Bitdefender Threat Debrief | June 2023

MDR Insights
Last month, we discussed how Bitdefender MDR protects customers by making intelligence actionable for our SOC and customers. Today, we'll focus on Bitdefender MDR's additional expertise: the Cyber Intelligence Fusion Cell (CIFC). CIFC's intelligence monitoring takes a multi-faceted approach to ensure customer environments are secure, while also keeping an eye on industry verticals and emerging cyber threats. From understanding a customer's threat landscape to supporting incident response, CIFC acts as a trusted advisor, helping mitigate risks.
CIFC is involved from the start of the MDR service, onboarding customers and utilizing their landscape information to activate intelligence alerts based on essential customer data. These alerts keep CIFC and the customer informed about potential risks. CIFC's monitoring is based on customer threat models, which are built using customer-provided data and OSINT research.
Once a customer is onboarded, CIFC diligently monitors them using threat intelligence tools to track and prioritize alerts. Alerting and customer notification are crucial in this process. Notifications are tailored to specific event discoveries, such as typosquatting or credential leaks, ensuring each situation is managed effectively and efficiently.
CIFC leverages its analytic perspective through Requests for Information (RFI), allowing both CIFC and the customer to address day-to-day concerns promptly. RFIs cover a range of subjects, from simple malware or exploit questions to complex inquiries about world events that may impact customer environments.
RFIs and daily monitoring of news and intelligence sources often lead to customized research that produces intelligence newsletters (called Tippers) for customers. These tippers consider high-priority current intelligence, including indicators of compromise, and provide a comprehensive understanding of a security event. They also offer options for customer actions. Tippers are particularly beneficial for customers or industries most likely to be affected.
Intelligence-driven hunts are CIFC's method of pursuing potential leads based on investigation findings. These hunts can involve one or several customers, as well as specific industry verticals. They help SOC analysts investigate customer environments under threat from emerging malware campaigns by looking beyond typical indicators of compromise and considering other activity indicators. Hunts that examine non-static indicators are crucial for ruling out harmful threats.
CIFC utilizes multiple intelligence sources and threat intel tools to deliver timely and relevant information, ensuring customers' environments remain secure. Whether investigating the latest zero-day vulnerability, notifying customers of malicious activity associated with a domain, or compromised credentials, CIFC provides a comprehensive outlook on current and future threats.
Ransomware Report
Spear phishing attacks are often used as an initial attack vector and ransomware infection is often the final stage of the kill chain. For this report, we analyzed malware detections collected in May 2023 from our static anti-malware engines. Note: we only count total cases, not how monetarily significant the impact of infection is. Opportunistic adversaries and some Ransomware-as-a-Service (RaaS) groups represent a higher percentage compared to groups that are more selective about their targets, since they prefer volume over higher value.
When looking at this data, remember these are ransomware detections, not infections.
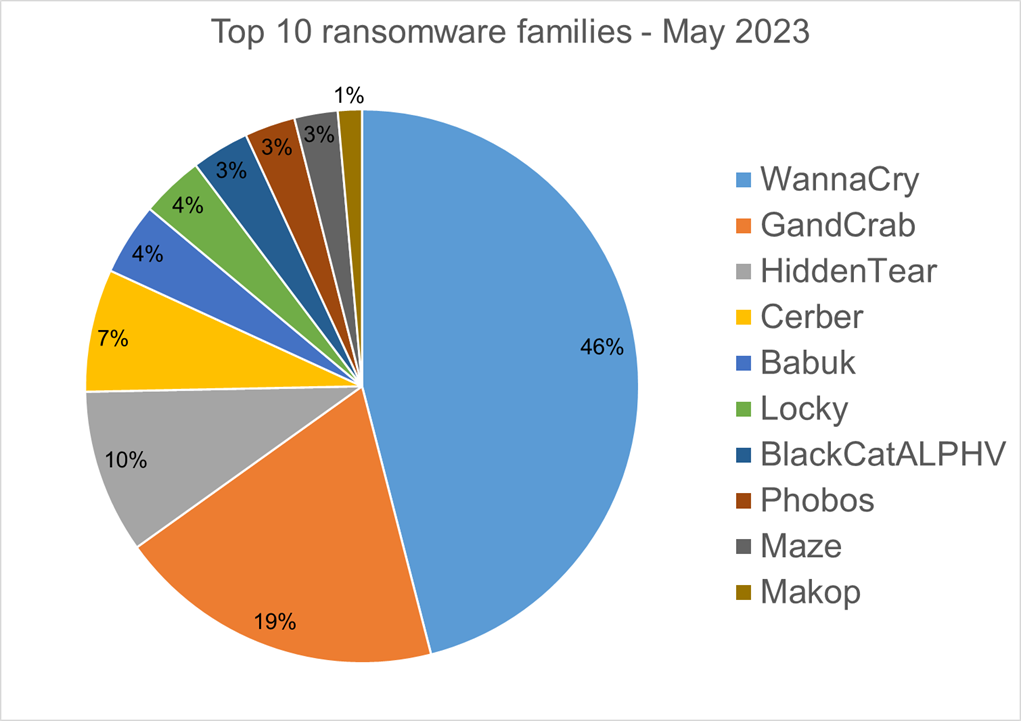
Top 10 Ransomware Families
We analyzed malware detections from May 1 to May 31. In total, we identified 186 ransomware families. Number of detected ransomware families can vary each month, depending on the current ransomware campaigns in different countries.
