Enterprise IoT Security for Smart Offices

Smart offices, whether big or small, are only as secure as the connected items you let through the door.
Why smart offices raise the stakes
Smart lighting, conference systems, printers, badge readers, cameras, vending machines and HVAC sensors have all brought new levels of convenience and efficiency to small offices. So much so that they are now indispensable to most modern office networks.
Unfortunately, this convenience poses a series of risks to the end users, mainly because many such devices aren’t managed like traditional laptops and phones. Organizations often underestimate the number of IoT devices they already operate and don’t see how these devices expose them to digital threats. So, the first step is visibility and lifecycle thinking.
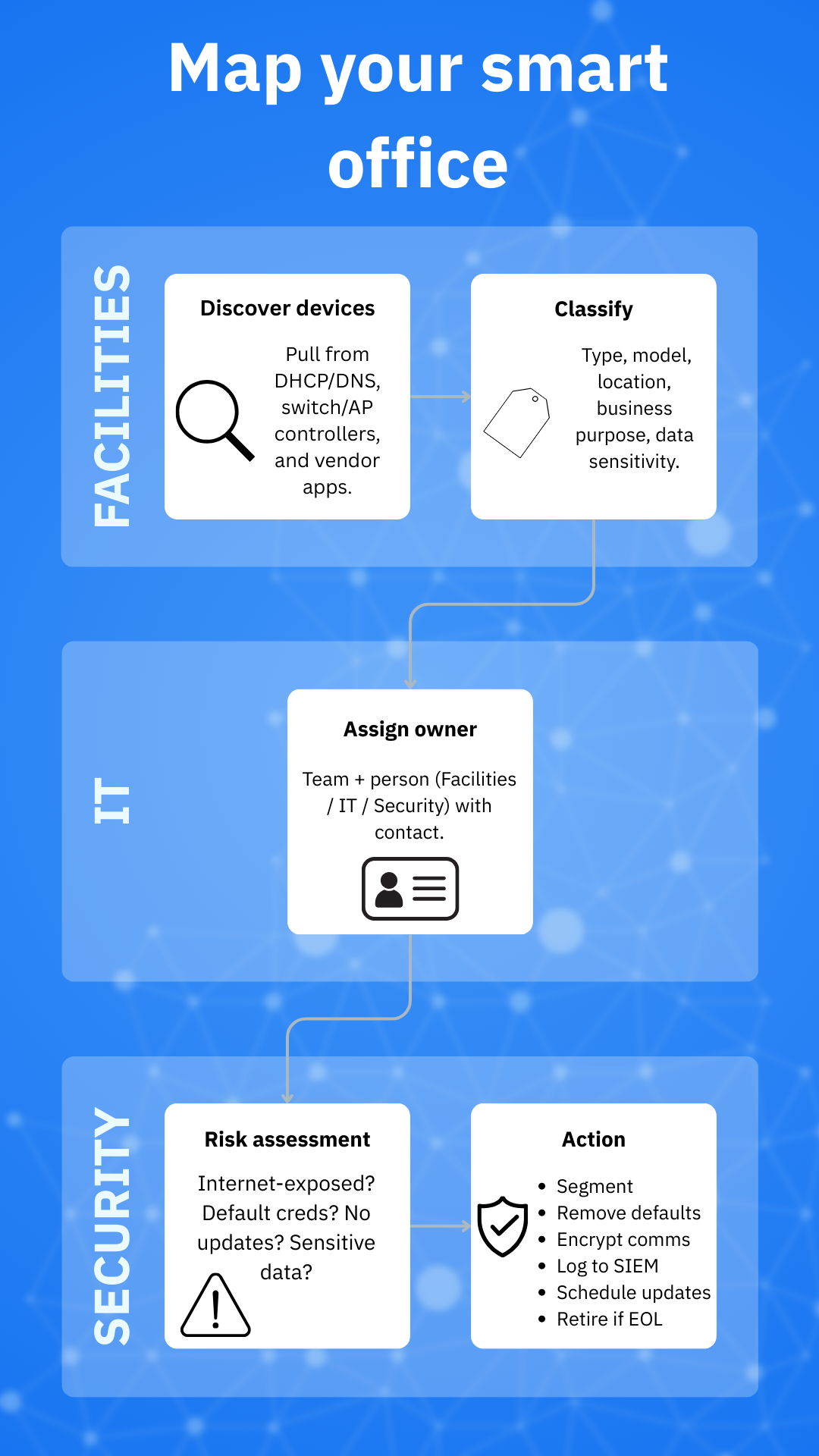
Start with an inventory and ownership model
A clean asset inventory means you don’t have to defend blind. When running an inventory, aim to capture things like device type, location, business purpose, firmware version, network segment, data handled and support status. Maintaining an accurate, lifecycle-long inventory can go a long way in mitigating against IoT-centric threat campaigns.
