A Heads-Up on Stalkerware, the Wolf Software in Sheep’s Clothing

Stalkerware is more prevalent than people think and more insidious than they imagine. Some iterations are freely distributed through official app stores, and a search using more unsavory methods will turn up others. Whichever the case, the blend of legal and illegal apps makes them all the more dangerous, especially for unsuspecting victims.
If we say that an application allows someone to remotely track your location, read texts or activate the camera and microphone, you would call that malware. Because these types of apps can have some legitimate uses, such as parental control or surveillance functions, it doesn’t mean that people can’t use them maliciously.
The definition of stalkerware is fluid, and plenty of companies would argue that they don’t make such a product, even when people can use their software for malicious purposes. And we’re not counting all the software designed specifically for spying on people, freely distributed through other means.
Why stalkerware is scary
The definition that really matters is the one concerning potential victims. If software can be deployed and used to spy on someone, it doesn’t really matter if it falls in any “official” category. If it behaves like stalkerware, it has to be treated as such.
Stalkerware is often used in abusive relationships, in which partners deploy it to monitor their spouse or friends illegally. It is also being used by all types of abusers to keep track of victims. Whether they are partners, family members friends, colleagues, or someone you’ve just met online, these abusers rely on software to stay in control, abuse and stalk from afar. Often times, these applications can grant the stalker access to:
· the victim’s location in real time, so they can track every move the victim makes
· access to mobile device sensors like camera and microphone so that the attacker can monitor ambient conversations
· access to the victim’s messages, call logs or chat history
· Access to the files on the device, such as pictures and incoming multimedia files received via IM apps
Stalkerware is such a pervasive method that it’s already become a severe problem with the advent of intelligent devices that allow such spying methods that don’t require any skill.
Signs that you might be a victim of stalkerware
Since many of these apps don’t reveal their presence on compromised devices, it’s difficult to tell if you might be a victim without a security solution installed. In some situations, users will notice that their phone heats up for no apparent reason or that the battery seems to last less than it used to. Some newer OS versions might inform the user that some apps access the camera or that the GPS is used in the background.
More than 1,000 different apps can be categorized as stalkerware, some of which are available in the official stores. While it’s true that Google and Apple have pruned the stores of many of these types of apps, they’re not gone completely.
While the iOS platform is a lot more controlled, making it more challenging for people to install their own apps, Android has fewer limitations and is more open. This is one of the few instances where an open platform is a drawback.
Let’s look at the 10 most “popular” stalkerware apps detected by Bitdefender on the Android platform in the past three months.
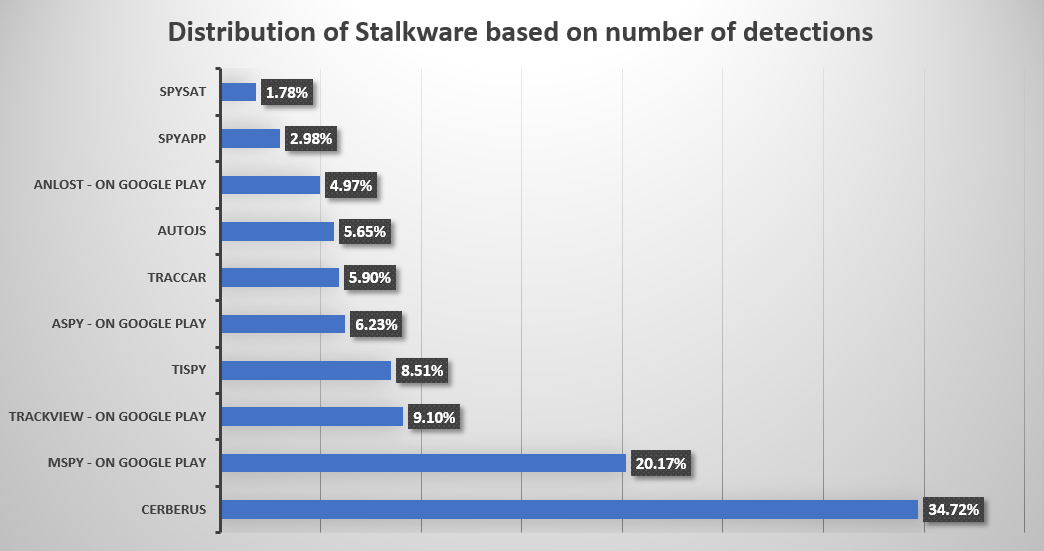
As you can see, two out of the three most-detected apps are available through the Google Play Store. The first one, Cerberus, is probably the most famous. The official website says that it’s an app for “phone theft, parental control, or personal safety,” but they offer a disguised version that will appear as System Framework and have a stock Android icon. The level of access Cerberus requests should worry anyone.
The second one is called MSpy, and the company says it’s available for all platforms, including Windows and macOS. The claim that it works on iOS is heavily disputed, but the company tries to get people to use it with things like “You’re here because you want to read their iMessages, see their pics and videos, and discover what they’re up to on their iPhone.” Of course, they say it’s for parental control.
The third place is occupied by TrackView, which is “designed for family safety applications. It turns your smartphones, tablets and PCs into a connected IP camera with GPS locator, event detection, alert and cloud/route recording capabilities.” Sure, you can use it like that, but functionalities such as remote audio and video recording, two-way audio, and remote control of the front and rear camera switch are enough to trigger the Bitdefender detection.
Stalkerware requires the best security
Victims of stalkerware often have no clue that their device has been compromised, but the presence of stalkerware applications can be easily detected by security software such as Bitdefender Mobile Security. Even if someone could get ahold of their phone, users can set up the security app to block sideloading or even installations from the official store.
The Bitdefender mobile security solutions detected 100% of threats in a real-world test, underlining the need for the best possible protection on mobile and desktop systems. Stalkerware developers will continue to improve their apps to circumvent existing operating system protections or even security solutions.
Even mobile operating system vendors continue to make their operating systems more secure, there will always be a market for stalkerware, for individuals who want to abuse their partners or simply spy on others. It’s yet another reason why using a security solution on a mobile device is not only a good idea; it’s mandatory.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








