Bitdefender Threat Debrief | December 2025
Growing RaaS Partners and Affiliates Spark Divide on Perceived Connections
This edition of the Bitdefender Threat Debrief features key events, including updates on RaaS alliances, Qilin’s activity following Korean Leaks, the React2Shell vulnerability, Akria’s potential targets, and more.
As ransomware continues to evolve, our goal with the monthly Bitdefender Threat Debrief is to help you stay ahead of the curve. To do this, we combine information from openly available sources (OSINT) - things like news reports and research – with data we gather by analyzing Data Leak Sites (DLSs), websites where ransomware groups post details about their victims. It is important to remember that we can't independently verify all of these claims but are confident in the trends we see over time.
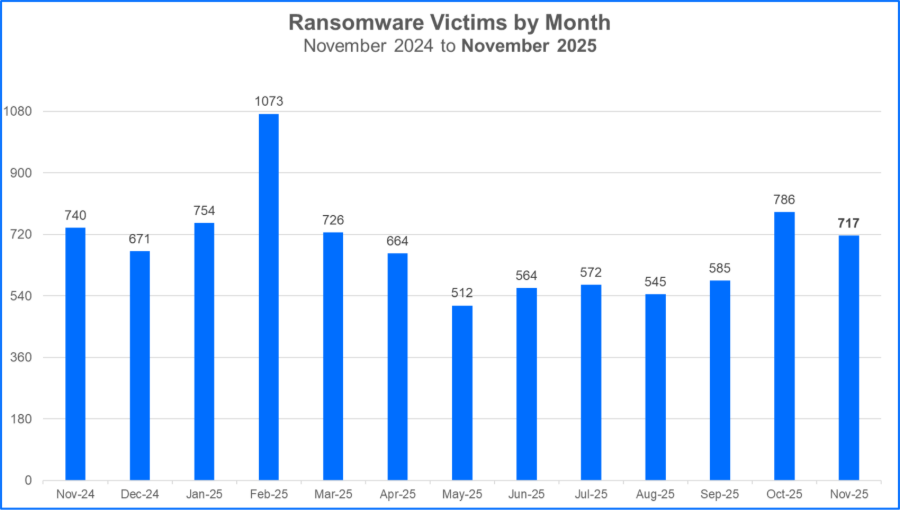
For this month's report, we analyzed data from November 1 to November 30 and recorded a total of 717 claimed ransomware victims.
Featured Story: Growing RaaS Partners and Affiliates Spark Divide on Perceived Connections
What happened?
From October through December, several ransomware groups announced new alliances. One of those alleged alliances emerged between Stormous, Devman, Coinbase Cartel, Nova, Radar, Desolator and Kryptos. In October Stormous posted about version 5 of their RaaS and a strategic partnership with the six groups. However, many in the research community questioned the validity of this alliance due to the number of groups involved, clashes in operational models, and the lack of communication that followed the announcement. There was no confirmation of mutual involvement or agreement between these groups.
Leaker Exposes Nova Ransomware Group Data
Another recent ransomware ecosystem development involves Nova, a group that launched their own RaaS, and sought out affiliate recruits this past summer. Another group exposed Nova’s inner workings in early December. A group named CBSecurity leaked the names and roles associated with Nova staff and multiple IP addresses tied to their infrastructure.
There’s a high likelihood that this exposure was orchestrated by an angry Nova affiliate or a competitor. According to one source, some with ties to Nova’s may have been upset that the group targeted victims in education along with non-profits. This is a possible variable used to justify exposing the group. Our threat researchers are monitoring the situation to see if additional leaks occur in the days ahead.
Ransomware Groups Developing Insider Threats at Organizations
An additional development that shows a change in how ransomware groups are operating is the gradual shift in the types of ranks that are incorporated into the cybercriminal hierarchy. Ransomware groups are moving beyond a reliance on the ranks of external software developers, penetration testers, and initial access brokers. An increasing number of groups are now developing in-house expertise and creating and managing their own RaaS platforms.
They’re also expanding recruitment efforts to reach employees at target organizations. This is evident with the group Kryptos, who encouraged corporate insiders to join the Kryptos initiative. Kryptos defined a system and a tiered approach to profit-sharing that insiders can benefit from. This expands beyond the traditional 85-90% profit margin we’ve observed in more typical RaaS models.
