Linux and Container Security: Removing module dependencies

Bitdefender recently announced GravityZone Security for Containers, expanding our cloud workload security (CWS) by offering run-time support for containers and infrastructures with Linux kernel module (LKM) independence for the Bitdefender technology.
The use of containers for cloud workloads has grown rapidly in recent years, as the tools can help developers speed application delivery and digital transformation initiatives. However, this can bring increased organizational risk as security teams remain largely blind to suspicious activity in their Linux environments and container workloads.
Some of the benefits and features of GravityZone Security for Containers include:
- Modular architecture improves performance and security efficacy without kernel crashes
- Detection of application zero-day and known exploit attacks takes place in real-time
- Complete security visibility over all containers and workloads across hybrid or multi-cloud environments
Kernel module independence
Most containers operate within UNIX and Linux environments. The kernel is the main component of a Linux operating system (OS) and has the privileged ability to oversee and control the entire system that the containers reside within. Kernel panic is a relatively common safety measure that occurs when an OS detects an internal fatal error and makes the decision to shut everything down. Though this is a relatively common safety procedure, it results in disrupted workflows and increased maintenance workloads for administrators. It can also increase the operational burden on regular Linux users, sysadmins, DevOps and infrastructure engineers. Applications operating in userspace leverage system calls (syscalls) to work with the kernel. When it requests data from the kernel, under certain conditions, the OS crosses over the user/kernel boundary space and copies kernel data in the userspace. As a result, userspace applications can experience severe performance implications and loss-of-contexts.
To avoid the above issue, Linux kernel modules are written to operate purely in the kernel space. The benefits of using LKMs over the traditional approach include no boundary crossing to assign memory from the userspace, the modules have access to everything they need from the kernel, and the modules allow visibility of the syscall traffic and can easily add functionalities to the kernel.
However, these modules can leave the kernel susceptible to exploits and each new Linux kernel version can break the introduced functionalities. LKMs, therefore need to be refactored to be compatible with the kernel versions to avoid crashing the production system or worse, introducing security risks.
What is eBPF and why does it matter?
Extended Berkeley Packet Filter (eBPF) is a modern and powerful technology focused in the Linux kernel. It extends kernel capabilities without requiring source code edits or loading LKMs.
In this modern and modular approach:
- Tiny programs can be written and loaded to the kernel
- They are attached to probes that allow dynamic modification of the kernel at runtime
- Data is written out for userspace applications to an eBPF map/ ftrace / perf buffer
Unlike a kernel module, eBPF is a part of the core Linux kernel that allows customized codes deemed completely safe to execute in the environment. It allows customers to quickly refactor their LKMs to the latest Linux distributions without kernel panics or introducing instability.
Companies that enable this feature may be able to reduce testing and validation requirements that kernel dependencies necessitate and avoid the risk of security and system stability challenges.
New Bitdefender technology to secure Linux and container workloads
The new Bitdefender Security for Containers delivers threat prevention, eXtended Endpoint Detection and Response (XEDR) and anti-exploit protection for containers running in private and public clouds.
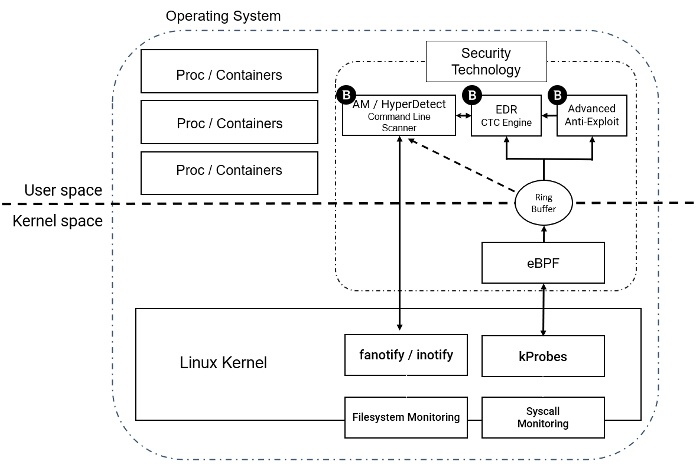
Figure: Bitdefender Linux and Container monitoring security model
Bitdefender has adopted and seamlessly integrated its advanced protection platform with the eBPF architecture to defend against modern exploits, zero-day application and OS vulnerabilities, and advanced persistent threats.
The modular architecture provides enhanced visibility, proactive prevention, and improves the security efficacy to avoid any compromise in the container environment.
kProbes and anti-malware
As seen from the figure above:
- kProbes enable kernel breakpoints that, when hit, execute a user configured eBPF program
- The output from kProbes is retrieved and placed on the Ring Buffer / perf buffer
- The Ring Buffer further distributes the events to EDR, Advanced Anti-Exploit and Anti-Malware/ HyperDetect
The anti-malware (AM) feeds the EDR component to enhance the root cause analysis (RCA) insights. Any malicious command line scripts or suspicious file modifications, for example zero-day applications are detected prior to adversarial exploitation.
For advanced anti-exploit (AAE), the eBPF programs are more elaborate than in the case of plain EDR events. For example, after each program execution, the technology checks new processes for any elevated privileges via unknown kernel bugs.
Bitdefender resolution for kernel dependencies
Bitdefender adheres to CIS benchmarks and provides an integrated solution to help customers identify vulnerabilities and threats proactively. Our advanced machine learning can quickly correlate and connect the dots between containers, hosts, applications and IOT devices.
The incident telemetry can accurately identify the root cause analysis along with detecting and responding in a manner which limits impact within a pre-defined risk tolerance.
GravityZone Security for Containers protects containers and cloud-native workloads against Linux kernel dependencies, application zero-day and known exploit attacks in real-time and identifies the full context of incidents including which images and pods were involved.
Along with focused detection and investigative capabilities, Bitdefender technology consumes less system resources and enables administrators to execute local, central and hybrid scans from within the same management console.
Discover more about how to implement an effective container security strategy and request a free demo.
Additional Resources
Complimentary whitepaper on how to effectively implement a container strategy
How to step-up Linux server and CWS security
tags
Author
Ashish is a Technical Marketing Engineer with Bitdefender. He has a Masters degree in Electrical Engineering from San Jose State University. Ashish enjoys spending his time reading up on threat reports, simulating exploits and producing high-visibility content.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks