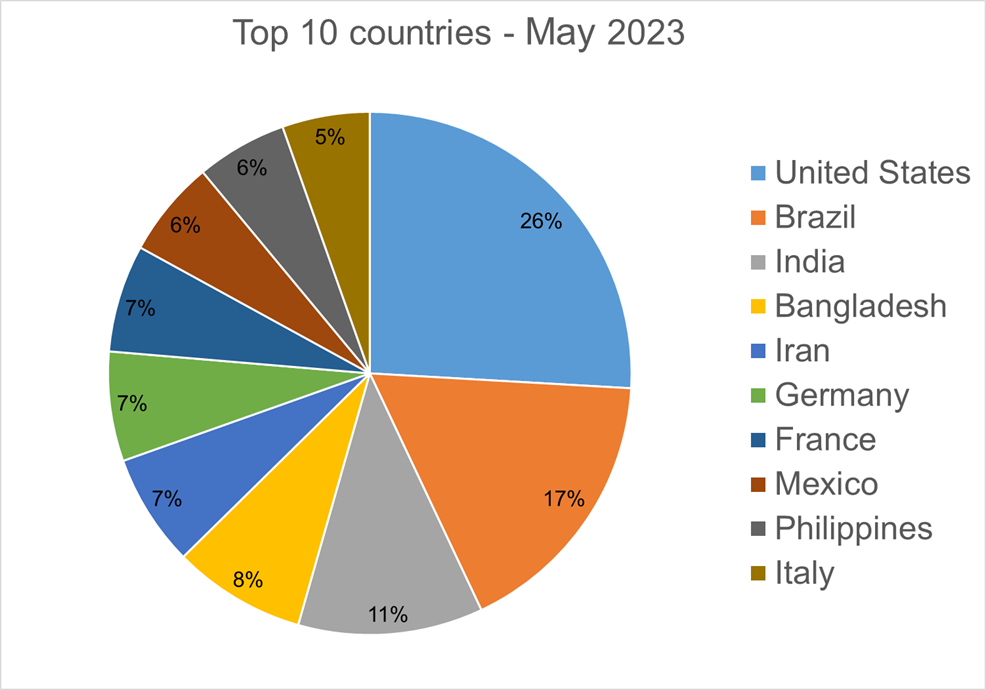
 Top 10 Ransomware Countries
Top 10 Ransomware Countries
In total, we detected ransomware from 190 countries in our dataset this month. Ransomware continues to be a threat that touches almost the entire world. Below is a list of the top 10 countries most impacted by ransomware. Many ransomware attacks continue to be opportunistic, and the size of population is correlated to the number of detections.
Android trojans
Below are the top 10 trojans targeting Android we have seen in our telemetry during May 2023.
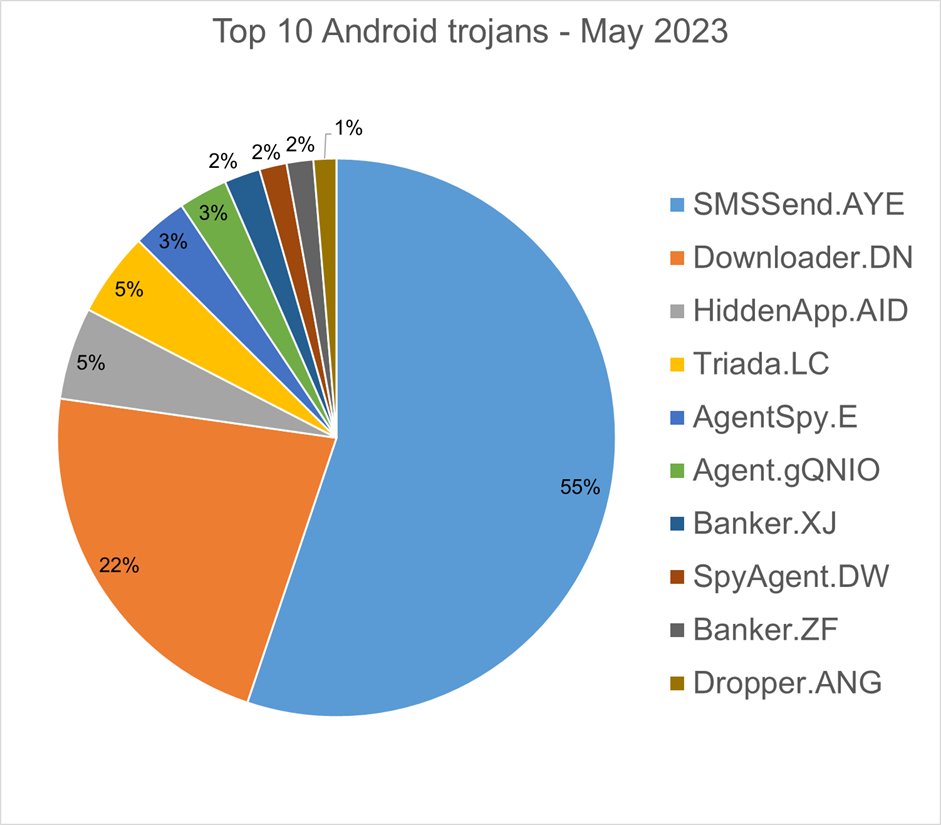
SMSSend.AYE - Malware that tries to register as the default SMS application on the first run by requesting the consent of the user. If successful, it collects the user's incoming and outgoing messages and forwards them to a Command & Control (C&C) server.
