Bitdefender Threat Debrief | August 2022

In this month’s Threat Debrief, we asked experts from our Managed Detection and Response (MDR) team to discuss threat hunting, how it's used for proactive defense as well as some of the most common misconceptions. We also dive into the latest Ransomware findings from our Labs.
MDR Insights
What is cyber threat hunting?
Cyber threat hunting is a proactive cyber defense activity. The key word is proactive. Threat hunters look to uncover nefarious activity that detection tools miss. Threat hunting uses manual queries, SIEM alerts, log reviews, and endpoint or network monitoring, either alone or in combination, to enable the detection of suspicious or malicious activity.
For example, proactive hunting allows analysts to find an attacker that may be hiding behind compromised credentials and/or living off the land (using common programs, processes, and other existing places to hide malicious activity). Cyber threat hunting is the human element to defend against threat actors, specifically advanced ones like nation-states and sophisticated criminal actors, such as Ransomware-as-a-Service groups, who are known for staying hidden long before detection.
Contrary to popular belief that the dwell time of adversaries (the time threat actors remain undetected) has been steadily increasing, the opposite is true. The most recent Verizon 2022 DBIR found that while the discovery time has decreased in recent years for most breaches, it’s not because companies are getting better at detection. The decrease is because threat actors themselves are more often disclosing breaches via extortion and data dump sites. Breaches lasting months factor in about 20% of breaches, according to DBIR, but have been on a steady decrease since 2017 (when this number was almost 50%).
This is not good news, as organizations now have less time to prevent a security incident from developing into a security breach. Proactive threat hunting gives organizations a fighting chance to find an attacker hiding in the network before damage is done. As threat actors shift their focus from breach of availability (ransomware) to breach of confidentiality (data exfiltration), detection and response capabilities become even more important.
Another way to consider threat hunting is that it’s an incident response without an incident. Analysts commonly look for clues from known, specific cyber threat campaigns, emerging threats without written signatures, or common tactics among a variety of threat actors during “hunts”.
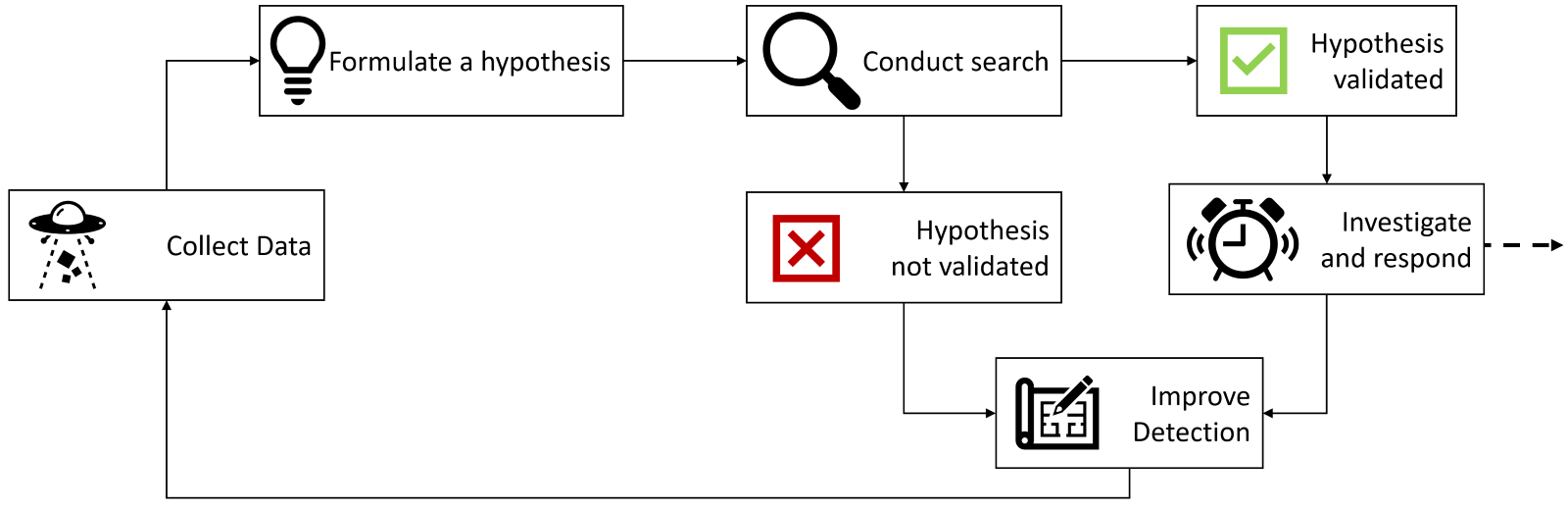
Simplified flow of Threat Hunting, an incident response without an incident
What cyber threat hunting is not
Unfortunately, there are quite a few common misconceptions about threat hunting. It’s not just a marketing term, it’s a layer of security that goes beyond just investigating alerts. Threat hunting protects organizations against all kinds of threats: Everything from automated botnets serving up commercial malware, to the Advanced Persistent Threats (APT) which include the most sophisticated criminal groups and nation-state actors.
Some common misconceptions include:
- “It's pen testing” - False: Penetration Testing or Red Teaming is a type of ethical hacking that attempts to evaluate a security system and find vulnerabilities. Although threat hunters can find vulnerabilities during their routine or intelligence-driven hunts, in which case they provide customer recommendations, it is not the sole purpose of threat hunting.
- “It's an alert investigation” - False: Alert triage is reactive, in which an activity has matched detection tool signatures and has alerted a security team to investigate. An important takeaway from Verizon’s 2022 DBIR is that the number of steps attackers take to breach an environment is less than five, in most cases. This means that by the time an alert fires for malicious activity, it's likely that the attacker has already made several steps to get there. Threat hunting proactively looks for the signs of an attack that may look benign or is attempting to evade detection—that is, the activity before the alert.
- “It can be fully automated” - False: Behind every cyber-attack is a human that can change tactics, switch targets, and pivot to a new operation. At the end of the day, automation is only as good as its code or signature, often meaning the discovery of threat activity that is already known, versus the unknown. Machine learning can be noisy at first, and too many false positives can lull defenders into ineffective signature tuning or lead to a false sense of security. Threat analysts can make decisions in real-time and, based on their expertise, can search for abnormal behavior such as users accessing systems or files they shouldn’t be, creating new folders, copying or downloading files, or logging in during irregular times. Analysts typically then confirm if the activity is malicious or not, and then add it to a baseline of normal activity or flag it for further review with the customer.
Threat hunting by Bitdefender managed detection and response (MDR)
Bitdefender MDR analysts start with a baseline of a customer’s environment, looking to understand all the factors in play: From understanding the technologies present in the environment to the network architecture and key users or third parties with access. MDR analysts often operate with customer pre-approved actions in mind, typically reaching back out to customers to verify legitimate activity, recommending best practices, or, as an example, shutting down network access to a potentially compromised machine during an incident.
Bitdefender MDR analysts also operate with access to the latest intelligence, which helps to understand emerging threats, such as new threat actors or known actors that have changed their tactics. These can consist of industry, location, and technology-focused threats that can affect multiple customers or a targeted threat that is tuned for a single customer. MDR and Cyber Intelligence Fusion Cell analysts often work closely to identify the latest threats and to develop intelligence-driven threat hunting packages to catch these new threats in the act.
Cyber threat hunting is a proactive search through an environment to hunt malicious, suspicious, or risky activities that have evaded detection by existing tools. There are few times in security where an activity that is easy to implement and use gets such an amazing return on investment; or, to misuse a common phrase, a stitch in time saves millions in post-breach costs.
Ransomware report
Spear phishing attacks are often used as an initial attack vector and ransomware infection is often the final stage of the kill chain. For this report, we analyzed malware detections collected in July 2022 from our static anti-malware engines. Note: we only count total cases, not how monetarily significant the impact of infection is. Opportunistic adversaries and some Ransomware-as-a-Service (RaaS) groups represent a higher percentage compared to groups that are more selective about their targets, since they prefer volume over higher value.
When looking at this data, remember these are ransomware detections, not infections.
