What’s Next in IoT Policy and Regulation in 2025

With Internet of Things (IoT) devices in nearly every home, regulators worldwide are stepping up to enforce meaningful cybersecurity standards.
The need for regulators in the IoT field
From smart fridges to voice-activated assistants and internet-connected light bulbs, the Internet of Things (IoT) is no longer a futuristic concept – it has found its way into our lives.
But as these devices increasingly tether our daily activities to the digital world, an important question arises: “Who’s making sure they’re safe?”
The answer is regulators.
For years, consumers have faced the issues of insecure IoT ecosystems head on – default passwords, unpatched vulnerabilities, nonexistent privacy policies, or devices that phone home to places you’ve probably never even heard of.
In 2025, things finally seem to be looking up. Governments and standards bodies worldwide are taking steps to establish clear rules for how manufacturers must build, maintain, and label connected devices.
In this article, we break down the latest developments in IoT policy and regulation, what they mean for you, and how you can make smarter, safer choices when it comes to connected tech.
A modern solution for a modern problem
In 2025, three key developments in IoT regulation are shaping the future of connected devices:
1. The European Union’s Cyber Resilience Act (CRA) introduces robust cybersecurity requirements for all connected products sold in the EU.
2. The Radio Equipment Directive (RED) is being updated with mandatory cybersecurity safeguards.
3. In the United States, the Cyber Trust Mark aims to help consumers easily identify IoT products that meet federal cybersecurity standards.
Although they differ in approach, all three initiatives aim to mitigate risks at the source by enforcing security-by-design principles.
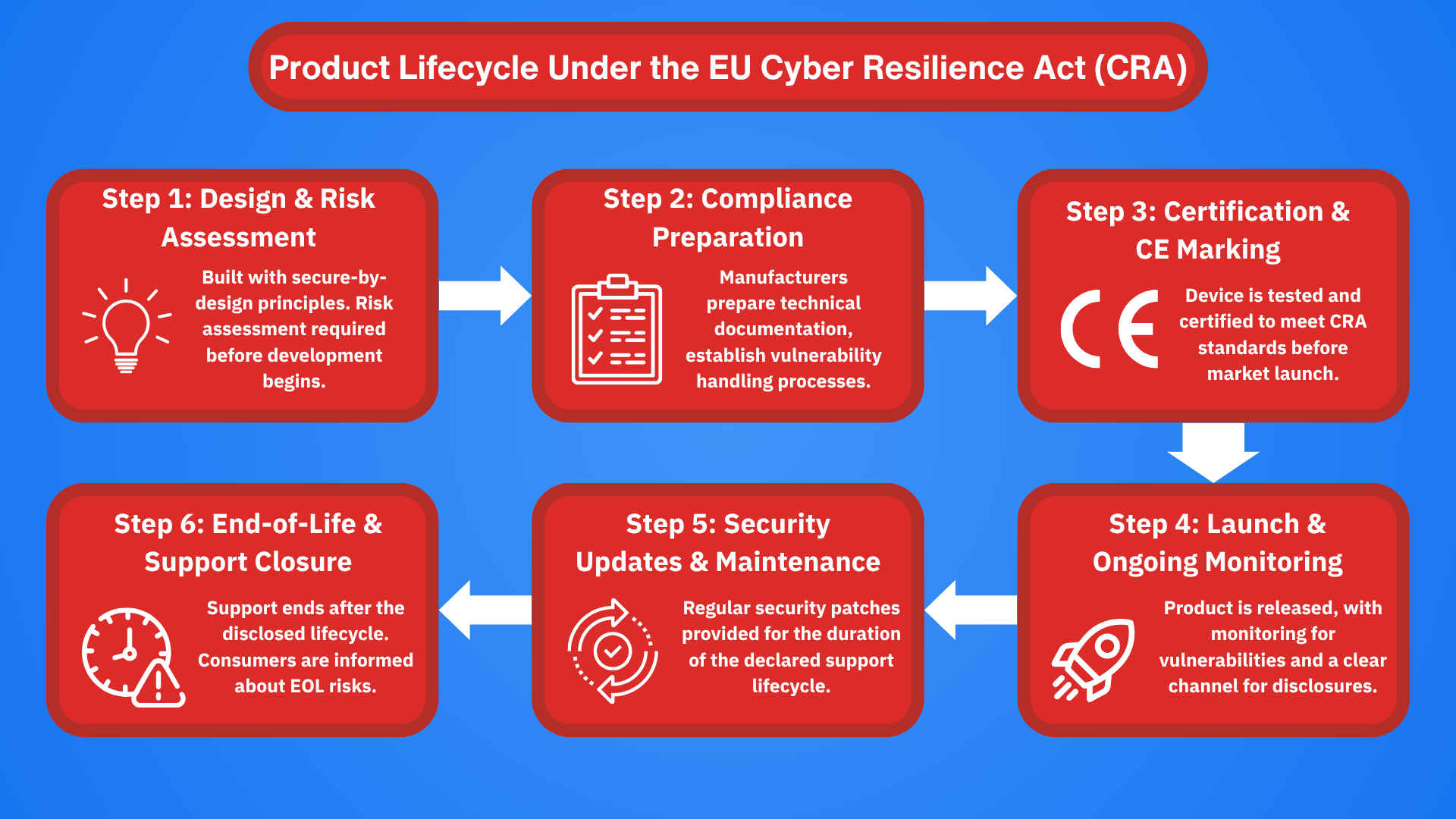
1. The Cyber Resilience Act raises the bar for EU products
If you live in the EU, or buy devices that are ultimately shipped there, the CRA will directly impact the connected products in your home. The act states that any product with digital elements (such as smart devices, wearables and connected toys) must meet strict cybersecurity requirements throughout its lifecycle.
