Bitdefender Threat Debrief | January 2026
LockBit Is Back!
This edition of the Bitdefender Threat Debrief covers the latest developments in the ransomware threat landscape, including an update on LockBit’s move to the Top 10, the Coinbase Cartel’s recent activities, a thwarted BreachForums comeback, and more.
As ransomware continues to evolve, our goal with this monthly Bitdefender Threat Debrief is to help you stay ahead of the curve. To do this, we combine information from openly available sources (OSINT) - things like news reports and research – with data we gather by analyzing Data Leak Sites (DLSs), websites where ransomware groups post details about their victims. It is important to remember that we can't independently verify all of these claims but are confident in the trends we see over time.
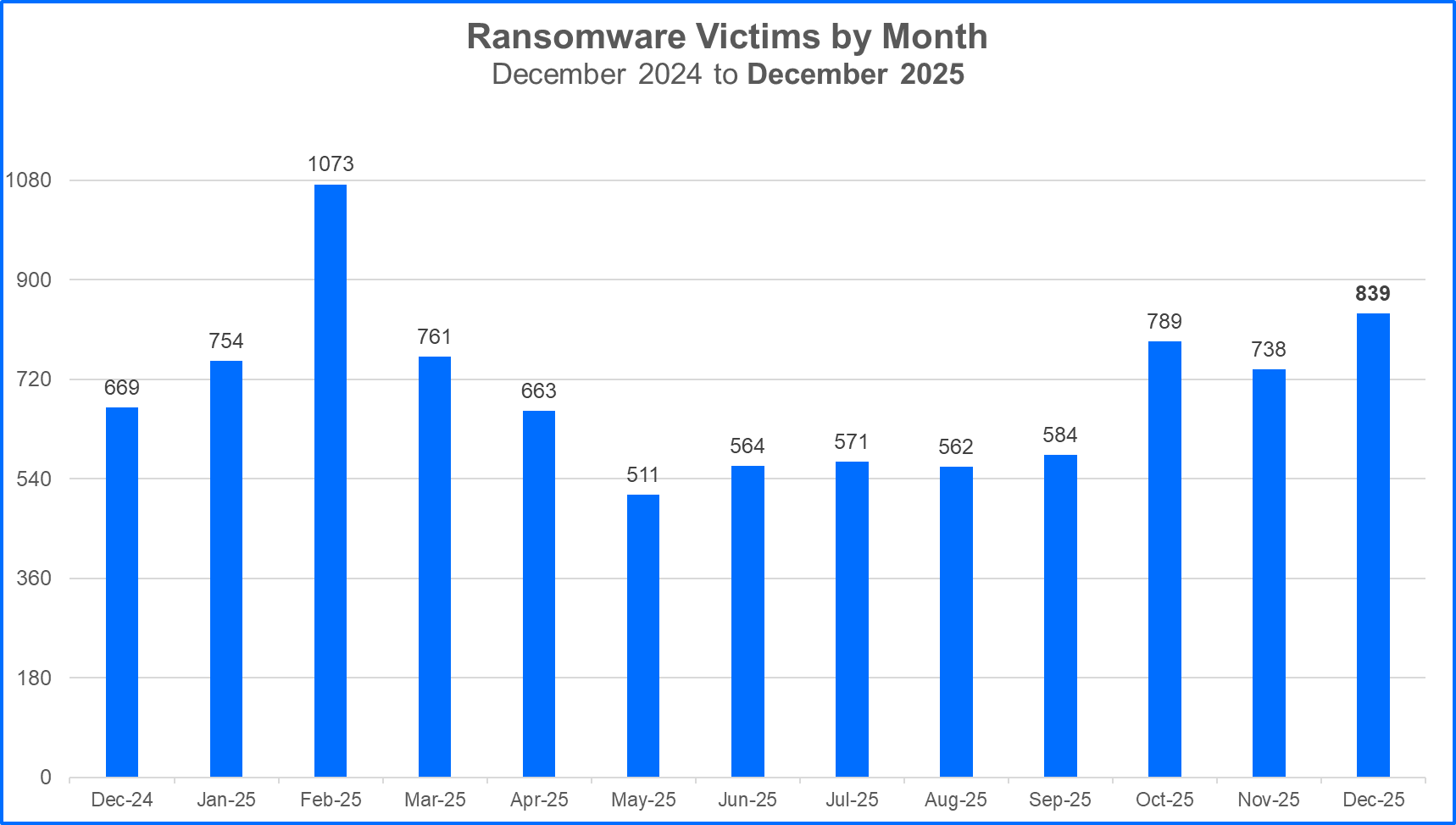
For this month's report, we analyzed data from December 1 to December 31 and recorded a total of 839 claimed ransomware victims, which was the second largest number of claimed victims of any month in 2025.
