Digital Twins Double the Attack Surface

Digital replicas of your home introduce new vulnerabilities that attackers can exploit – unless you secure both worlds.
The rise of digital twins in smart homes
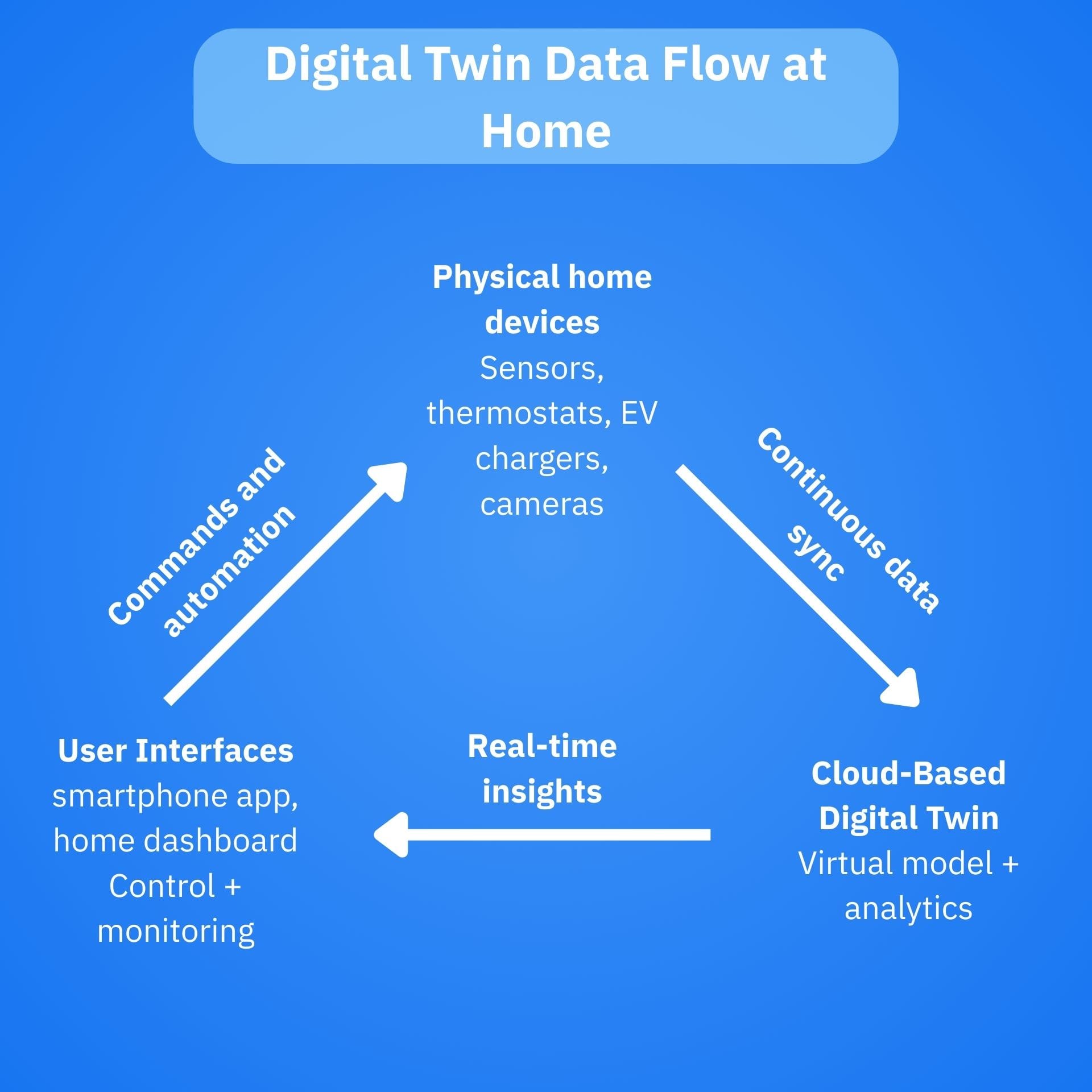
Your home is slowly turning into a digital mirror. From smart thermostats and EV chargers to entire home energy dashboards, consumer tech is moving toward building “digital twins,” virtual replicas of your physical environment that continuously sync with real-world data. These digital twins are powerful and convenient, but they can also attract threat actors if not properly secured.
