Pi2Day Scams: Crypto Users Targeted in Coordinated Facebook Ad Campaign Delivering Malware and Stealing Wallets

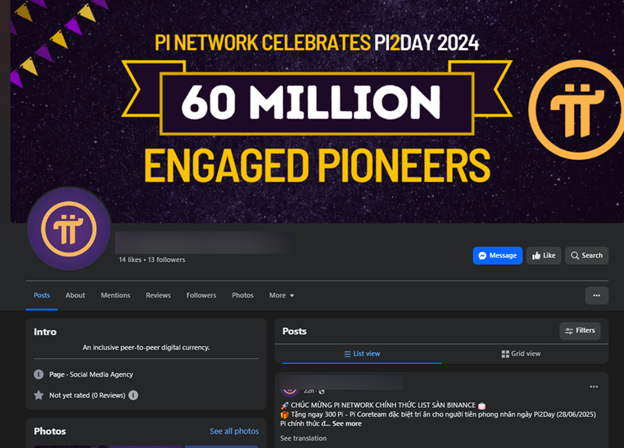
The Pi2Day event, celebrated June 28, is a highly anticipated moment for the Pi Network community, traditionally marked by feature launches, development updates, and platform milestones. This year, though, the celebration has attracted cybercriminals, who are running a malicious ad campaign on Facebook to phish for crypto wallet recovery phrases and spread malware.
Bitdefender Labs researcher Ionut Baltariu has identified this wave of scams as part of a larger, ongoing operation that also includes:
- A malicious campaign exploiting cryptocurrency brands
- Fake “message notifications” from platforms like Binance and TradingView that push malware under the guise of urgent security actions.
What’s the Pi2Day Scam?
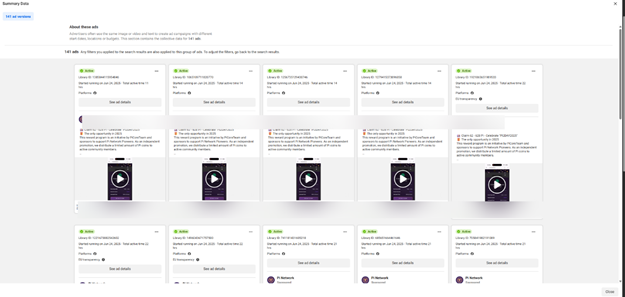
Since June 24, threat actors have set up over 140 ad variations using the Pi2Day branding and Pi Network visuals to drive traffic to phishing pages or malicious apps. According to our analysis, attackers are targeting users globally, including the US, Europe, Australia, China, Vietnam, India and the Philippines.
Let’s break down the two scam variations:
Phishing Pages
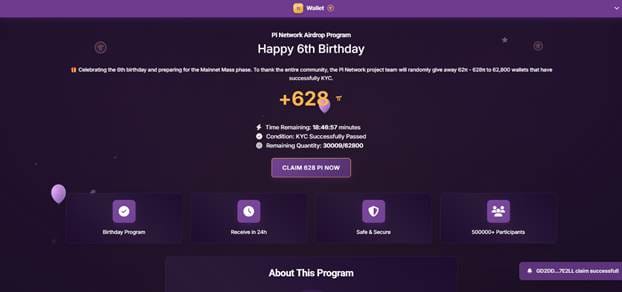
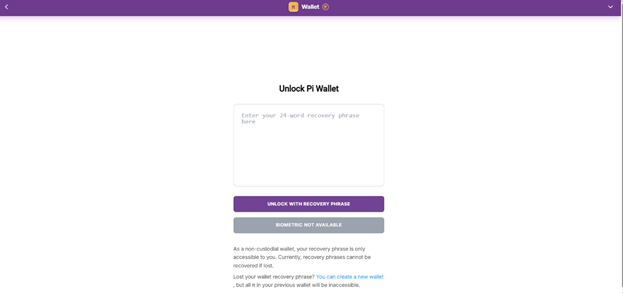
The fake websites mimic Pi Wallet portals and prompt users to enter their 24-word recovery phrase under the promise of claiming 628 Pi tokens or accessing airdrop events.
If entered, the attacker gains full control over the wallet and can transfer any funds immediately.
Malware-Embedded "Mining Apps"
Other versions offer free Pi mining software or “claim” apps promising users bonuses of 31.4 PI for installing PC applications. These installers actually contain malware — the same strain found in our earlier analysis: Generic.MSIL.WMITask and Generic.JS.WMITask (Only this tactic is used to deliver the multi-stage malware described in our May 2025 research).


These malicious payloads can:
- Steal saved credentials and crypto wallet keys
- Log user input
- Download second-stage malicious components
- Remain stealthy using obfuscation and sandbox evasion
Why This Scam Is So Dangerous?
Pi Network’s appeal lies in its easy “mining” model on smartphones, attracting many users with little or no experience in cryptocurrency. These users may not realize:
- That recovery phrases must remain private
- That even verified Facebook ads can be fraudulent
Add hype, rewards, and a tight countdown timer and you have a scam designed to go viral.
What do all of these campaigns have in common?
All three of these campaigns:
- Exploit trust in popular platforms (Meta/Facebook, Binance, Pi Network)
- Use deceptive Facebook ads to lure users to malicious websites
- Deliver a strain of multi-stage malware already analyzed by Bitdefender
- Share identical detection-evasion tactics and infrastructure patterns
This strongly suggests that a single threat actor group is behind all of them — running parallel fraud schemes on Meta to maximize reach, financial gain, and targeting efficiency.
How Bitdefender Responded
Bitdefender was the first vendor to detect and block the latest variants of the malware used in this campaign. All fake domains and payloads in this attack are now actively blocked by Bitdefender solutions.
How to Stay Safe
- Never enter your wallet’s recovery phrase on any website.
- Don’t trust ads offering crypto bonuses, free mining apps, or Pi airdrops without verifying the source.
- Only download apps from official app stores or the official Pi Network site.
- Use Bitdefender Scamio to verify suspicious messages and websites before interacting.
- Keep Bitdefender Security Solutions active on both your PC and smartphone to protect against phishing and malware downloads.
We urge all investors, new and seasoned, to watch out for these scams. This isn’t just a one-off swindle exploiting the June 28 event. It’s part of a coordinated campaign leveraging Meta's ad system to run multiple simultaneous scams against investors and crypto afficionados. Beware of:
- Fake security alerts tied to Facebook accounts
- Malware disguised as partnership messages from Binance and TradingView
- Pi2Day scam exploiting crypto novices
By shifting themes and visuals while reusing the same malware and infrastructure, this group maximizes their ability to evade detection and defraud more people.
Bitdefender will continue to track and stop these threats, and we urge users to approach Facebook ads (YES, even from verified accounts) with a healthy dose of skepticism.
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsYou might also like
Bookmarks