Here are a few quick tips to get you started in running an inventory for your small smart office:
- Use your switch/AP controller and DHCP/DNS logs to enumerate MAC/OUI “things”
- Tag each device to a business owner (i.e., Facilities, HR, Security, Reception)
- Note cloud dependencies such as vendor portals, mobile apps, and MQTT brokers
Buy (and deploy) with standards in mind
Treat procurement as a security control. Ask vendors to meet certain core baselines – such as secure update, device identity, advanced logging and secure communications – and align your requirements to modern IoT policies and regulations. For any consumer-grade devices you adopt, look for ETSI EN 303 645 conformance (no universal default passwords, vulnerability disclosure, secure communications, updates, data protection). For general governance, ISO/IEC 27400 provides comprehensive IoT security and privacy guidelines.

Segment the network and control access
Segment your network mindfully and avoid dangerous situations such as installing badge readers and TVs next to payroll. Use VLANs and ACLs to restrict device-to-device communication to what’s strictly necessary, and separate IT from OT/facilities networks.
CISA emphasizes segmentation as a core technique to limit blast radius and lateral movement. Pair segmentation with a Zero Trust approach – assume no implicit trust based on location, and verify device identity and posture each time instead.
Enhance control with IoT-specific tools. For instance:
- 802.1X / WPA3 Enterprise on WI-Fi to authenticate devices against a RADIUS/IdP and enable Protected Management Frames, if possible
- MUD (IETF RFC 8520) to let devices advertise intended network behavior and automatically apply minimal ACLs
- Easy Connect / DPP for secure QR-code onboarding of screenless devices at scale
Kill all defaults, harden and minimize
Default credentials are still a key path for compromise. CISA’s Secure by Design guidance urges eliminating default passwords altogether. In your environment, you should refuse devices that ship with universal defaults and enforce unique per-device credentials.
Disable unnecessary services such as UPnP and SSDP/mDNS across segments, change administration portals to non-default URLs/ports when supported, and enforce multi-factor authentication (MFA) for dashboards and cloud portals.
A quick list of tips for each device type:
- Rename SSIDs and hide management planes behind VPN or SSO
- Turn off unused radios/ports and vendor “remote access” features where possible
- Log to a central syslog/SIEM and time-sync devices (NTP) for forensics
Secure the data paths and protocols
Many smart-office systems communicate over MQTT/HTTP to cloud services. Require TLS everywhere and prioritize mutual TLS (client certificates) for device-to-broker communications. Also, enforce topic-level ACLs and least privilege on the broker.
If devices can’t meet that bar, isolate them more aggressively at the network layer and proxy their traffic through gateways you control.
Patch, update and plan for end-of-life
Ask for a firmware update policy and vulnerability disclosure process before you buy. Keep a calendar for update windows (signage players, printers, cameras) and test in a staging VLAN first. NIST’s IOT work and ETSI EN 303 645 both foreground keeping software updated and having a coordinated vulnerability process, so you should prioritize making these non-negotiable.
End-of-life (EOL) policy should include the following:
- Flag devices that stop receiving security updates
- Quarantine EOL devices to a heavily restricted network, or replace them