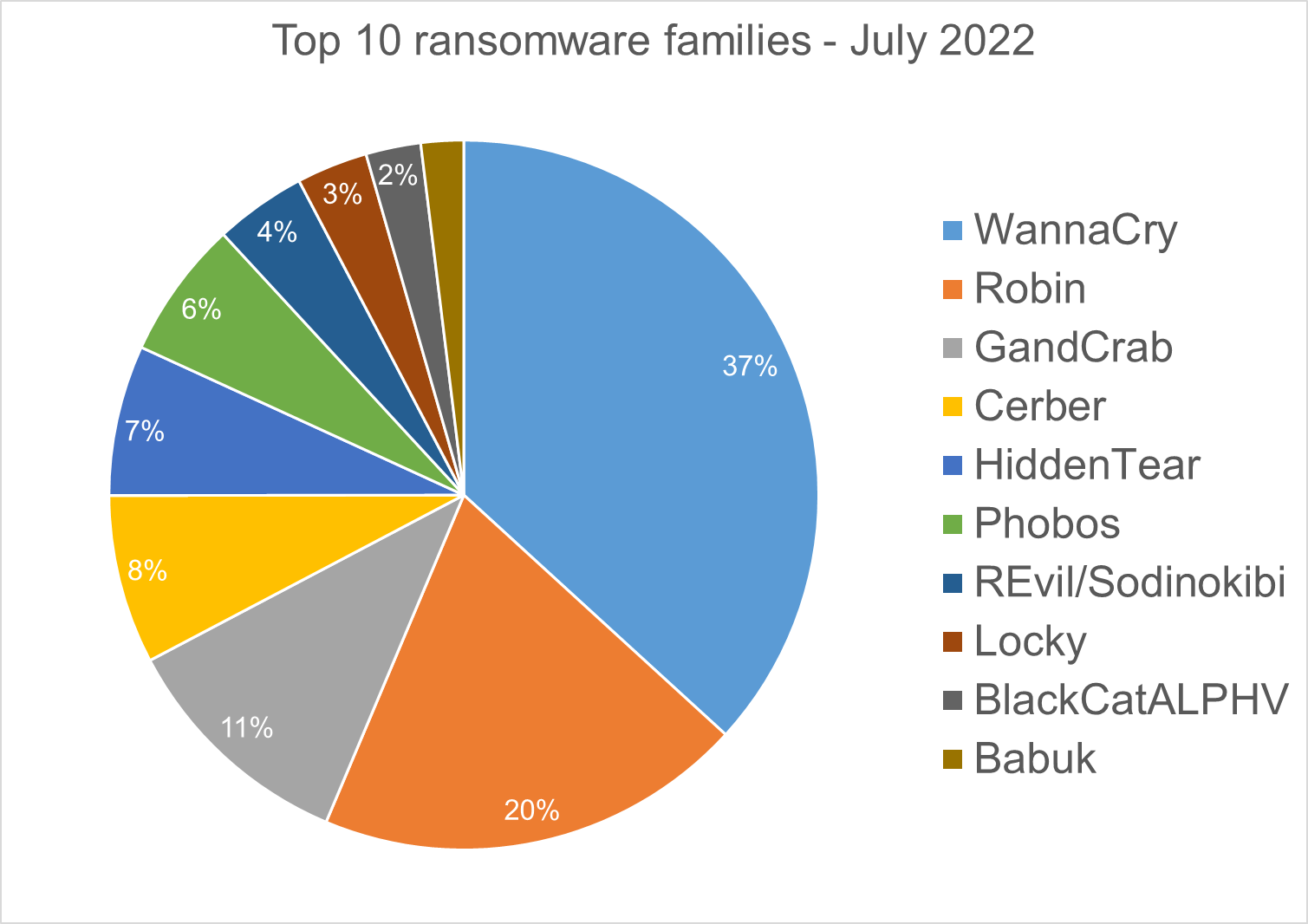
Top 10 ransomware families
We analyzed malware detections from July 1 to July 31. In total, we identified 205 ransomware families. The number of detected ransomware families can vary each month, depending on the current ransomware campaigns in different countries.
