Why Security Software Detects Coin Miners as Potentially Unwanted Applications
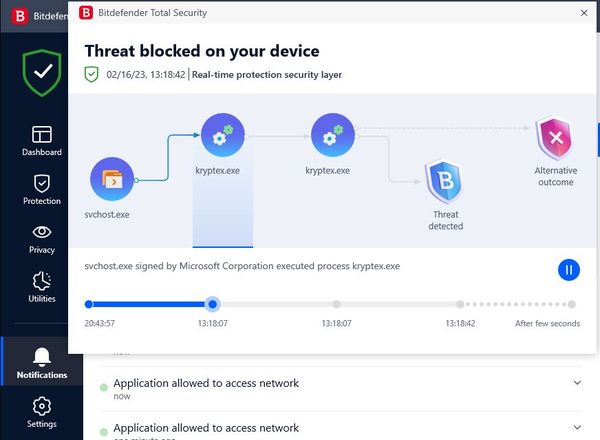
Mining crypto might look like an easy way to make money because so many people are doing it around the world. But installing such software on any PC running a dedicated security solution would immediately trigger the protection software, preventing users from proceeding with the installation unless they know what they’re doing.
Most anyone can carry out crypto mining; install a crypto mining app, set up an account and wallet, and simply start mining away. The mining process is not difficult to understand, as the software makes the complex mathematical calculations needed to validate blockchain transactions. The software uses the PC resources, depending on the type of coin mined. Some mining processes are more demanding than others and some use the CPU, while others are more GPU (graphics card) intensive.
Coin miners, though, are considered Potentially Unwanted Applications (PUA) by any cybersecurity vendor, even if the application is legit. The security solution will block the installation of the software. The reason for this nondiscriminatory filtering is a simple one, even if it’s not apparent to everyone.
Usually, to get any meaningful gains from cryptomining, you need many computers or many dedicated systems built specifically for the task. As you can imagine, this also makes the venture costly.
Criminals know this very well, so they’ve devised attacks and malware that can compromise computers or servers, deploy mining software and allow them to use someone elses’ hardware to make money. While the malware they usually employ is built specifically for the task, the mining software is legitimate. The only change is the configuration file that allows them to redirect the profits to their own wallets.
For example, that’s how Bitdefender tracked an active cryptojacking campaign from a group trying to compromise Linux servers. In that situation, the attackers were trying to mine Monero by using a legitimate miner named XMRig with a custom-embedded configuration file.
That’s why it’s simply safer to block the installation of mining software by default on any computers running security solutions, such as Bitdefender Total Security. The only difference between an infected system running mining software and a clean one is a configuration file with different wallets. Better to be safe than sorry.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








