Countdown to CRA 2026 – What EU IoT cyber rules mean for your next smart device

Why the EU’s Cyber Resilience Act (CRA) turns 2026 into a turning point for smart device security and what it means for your connected home.
What the Cyber Resilience Act (CRA) means for IoT security
If you buy smart plugs, cameras, robot vacuums or a shiny new mesh Wi-Fi system, you’ve probably noticed an awkward pattern: features ship lightning fast, while security updates lag behind or simply stop coming. Not to mention how “lifetime support” often turns into “until the next model launches.”
The EU Cyber Resilience Act (CRA) is meant to change that by making baseline cybersecurity a legal requirement for products with digital elements. It will affect all hardware and software that can connect to a network.
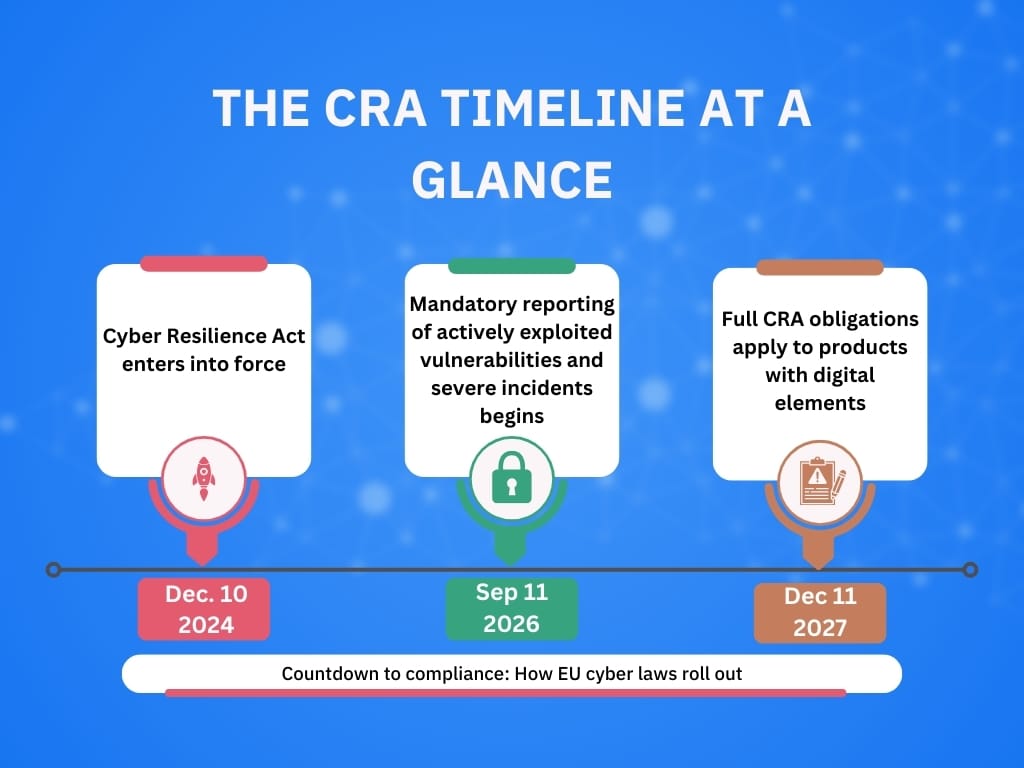
Although the CRA’s main obligations will start becoming mandatory in December of 2027, this year is far from uneventful. 2026 is actually the year the reporting clock starts ticking – an early pressure test that should push manufacturers to tighten their vulnerability handling well before the broader compliance deadline.
CRA reporting obligations and IoT devices
The CRA’s reporting obligations kick in on Sept. 11, 2026. Starting then, manufacturers must report actively exploited vulnerabilities and severe incidents impacting the security of products with digital elements.
For consumers, this matters because it nudges the industry toward a more mature posture, which will favor a more structured disclosure, faster issue remediation and fewer “we-didn’t-know” scenarios. It also creates a paper trail that regulators can use to spot repeat offenders.
What ‘secure by design’ should look like in practice
The CRA’s essential requirements are intentionally broad, or technology-neutral. However, the direction is clear. It aims to enforce fewer insecure defaults, less data exposure and faster patching, all without turning the consumer into a cybersecurity expert.
Some examples of changes that buyers could feel include:
- Secure-by-default setup (less “admin/admin” credential combinations, more mandatory password changes and saner defaults)
- No known exploitable vulnerabilities at launch (legal incentives to stop shipping products with obvious issues)
- Actually functional update capability, including support for automatic security updates enabled by default (while also allowing users to opt out)
- Data protection expectations, such as confidentiality safeguards, often translated into modern encryption, and data collection minimization
- Attack surface reduction (fewer unnecessary open services and exposed interfaces)
Manufacturers also need real vulnerability-handling processes behind the scenes, including intake, triage, fixes and communications, because reporting exploited bugs without having a remediation engine doesn’t look good even on paper.
How to prepare your smart home for EU IoT cyber compliance
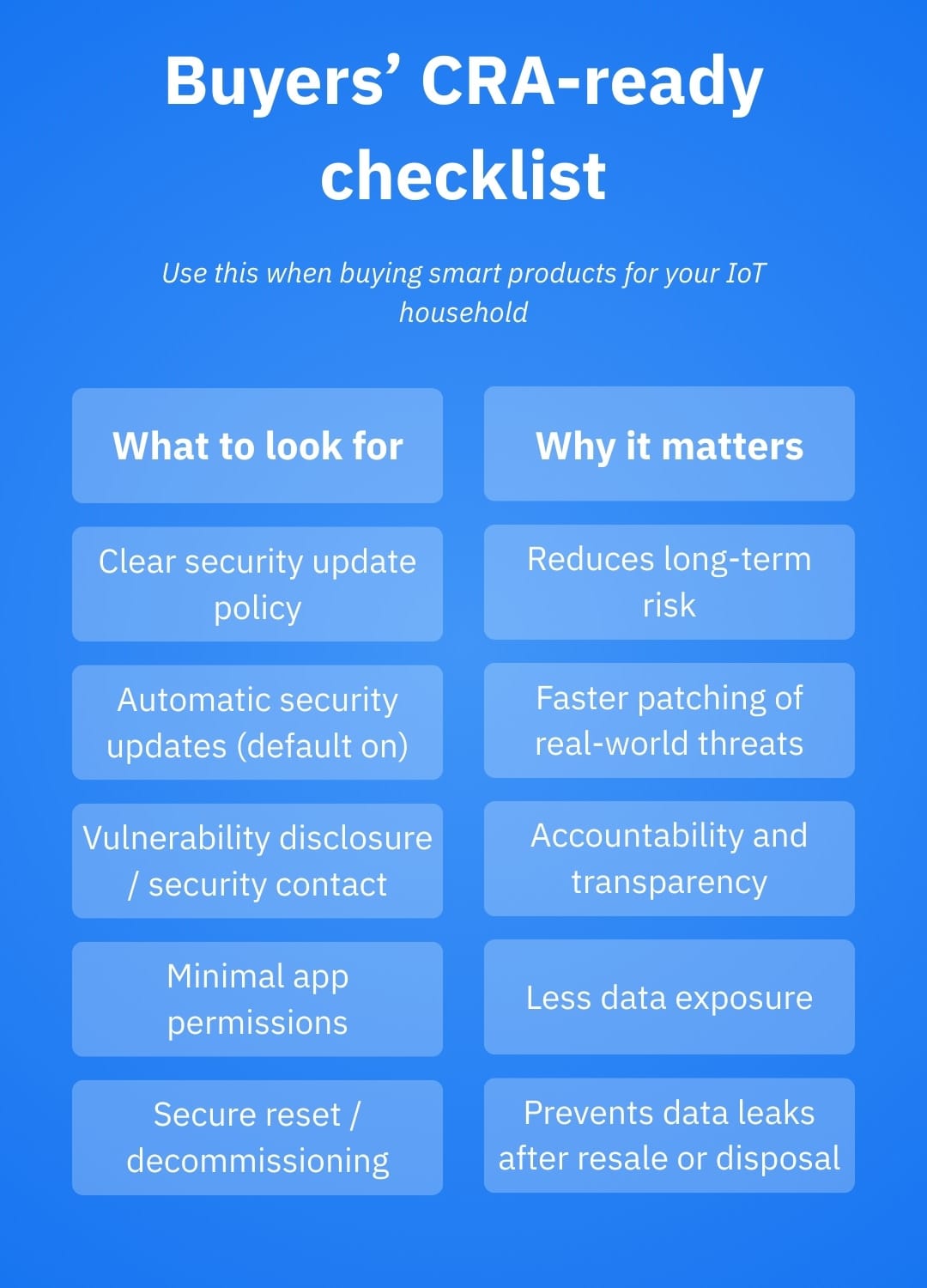
You won’t read technical annexes while standing in an aisle (nor should you). However, what you can do is shop like someone who’s tired of surprise botnets. When you’re choosing your next IoT device, look for these signals:
- Clear update policy: Does the manufacturer say for how long they provide security updates?
- Automatic updates: Is there an option to automatically install security fixes? Is it on by default?
- Responsible disclosure channel: A security contact or vulnerability reporting page is a green flag.
- Least-privilege app permissions: If a smart bulb app wants microphone access, walk away
- Secure reset/decommissioning: Can you wipe data and credentials before reselling or recycling?
The part nobody wants to hear: Compliance doesn’t equal instant protection
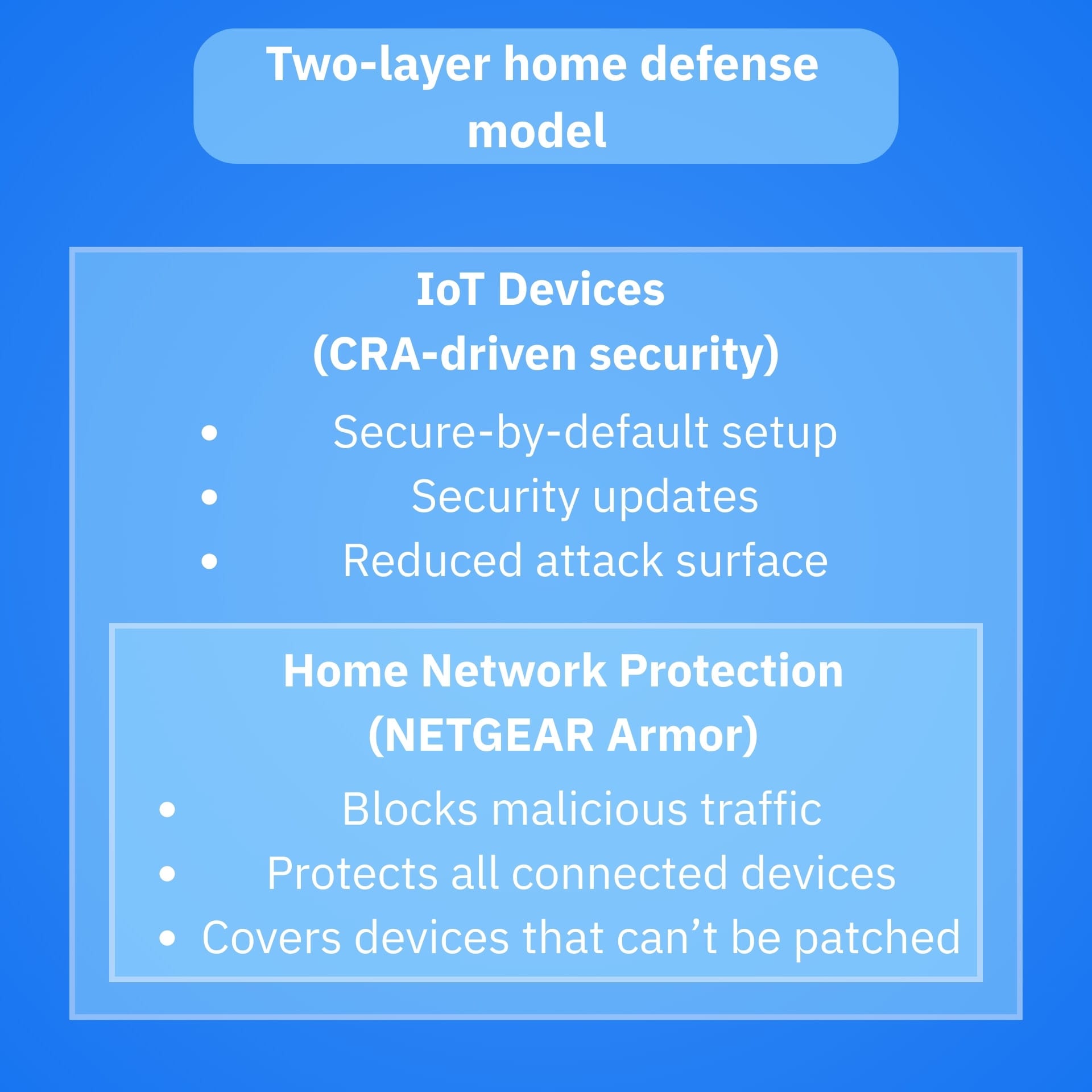
Even perfect regulation can’t patch devices already installed in smart homes, nor can it stop attackers from scanning the internet tonight. CRA is a structural fix, so you can’t expect it to do all the legwork. In other words, you still need an operational layer of defense around your smart home perimeter, especially since many IoT gadgets are hard to monitor, rarely updated, or even abandoned by their manufacturers.
That’s where network-level protection earns its keep. Instead of betting on each device being well-built, you can add security at the point where all traffic converges: your router or mesh system.
Network security strategies beyond CRA compliance
If you want a practical seatbelt for a home full of mixed-brand smart devices, NETGEAR Armor is designed to protect devices connected to your Wi-Fi and to extend protection through its companion app, powered by Bitdefender’s security stack.
For consumers, the value proposition is straightforward:
- Whole network coverage: Helps you protect devices that can’t run traditional endpoint security (many IoT devices fall into this category)
- Malicious site blocking and safer browsing signals: Blocks known bad destinations at the network layer
- Security visibility: Device management and vulnerability-style assessments on the network help you spot weak links
Conclusion
CRA won’t magically make every smart device safe by September 2026, but that date is still important because reporting obligations will force manufacturers to operationalize vulnerability response earlier than many would prefer.
As a consumer, you can use that momentum to buy smart products with update commitments and sane defaults. It’s also worth considering protecting your household immediately with a network security layer like NETGEAR Armor, especially if your home includes IoT devices that are hard to secure individually.
Frequently asked questions (FAQ)
What is the EU CRA compliance?
EU CRA compliance refers to meeting cybersecurity requirements set by the EU Cyber Resilience Act (CRA), which mandates that connected products sold in the EU be designed, developed and maintained with security in mind throughout their lifecycle.
What is CRA compliance?
CRA compliance means following the Cyber Resilience Act (CRA) rules for secure-by-design products, vulnerability handling, security updates and incident reporting for products with digital elements.
Who does the CRA apply to?
The CRA applies primarily to manufacturers of hardware and software with digital elements placed on the EU market, as well as importers and distributors that make those products available in the EU.
How to be CRA compliant?
To be CRA compliant, manufacturers must build security into products from the start, eliminate known vulnerabilities before release, provide timely security updates and implement clear processes for vulnerability disclosure and incident reporting.
What is the Cyber Resilience Act 11 September 2026?
11 September 2026 is the date when the Cyber Resilience Act’s mandatory incident and actively exploited vulnerability reporting requirements begin to apply to products with digital elements placed on the EU market.
tags
Author
Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsYou might also like
Bookmarks