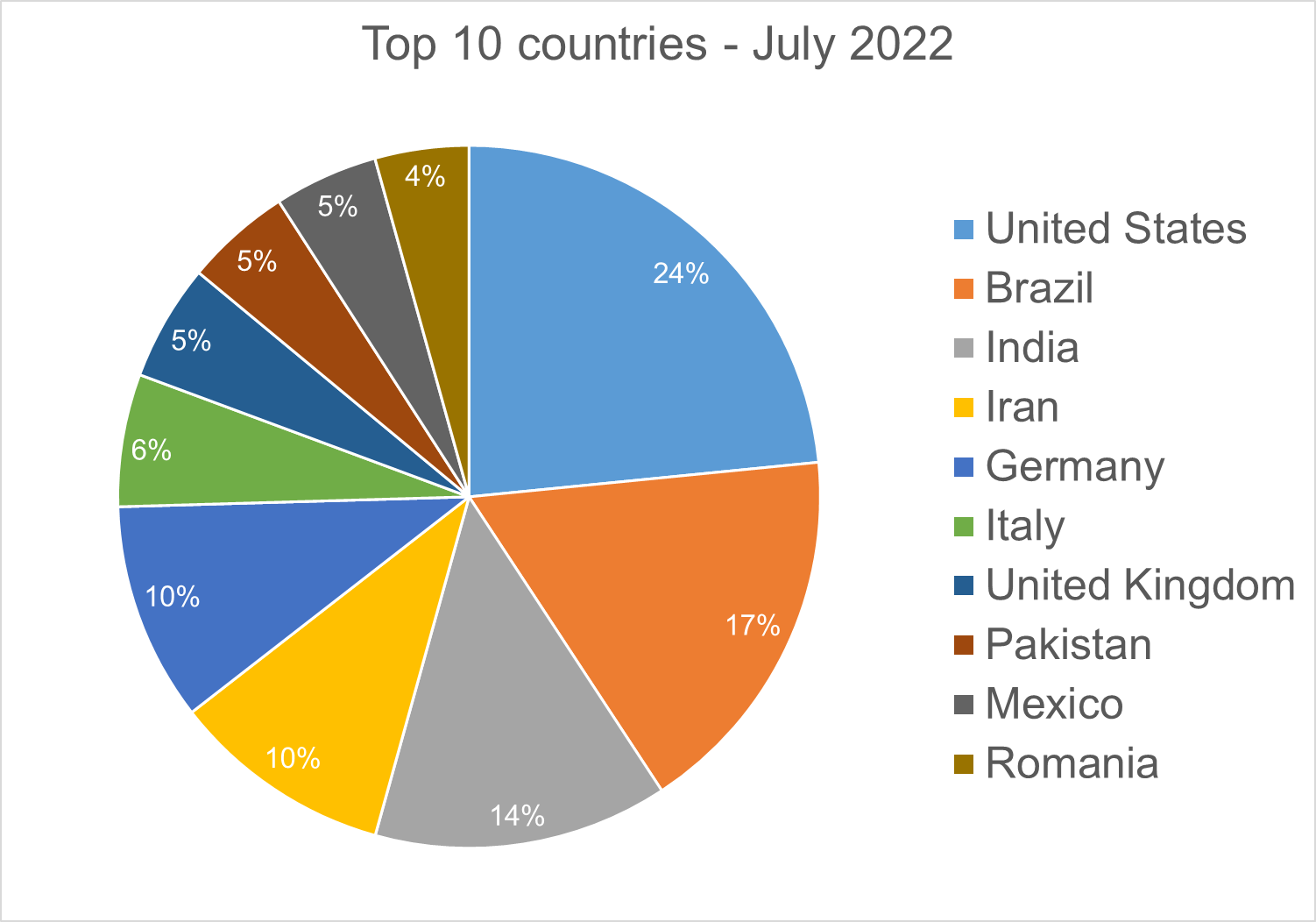
Top 10 countries
In total, we detected ransomware from 151 countries in our data set this month. Ransomware continues to be a threat that touches almost the entire world. Below is a list of the top 10 countries most impacted by ransomware. Many ransomware attacks continue to be opportunistic, and the size of population is correlated to the number of detections.
Android trojans
Below are the top 10 trojans targeting Android we have seen in our telemetry during July 2022.
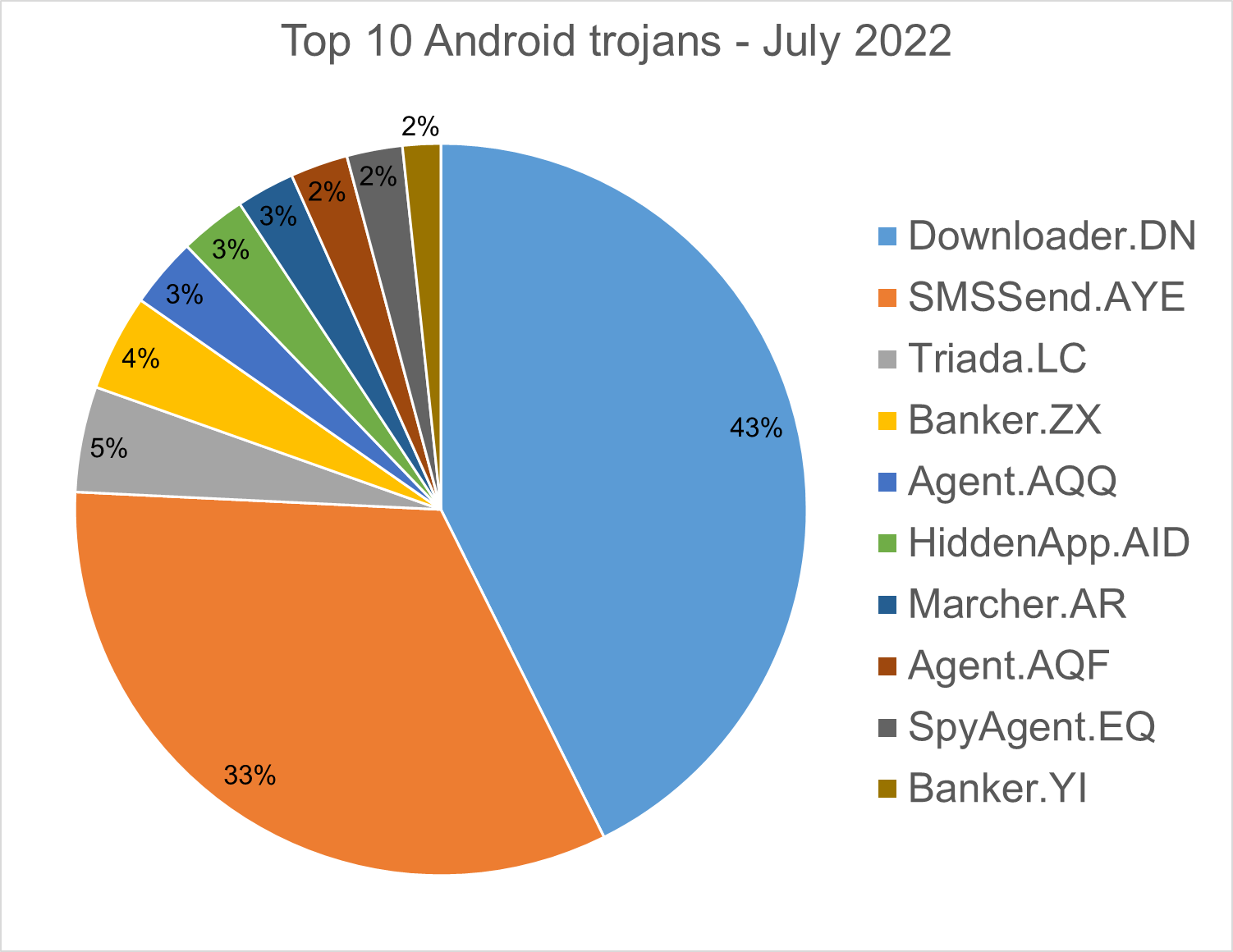
Downloader.DN – Repacked applications taken from Google App Store and bundled with aggressive adware. Some adware downloads other malware variants.
SMSSend.AYE - Malware that tries to register as the default SMS application on the first run by requesting the consent of the user. If successful, it collects the user's incoming and outgoing messages and forwards them to a Command & Control (C&C) server.
Triada.LC – Malware that gathers sensitive information about a device (Device IDs, Subscriber IDs, MAC addresses) and sends them to a malicious C&C server. The C&C server responds by sending back a link to a payload which the malware downloads and executes.
Banker.ZX – Applications that disguise themselves as banking apps and can imitate conversation with customer support. When the malware runs for the first time, it asks for permissions to access contacts, microphone, geolocation, and camera. Once the permissions are granted, the malware can receive commands from the C&C server to exfiltrate sensitive data from the phone.
Agent.AQQ - A dropper malware is a trojan that hides the dangerous payload inside an app as an evasion technique. If it can avoid security defenses, this payload is deployed. The malicious payload is decrypted and loaded by the dropper.
Agent.AQF - A dropper malware is a trojan that hides the dangerous payload inside an app as an evasion technique. If it can avoid security defenses, this payload is deployed. The malicious payload is stored as base64 in resources files.
HiddenApp.AID - Aggressive adware that impersonates AdBlock applications. When running for the first time, it asks permission to display on top of other apps. With this permission, the application can hide from the launcher.
Marcher.AR –Applications that disguise themselves as Play Store applications. The malware tries to ask for accessibility permissions to capture keystrokes and uses the VNC screen recording function to log user’s activity on the phone.
SpyAgent.EQ - Applications that exfiltrate sensitive data like SMS messages, call logs, contacts, or GPS location.
Banker.YI - Polymorphic applications that impersonate legit apps (Google, Facebook, Sagawa Express ...). Once installed, it locates banking applications installed on the device and tries to download a trojanized version from the C&C server.
