Hugging Face Repositories Used to Spread Android RAT

Bitdefender security researchers have identified a new Android malware campaign that used the Hugging Face public-facing infrastructure to host its malicious files.
Attackers are always searching for trustworthy domains they can use to host their files. These domains don’t usually generate suspicious traffic, so criminals know they can use them to launch attacks that are harder to intercept.
Hugging Face is an open-source platform deployed by users and researchers across the world to host machine learning models, datasets and other tools. It’s mainly used to develop and deploy natural language processing and other AI apps.
While the platform has been used in the past to deploy malicious models, its main attraction in this case is that it offers a way to host various file types, not just those needed to develop AI solutions.
Sideloading APKs is still a problem
In this campaign, attackers hosted the necessary APK files directly on Hugging Face, inside a dataset that was set as public.
Potential victims likely saw an ad or a warning that their device was infected, and were encouraged to download a security app named TrustBastion that promised to do everything they wanted, for free.
Unfortunately for the victim, the fake security app is actually a dropper for an Android RAT (remote access trojan) and contains no actual functionality.
Once the user manually installs the app, the dropper immediately displays a prompt that tells users an update is required to continue using the application.
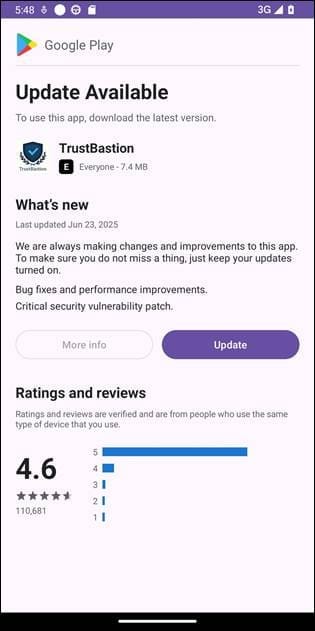
The victim is presented with visuals that are made to look like Google Play and Android system update dialogs. If they go through with the installation and follow the instructions, they will eventually install an application capable of recording user activity and capturing screen content. It can also harvest sensitive credentials, like the lockscreen password.
Hugging Face is also a victim
The malware is not particularly surprising with its RAT functionality – what makes this campaign all the more interesting is its use of Hugging Face’s infrastructure. The service’s public-facing repositories were used to host the APK eventually served to victims.
Hugging Face deleted the repositories very quickly after being notified.
Android malware doesn’t always come from shady websites. Attackers often abuse trusted platforms to distribute malicious apps. Bitdefender Mobile Security for Android protects you with real-time malware detection, blocks malicious APKs before installation, and detects spyware and Android RAT behavior, even when threats are hosted on legitimate services.
You can check our in-depth analysis of this malware on Bitdefender Labs.
FAQ – Hugging Face and Android malware
What is Hugging Face?
Hugging Face is an open-source platform used to host AI models, datasets and machine learning tools.
Why did attackers use Hugging Face?
As a trusted domain, files hosted there are less likely to raise security warnings.
Was Hugging Face hacked?
No. Attackers abused legitimate public repositories.
What malware was delivered?
An Android dropper that installs a Remote Access Trojan (RAT).
How were victims infected?
Users were tricked into sideloading a fake security app called TrustBastion.
Why is sideloading dangerous?
It bypasses Google Play’s security checks and exposes users to unverified apps.
What does the RAT do?
It monitors user activity, captures screens and steals sensitive credentials.
How did Hugging Face respond?
The malicious repositories were removed shortly after notification.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
How Do You Manage Your Passwords? We Ask Netizens
December 18, 2025
Cybercriminals Use Fake Leonardo DiCaprio Film Torrent to Spread Agent Tesla Malware
December 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