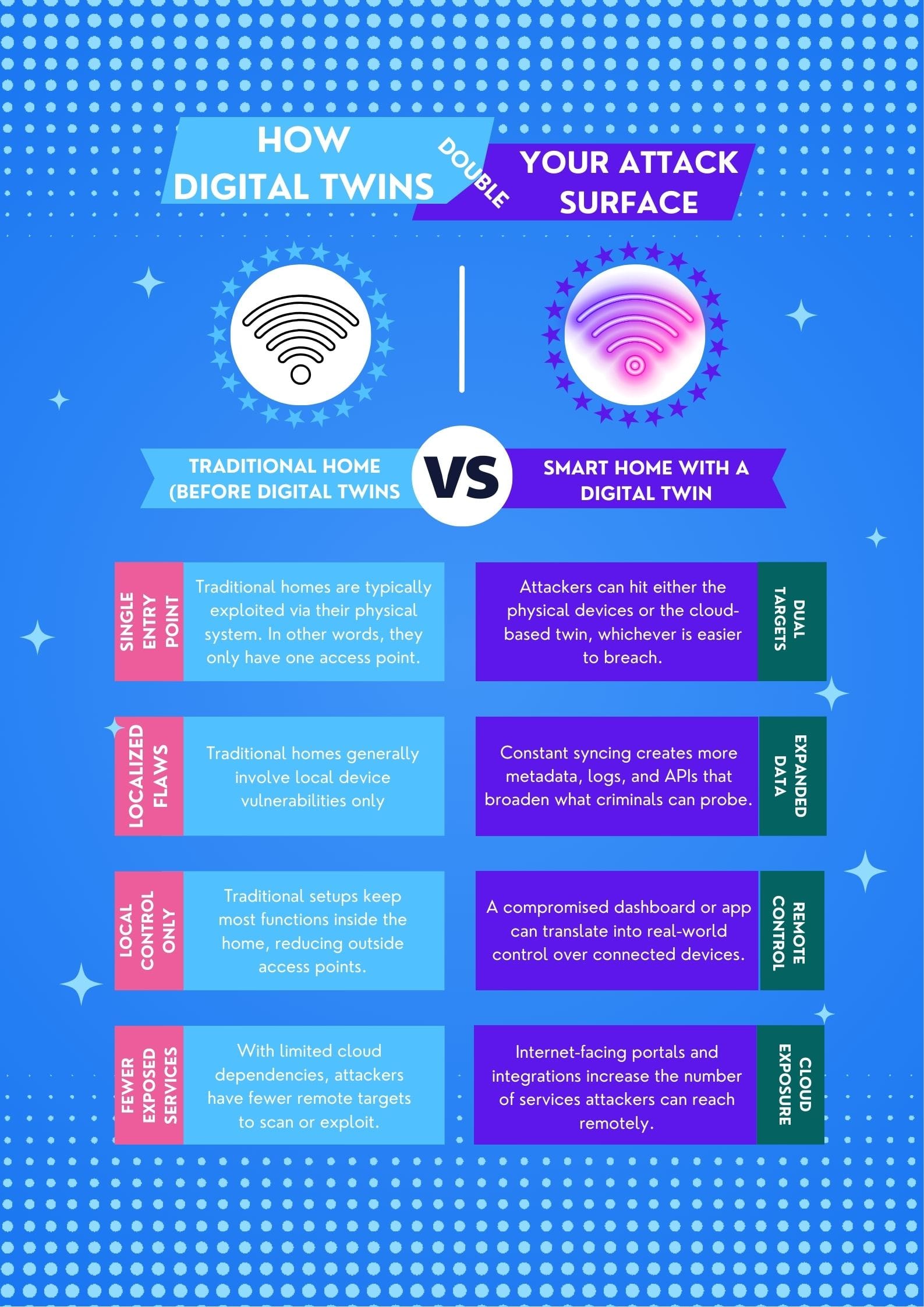
When you create a digital twin of a system, the attack surface effectively doubles: criminals can target either the physical system or its virtual counterpart, whichever is more convenient to reach and breach.
In this guide, we explain what digital twins are, why they are a growing risk for smart homes and connected consumers, and how to strengthen your digital resolve.
What is a digital twin?
In industrial settings, a digital twin is a detailed virtual model of a factory, wind farm, or power grid that continuously reflects real-world status and performance. At home, we are seeing a more consumer-friendly version of the same idea, in the form of:
- Smart home apps that show every light, sensor, camera, and plug as an interactive map of your house
- EV charging platforms that mirror your vehicle’s battery, charging schedule and location in real time
- Home-energy dashboards that twin your solar panels, heat pumps and battery storage
All these examples rely on dense networks of IoT sensors, cloud services, APIs and mobile apps to constantly sync data between the physical and digital realms. However, the more objects, sensors, and connections you add to power a digital twin, the wider its exposure and the larger the potential attack surface.
