Five Things You Need to Know About the Cyberwar in Ukraine

Einstein once said he doesn't know what weapons will be used for the next World War, but he fears the war after it will be fought with sticks and stones. A new world confrontation is highly unlikely at this moment but the weapons used are as high-tech as it gets as some of them use code instead of gunpowder.
As the first Russian troops started rolling into Ukraine, cybersecurity experts everywhere braced for the worst -- some of the biggest cybercrime gangs in the world are known to have close ties with the Russian government and operate from so-called “hacker heavens” in the ex-Soviet space.
The fears came to life when the Conti ransomware group publicly pledged its support to the Russian cause. Several Ukrainian banks and public institutions were hit by DDoS attacks and data-erasing malware, but, retaliatory attacks against western public institutions and companies have remained scarce. For now.
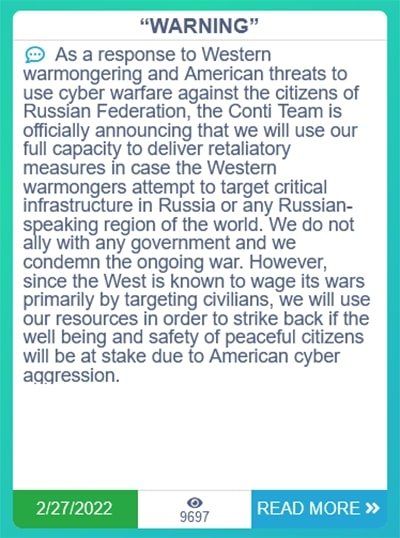
Is this a sign that most organizations have correctly assessed the danger and strengthened their security, or is it just the calm before the storm?
Here’s what we know so far:
1. For now, Ukraine is the main target
Most of the cyberattacks so far have focused strictly on hitting Ukrainian organizations, in at least three separate waves:
- on Jan. 14, 70 government websites were defaced and taken offline, including the Ministry of Foreign Affairs and the Security and Defense Council. However, according to the reports no data was leaked, and downtime lasted a few hours. Almost at the same time, the Microsoft Threat Intelligence Center (MSTIC) reported active malware, dubbed WhisperGate, that was made to look like ransomware but lacked a recovery component. This meant it was actually designed to destroy data.
- on Feb. 15, Ukraine's two largest banks were taken offline by a massive Distributed Denial of Service (DDoS) attack that also affected mobile apps and ATMs.
- on Feb. 23, another DDoS attack took out military and government sites while a data wiper called HermeticWiper was detected on hundreds of computers belonging to various Ukrainian organizations. Simultaneously, MSTIC detected a trojan dubbed FoxBlade that can surreptitiously weaponize victims’ computers and use them in DDoS attacks.

Despite the obvious interest in disrupting the Ukrainian infrastructure there’s no guarantee malware like WhisperGate, HermeticWiper or FoxBlade can’t spill over to computers in other countries too. Additionally, as more countries join the sanctions against Russia, Russian-backed hackers could shift their focus and retaliate.
2. Ukraine is fighting back
Kremlin-backed hackers may have had the benefit of surprise, but the cyberwar isn’t one-sided at all. On the contrary, after the initial shock, the Ukrainian government called for the assembly of a volunteer IT army that quickly started retaliating: the hacker collective Anonymous took down the Belarussian Railways internal network and almost 300 company websites in Russia. Conti’s internal messages and source code were leaked, the Kremlin site was hacked, the Russian Nuclear Institute and the Russian Space agency suffered data breaches and Russian tv channels were hacked to show real footage from Ukraine.

