The Many Dimensions of Phishing and How to Defend Yourself

Phishing is a key attack vector responsible for most of the data breaches in the news. Bad actors capitalize on the weak human factor to compromise the target infrastructure and steal data or deploy malware. The same social engineering tactic is wielded to steal passwords and defraud regular users. Phishing takes many forms, and it’s important to stay educated to fend off this social engineering threat.
A Bitdefender survey reveals that most online consumers engage in risky behavior for data protection, digital identity and device management. Six in 10 users have faced at least one cyber threat – phishing and phone scams topping the list.
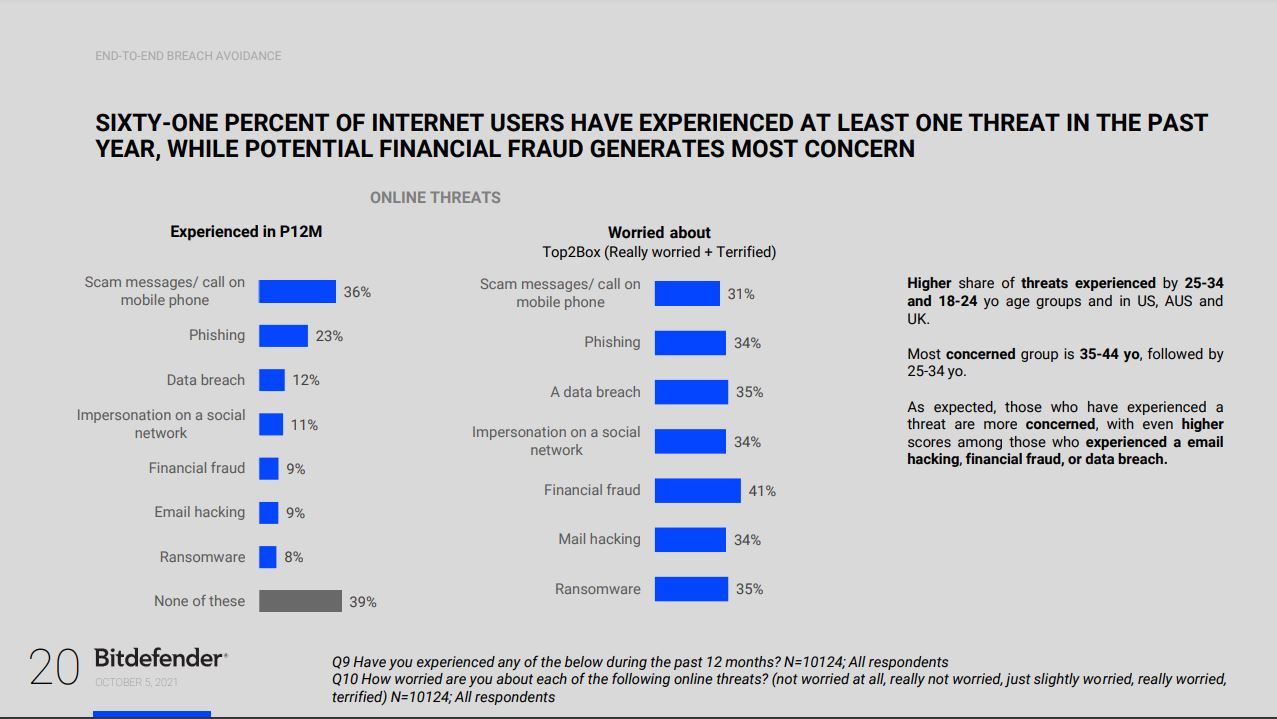
Email phishing
Probably the most common form of social engineering, phishing emails arrive in our inboxes due to improper handling of our email address. Whether it’s our own fault or because a company handled our data poorly (or got breached), bad actors use mass lists of email addresses to spam us with scary or tantalizing emails.
Some messages say “your account has been compromised“ and urge you to “change your password now!” Others try to lure you into “collecting” a gift, a prize or a refund. Whatever the scenario, the message almost always tries to create a sense of urgency as it seeks your login credentials for a certain platform, such as your online banking portal or your Instagram account, or anything in between.
Always be skeptical when an unsolicited email hits your inbox with warnings or perks. If in doubt, do the following:
· Verify the sender’s email address and make sure they are who they claim they are (check via a different channel or medium).
· If the message feels urgent, double check and triple check everything. It might be a scam. Real companies typically address users in a calm and composed manner, providing all the details necessary to make an informed decision.
· Hover with your mouse over links in the message to preview where the link really takes you (typically displayed in the bottom left-hand corner of the window).
· Do not download attachments and certainly don’t open them if you have reason to believe the message isn’t from a legitimate source.
· Take note of spelling or grammar mistakes.
· If the sender isn’t addressing you by name, it could be a scam. Entities that you do business with typically know your user information beforehand.
Use a trusted security solution that can flag suspicious emails.
Phishing websites
Much like phishing emails, phishing websites are rigged for the same purpose – to steal your login information (username & password) or banking data (credit card number, security number / CVV). In this scenario, it may be hard to discern fake from real, but as a general rule, never fill out a form with your personal and financial data if you haven’t vetted the platform.

Verify the site’s domain and make sure it’s the real company you do business with – not a spoofed version. A good example is the insidious homographic phishing scheme where attackers use similar characters to pretend to be another site – for example, substituting „o“ for „0“ (i.e. g00gle.com).
To stay on the safe side, use a security tool that can sniff out and block websites that masquerade as trustworthy to steal financial data such as passwords or credit card numbers. Our advanced filtering system warns you whenever you visit websites that may try to scam you.
Smishing (SMS phishing)
Phishing scams are more or less the same, regardless of where or how they’re deployed. That includes the traditional SMS on your phone. Typical SMS phishing messages pretend to be from a delivery company, your bank, or your telecoms operator.

The attacker may try to create a worrisome scenario where your last payment hasn’t been registered, or your account has some issues and you need to take steps to unlock it.
Other times, attackers may try to dupe you into believing you’ve got to start paying for a service that was free until now.
WhatsApp, the popular IM platform used by more than half a billion people worldwide, is also in hackers’ crosshairs. Security researchers have discovered dozens of types of fraudulent messages promising users all kinds of perks, like free iPhones, Amazon offers, terabytes of free internet data, and more.
If a message looks suspicious or sounds too good to be true, don’t do anything rash. Take your time to analyze it and try to confirm its veracity by contacting the company it claims to be from. If it claims to come from someone in your contacts list but it doesn’t feel quite right, contact that acquaintance on a different channel to confirm if they indeed sent the message.
Don't tap on links either. Some attacks need very little input from the user. Accessing a link can sometimes be enough.
While these tips should keep you on the safe side most of the time, it’s still highly recommended to use a trusted mobile security solution on your iOS or Android device.
Tech support scams
Technically also a type of phishing attack, tech support scams are extremely dangerous. The attacker typically cold-calls the victim, trying to persuade them to divulge sensitive data or to send money.

They use various methods. Keep an eye out for these pretexts:
“We’ve accidentally refunded you too much money and you need to send some back to us”
“buy a $100 gift card, scratch the card and send me the code to call it even”
“Your PC is infected. I need to remote access to fix your computer. Install TeamViewer”
… and the list goes on.
The scam typically targets the not-so-tech-savvy demographics, like senior citizens. However, they can be so devious that even scam baiters can get bamboozled.
Stay safe!
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
Fake Download of Mission: Impossible – The Final Reckoning Movie Deploys Lumma Stealer
May 23, 2025
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