Why digital twins double your attack surface
Digital twins attract threat actors for two big reasons: reach and detail.
1. Two ways in instead of one
When a twin exists, perpetrators can go after their malicious objective in two ways:
- By breaching the physical system (routers, smart plugs, cameras)
- By exploiting the digital twin environment (cloud dashboards, web portals, APIs, mobile apps)
Sometimes, real-world devices can be hard to reach, as they may be placed behind NAT or firewalls, but cloud-hosted twins are usually exposed over the internet and easier to probe.
2. A blueprint for your house
Digital twins that mirror your home, car or energy system can serve as virtual blueprints for attackers: they show what you own, how everything is wired together, and sometimes even your daily routines. Compromised twins can leak sensitive data, help map vulnerabilities or support targeted attacks against the physical system itself.
3. IoT devices as weak links
IoT gadgets are often the soft underbelly of a digital twin setup. They are always connected, constantly exchanging data and are often poorly secured. Many can be discovered with search engines such as Shodan and abused in man-in-the-middle attacks, botnets or credential-stuffing campaigns.
For everyday users, this means the very smart devices that feed your real-time dashboards also enlarge the attack surface that threat actors can exploit.
Real-world risks for smart homes
A common misconception is that only industrial environments are exposed to risks associated with digital twins. However, you don’t need to own a power plant to be in this situation. If your home relies on cloud dashboards and “digital replicas” of devices, you can be easily exposed to the following scenarios:
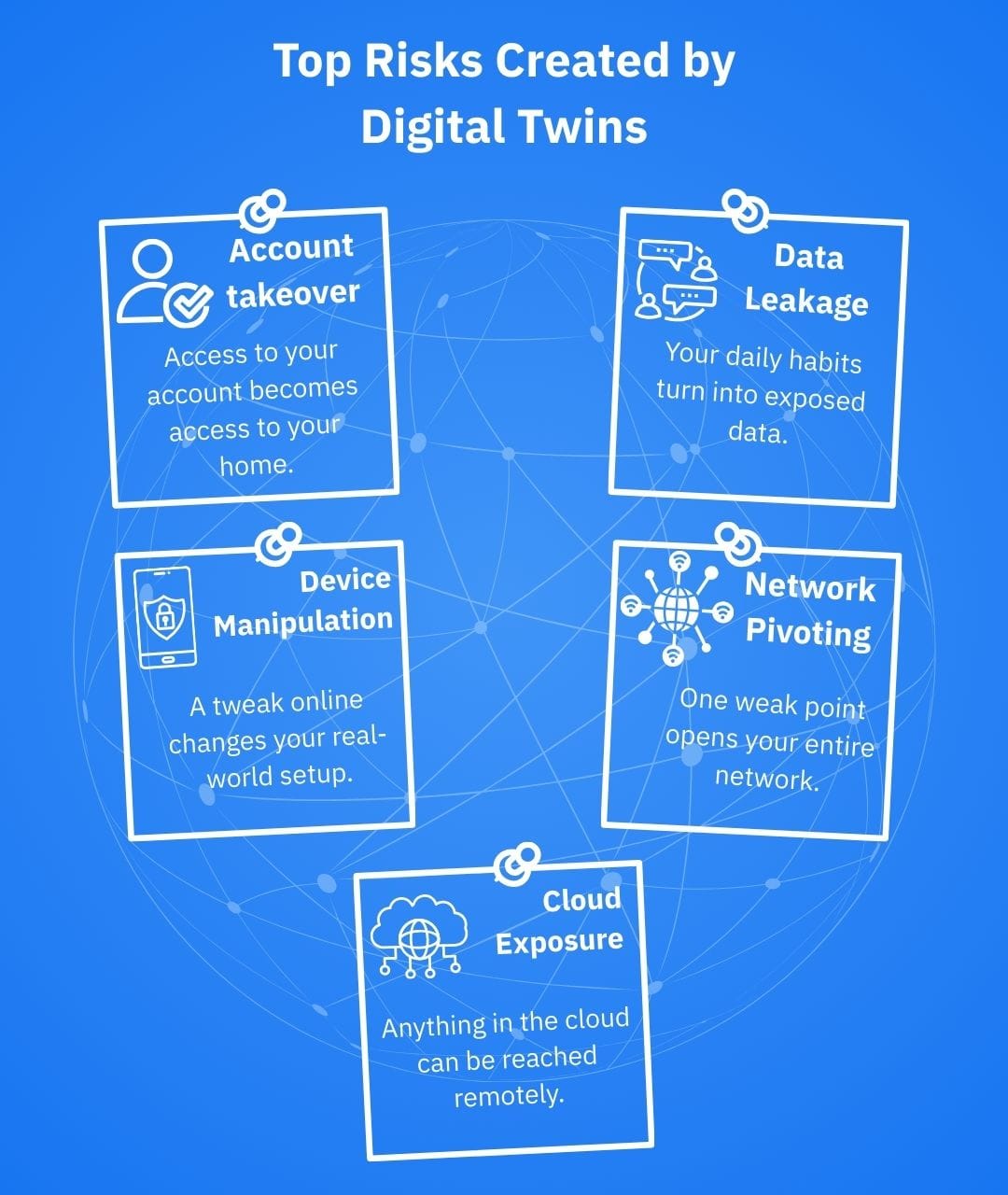
- Account takeovers: Weak or recycled passwords give threat actors access to the twin, allowing them to see devices and routines. Some of the more severe cases had perpetrators assume direct control over breached devices.