3. It’s not just about companies
There’s a general belief state actors only go after companies and public institutions, but that’s not the case. Sometimes they also target regular people. In late February, the national Computer Emergency Response Team for Ukraine issued a warning of a major phishing campaign against military personnel. Even more worrying, European officials were targeted with malware in an apparent attempt to disrupt efforts to help Ukrainian refugees.
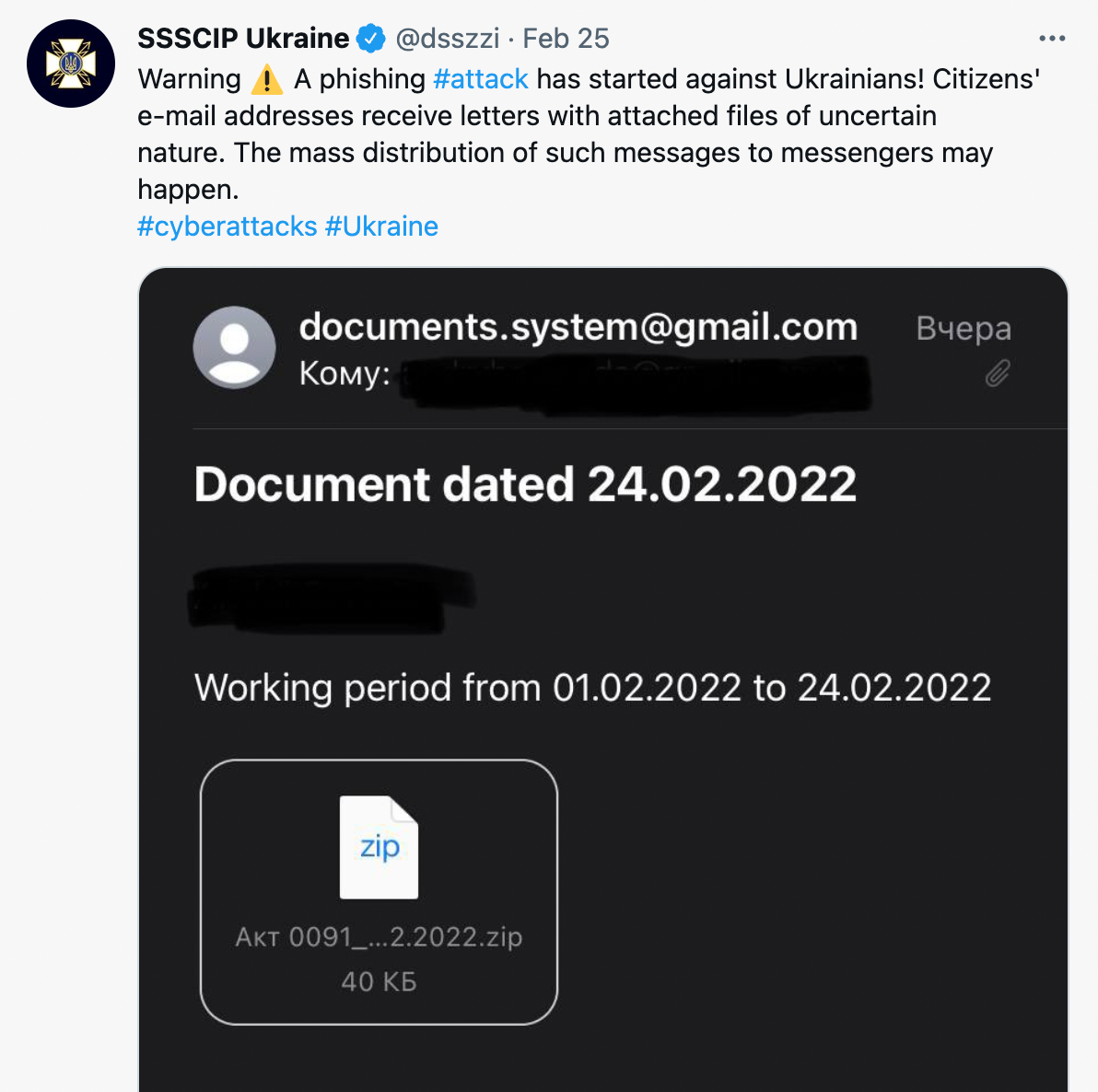
Whether they’re looking to gather intelligence, phish for credentials or obstruct humanitarian efforts, state actors don’t discriminate when it comes to targeting regular people. Even if you’re not directly involved in the current situation, it’s always a good idea to protect your devices from malware, update them regularly, use strong passwords and watch out for scams and phishing emails.
4. There are third parties taking advantage of the situation
Researchers at Bitdefender Labs picked up waves of fraudulent and malicious emails exploiting the humanitarian crisis and charitable spirit of people across the globe. The conflict in Ukraine is a gold mine for scammers and criminal groups that aren’t necessarily politically involved but love making money. One of the preferred methods is using fraudulent emails asking recipients to donate money. Scammers are impersonating the Ukrainian government, international humanitarian agency Act for Peace, UNICEF, and the Ukraine Crisis Relief Fund to ask for crypto donations.
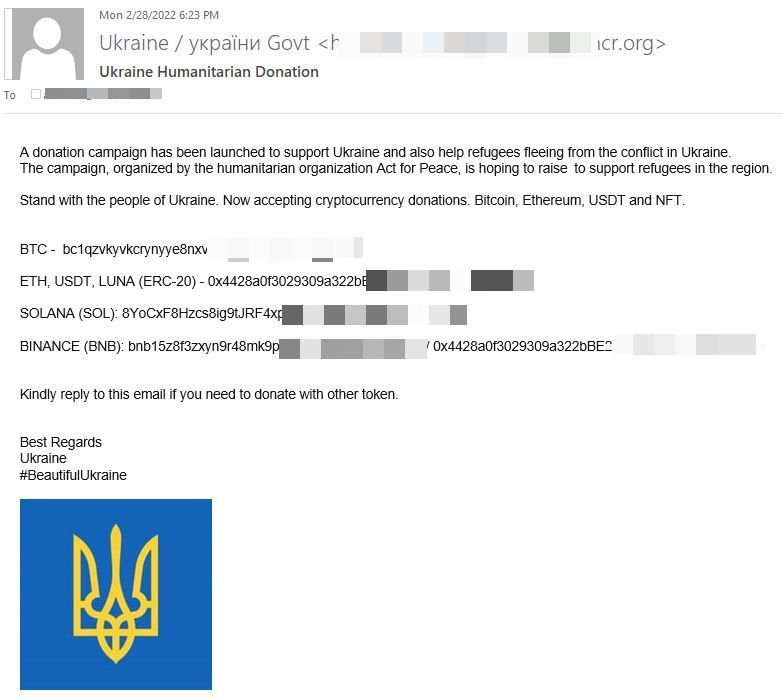
5. Cyberwar could be the next cold war
The lack of devastating attacks on western targets on the scale of Colonial Pipeline or Kaseya doesn’t mean the danger has passed. Even if the military conflict ends, the cyber conflict is likely to persist for years, and all parties involved, whether government agencies, private companies, or regular users, must come to terms with it.
Whether we like it or not, cyberattacks used for sabotage or spying aren’t going away anytime soon for a number of reasons: they’re cheap and efficient, they can be launched from anywhere in the world, they bring in good money, state responsibility is hard to prove and, most importantly, the number of potential targets is virtually unlimited.
For more tips, please check our dedicated cybersecurity guide in armed conflict zones.
In response to the military crisis and increased cybercriminal activity, Bitdefender & the Romanian National Cyber Security Directorate (DNSC) are offering free cybersecurity protection for any Ukrainian citizen, company or institution, as long as necessary.
tags
Author

Radu is a tech-geek with 15 years of experience in writing, journalism and copywriting. When he’s not writing he’s probably taking something apart, trying to figure out how things work.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