Kryptos’ multi-tiered system for insiders at their target organizations invites IT admins, executive assistants, and third-party vendors to give away access to corporate networks via VPN, MFA, SSH, etc. The payoff for those willing to become an insider threat runs from thousands of dollars all the way up to millions of dollars. Organizations should be aware that ransomware operators are increasingly trying to recruit their employees to increase the odds of a successful attack. This approach removes the need for resources that other groups prioritize, such as EDR and AV killers, along with InfoStealers.
ShinyHunters Releases ShinySo1d3r RaaS
The ShinySp1d3r RaaS was announced just before the publicized fall of Scattered LAPSUS$ Hunters in August. The RaaS release features information on the Windows encryptor and its capabilities, including the encryptor’s ability to hook EtwEventWrite to offset the writing of data into Windows Event Viewer, its ability to force kill open processes, and also run malware locally via actions such as deployViaSCM and deployViaWMI. ShinyHunters has taken credit for the release of the ShinySp1d3r RaaS; yet, the group stated that the platform will be managed under the brand of their former coalition. Whether this is a PR stunt to garner more recognition for Scattered Spiders and LAPSUS$ after law enforcement’s seizure of BreachForums remains unclear. However, Scattered Spider’s (and by extension ShinyHunters’) creation of their own encryptors and dedicated platform may serve as a model for more groups to follow, helping them to break away from affiliate relationships.
Other Notable Ransomware News
Now, let’s explore the notable news and findings since the last Threat Debrief release.
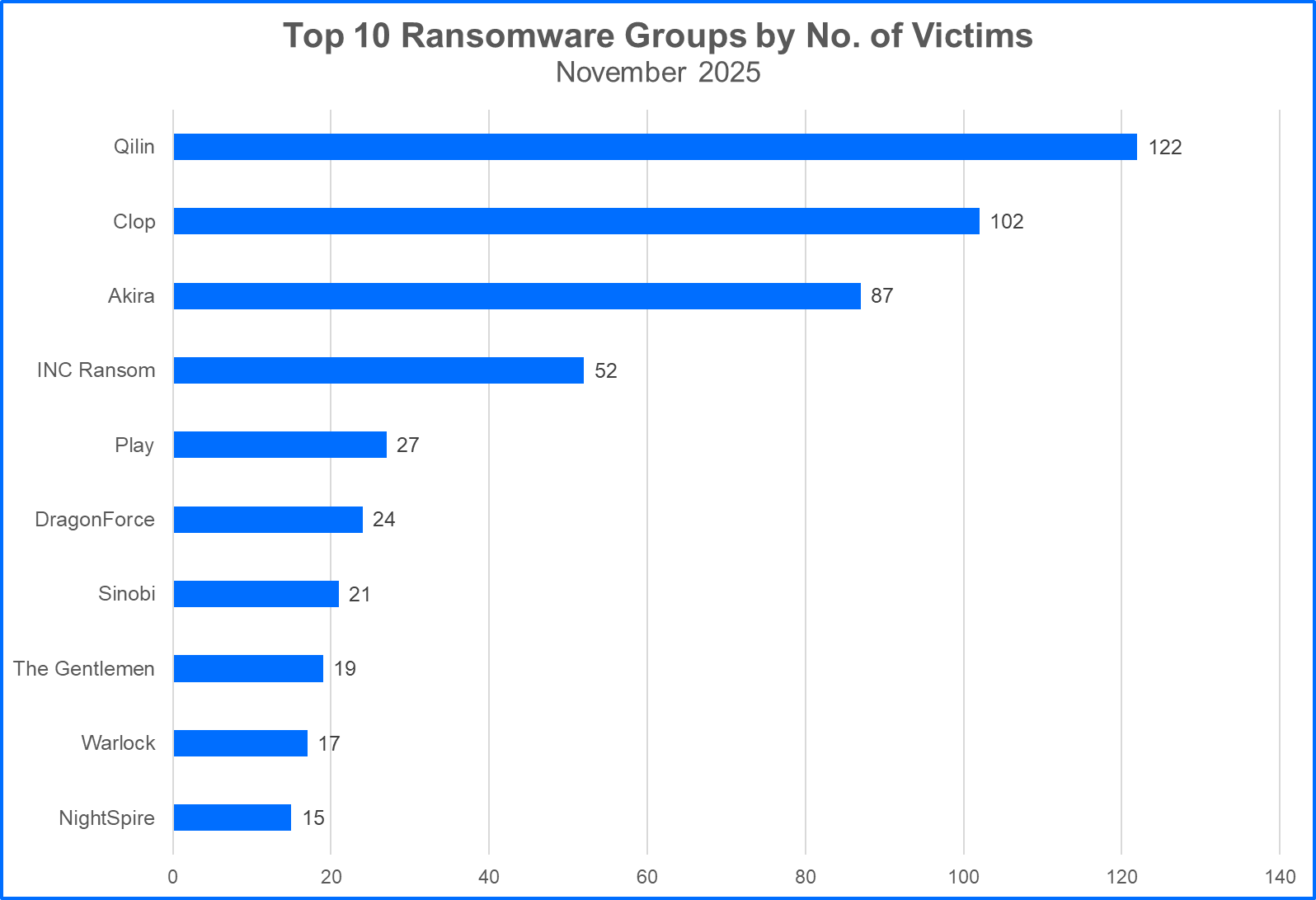
- Qilin’s claimed victims decline after Korean Leaks Campaign: Qilin claimed 122 victims in November, which is a stark contrast from the 205 victims reported in the previous month. From August to October, Qilin, assisted by another threat actor (likely Moonstone Sleet), leveraged the compromise of an MSP ecosystem to leak data from more than 30 organizations based in South Korea. While the group has secured the first rank in our Top 10 again, their victims are far lower than anticipated and do not feature organizations from East Asian regions.
Read More: The Korean Leaks – Analyzing the Hybrid Geopolitical Campaign Targeting South Korean Financial Services With Qilin RaaS - Clop Climbs to Second Place: Clop claimed 102 victims, surpassing Akira and reclaiming a position in the Top 10. The majority of Clop’s victims in the past month have been organizations in the manufacturing, technology, and healthcare industries. The group has repeatedly exploited a zero-day vulnerability to compromise numerous systems. Clop’s attacks have also targeted systems impacted by CVE-2025-61882, which leads to the compromise of Oracle Concurrent Processing. Organizations using Oracle E-Business Suite versions 12.2.14 to 12.2.3 are advised to implement the latest patch to mitigate this flaw.
