Google Day Scams Put Your Account at Risk

If a message says you won something because “Google is celebrating today,” assume the only thing you’re celebrating is not clicking.
The danger behind Google Day scams
Threat actors have long exploited big names to make their cons more believable, and Google is one of the biggest names. Over the years, fake prize schemes branded as “Google Day” or “Google Anniversary” celebrations have circulated online, tempting victims with promises of rewards for being a “lucky searcher” or “long-time user.” These scams often appear as convincing pop-ups, emails, or text messages and can lead directly to stolen personal information, drained bank accounts or full-blown account takeovers.
For creators and consumers alike, the risks are bigger than losing a few dollars. A compromised Google account often means losing access to Gmail, YouTube, Drive, Photos, and other linked services. That kind of takeover can derail a person’s livelihood, especially for content creators who rely on their channels for income. Understanding how “Google Day” scams work, why they succeed, and how to defend against them is crucial for staying safe online.
What people mean by ‘Google Day’ scams
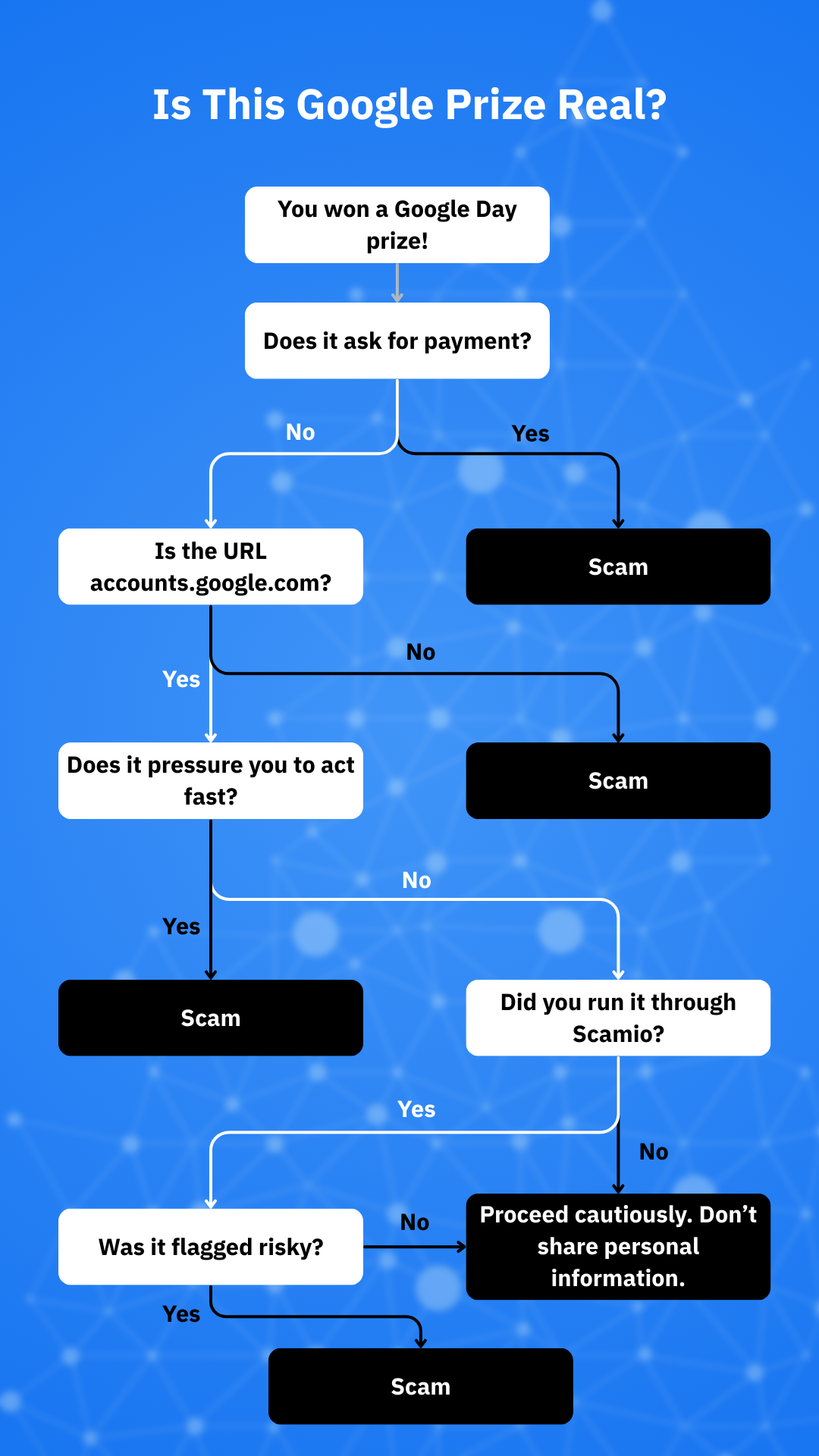
Keep in mind that there’s no such thing as official “Google Day” giveaways or sweepstakes. If you realize that, you’ve already won most of the battle. Scammers simply slap Google’s name and logo onto pop-ups, emails, texts and social posts that claim you won a prize because it’s “customer appreciation” day or an occasion to celebrate an “anniversary” or the “5-billionth search.” The goal is to rush you into handing over personal info, payment details for “fees,” or your Google Account credentials. Google itself warns that it doesn’t run lotteries or prize programs and provides a path to report brand abuse.
Recent waves of look-alike lures include the infamous “5-billionth search” pop-up and “anniversary award” emails. These are both pure phishing attempts wearing celebratory clothing. They often appear via sketchy ad networks or hacked sites and funnel you to forms that harvest data or push malware.
How the scams actually work
At a higher level, the playbook looks like this:
1. The hook: A pop-up, SMS, WhatsApp DM or email claims you’re a lucky winner “today only.”
2. The urgency: A countdown timer or “act now” prompt amplifies the pressure.
3. The harvest: Victims are sent to a web form to enter data or “verify” a Google login on a phishing page.
4. The payoff: Attackers monetize stolen data, take over accounts or install adware/stealers for broader access.
Modern threat actors also abuse Google’s own infrastructure to boost credibility and bypass filter mechanisms. Some malicious campaigns use Google Sites to send emails that look like they come from legitimate Google addresses, (e.g., no-reply@google.com) and Google Forms to trigger convincing “confirmation” emails that redirect to crypto-theft pages.

How these scams could lead to account takeovers (ATOs)
Both creators and everyday users are prime targets because a single Google login unlocks an array of services, including Gmail, YouTube, Drive, Photos and more. Two of the most common ATO paths are:
- Cookie/session theft (“pass the cookie”): Malware or a malicious site steals your session token, letting attackers hijack your account without your password or multi-factor authentication (MFA). Cybersecurity researchers have spotted large-scale campaigns using this exact trick against YouTube creators.
- Adversary-in-the-Middle (AitM) phishing: Kits like VoidProxy can be used to proxy Google’s real login page, intercept credentials and capture MFA codes or session cookies in real time, bypassing weaker MFA setups.
In response, Google and the broader ecosystem have rolled out passkeys widely because they’re resistant to phishing. Furthermore, they implemented the use of Device Bound Session Credentials (DBSC) to render stolen cookies far less useful by cryptographically linking sessions to devices.
Red flags that scream ‘fake Google prize’
The first line of defense against Google Day scams is vigilance. If people recognize the latest scam tactics and learn to identify red flags, scammers’ attempts to deceive may fall short. Common red flags to watch for include:
- “Pay shipping/taxes/processing to claim your reward from Google.” You don’t have to pay for real prizes, particularly from a reputable company like Google.
- The sender domain does not belong to Google or is hidden behind a URL shortener. Look out for links that land on odd TLDs like .xyz or .icu.
- The “reward” page lives on a random website or a hastily built “giveaway” portal. The design may mimic Google but the URL doesn’t match accounts.google.com.
- Messages that use countdown timers, urgent language or too-good-to-be-true giveaways.
Although con artists may stray from the above techniques or use variations, the bottom line is this: you shouldn’t pay for a prize. Also, always slow down when you’re pressured to act “today.”

Do this right now (5-minute security checklist)
Even though Google Day scams come unexpectedly (they do tend to intensify around Google’s anniversary), that doesn’t mean you shouldn’t be prepared for unwanted guests. Make scammers feel unwelcome at your digital doorstep by going through this quick security checklist:
- Enable passkeys for your Google account and keep MFA as backup. Avoid SMS MFA if possible, as it could be bypassed by SIM-swapping attacks, and go for authenticator apps or security keys.
- Run Google’s Security Checkup, review devices and sessions and sign out of anything you don’t recognize or devices you haven’t used for a long time.
- Lock down recovery options (phone, email) and add a hardware key instead, if possible.
- Update your browser and operating system, and enable Enhanced Safe Browsing in Chrome
- Use unique passwords, store them in a reputable password manager (like Bitdefender SecurePass) and quickly change any reused passwords. Recycled passwords can be easily exploited in credential stuffing attacks.
If you already clicked or entered data
Sometimes scammers can deceive even the keenest eye. The sense of urgency often found in rogue communications is especially effective at impeding victims’ critical thinking. If you suspect you’ve already fallen prey to a Google Day scam, here are a few damage control tips:
1. Terminate the session: From another device, change your Google password and sign out of all sessions.
2. Rotate MFA: Remove old app passwords, re-enroll MFA and add a security key or passkey.
3. Scan your devices: Although you may have changed your passwords, your device can still harbor malware. Scan for malware/stealers and remove any suspicious extensions or apps from your devices.
4. Check Gmail filters and forwarding rules: Some threat actors set forwarding rules so they can slide right back in if they’ve been detected. Make sure to check for malicious auto-forwards and remove them as soon as possible.
5. Report the scam: Google has a dedicated page for reporting spam, malware or phishing. Use it so that others don’t share the same fate.
Tools that help you dodge ‘Google Day’ scams
Although vigilance and quick mitigation are crucial to fending off Google Day scams, they might not always be enough. Here’s where dedicated security software shines.
Bitdefender Security for Creators is built for creators and their teams, as it blends continuous account monitoring, anti-scam email protection, account recovery assistance and a unified dashboard across channels and devices. It’s designed to spot suspicious activity early and help you recover fast if something goes wrong.
Scamio, our free AI-powered scam checker, lets you send it messages, links, screenshots or described situations and gives you an instant read on risk. It’s an ideal tool for when the unexpected “Google anniversary prize” DM lands and you want a second opinion before you tap.
Conclusion
“Google Day” is a story scammers use to quickly trick lure people into their trap. If you ever receive such a message, take a deep breath, step back, and assess.
If a prize demands payment or personal info, it’s a scam. Lock down your Google Account with passkeys, keep an eye on sessions and use dedicated security tools to catch red flags early. Your best defense is a cool head, a quick URL check and a security stack that’s built for the tricks criminal often use.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsYou might also like
Bookmarks