 Featured Story: LockBit is Back
Featured Story: LockBit is Back
What Happened?
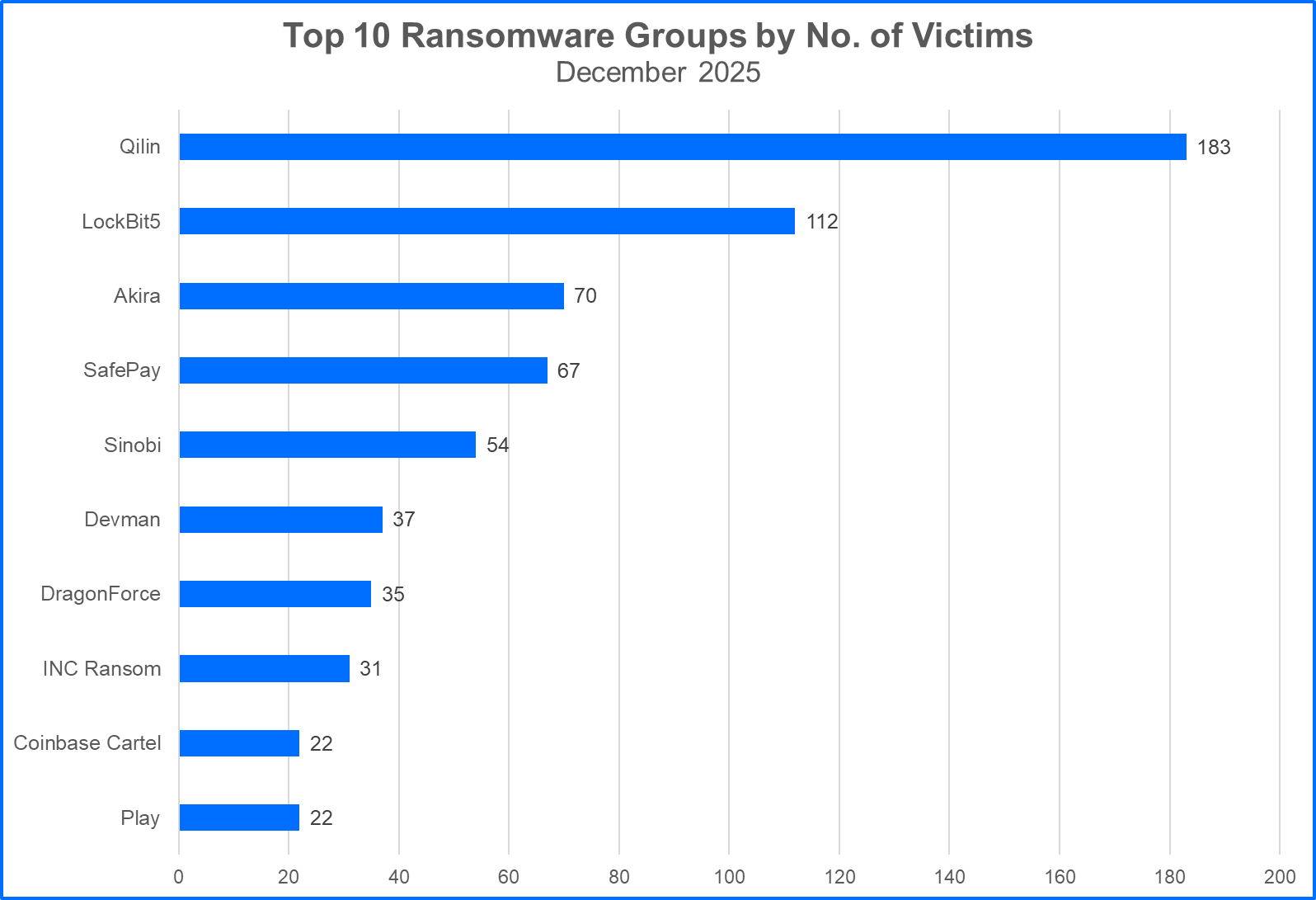
LockBit returned to the list of Top 10 Ransomware Groups in December, claiming 112 victims. This was a significant milestone for LockBit, which suddenly fell from the Top 10 list in October 2024 and failed to claim any victims at all from June to November 2025. This period of inactivity may be due to changes in infrastructure or allowing time to expand the internal team and affiliate network.
The group’s victims were hit with the LockBit5 ransomware variant, and the main industry targets in December included manufacturing, technology, and construction. The group also targeted other industries like transportation, financial services, and healthcare.
LockBit’s Reputation Roller Coaster
LockBit’s reputation has been both up and down over the years. It took a significant hit following Operation Cronos, which disrupted the group’s operations in 2024. LockBit tried to rebuild its reputation by announcing a 2025 collaboration with the Qilin and DragonForce ransomware groups. However, this may have been more talk than action, and many security researchers remain skeptical that this was a legitimate ransomware alliance amongst the three groups.
And while ransomware groups frequently compromise organizations, they are sometimes targeted themselves, and LockBit is no exception. Details on LockBit’s infrastructure, including their domains and an IP address, have already been leaked. That’s why some security researchers are questioning the longevity of the group’s return and the effectiveness of their operations, which are marked by a history of OPSEC (operational security) deficits.
One helpful development for defenders is that one of the tools LockBit incorporates into its attacks has been identified. The tool, SmokeLoader, has been used by groups like Qilin and ALPHV for several years. This suggests that LockBit lacks the resources needed to incorporate (and develop) a broader range of toolsets into attacks.
What Aspects of LockBit5's Activity Are Most Concerning to Organizations?
Like other ransomware, LockBit5 has iterations to use against different hosts, including Windows, Linux, and VMware ESXi servers. As groups such as LockBit continue to prioritize hypervisors specifically, it is important to ensure that security practices to protect against such threat actors are implemented. The most essential practices include updating hypervisor and related management platforms, implementing a tested, quality backup and recovery plan, and adopting an attack surface reduction solution to identify and mitigate threats as they move across the environment in real time.
Other Notable Ransomware News
Now, let’s explore some other notable news and findings since the last Threat Debrief.
- Qilin’s Claimed Victims Decline After Korean Leaks Campaign Qilin claimed 183 victims in December, more than any active group for the month. While the ransomware group’s greatest victim population has been organizations based in the United States, over the last few months , Qilin's breaches targeted organizations based in East and Southeast Asia. In December, both Malaysia and the Philippines were among the Southeast Asia regions affected by Qilin's attacks.
- Clop Falls from the Top 10 Groups
While Clop claimed 14 victims in October and 98 victims in November, the group had a rapid decline in activity in December, claiming only one victim. This could indicate a break, or perhaps the group is prioritizing recruitment efforts or vulnerability research initiatives before launching a new campaign. Clop had a similar pattern of reduced activity from April to August 2025 following the group’s record-breaking surge in attacks which totaled over 300 victims in March.
- Coinbase Cartel Strikes United Arab Emirates Healthcare Organizations
Coinbase Cartel, a ransomware group initially known for their focus on data theft and data brokering, claimed 11 healthcare victims in December, which represented 50% of their victim demographic. Healthcare continues to be a targeted industry due to its critical services, interactions with multiple sensitive datasets, and common use of legacy or vulnerable systems in various fleets that may interact with the network, IoT devices, and other medical equipment.
- Orion Claims LockBit Victims and Publishes Their Leaks
Orion, also known as Orion Leaks, is a group that emerged in the shadow of LockBit’s recent Top 10 milestone. When examining Orion’s data leak site, it’s apparent that they are listing the same victims associated with LockBit as well as LockBit’s leaks. This strategy of claiming victims from attacks orchestrated by other ransomware groups was observed in early 2025 with the group Bjorka, making plausible the theory that Bjorka was rebranding or evolving.
- BreachForums Revival and Disruption
BreachForums, a site marketed to cybercriminals to acquire goods and purchase hacking and other services, dates back to 2023. Earlier this year, law enforcement seized two iterations of the BreachForums site: one in June and another in October. Both were associated with ShinyHunters, particularly the collective Scattered LAPSUS$ Hunters. The site that emerged in December is likely a version of a past instance. However, ShinyHunters recently leaked a BreachForums database file containing the names of thousands of users registered on the forums and unique IP addresses associated with users. The leaked data shared on a ShinyHunters site was posted by the user James. This compromise shows the struggle and competing forces at play between BreachForum’s current staff and the ShinyHunters group to determine who will manage future infrastructure. - BBQLL Ransomware Group Recruits Affiliates
BBQLL is a ransomware group that is actively seeking out those with experience in AD (Active Directory) penetration testing, cloud penetration testing, and container penetration testing to join their operations. The group is offering affiliates 90% of profits and boasts features such as tooling written in Rust, a self-deleting executable, swift encryption, and support for BYOVD attacks. BBQLL has even offered affiliate candidates the opportunity to submit their interest and contact information for the chance to trial its RaaS platform. These claims from a lesser-known ransomware group are striking and likely indicate that we’ll be hearing much more about this group’s victims in the future.
Top 10 Ransomware Families
Here are the top 10 most active ransomware groups:
 Bitdefender's Threat Debrief analyzes data from ransomware data leak sites, where groups publicize their claimed number of compromised organizations. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and may be unreliable. Additionally, this method only captures the number of victims claimed, not the actual financial impact of these attacks.
Bitdefender's Threat Debrief analyzes data from ransomware data leak sites, where groups publicize their claimed number of compromised organizations. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and may be unreliable. Additionally, this method only captures the number of victims claimed, not the actual financial impact of these attacks.
Top 10 Most Attacked Countries
Here are the top 10 countries where ransomware groups victimized organizations: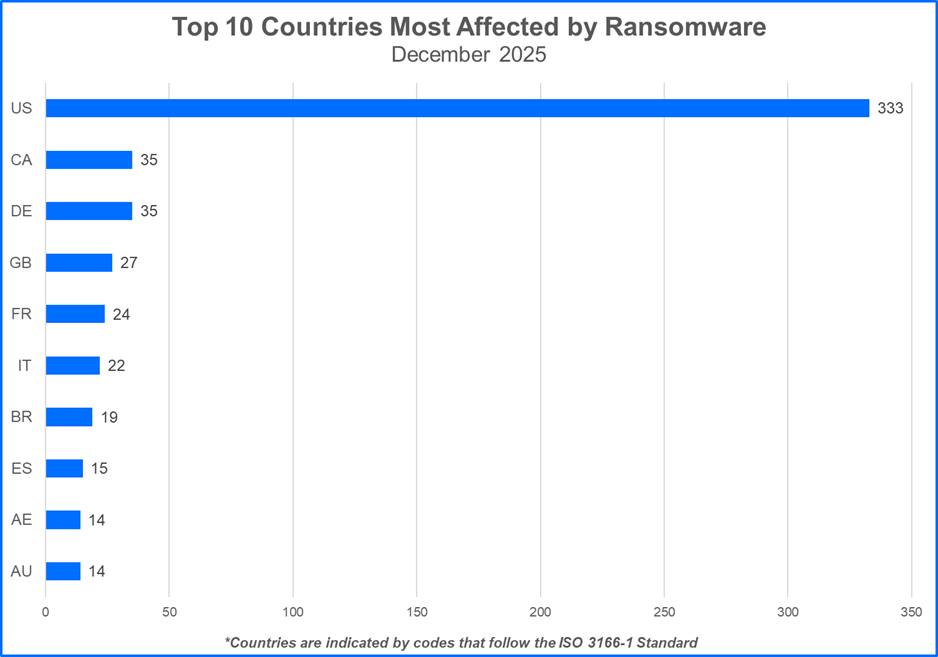 Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. In many cases, this means focusing on developed countries with higher projected growth rates. Threat actors may also execute strategic attacks that unfold during geopolitical conflicts or periods of social unrest.
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. In many cases, this means focusing on developed countries with higher projected growth rates. Threat actors may also execute strategic attacks that unfold during geopolitical conflicts or periods of social unrest.