- Data leaks and profiling: Compromised dashboards can expose occupancy patterns, energy usage, EV locations, camera feeds and more. These details can help criminals carry out even more malicious activities such as stalking, doxxing, or real-world burglary planning.
- Manipulation of physical systems: Changing thermostat targets, EV charging times, or access rules in the twin can translate into real-world consequences, from wasted energy and higher bills to safety and privacy issues.
- Stepping-stone attacks: Once inside your smart-home environment, threat actors can pivot to other devices on your network (PCs, phones, NAS) for malware deployment or data theft.
How to shrink your digital-twin attack surface
Although this digital twin situation seems grim, the good news is that you don’t need to be an OT security engineer to reduce your risk. These consumer-friendly practices can go a long way:
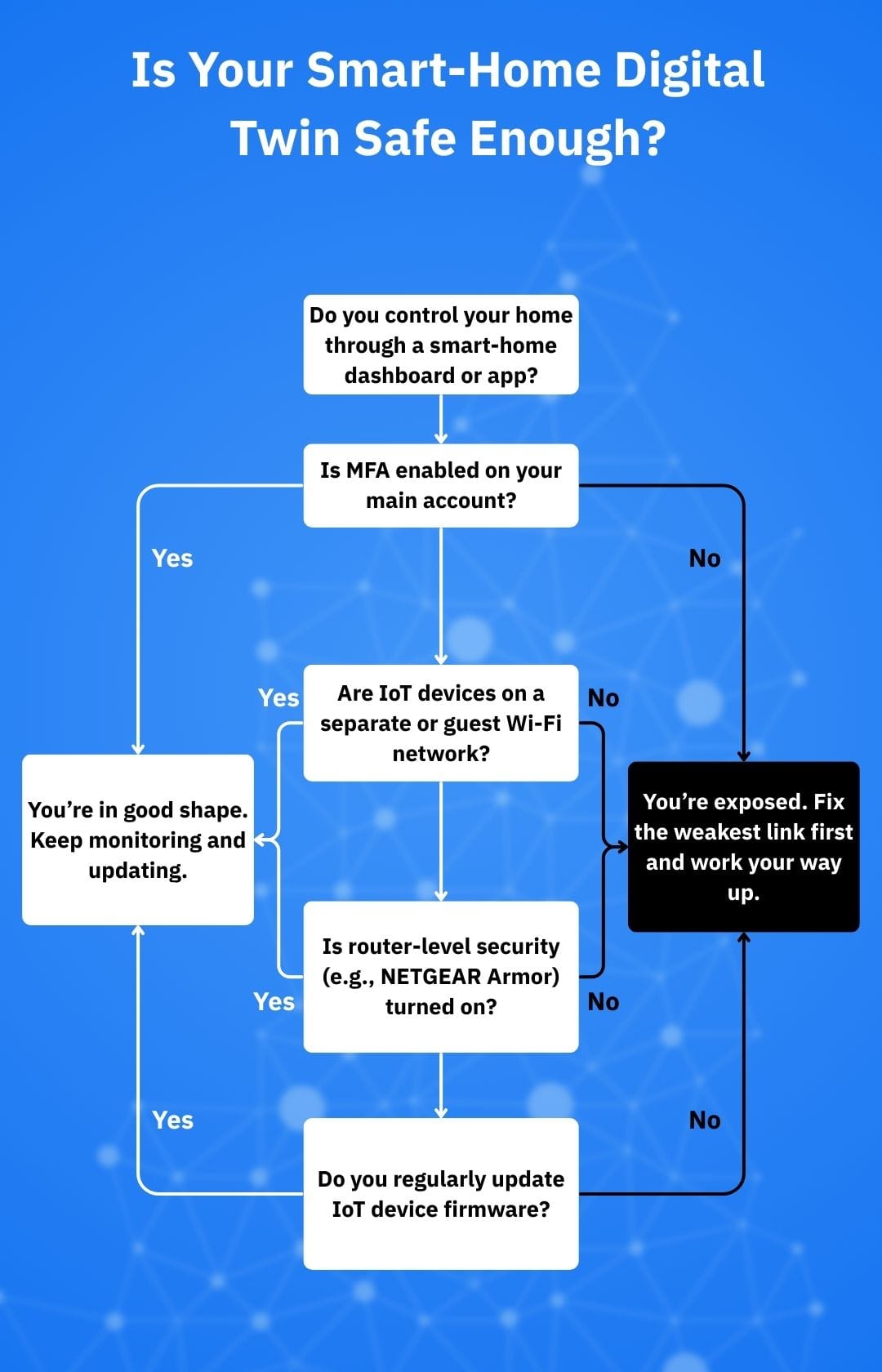
1. Harden your account and apps
Your digital twin usually lives in the cloud, fronted by an app or web portal. Treat those logins as crown jewels:
- Always enable multi-factor authentication (MFA) on smart-home, EV, and ISP/router accounts
- Use unique, strong passwords. Opt for a reputable password manager such as Bitdefender SecurePass, if possible
- Regularly review app permissions and revoke access for old devices and guests
2. Secure the IoT network feeding your twin
Every sensor and camera feeding your dashboards is another potential entry point. To reduce the risks, consider:
- Keeping your router firmware and IoT devices fully upgraded. Many security flaws are patched only via firmware updates
- Segregating IoT devices onto a separate Wi-Fi or guest network if your router allows it – that way, compromised gadgets can’t easily reach your laptop or work PC
- Disabling unused remote-access and UPnP features unless you absolutely need them
3. Use network-level protection
Even careful users can’t manually monitor dozens of devices and connections. This is where router-level protection such as NETGEAR Armor (powered by Bitdefender) comes in.
NETGEAR Armor runs on compatible NETGEAR routers and mesh systems such as Orbi and Nighthawk and adds:
- AI-powered threat detection for every device on your network, including IoT gadgets that can’t run traditional antivirus software
