A miracle: A company says sorry after a cyber attack - and donates the ransom to cybersecurity research
One of the sad truths about this world of seemingly endless hacks and data breaches is that companies just won't apologise.
Even when customers, partners, and employees are left wondering when their data will be published by malicious hackers on the dark web, breached organisations will seemingly do everything they can to avoid saying what seems to be the hardest word of all: sorry.
Hacked businesses will stall, waffle, and hide behind phrases like "out of an abundance of caution" and "we take your security and previously seriously."
What they typically will not do is admit they goofed up, confess to their mistakes, and promise to make things better.
It's as though lawyers whispering in their ears to "admit nothing" in fear of a class action suit has won, and never mind building trust with your clients, business partners, and workers.
And the sad truth is that every hour of hiding behind bland security advisories about "incidents" damages trust far more than a clear apology ever would.
Which is why I found it so refreshing to read a blog post by payment processing service Checkout.com.
It appears that the ShinyHunters hacking group are to blame for a heist which accessed data from a legacy third-party cloud storage system operated by Checkout.com.
According to Mariano Albera, CTO of Checkout.com, it is thought that "less than 25%" of the company's current merchant base was affected by the data breach of a system that "was used for internal operational documents and merchant onboarding materials at that time."
Well, it is certainly good news to hear that it was not Checkout.com's live payment platform that was compromised, and payment card information was not taken by the hackers, and that instead it was an old system used "in 2020 and prior."
Checkout.com received a ransom demand from the hackers (who had exfitrated data rather than encrypted it), who threatened to publish the stolen information on the dark web if payment was not received.
It was Checkout.com's response that I really liked, and that is so unusual to hear from hacked businesses today. Checkout.com didn't give excuses. Instead, it publicly disclosed the incident, and apologised,
Yes, they actually said the word "sorry."
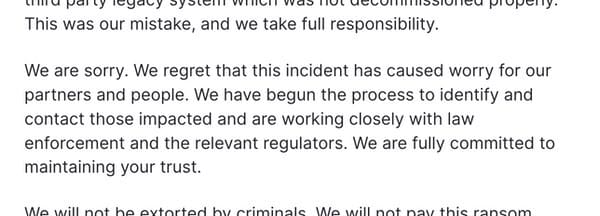
This was our mistake, and we take full responsibility. We are sorry.
Wow - that feels good to hear!
But Checkout.com went further...
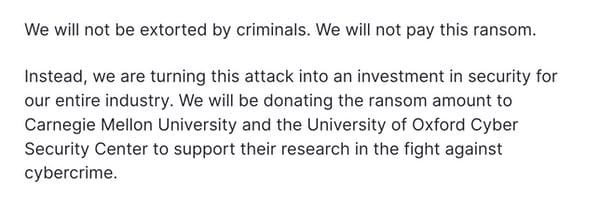
We will not be extorted by criminals. We will not pay this ransom... We will be donating ransom amount to Carnegie Mellon University and the University of Oxford Security Center to support their research in the fight against cybercrime.
How brilliant is that? And what a glorious contrast to the typical "We're investigating," "We take security seriously," and "We have no further comment at this time..."
But good as this is, let’s not get carried away just yet.
Because the uncomfortable truth is that although Checkout.com communicated quickly amd clearly, and took responsibility for what had occurred, it does not erase their security failure.
The data was found by the hackers on a legacy system that the company had seemingly not used since 2020. Legacy systems are a liability - often left still accessible, unmonitored, misconfigured, and unpatched.
Ultimately the reason that this data breach happened was because a legacy data storage system had not been fully decomissioned. For all the plaudits I am giving Checkout.com for its handling of the breach, there is still evidence of a process failure.
Other companies can avoid falling into this type of scenario themselves by looking for potential problems before they are found by malicious hackers.
Instead of waiting for incidents to occur, security teams should conduct pre-mortem exercises - exploring what systems exist that teams have forgotten about, which legacy platforms still have valid credentials, what would be easiest for an attacker to find, and what data exists in systems which currently fall outside security monitoring.
Be more proactive in your attitude to securing your data, identify the vulnerabilities before they become breaches, and your company won't be the one wondering if it is time to say "sorry" or not.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsYou might also like
Bookmarks