What does that mean in practice?
Manufacturers must:
- Conduct thorough security audits before bringing products to market
- Include mechanisms for vulnerability handling and disclosure
- Provide security updates for a period that matches the expected lifespan of the product
- Maintain documentation to demonstrate compliance
For consumers, this is a major shift from the Wild West of “plug-and-pray” to a more structured, safer IoT ecosystem. Companies that fail to comply could face fines of up to €15 million, or 2.5% of global turnover, whichever is higher.
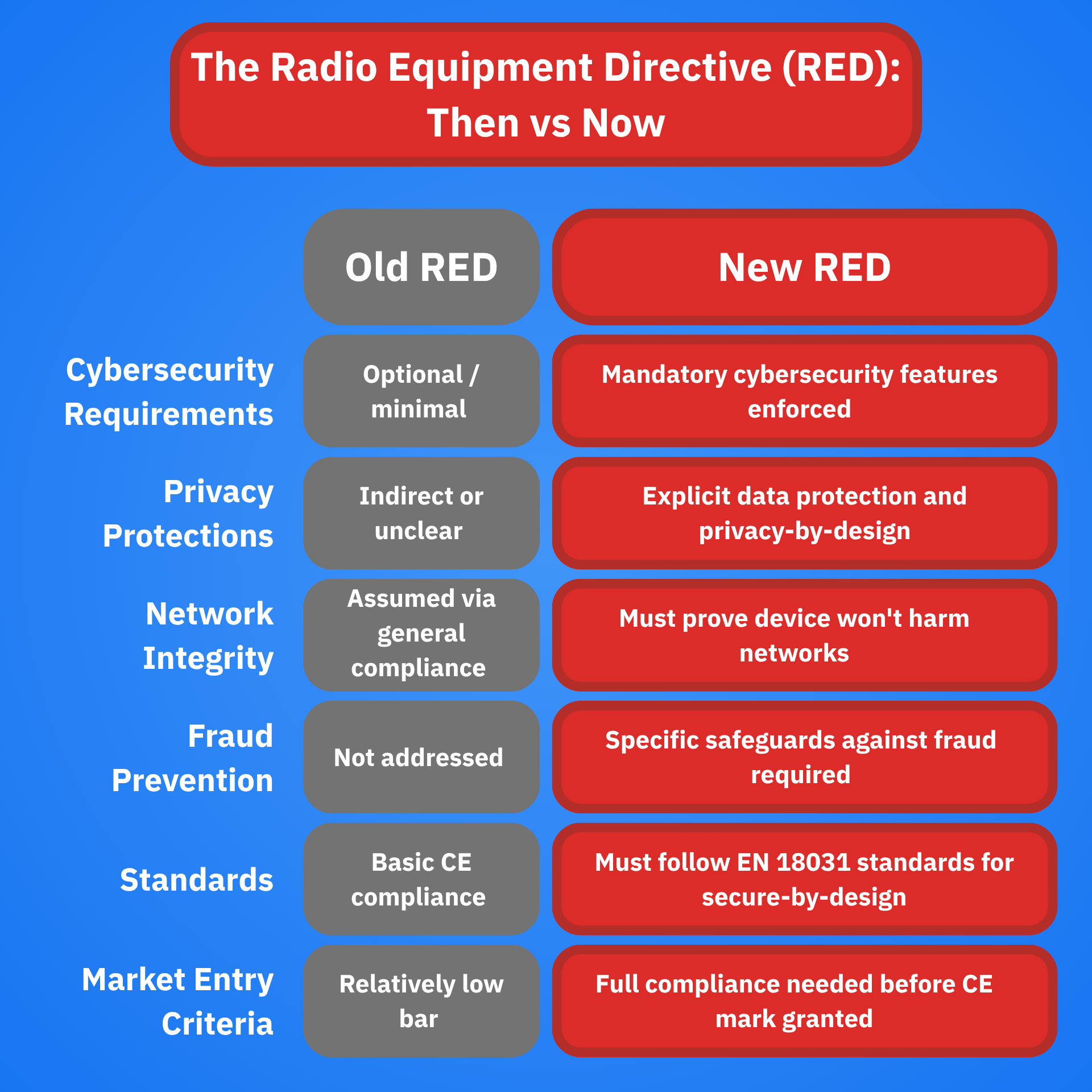
2. RED gets sharper teeth
Also in the EU, the Radio Equipment Directive (RED) is undergoing a cybersecurity revamp. Starting Aug. 1, 2025, manufacturers of wireless products must ensure that devices:
- Don’t compromise communication networks
- Don’t misuse network resources
- Protect personal data and privacy
- Are secure from fraud and abuse
These enhancements make security a prerequisite for market entry. Furthermore, manufacturers must demonstrate compliance with new harmonized standards, such as EN 18031, before attaching a CE mark.