- React2Shell Vulnerability is Disclosed: CVE-2025-55182 is a critical flaw affecting React Server Components. The vulnerability allows an attacker to gain initial access and perform remote code execution after sending HTTP requests containing malicious objects to the server. React versions 19.0.0, 19.1.0, 19.1.1, and 19.2.0 are affected. The flaw also impacts the default configurations across the Next.js framework (15.x, 16.x) and Canary builds (14.x). Organizations using these iterations of React and supported components, are advised to patch them immediately. The React2Shell vulnerability may result in a widespread impact similar to those experienced with the exploitation of the Apache Log4Shell and Log4j flaws in ransomware attacks that hit multiple sectors.
- CISA Updates Akira Advisory to Include Targeted Nutanix VMs: Hypervisors such as ESXi and Hyper-V environments have been prevalent targets for many ransomware groups aiming to take down hundreds of machines in seconds, Akira has launched campaigns targeting Nutanix VMs for nearly a year. Unlike with the ESXi systems, Akira’s Linux encryptor used in the Nutanix AHV environment can skip the process of powering off virtual machines and encrypt virtual disks (ending in .qcow2). Organizations are advised to ensure that flaws acting as common entry points for Akira and other ransomware groups such as CVEs impacting VPN and network appliances are identified and remediated. It is also recommended that they implement an effective backup and recovery plan.
- Warlock Claims Several More Victims Based in Russia: Warlock claimed 3 victims in November that were based in Russia. This instance of more than one Russian-based organization being claimed in one month, and by the same ransomware group, is an anomalous event. This leads many to question Warlock’s motivations and origins. Notably, threat actors utilize capabilities mirroring that of a state-sponsored group, Storm-2603, which has leveraged Warlock ransomware in campaigns that abused flaws affecting SharePoint ToolShell. Shared TTPs between the two entities supports hypotheses that Warlock is an established, China-based threat in spite of the fact that China tends to support Russian-aligned interests.
Top 10 Ransomware Families
Bitdefender's Threat Debrief analyzes data from ransomware data leak sites, where groups publicize their claimed number of compromised organizations. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and may be unreliable. Additionally, this method only captures the number of victims claimed, not the actual financial impact of these attacks. Here’s the Top 10 ransomware groups.
