Juice Jacking Hits the Highway with Hacked EV Chargers

Public chargers are becoming the next lure in the juice-jacking playbook, this time targeting your phone, your wallet, and – in edge cases – your car. Here’s what EV drivers need to do before plugging in.
Why this matters now
EV charging is exploding, and, with it, a flurry of payment apps, QR codes, vendor backends and new car-to-charger protocols.
Researchers and agencies have been warning for years about “juice jacking” against phones via shady USB ports; threat actors are now adapting similar tricks around EV charging sites, most commonly with fake QR codes for payments and, sometimes, by abusing weaknesses in charger networks.
Quick definitions (plain English)
- Juice jacking (classic): A malicious USB port or cable that charges your device while silently trying to steal data or install malware. Avoid any public USB that isn’t yours.
- EV “juice jacking,” modern flavor: Perpetrators hitch a ride on the EV charging experience, usually with fake QR codes (quishing) that send you to bogus payment sites. Sometimes, they probe charger networks and backends for security gaps.
How attackers target EV drivers
1. Your phone at the site
Some charging plazas still expose USB ports around kiosks or in lounges. Treat any third-party USB as hostile. If your phone prompts for “data access,” deny it. Better yet, use your own AC adapter or a power bank. Multiple government advisories now warn against public USBs for exactly this reason.
Safer choice: Use your own wall plug in a mains outlet or a data-blocking USB adapter.
2. Your wallet via quishing (fake QR payments)
The most common EV-specific scam is low-tech but effective: threat actors slap a sticker QR code over the real one. You scan, land on a convincing fake portal, enter card details or app credentials, and your money is gone. This pattern has been reported at parking meters and EV sites in multiple countries, and consumer groups have issued alerts.
Red flags to spot:
- Watch for bubbly, misaligned or duplicate QR stickers; a QR that covers another label; URLs that don’t match the operator, and sudden demands to “install an app from this link.”
- Payment flows that ask for card plus CVV on a site you’ve never seen from that operator. Use the official app or contactless card on the terminal instead.