For consumers, this should mean fewer shady imports and more peace of mind when buying that smart speaker or baby monitor.
3. The US Cyber Trust Mark adds security you can see
Stateside, the Federal Communications Commission (FCC), in collaboration with the National Institute of Standards and Technology (NIST), is rolling out the Cyber Trust Mark, a voluntary cybersecurity labeling program for IoT.
The label will resemble the US Energy Star symbol and include a QR code linking to a registry of certified products. By scanning the code, consumers will be able to check if a device meets security requirements such as:
- Unique, non-default passwords
- Secure data transmission
- Software updates
- Incident reporting processes
Although this label is voluntary, unlike the mandatory approach in the EU, the industry is already reacting. Big brands are jumping on board, and retailers are signaling that they could start prioritizing certified devices.
Think of it as a shorthand for “this device won’t turn your toaster into a botnet node.”
What does this mean to you?
These regulations are, ultimately, consumer protection laws. But they only work if you know how to take advantage of them.
Here’s what to expect in 2025 and how to prepare:
1. Expect better default protections
Devices that used to come with admin/admin logins could now be shipped with randomized username/password combinations or QR-based configuration flows. This could prevent threat actors from exploiting default credentials in vulnerable IoT devices to breach networks.
2. Expect more transparency
You’ll see more labels, longer documentation, and more upfront disclosures, such as the duration for which a device will receive security updates. This could significantly reduce the incidence of attacks exploiting outdated devices or, at the very least, raise awareness that certain devices aren’t made to be secure forever.
3. Expect fewer shady imports
In regulated markets, devices that don’t meet the new bar won’t be allowed on the market. This could reduce the chance of unknowingly purchasing devices with subpar security standards, or ones that have been tampered with (i.e., backdoored).
Still… don’t let your guard down.
Although regulations are there to help, they’re not foolproof. Users should still be vigilant and ensure that their household ecosystems are secure by:
- Changing default credentials
- Regularly updating firmware
- Disabling unused features or ports
- Using guest networks for IoT devices

Where we still need work
Despite progress, some aspects remain challenging and can diminish efforts to fully secure the IoT landscape. For instance:
- Global harmonization is missing: The EU and US define compliance differently. That makes things messy for global companies and confusing for consumers.
- Enforcement varies: Voluntary labels are only helpful if consumers demand them. Without that pressure, manufacturers may skip the extra work.
- Legacy devices remain vulnerable: Regulations apply to new products, but millions of outdated, insecure devices are still in use, with no update in sight.
Unfortunately, truly securing the IoT landscape would involve commitments for longer-term support, trade cooperation, and a cultural shift where security sells just as much as convenience or cost.
Final thoughts
On the bright side, IoT regulation in 2025 is a significant consumer milestone. For the first time, we’re seeing real progress in laws designed to protect people from insecure devices in their homes.
As consumers, the best we can do is get informed, look for the labels, and make security a non-negotiable part of our buying decisions.
When everything is connected, everything becomes an attack surface. Regardless of regulation, security always starts with awareness.
Frequently asked questions about IoT policy and regulations
What are the IoT standards and regulations?
IoT standards encompass all the guidelines and specifications that ensure the compatibility and interoperability of devices, including data formats, protocols, and security requirements.
What is the EU IoT policy?
The EU’s IoT policy promotes the use of novel technologies to support the digital transition, covering aspects such as carbon footprint, privacy, security, safety, environmental footprint, and energy consumption.
What is regulatory compliance in IoT?
IoT compliance implies adhering to various operational and security standards that are generally enforced to protect against cyberattacks, unauthorized access and vulnerabilities.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsYou might also like
Bookmarks