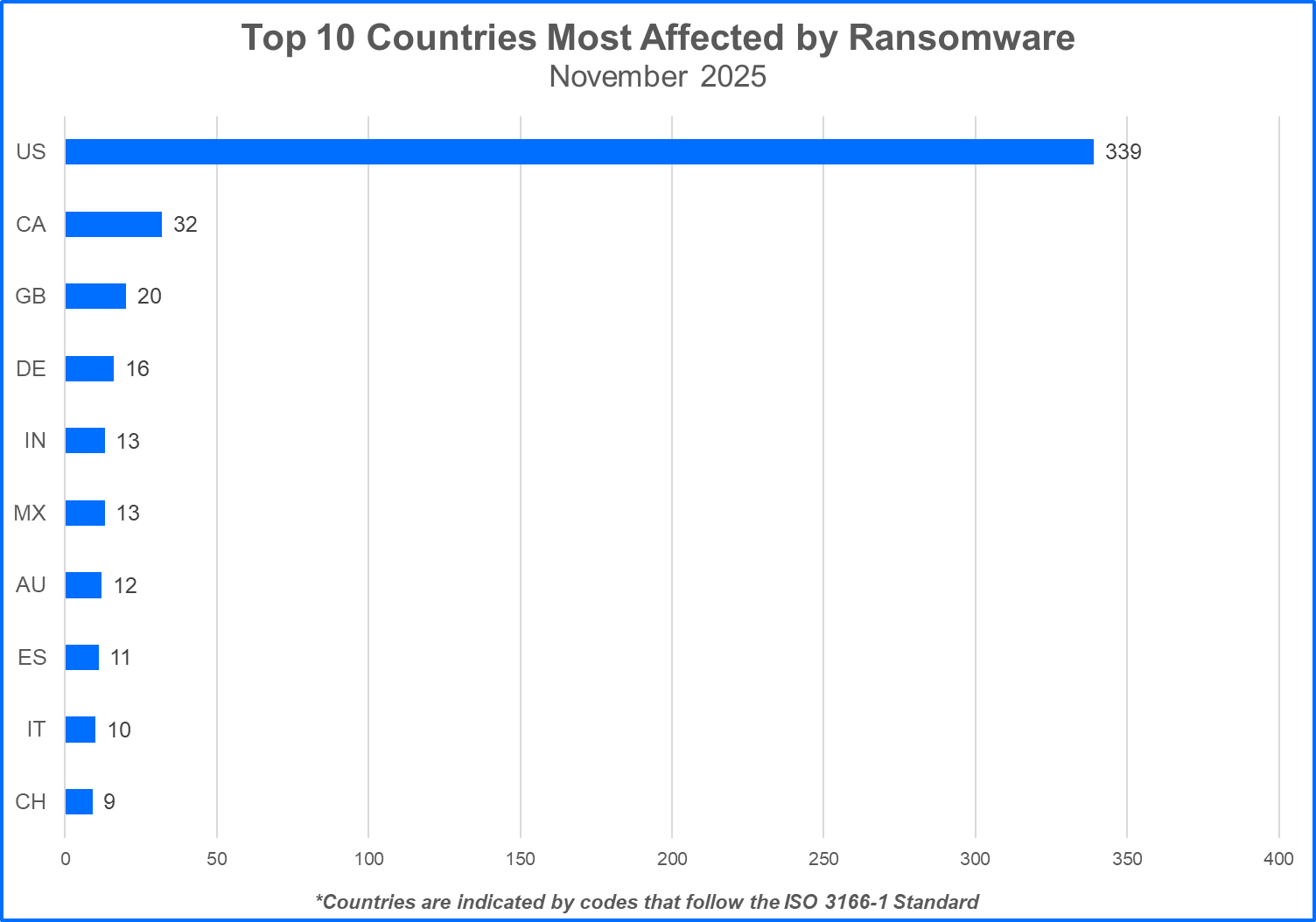
Top 10 Most Attacked Countries
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. In many cases, this means focusing on developed countries with higher projected growth rates. Threat actors may also execute strategic attacks that unfold during geopolitical conflicts or periods of social unrest. Let’s see the top 10 countries that took the biggest hit from ransomware attacks.