- Factory-reset and securely wipe storage on decommissioned devices for safe user-data handling
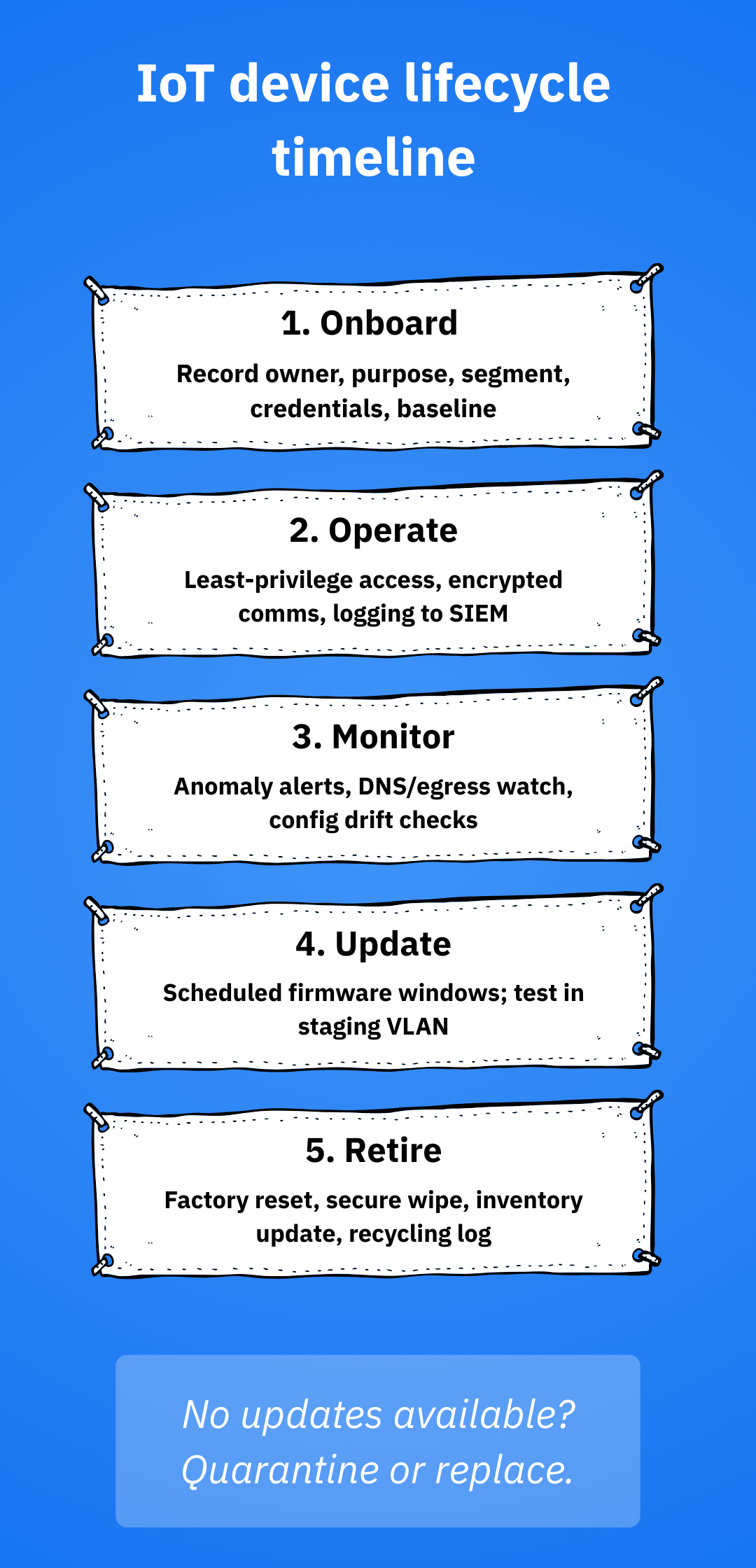
Monitor continuously and respond fast
Even with segmentation, always assume that some devices will misbehave. Baseline normal traffic (destinations, ports, talkers) and alert on anomalies. For instance, cameras shouldn’t phone random IP addresses, so act immediately if you see anything suspicious.
Stream logs to your SIEM, watch for DNS beacons, and use NDR to spot cross-segment movement. Last but not least, aim to apply Zero Trust continuously: verify identity and posture per request, not once at join time.
Optional tooling tip (for small offices on prosumer gear): If your smart office runs on NETGEAR Orbi/Nighthawk hardware, consider enabling NETGEAR Armor (Powered by Bitdefender). Armor adds router-level threat blocking and safe-browsing filters, runs vulnerability assessments to flag weak passwords, outdated firmware or risky settings on connected devices, and can extend protection off-network via its mobile/desktop app. Treat it as a compensating control that complements (not replaces) segmentation, strong credentials and regular patching.
Quick reference checklist
- Maintain an owner-tagged IoT inventory with lifecycle metadata
- Procure to NIST 8259A / SP 800-213, ETSI EN 303 645, ISO/IEC 27400
- Enforce network segmentation (VLANs, ACLs), WPA3-Enterprise/802.1X, MUD and DPP onboarding
- Remove defaults, require unique credentials and MFA, and restrict services
- Use TLS everywhere, prefer mTLS and broker-level least-privilege for MQTT
- Plan updates and EOL from day one and insist on vulnerability disclosure policies

Conclusion
Although IoT devices have increased the attack surface for smart offices, they’re not breached because they’re “smart,” but because they’re unmanaged. Treat every connected device like a business system with an owner, a purpose and guardrails.
If you do nothing else, make visibility your north star. Buy against recognized baselines, separate what shouldn’t talk, remove defaults, encrypt the pipes and plan for updates and end-of-life from day one. Perfection isn’t the goal – reducing blast radius and catching drift early on is. With a lean, repeatable playbook, you can keep the convenience and innovation of a smart workplace without gambling on its security.
Frequently asked questions about IoT security for smart offices
What is an IoT office?
An IoT office is a workplace where everyday equipment, such as lights, thermostats, printers, cameras, meeting room panels and badge readers, is connected to the network to collect data and automate tasks. These devices optimize energy use, security, and maintenance, often via cloud dashboards and mobile apps. The upside is efficiency and comfort; the downside is a larger attack surface.
What is the weakest point in IoT security?
The weakest point in IoT security is usually lack of proper management. Unknown or poorly owned devices running default credentials on flat networks with outdated firmware are often a digital hazard for the whole office network. It is often theorized that an IoT network is as strong as its weakest device. In other words, if a weak device is left on a network, threat actors could exploit it and breach the network.
What is IoT in smart buildings?
IoT in smart buildings refers to connected devices, such as sensors and controllers, HVAC, lighting fixtures, elevators, and access control, controlled by a building management system to improve comfort, safety and energy efficiency.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks