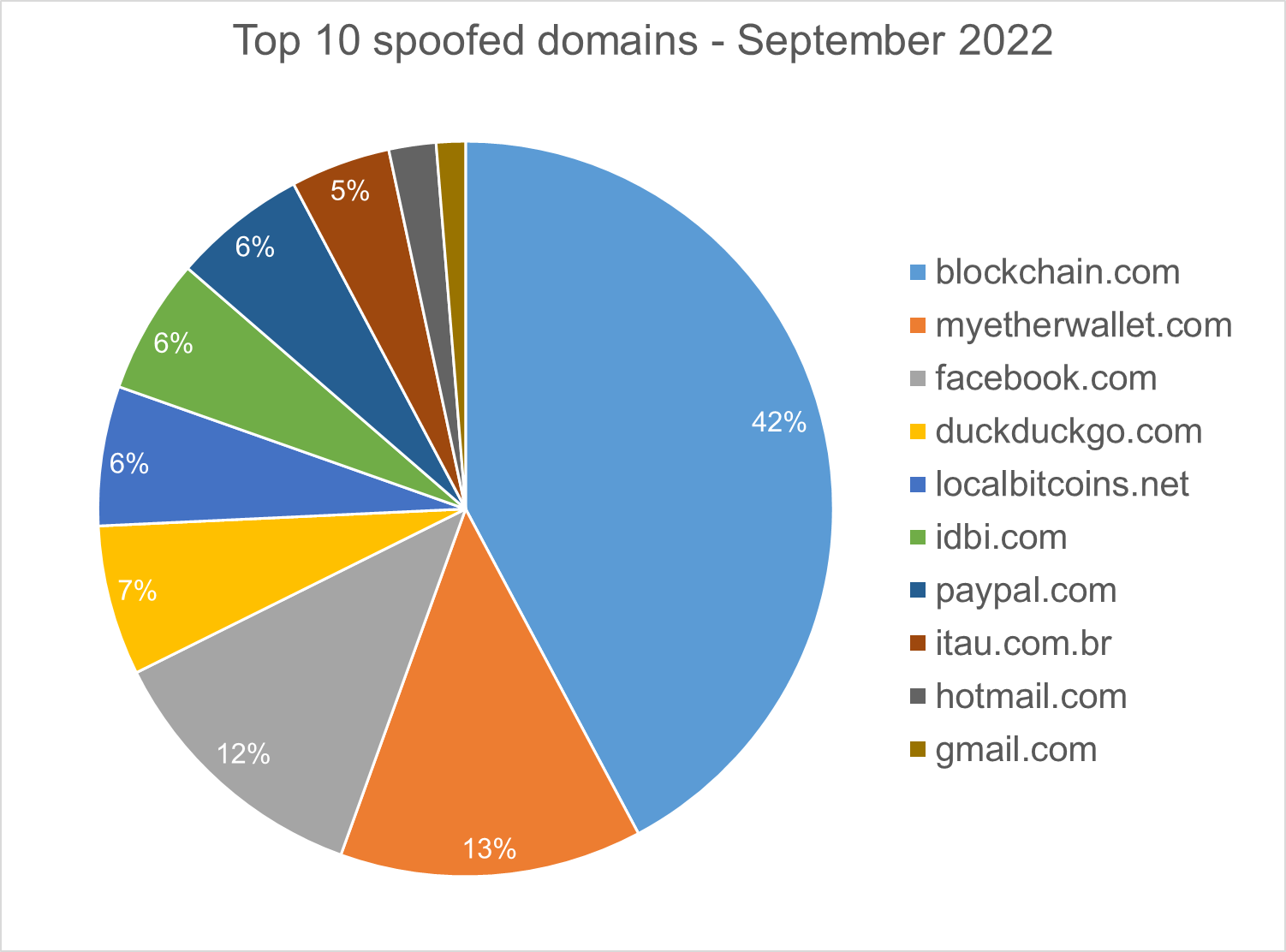
Homograph Phishing Report
Homograph attacks work to abuse international domain names (IDN). Threat actors create international domain names that spoof a target domain name. When we talk about “target” of IDN homograph phishing attacks, we refer to the domain that threat actors are trying to impersonate. You can read more about this type of attack in one of our previous reports.
Below is the list of the top 10 most common targets for phishing sites.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 150 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank bitdefenders Tyler Baker, Alin Damian, Mihai Leonte, Andrei Mogage, Sean Nikkel, Nikki Salas, Rares Radu, Ioan Stan, Marius Tivadar, and Horia Zegheru (sorted alphabetically) for their help with putting this report together.
tags
Author
Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsYou might also like
Bookmarks