Downloader.DN – Repacked applications taken from Google App Store and bundled with aggressive adware. Some adware downloads other malware variants.
HiddenApp.AID - Aggressive adware that impersonates AdBlock applications. When running for the first time, it asks permission to display on top of other apps. With this permission, the application can hide from the launcher.
Triada.LC – Malware that gathers sensitive information about a device (Device IDs, Subscriber IDs, MAC addresses) and sends them to a malicious C&C server. The C&C server responds by sending back a link to a payload that the malware downloads and executes.
AgentSpy.E - Applications that were taken from Google Play Store and re-packed with malware. The malware packages are obfuscated, with the primary objective of stealing personal data.
Agent.gQNIO - Generic name that detects obfuscated applications that are signed with debug certificate and bundled with numerous adware SDKs.
Banker.XJ - Applications that drop and install encrypted modules. This trojan grants device admin privileges and gains access to manage phone calls and text messages. After deploying, it maintains a connection with the C&C server to receive commands and upload sensitive information.
SpyAgent.DW - Applications that exfiltrate sensitive data like SMS messages, call logs, contacts, or GPS location.
Banker.ZF - Applications that disguise themselves as banking apps and can imitate conversation with customer support. When the malware runs for the first time, it asks for permissions to access contacts, microphone, geolocation, and camera. Once the permissions are granted, the malware can receive commands from the C&C server to exfiltrate sensitive data from the phone.
Dropper.ANG - Applications that include an additional malicious application within their payload. When executed, the applications will drop and install the payload which is designed to exfiltrate sensitive data from the user's mobile device.
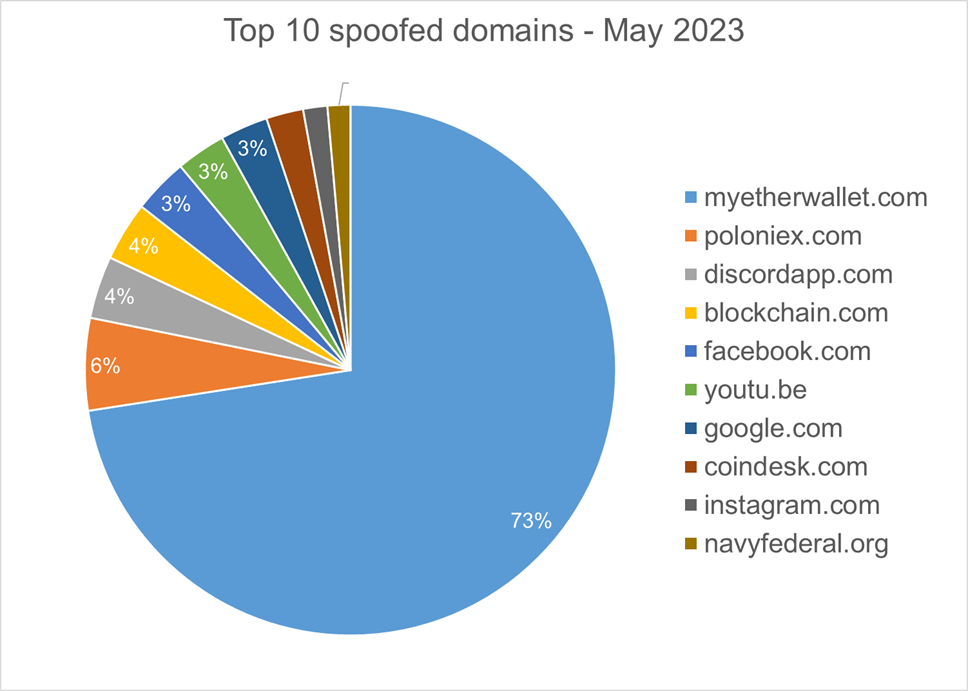
Homograph Phishing Report
Homograph attacks work to abuse international domain names (IDN). Threat actors create international domain names that spoof a target domain name. When we talk about “target” of IDN homograph phishing attacks, we refer to the domain that threat actors are trying to impersonate. You can read more about this type of attack in one of our previous reports.
Below is the list of the top 10 most common targets for phishing sites.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 150 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank bitdefenders Alin Damian, Mihai Leonte, Justtin Mills, Andrei Mogage, Sean Nikkel, Nikki Salas, Rares Radu, Ioan Stan, Marius Tivadar, and Horia Zegheru (sorted alphabetically) for their help with putting this report together.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