Top 10 Most Attacked Industries
Here are the Top 10 industries affected by ransomware attacks. Manufacturing was hardest hit: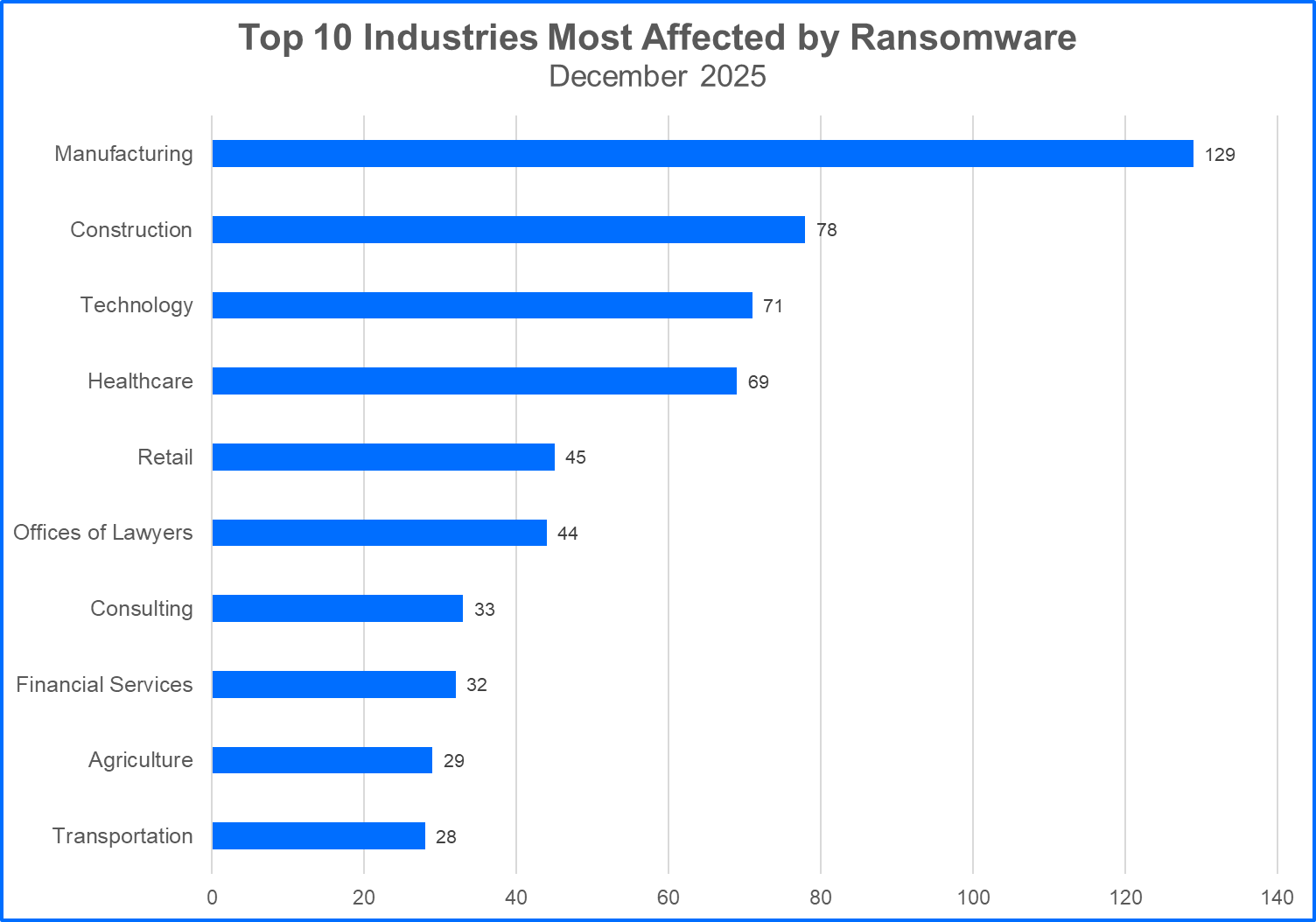 Ransomware gangs may target organizations in critical infrastructure sectors, select other organizations that offer services tailored to consumers, or attack organizations that fall into both categories. Understanding the trends and ramifications associated with specific industries, and how specialized services and clientele are impacted is crucial for assessing risk.
Ransomware gangs may target organizations in critical infrastructure sectors, select other organizations that offer services tailored to consumers, or attack organizations that fall into both categories. Understanding the trends and ramifications associated with specific industries, and how specialized services and clientele are impacted is crucial for assessing risk.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on X.. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed Bitdefender technology and added it to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Stefan Hanu, Mihai Leonte, Gabriel Macovei, and Andrei Mogage for their help putting this report together.
tags
Author
Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsYou might also like
Bookmarks