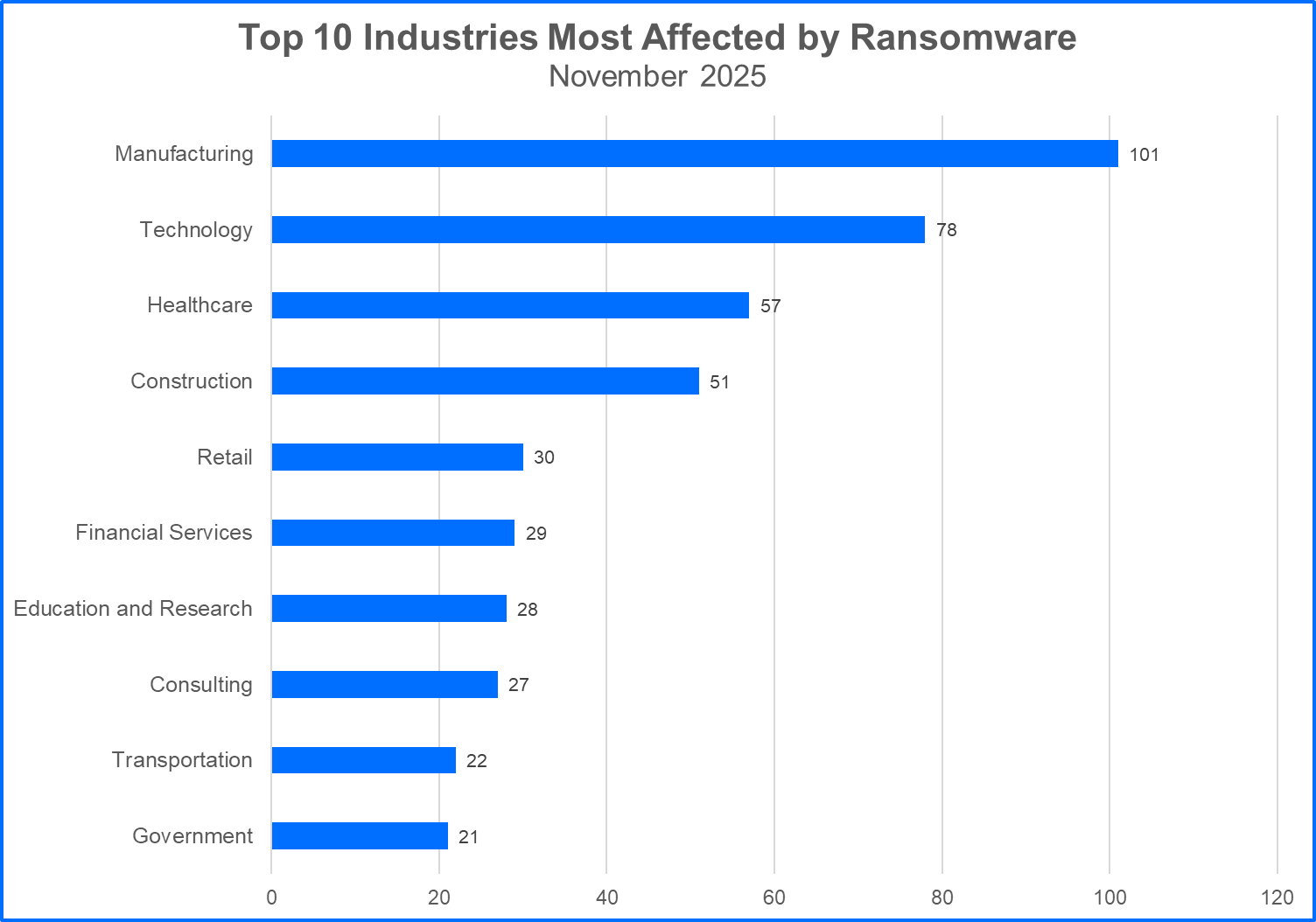
Top 10 Most Attacked Industries
Ransomware gangs may target organizations in critical infrastructure sectors, select other organizations that offer services tailored to consumers, or attack organizations that fall into both categories. Understanding the trends and ramifications associated with specific industries, and how specialized services and clientele are impacted is crucial for assessing risk. Here are the Top 10 industries affected by ransomware attacks.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Gabriel Macovei, Andrei Mogage, and Rares Radu for their help putting this report together.
tags
Author
Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks









