IoT Device Life Cycle: When Is It Time for Replacement?
Smart gadgets don’t last forever. Knowing when to retire dated devices is a crucial part of maintaining a secure IoT ecosystem.
Why device life cycle matters for security
Each connected device – from smart plugs to baby monitors – moves through a life cycle: purchase, setup, use, maintenance, and decommissioning. Security risks evolve throughout their entire life cycles, and almost always spike toward the end of support.
The importance of managing IoT-associated risks through the device’s life, including end-of-life (EOL) and disposal, cannot be overstated. As expected, many households fall short exactly at the device’s last life cycle step – disposal.
Aside from suggesting and implementing new rules and policies, regulators increasingly expect clearer update practices from manufacturers and consumers. In the UK, the Product Security and Telecommunications Infrastructure (PSTI) regime, enforced since April 29, 2024, mandates better baseline security and transparency (including related to updates) for consumer-connected products.
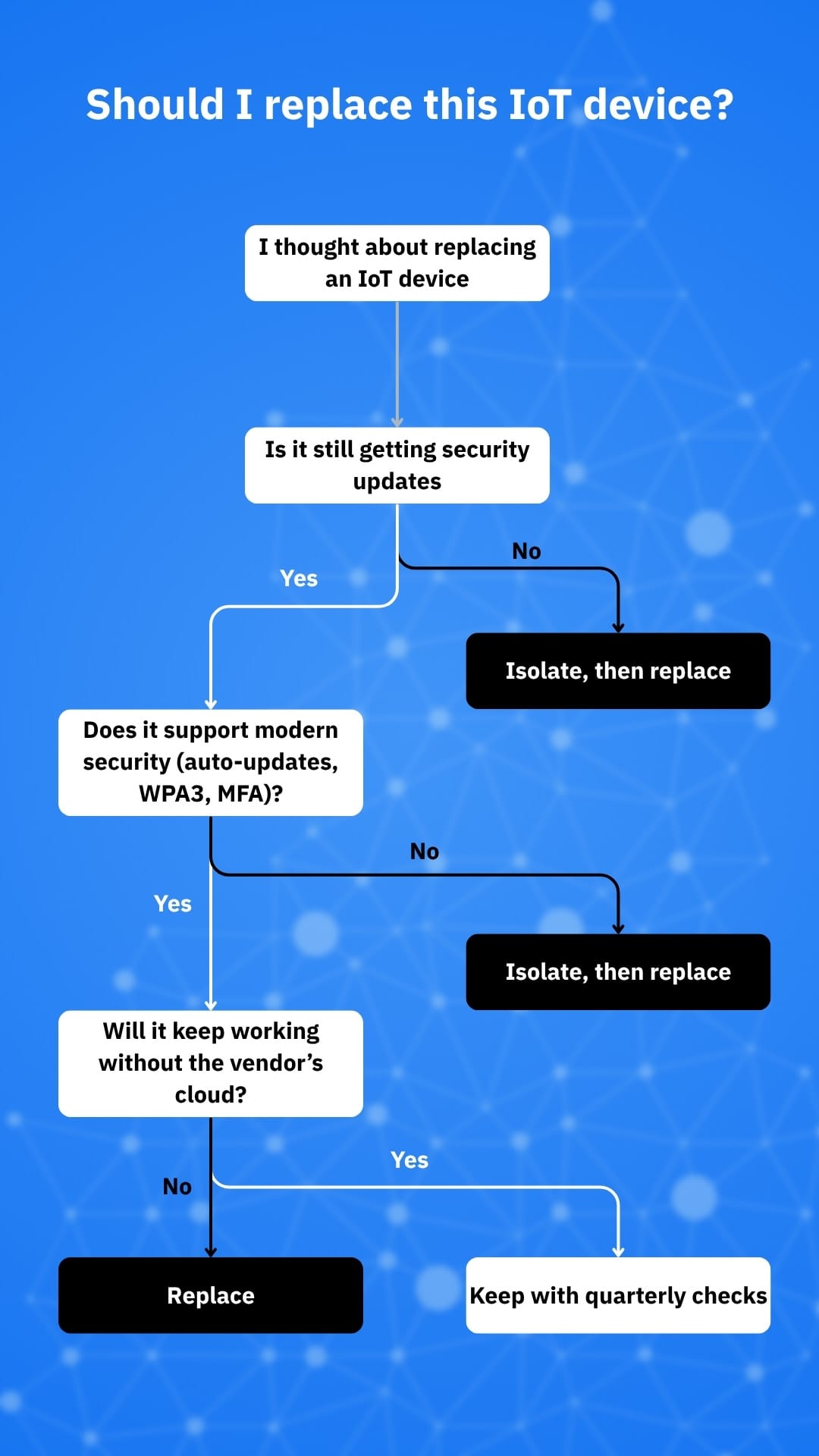
The quick solution: replace a device when any of these are true
Several factors help you determine where exactly your product is in its life cycle. If you want a quick answer, though, just use the short list below as your baseline and start planning a replacement if you hit any of these:
- No security updates (EOL/EOS): If the vendor no longer issues patches, the safest path is to take the device offline or retire it entirely. A lack of updates can leave you exposed and even break functionality.
- Cloud dependency at risk: If a device stops working without the vendor’s cloud and that service is shutting down (or looks like it’s about to), plan for replacement. The 2016 Revolv hub shutdown is a classic cautionary tale: a working $300 device became an expensive paperweight when the cloud died.
- Insecure or obsolete protocols: If a device forces weak wireless standards (e.g., older WPA2-only in a setup that could run WPA3, or worse, legacy modes), it’s time to phase it out. WPA3 is the current Wi-Fi security baseline for modern gear.
- Unpatchable vulnerabilities or repeated compromises: When a device keeps getting hit and patches lag (or the vendor simply can’t fix it), replacement beats containment. Improperly managed Internet-facing “edge” devices, including IoT, pose a serious risk to most households.
- No meaningful vendor transparency: If you can’t find exactly how long updates last, whether there’s a disclosure program, or how to export your data, that’s a red flag.

Special cases worth fast-tracking
Routers and Wi-Fi gear
It’s worth noting that your router is a security boundary that links all network-enabled devices in your household to each other and to the internet. If it’s out of support or can’t do WPA3, prioritize replacement. This single upgrade often raises the bar for your entire household ecosystem. Edge devices such as routers are often prime targets for cyberattacks.
Cameras, baby monitors and smart doorbells
If updates stop or the vendor’s cloud is shaky, replace your device immediately. Look for models with local recording abilities and clear update commitments. Cloud shutdowns can kill critical functions overnight, so it’s better to jump out of a sinking ship while there’s still time.
Smart TVs and appliances
When a manufacturer halts updates, disconnect the device from the internet (keep it “dumb”) and pair it with a separate, supported streaming box, then plan a replacement cycle. Disconnecting smart devices once they reach their end-of-life/end-of-support (EOL/EOS) can greatly reduce the risk of being targeted by attacks that exploit unpatched vulnerabilities or zero-days.
How to check support status in minutes
One of the most common hiccups in managing IoT device life cycles is that, for many consumers, the process of checking a device’s support status can be confusing. Here’s how you can do so with minimum effort:
1. Find the firmware page
Identify your device using its exact model and serial number, if possible, on the manufacturer's website. Note the latest version and date, and check that the firmware used by your device matches these two parameters.
2. Scan security/news pages
Keeping an eye out for the latest developments regarding your devices can keep you out of trouble. Simply search for news regarding your brand and model online (e.g., “[brand] vulnerability disclosure” and “[brand] EOL policy”) and you should receive info that could help you plan your device’s life cycle accordingly.
3. Look for stated update windows
Reputable manufacturers are typically transparent with their devices’ update windows. If you want to make sure, search for your model number paired with key phrases like “receives security updates for at least X years” and you should find something useful. Regulators now push for this level of transparency.
4. If unclear, assume the clock is ticking
Sometimes the steps you need to take to determine how much time your device has left are so convoluted that people outright give up on checking. Some manufacturers intentionally make these steps hard to follow to extend the likelihood of customers purchasing devices nearing EOL/EOS. If you’re unsure or simply can’t find a way to check your device’s life cycle, start planning for isolation or replacement as soon as possible or within 6-12 months.

Choosing a safer replacement without blowing the budget
When you shop, evaluate three things:
- Update commitment and security baseline: Look for things like automatic updates, unique default passwords and a published minimum update period
- Local controls and open standards: Prioritize choosing devices that still function if the cloud disappears and that use common standards so you can switch ecosystems later.
- Ecosystem hygiene: Confirm the maker has a vulnerability disclosure program and plain-language security documentation.
Plan the swap and mitigate risks while you wait
1. Isolate old devices on a guest or IoT network: Keep decommissioned devices outside of your main network, without access to your laptop/smartphones. If your router doesn’t support network segmentation, that itself could be a replacement signal.
2. Inventory credentials: Keep track of important things like admin logins and API keys, backup configurations if possible and export any data you want to keep.
3. Stage the new device: Enable automatic updates and enforce strong authentication on day one. Prefer WPA3 if your router supports it.
Decommissioning without leaking your data on the way out
Before you sell, recycle, or toss a smart device, follow these few steps to reduce your exposure post-decommissioning:
- Erase all personal traces: Remove the device from your account, unpair integrations and factory-reset it based on the maker’s instructions.
- If you can’t reset: Sometimes things like broken controls or dead screens can prevent you from resetting. In this case, change your Wi-Fi SSID/password and any linked account passwords to cut off lingering access.
- Recycle responsibly: Look for local e-waste programs that accept connected gear. Many retailers even offer trade-in programs where you can recycle old devices and get vouchers to purchase newer models.

A realistic replacement cadence
While there’s no universal answer, for most homes the following replacement scheme seems to work great:
- Routers/Wi-Fi gear: 3-5 years or until EOL/EOS, whichever comes first. Upgrade sooner if you can’t access crucial features like WPA3 or segmenting.
- Cameras/doorbells/locks: Replace at EOL/EOS or if cloud reliability is uncertain. Always prefer models with local/physical fallback.
- Smart TVs/streamers/appliances: When updates stop, disconnect from the internet (keep using them in “dumb” mode) and plan a replacement cycle based on support transparency.
Conclusion
If a device no longer receives patches, locks you out of usage if its cloud stops working or can’t meet modern security standards like WPA3 and auto-updates, it’s time to replace. Use the decision flow, isolate what you can while you wait and always decommission safely. Treat replacements as routine security maintenance instead of failure and you’ll keep convenience without inviting in risk.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsYou might also like
Bookmarks