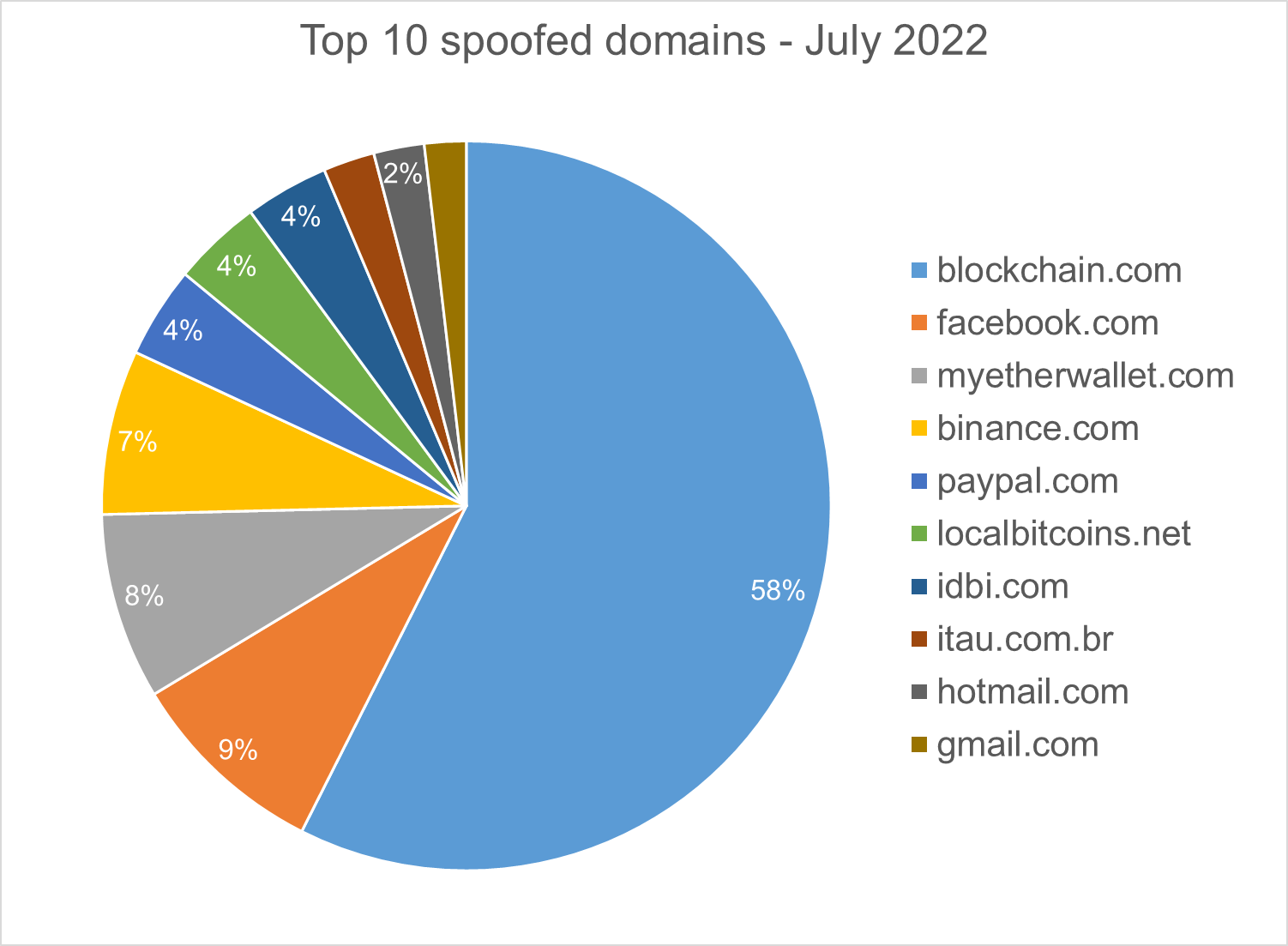
Homograph phishing report
Homograph attacks work to abuse international domain names (IDN). Threat actors create international domain names that spoof a target domain name. When we talk about “target” of IDN homograph phishing attacks, we refer to the domain that threat actors are trying to impersonate. You can read more about this type of attack in one of our previous reports.
Below is the list of the top 10 most common targets for phishing sites.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 150 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Tyler Baker, Alin Damian, Mihai Leonte, Andrei Mogage, Sean Nikkel, Nikki Salas, Rares Radu, Ioan Stan, Marius Tivadar, and Horia Zegheru (sorted alphabetically) for their help with putting this report together.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