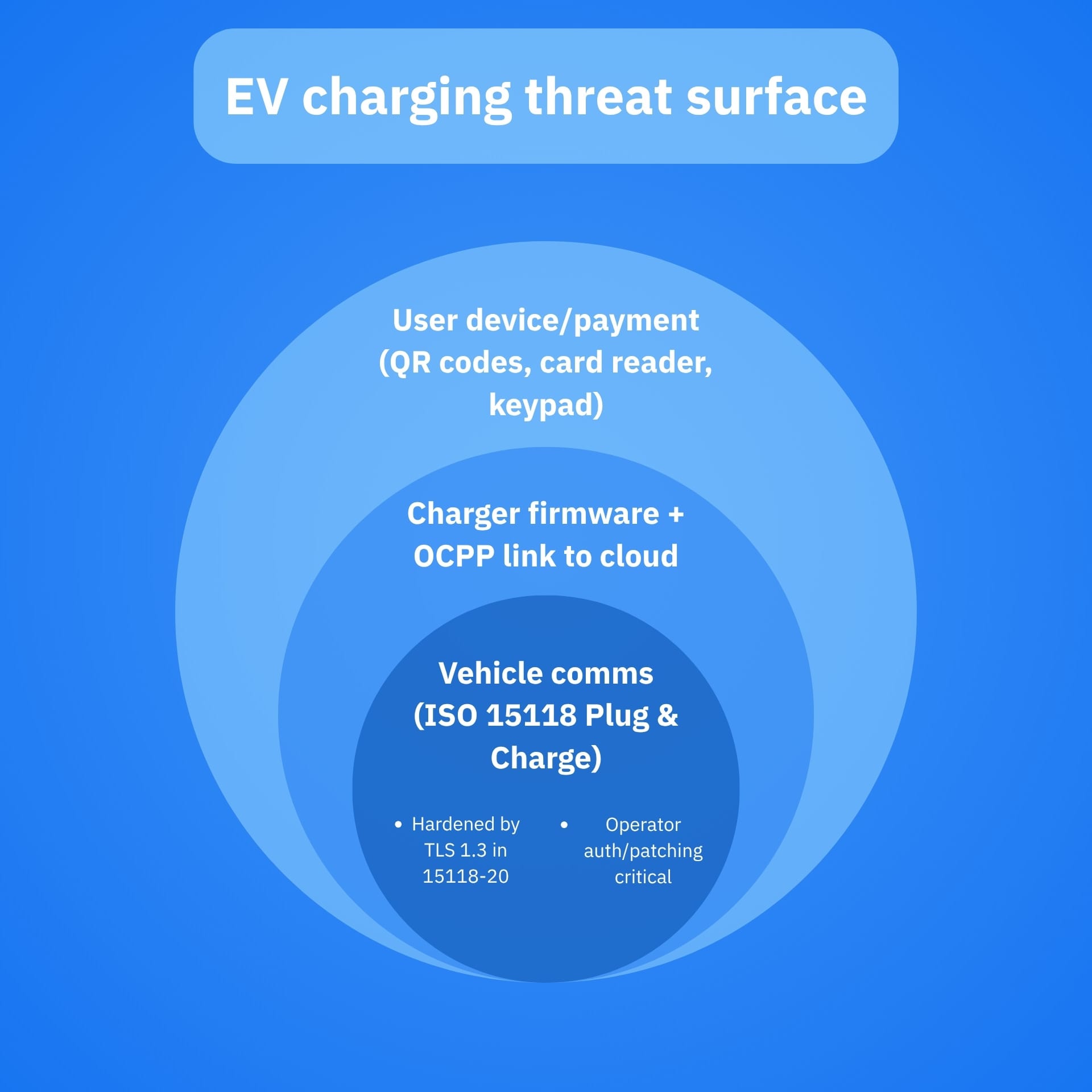
3. Your car via charger/backend weaknesses
Charging networks rely on standards like the OCPP (charger <-> cloud) and ISO 15118 “Plug & Charge” (car <-> charger). Studies have documented risks: weak auth on some OCPP deployments and earlier ISO 15118 variants that allowed unencrypted sessions in certain scenarios (fixed in ISO 15118-20 with mandatory TLS 1.3). Practical car-hacking from a public charger is still a high-skill, low-frequency scenario, but the research tracks show why operators must harden systems.
Real-world signs that chargers can be compromised aren’t always subtle. Remember those UK chargers that were hacked to display explicit content? If vandalism is possible, tampering is just a step away.
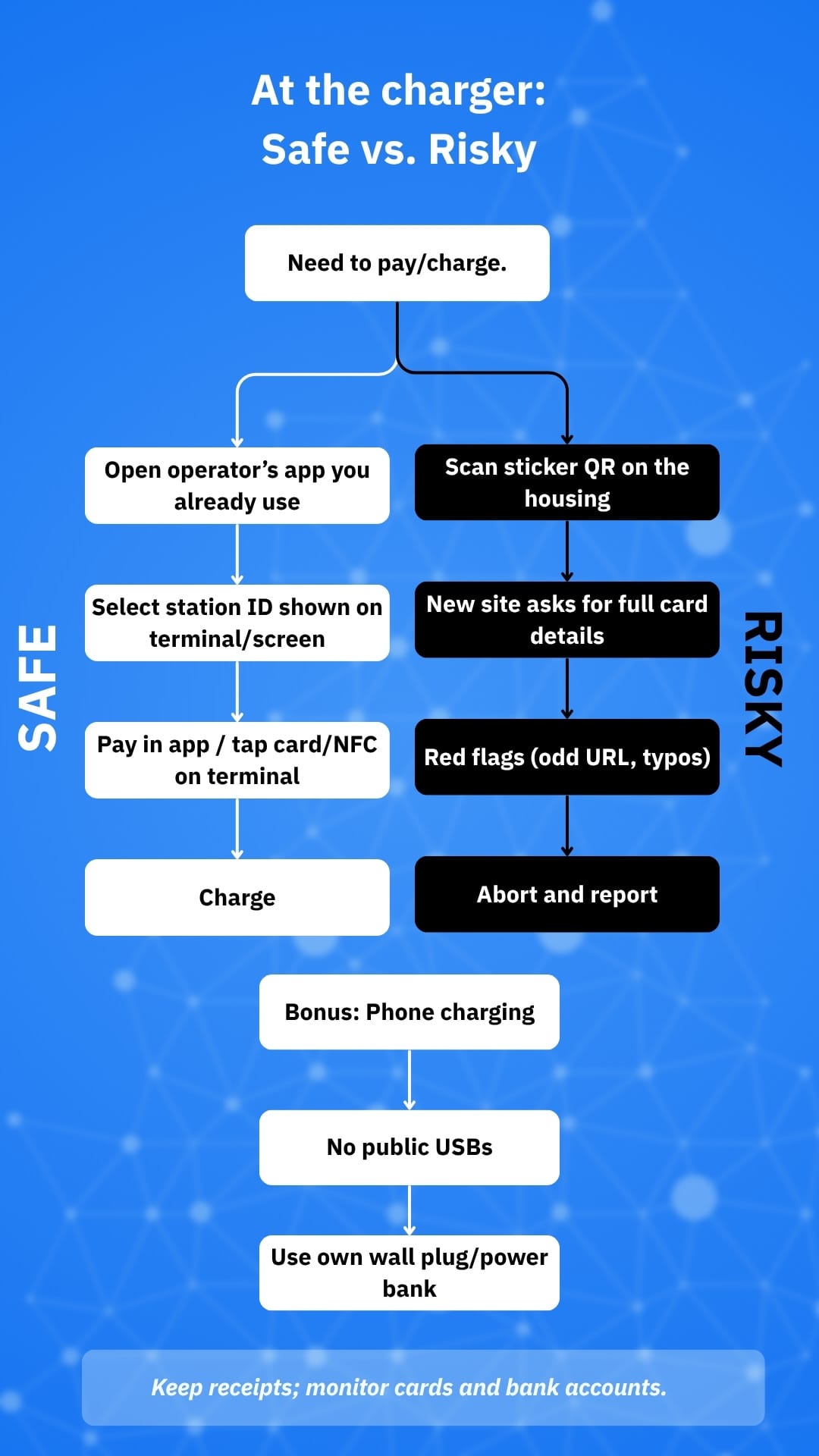
What to do at the charger (field-tested checklist)
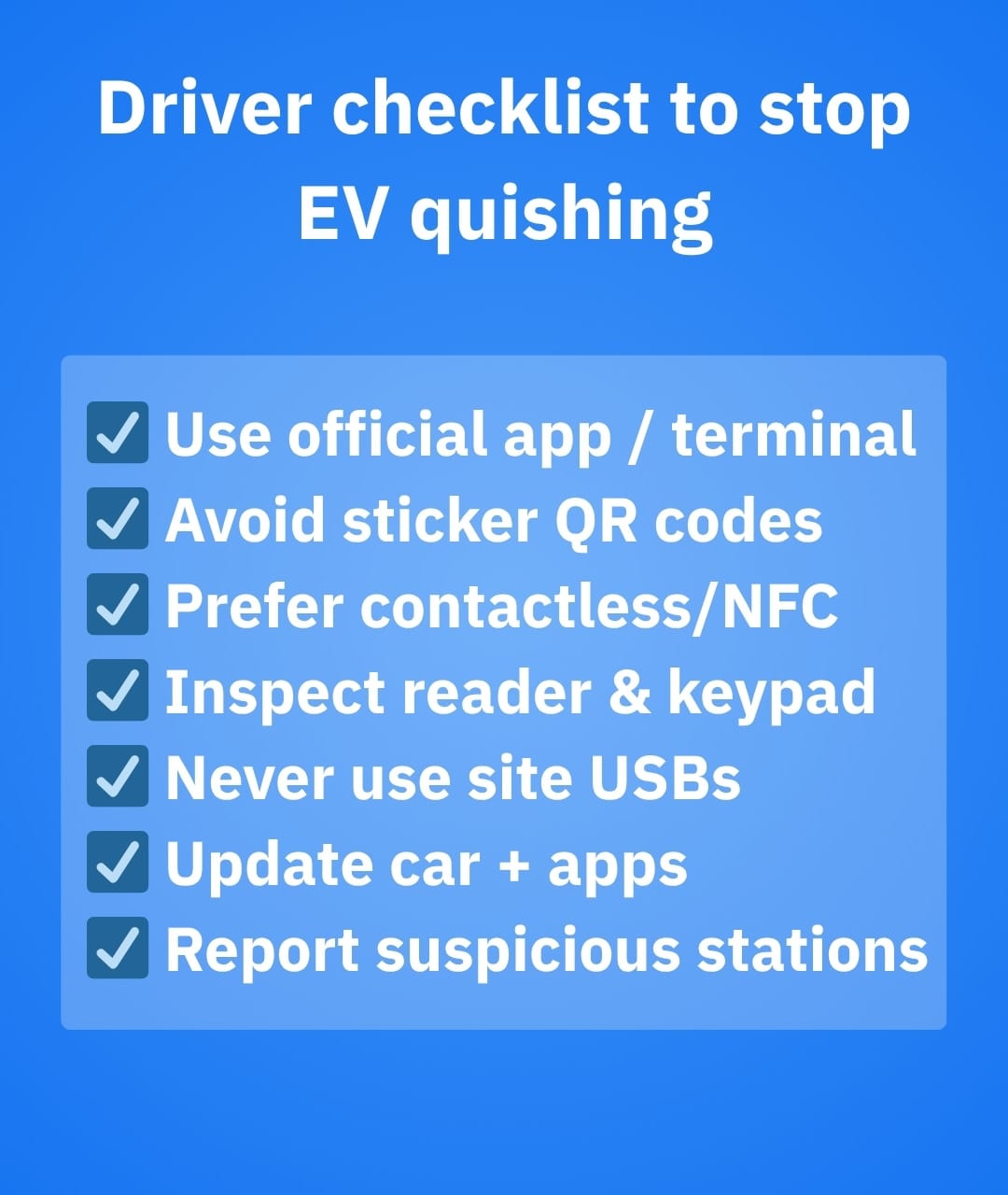
- Use official apps or the built-in terminal only. Don’t follow QR codes stuck onto hardware; if you must scan, compare the URL against the operator’s website or app.
- Prefer contactless card/NFC on the terminal over QR payments. If there’s no terminal, launch the operator’s app from your phone, not from a sticker link.
- Inspect before you tap: tug the bezel around readers; loose overlays can be skimmers. Cover your PIN if a keypad is used. These skimmer tactics from fuel pumps or ATMs are migrating to wherever cards are used.
- Avoid stray USB ports. If you must charge your phone, use your own power brick in a mains outlet or a power bank.
- Keep your EV and apps updated. Firmware and app updates close known holes in chargers and vehicles as research labs continue to find issues.
- Report suspicious sites or equipment to the operator and your card provider quickly – faster reports can limit losses and help others.
Myth vs reality
- “Public chargers will hack my car.” Reality: consumer-grade attacks usually target your phone or payment, not deep in-car systems. Charger/backend hacks do exist in research and occasionally in the wild, but they’re far more rate than QR scams or skimming.
- “QR payments are always safe.” Reality: QR codes are just pointers, easy to replace with a malicious lookalike. If the code wasn’t printed under the panel or shown inside the official app, risk exists.
For the technically curious
- OCPP is the lingua franca between chargers and their cloud; poorly authenticated instances and outdated deployments are a known risk. Pentesters regularly find exposed or misconfigured backends.
- ISO 15118-20 tightens Plug & Charge with mandatory TLS 1.3, significantly raising the bar against man-in-the-middle or message tampering that earlier variants left open in some contexts.
Specialized software
Before you plug in to your next public charger, take two minutes to boost your digital defenses: run the QR or payment link through Scamio and make sure your devices and identity are covered by an all-in-one suite like Bitdefender Ultimate Security. It’s one of the smartest ways to charge with peace of mind.
- Bitdefender Scamio: A free, AI-powered scam-detection tool that helps users verify links, QR codes, messages, images, and other potential fraud vectors (including fake charging station QR scans).
- Bitdefender Ultimate Security: A full-suite digital protection solution covering malware, VPN, password manager, scam detection features and more – perfect for EV drivers exposing themselves to varied infrastructure threats.
Frequently Asked Questions (FAQ)
Does juice jacking still happen?
Yes. It’s rare but still occurs in public USB ports. Most modern scams now target payment info via fake QR codes instead of skimming payment terminals. The core advice is the same: avoid public USB ports and use your own trusted power source.
Do portable chargers prevent juice jacking?
Absolutely. A portable power bank acts as a physical barrier between your device and any potentially compromised charging port. Since your phone connects only to your own battery’s USB output, no data can be exchanged with an attacker-controlled port. It’s the simplest and most reliable way to stay safe when you need power on the go.
Is the FBI warning about USB charging?
Yes. The FBI has repeatedly warned consumers to avoid public USB charging stations, especially in airports, hotels and shopping centers, because criminals can modify them to install malware or steal data. The bureau recommends carrying your own charger and plugging into an AC outlet instead.
How to stop people from stealing chargers?
If you mean your personal EV charger or portable cable, practical deterrents help:
- Use lockable charging cables or a padlock system if your EV allows it.
- Keep home chargers indoors or in locked enclosures.
- Label and customize cables; unique markings discourage resale.
- Use motion lighting or cameras near your charging point.
- In public settings, never leave portable chargers unattended, as theft is far more common than tampering.
Conclusion
Public chargers are essential infrastructure, and they’re attractive to scammers. The everyday risk today is payment fraud via fake QR codes and skimmers, while deeper charger/network exploits remain on the rare side, but under active study.
If you pay through official channels, avoid sticker QR codes, skip public USBs and keep firmware current, you’ll neutralize the vast majority of threats while keeping your road trips smooth.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsYou might also like
Bookmarks