- URL and phishing protection to block access to malicious sites at the router level
- Vulnerability assessment that scans for weak passwords, open ports and outdated firmware across your smart-home devices
- On-the-go device protection and VPN features via Bitdefender apps, so your phones and laptops stay protected even when outside the home
For a household that increasingly relies on digital-twin-style apps and dashboards, this kind of always-on, network-wide defense acts as a safety net when a single gadget or account is misconfigured or forgotten.
4. Adopt a ‘trust but verify’ mindset
Finally, treat your digital twin like any online service that can be compromised:
- Regularly review activity logs where available (logins, new devices, automation changes)
- Limit data sharing and integrations to what you genuinely need and disconnect third-party services you no longer use
- Assume that any dashboard that can control real-world devices needs the same care as you would give to online banking
Frequently Asked Questions (FAQ)
What are the four types of digital twins?
The four types are component twins, asset twins, system twins and process twins, each representing increasingly complex models of a real-world system.
What is a real example of a digital twin?
A common example is a smart-home energy dashboard that mirrors your home’s solar panels, HVAC system and battery usage in real time.
Is digital twin an IoT?
A digital twin is not IoT itself, but it relies on IoT devices and sensors to collect real-time data and accurately replicate the physical environment.
Do digital twins use AI?
Yes. Many digital twins use AI and machine learning to analyze data, predict behavior, detect anomalies and automate decision-making.
Conclusion
As digital-twin technology filters from factories into homes, it brings both convenience and complexity. The key takeaway for consumers is simple: every digital replica of your home, car or energy system is a doorway that needs a lock.
Strong accounts, hardened IoT devices and network-wide protection such as NETGEAR Armor give you a fighting chance to enjoy the benefits of digital twins without handing threat actors a convenient map of your life.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks