Building Resilience Through Threat Intelligence (TI)

This article provides a detailed overview of building resilience through threat intelligence. The data and information discussed here were provided by Cristina Vatamanu, Manager of the Forensic and Investigation Team from the Cyber Threat Intelligence Lab at Bitdefender.
The article outlines how threat intelligence has evolved in recent years, how it can be put into context, and how attacks can be attributed to specific threat actors.
The evolution of Threat Intelligence
Threat intelligence as a concept has grown much more complex and effective over time. In the beginning, threat intelligence focused on identifying simple indicators of potential compromise, but many other valuable insights, frameworks, and models have been included since then.
One such model is the Pyramid of Pain. This conceptual model is followed to effectively use cyber threat intelligence to detect threats, with importance placed on increasing the threat actor’s operational costs.
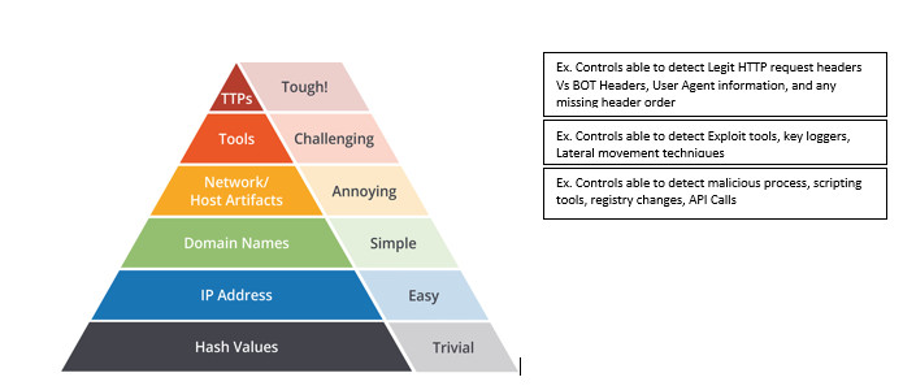
Source:https://www.linkedin.com/pulse/use-cases-perspective-pyramid-pain-rajasekaran/
In addition to new models, operational and tactical information have become much more in-depth, focusing on current trends and mapping entire attacks using tactics, techniques, and procedures (TTP) from frameworks such as MITRE. By doing so, cybersecurity teams can identify the structure of an attack, otherwise known as the Kill Chain.
Putting TI into context
Obtaining threat intelligence is all well and good, but it needs context, both internal and external, for security teams to understand the much bigger picture.
The process of gathering and developing threat intelligence can be broken down into six stages:
- Gathering the data
- Sorting the data for relevance
- Arranging the data into usable forms
- Visually presenting the data
- Explaining the data with a story (for example, a case study)
- Using the intelligence that is deemed useful
All steps are equally important, but the final two steps give the threat intelligence context and purpose. The initial indicators of compromise make it possible to identify and monitor potential threats, but the context allows IT teams to predict an attack, letting them take preventative measures.
The final step refers to situational awareness, helping organizations tailor threat intelligence to their needs. Unfortunately, many forensic investigations show that organizations often take the wrong action, contributing to security breaches or the destruction of evidence.
Therefore, the final step is vital to ensure organizations:
- Follow the correct procedures
- Take the necessary action
- Improve their operations
- Prioritize the right incidents
- Identify risks
- Protect and build resilience
Next, let’s look at two examples of context given to threat intelligence.
Threat Intelligence - study cases
Covid-19 themed malware
Covid-19 triggered exploitation of vulnerabilities in the health sector, which became the most popular target for cybercriminals. At Bitdefender, the team’s focus shifted to monitoring the health vertical in March 2020. It was clear from the start that there was a significant increase in malicious reports related to the coronavirus - over five times more than the previous month.
Hospitals, pharmacies, labs, and clinics all suffered ransomware attacks, and due to their need to function 24/7, there was little time to think about whether to pay ransom. Public institutions were especially vulnerable as cybersecurity was a low-priority focus at that time.
Most of the aggressive campaigns were launched in Europe, in particular Italy, which was the first country to be strongly impacted by the virus on the continent. Threat actors preyed on fear and confusion by spreading spam propaganda to fuel hysteria.
Once the pandemic went global in April, cyberattacks spread to all continents. In the US, attacks were most prominent in the states that were in the Top 3 for known infections and deaths, New York, Florida, and California.
Based on European trends, it was easier to identify where most attacks in the US would occur, helping cybersecurity teams act and communicate quickly to release indicators, raise awareness, and detect attacks. This helped everyone take the right actions promptly to prevent ransomware attacks.
Even small businesses fell victim to Covid-19 ransomware, proving that any organization can be a target. With attacks on small and mid-sized companies increasing by 150% over the last two years, protecting cash flow and the safety of monetary operations should be at the forefront of any cybersecurity strategy.
Industrial espionage
When considering more targeted attacks, industrial espionage has always interested the team at Bitdefender, which recently conducted a forensic investigation in this area. In the industrial espionage case, the victim was an organization in the technology industry that recently had a major product release.
The investigation showed that the organization had been compromised for several months before the product release and the purpose of the attack was exfiltrating intelligence. To execute the attack, the threat actor needed SSH Keys, VPN certificates, and credentials, and they also targeted the exfiltration of source code. This hybrid attack used both automated processes and manually executed commands.
Investigators discovered that the initial vector for the infection was an internet-facing instance of the ZOHO ManageEngine ADSelfService Plus web server that the hackers used to exploit a known unpatched vulnerability. It is one of the most exploited vulnerabilities, allowing attackers to bypass security authentication and execute malicious code.
After gaining access to the system, hackers deployed a combination of web shells in an internet-accessible directory, obtaining remote access to the company’s server. Once the system’s areas of interest were located, the attacker compressed and cloned files, pulled archives, and pushed data to a central exfiltration folder. Then, exfiltration was launched using normal HTTP GET requests via the internet.
Over 650 IPs were used to exfiltrate this data, and most of them can be traced to China.
Forensic processes
The aim of the analysis is to obtain as much information about a threat as possible. This can be achieved in two ways:
- Statistically, for example, decrypting an embedded config file from which we can extract the addresses of the command-and-control servers, reverse engineering the communication protocol, and so on.
- Dynamically, trying to reproduce the communication protocols to download new payloads, commands, or other config files.
The forensic processes contribute to finding similar payloads that can be automatically attributed to the investigated threat actor, mapping a botnet network, or obtaining information about targets or specific threat details.
Besides the commercial level, forensic analysis is used to identify threats that target individuals, particularly attacks that target personal finances. A secure online bank account, combined with multi-factor or biometric authentication, is essential to prevent such threats.
Threat attribution
In terms of threat attribution, it needs to be understood that malware creators are programmers and each piece of malware that is created needs a wide range of functions, from downloading the payload to encrypting files.
Because malware creators are very likely to work on numerous projects, it’s very likely that they will reuse code from previous projects. The key is identifying functions that are relevant to specific threat actors, effectively leaving a fingerprint.
Analyzing these files is also much easier using machine learning ML frameworks together with Yara rules.
Conclusion
Threat intelligence is an indispensable tool in cybersecurity, and it is an essential component in building resilience within an organization. It can be used to identify trends to help prevent similar attacks in the future, and by using forensic analysis, it can also attribute attacks to specific threat actors. Without threat intelligence, it is much harder for cybersecurity teams to understand the bigger picture.
Learn more about turning data into actionable insights and responding to security threats quickly.
tags
Author
Shanice Jones is a passionate business technology writer. She is based in Chicago, USA. For more than five years, she has helped over 20 startups build B2C and B2B content strategies that have allowed them to scale their businesses globally.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks